Some friends of mine they worry about the risk of Man-in-the-middle so they ask me how to verify the potential risk of some Apps.
Take a popular shopping app “X” for example, If “X” does not meet the requirement of “Certificate Pinning”, we could definitely use proxy tool like Burp Suite to intercept any confidential between mobile device and servers.
- Run Burp Suite on my laptop and my laptop becomes a proxy server. (Don’t foreget to change policy of firewall to allow connection to its proxy server listening port.)
- Download Certificate from Burp Suite and install this cert file into my mobile phone.
- Setup the proxy server ip and port in my mobile phone’s wifi settings.(Of course the ip is my laptop’s ip; the port number is the listening port of proxy server on my laptop)
- Make sure Burp suite is ready to intercept packets.
Now we could run this app “X” and start to login. Let’s see what data Burp could intercept. To my surprise “nothing” found in intercept tab.
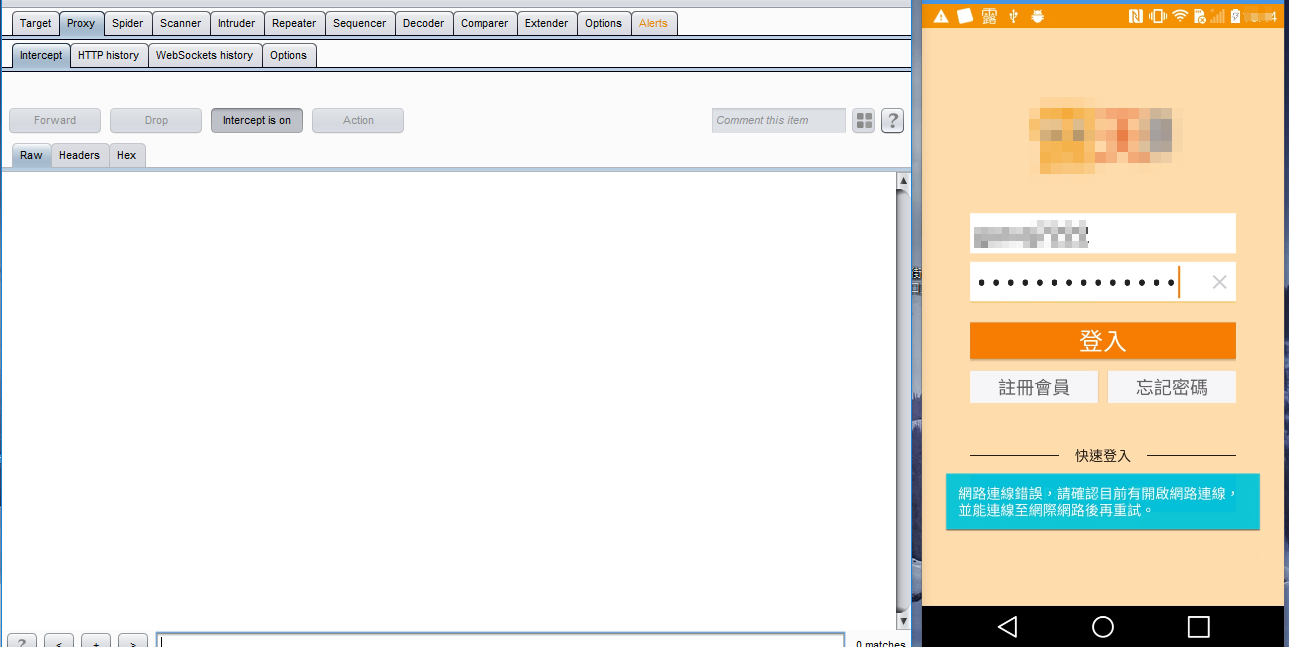
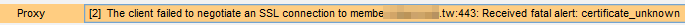
The “Alert” tab turns orange means something happens. It looks like “X” could meet the requirement of certificate pinning.
Don’t jump to conclusions too soon. Let’s take a look at account registry. Input some data such as ID, username , password, phone number, e-mail and click “Submit”. Guess what? Those confidential data being intercepted by Burp suite.
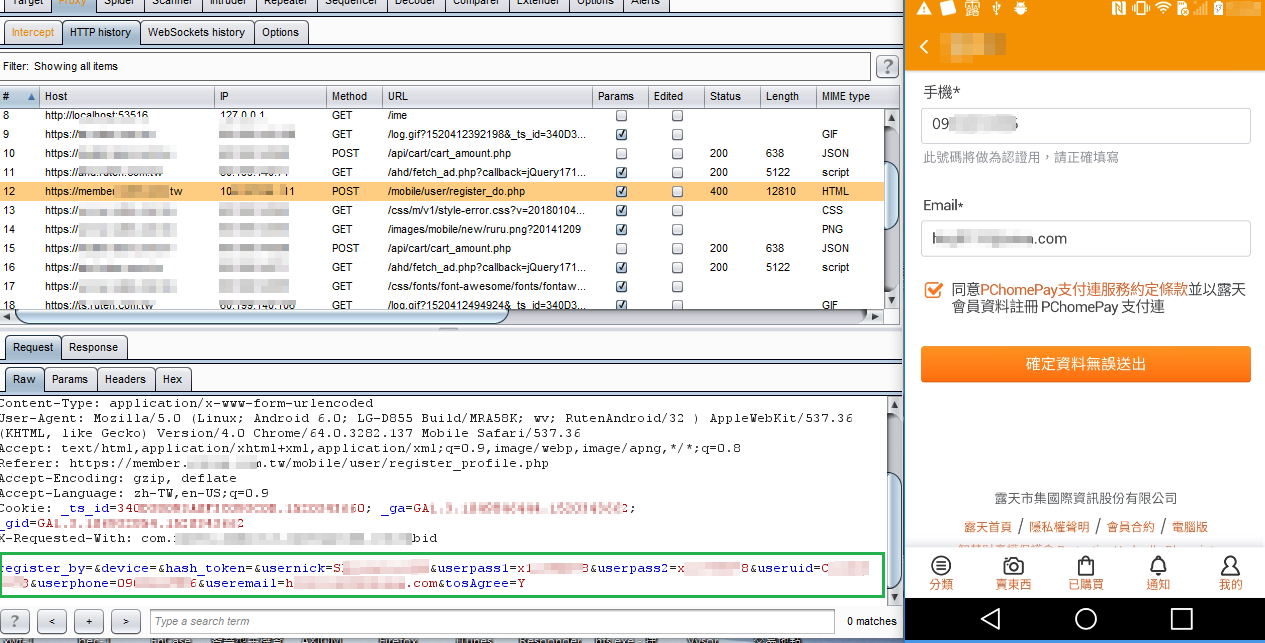
“X” still need to do certificate pinning to avoid the risk of MITM. Now my friends know how to verify certificate pinning by using proxy.