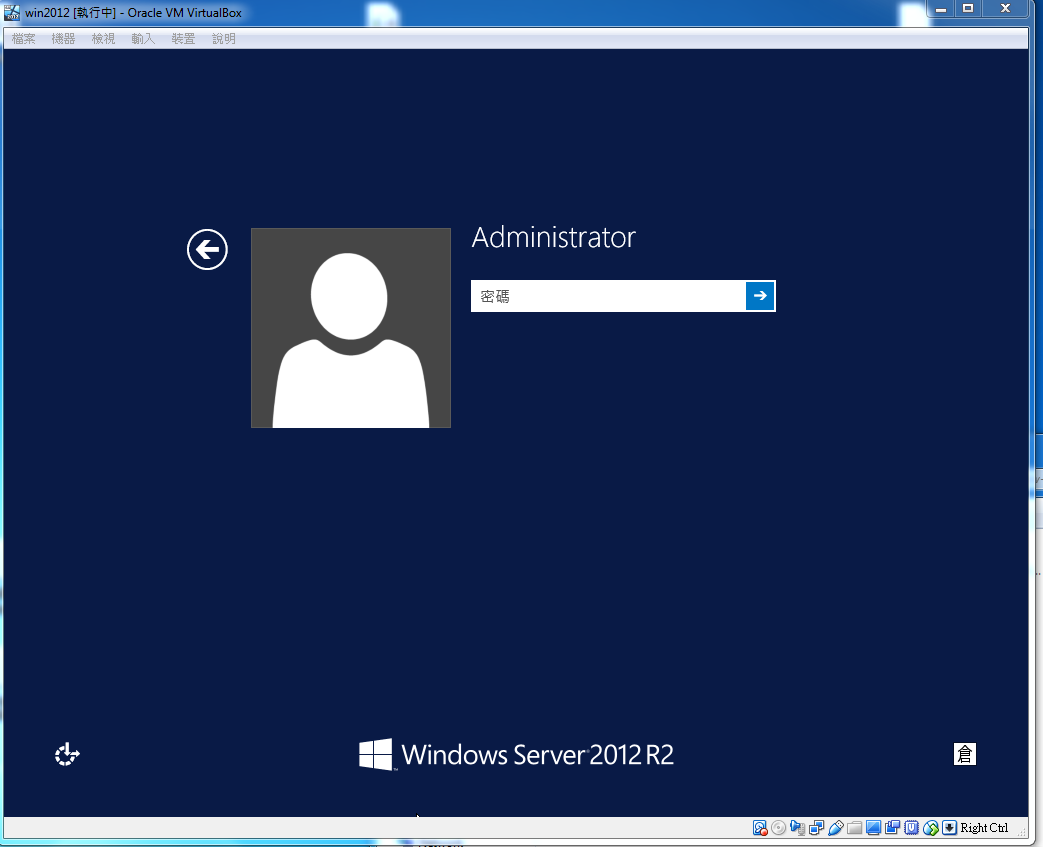
When it comes to booting up evidence files acquired from target disk, you got two options. One is VFC and the other is Live View. Both of them could create snapshots out of images such as EWF(E01). So forensic examiners could conduct a live forensic as if suspect's computer/laptop is in front of them.
Some may ask if there is another option to bootup evidence files. And the answer is "yes". I will show you the combination of FTK Imager and Oracle VirtualBox. First we have to mount evidence files with Admin privileges.
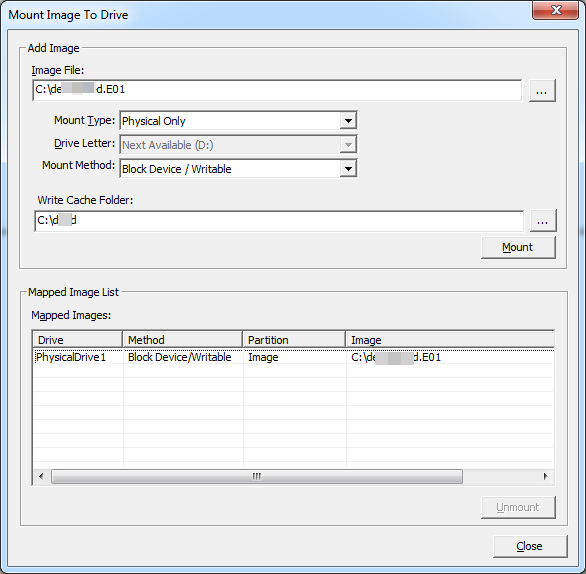
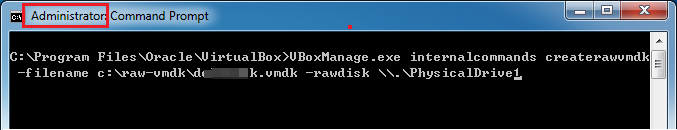
Now we know these evidence files mounted as "PhysicalDrive1". So we have to create vmdk out of this physical drive. Look! It also requires Admin Privileges to run this command prompt.
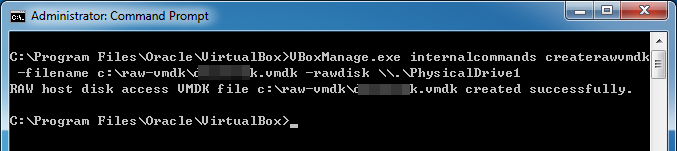
If everything is fine and the result shows that we successfully create vmdk files from PhysicalDrive1.
Next we have to create a Virtual Machine by choosing the existing vmdk files we created as above.
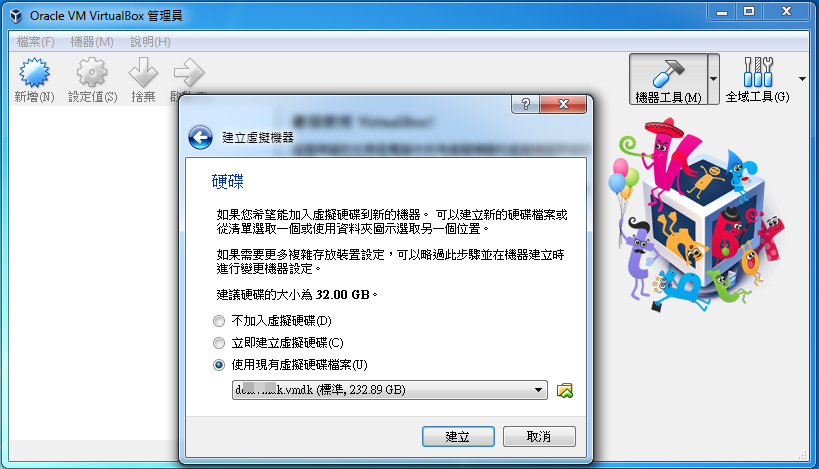
Finally we could bootup suspect's computer/laptop and conduct a live forensics.