2. process::firewall::install(move(rules));如果有参数--firewall_rules则会添加规则
对应的代码如下:
// Initialize firewall rules.
if (flags.firewall_rules.isSome()) {
vector<Owned<FirewallRule>> rules;
const Firewall firewall = flags.firewall_rules.get();
if (firewall.has_disabled_endpoints()) {
hashset<string> paths;
foreach (const
string& path, firewall.disabled_endpoints().paths()) {
paths.insert(path);
}
rules.emplace_back(new DisabledEndpointsFirewallRule(paths));
}
process::firewall::install(move(rules));
}
|
对应的命令行参数如下:
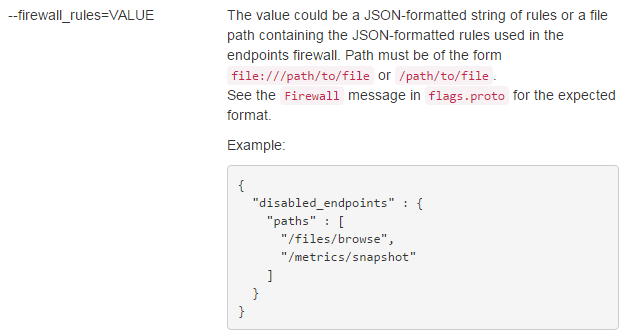
这个参数的主要作用为,并不是Mesos的每一个API都想暴露出来,disabled_endpoints里面就是不能访问的API。
上面的install的代码会做下面的事情


最终会放到环境变量firewallRules里面。
那这些firewall是什么事情起作用的呢?
在3rdparty/libprocess/src/process.cpp里面有函数

synchronized (firewall_mutex) {
// Don't use a const reference, since it cannot be guaranteed
// that the rules don't keep an internal state.
foreach (Owned<firewall::FirewallRule>& rule, firewallRules) {
Option<Response> rejection = rule->apply(socket, *request);
if (rejection.isSome()) {
VLOG(1) << "Returning '"<< rejection.get().status << "' for '"
<< request->url.path << "' (firewall rule forbids request)";
// TODO(arojas): Get rid of the duplicated code to return an
// error.
// Get the HttpProxy pid for this socket.
PID<HttpProxy> proxy = socket_manager->proxy(socket);
// Enqueue the response with the HttpProxy so that it respects
// the order of requests to account for HTTP/1.1 pipelining.
dispatch(
proxy,
&HttpProxy::enqueue,
rejection.get(),
*request);
// Cleanup request.
delete request;
return;
}
}
}
|



