代码来自《精通metasploit 第一版》
#require 'msf/core'
require 'rex/proto/http'
class Metasploit3 < Msf::Auxiliary
include Msf::Exploit::Remote::HttpClient
include Msf::Auxiliary::Scanner
# include Msf::Auxiliary::Report
def initialize
super(
'Name' => 'Server Service Detector',
'Description' => 'Get some system versuib information.',
'Author' => 'Pr1s0n',
'License' => MSF_LICENSE
)
end
def os_fingerprint(response)
if not response.headers.has_key?('Server')
return "Unknowen OS(No Server Header)"
end
case response.headers['Server']
when /Win32/, /(Windows/, /IIS/
os = "Windows"
when /Apache//
os = "*Nix"
else
os = "Unknown Server Header Reporting:" + response.headers['Server']
end
return os
end
def pb_fingerprint(reponse)
if not response.headers.has_key?('X-Powered-By')
resp = 'No-Response'
else
resp = response.headers['X-Powered-By']
end
return resp
end
def run_host(ip)
connect
res = send_request_raw({'uri' => '/', 'method' => 'GET'})
return if not res
os_info = os_fingerprint(res)
pb = pb_fingerprint(res)
fp = http_fingerprint(res)
print_status("#{ip}:#{rport} is running #{fp} version And Is Powered By: #{pb} Running On #{os_info}")
end
end
一直报的这个错误
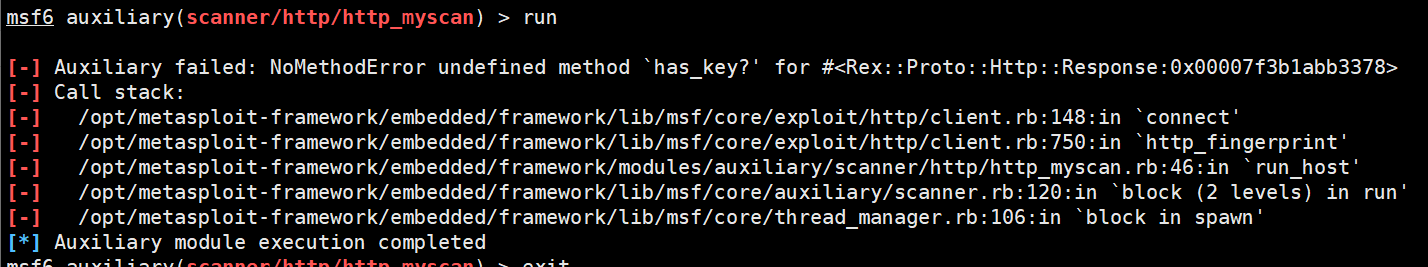
一开始没理解报错原因,还以为问题出在has_key?上,查了一下发现
hash.has_key?(key) [or] hash.include?(key) [or]
hash.key?(key) [or] hash.member?(key)
检查给定的 key 是否存在于哈希中,返回 true 或 false。
这个写法是没错的
头发都快薅秃了最后才想到可能是因为书里的msf版本和现在的msf6有差异,更改了http_fingerprint(这玩意儿命名搞得一点也不像官方函数)的调用方式
于是我就看了一下官方自带的http_version模块
http_fingerprint接收一个http请求返回值时的用法为
http_fingerprint(:response => res)
修改后成功运行
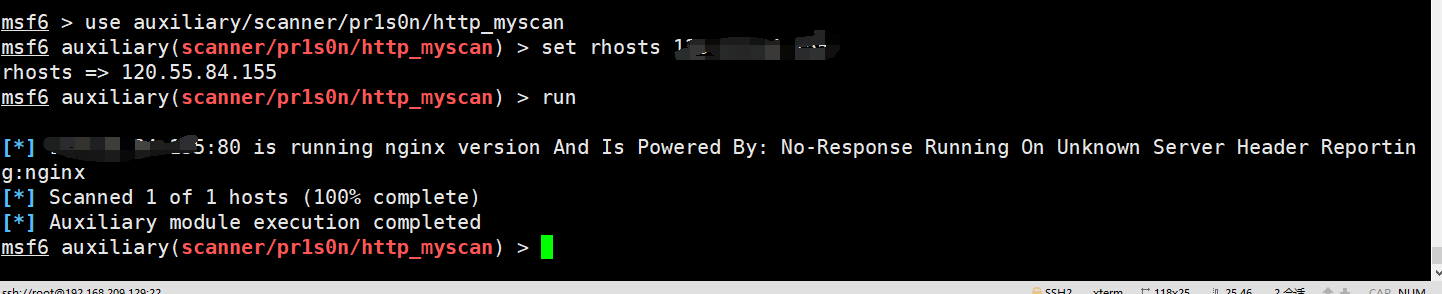
最终代码为
require 'msf/core'
require 'rex/proto/http'
class Metasploit3 < Msf::Auxiliary
include Msf::Exploit::Remote::HttpClient
include Msf::Auxiliary::Scanner
include Msf::Auxiliary::WmapScanServer
# include Msf::Auxiliary::Report
def initialize
super(
'Name' => 'Server Service Detector',
'Description' => 'Get some system versuib information.',
'Author' => 'Pr1s0n',
'License' => MSF_LICENSE
)
end
def os_fingerprint(response)
if not response.headers.has_key?('Server')
return "Unknowen OS(No Server Header)"
end
case response.headers['Server']
when /Win32/, /(Windows/, /IIS/
os = "Windows"
when /Apache//
os = "*Nix"
else
os = "Unknown Server Header Reporting:" + response.headers['Server']
end
return os
end
def pb_fingerprint(response)
if not response.headers.has_key?('X-Powered-By')
resp = 'No-Response'
else
resp = response.headers['X-Powered-By']
end
return resp
end
def run_host(ip)
begin
connect
res = send_request_raw({'uri' => '/', 'method' => 'GET' })
return if not res
os_info=os_fingerprint(res)
pb=pb_fingerprint(res)
fp = http_fingerprint(:response => res)
print_status("#{ip}:#{rport} is running #{fp} version And Is Powered By: #{pb} Running On #{os_info}")
end
end
end