一、CA简介
CA是什么?CA是Certificate Authority的简写,从字面意思翻译过来是凭证管理中心,认证授权。它有点类似我们生活中的身份证颁发机构,这里的CA就相当于生活中颁发身份证的机构。不同于生活中的颁发机构,这里的CA是给服务器颁发证书。颁发证书的目的同生活中的办理身份证的目的类似,都是为了证明一件事,生活中的身份证可以证明我们是一个合法的公民,而服务器颁发证书的目的也是证明我们服务是一个合法的服务器,换句话说就是有了证书我们就可以清楚知道我们访问的服务器到底是不是我们真正想访问的服务器。从而识别我们访问的服务器的真假。
二、中间人攻击原理
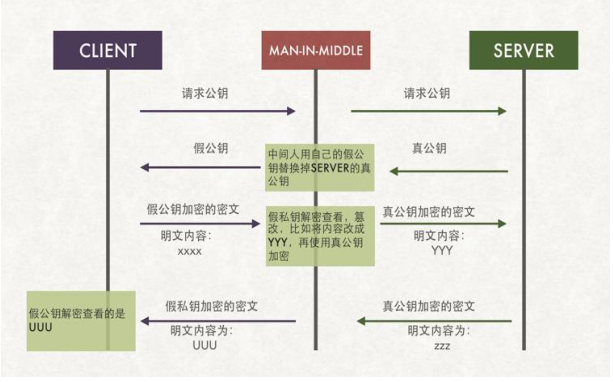
如上图所示,我们在和对方服务器通信的过程,存在着中间人攻击的情况。所谓中间人攻击,就是攻击者站在通讯双方的中间,对于客户端它充当着服务器的角色,对于服务器端它又充当着客户端的角色。简单说它就是两边欺骗。当我们向服务器发起通信请求时,中间人会截获我们发向服务器端的报文,从而进行修改,然后把修改后的报文发送给服务端,服务端收到中间人篡改的数据报文,进行响应,把响应报文发送给中间人,然后中间人再发给客户端。这样一个过程就是中间人攻击的过程。可以看到客户端服务端双方直接通信是不安全的。如上图所示,通信双方交换密钥,直接交换就存在中间人欺骗,因为我们不能够确定远端服务器的真伪和客户端的真伪。为了解决这一问题,由此衍生出CA。CA在这里的充当的角色相当于中间人角色,不同的是CA是一个权威的中间人。它可以证明客户端和服务端的真伪。
三、加密解密以及获取公钥过程
众所周知常用的加密方式有三种,单向加密,对称加密,和非对称加密。单向加密从字面意思理解就是一方加密,在加密过程中不使用密钥,我们把单向加密也叫不可逆加密,通常用于验证文件的真假,或者验证文件是否改动,从而验证文件的完整性。常用的单向加密算法有md5,sha。对称加密讲的是加密和解密用的同一密钥。换句话说对称加密只有一个密钥,只要拿到对应的密钥就可以解密。常用的对称加密有des。非对称加密讲的是公钥加密私钥解密,私钥加密公钥解密,且公钥和私钥是一对,加密解密都需要的是一对密钥里的任意一个。这种加密比前两种更加安全和适用,缺点是加解密大文件速度慢。
了解了非对称加密的特性,我们再来说说它的过程。通信双方要进行非对称加密通信,前提是需要拿到对方的公钥,私钥放在各自手里,各自的公钥则存放在对方的手上。换句话讲,客户端需要拿到服务端的公钥,才能和服务端通信,服务端需要拿到客户端的公钥,才能主动和客户端通信。从而才可以实现非对称加密通信。那么客户端怎么得到服务端的公钥呢?如果客户端直接向服务端发送公钥,上面我们说过,这种方式存在中间人攻击,因为直接交换公钥是不都能确定对方身份的。这个时候就需要说说CA证书的作用了。
证书里面存放了申请证书机构服务器的公钥和CA的信息以及有效期。通讯双方在建立加密通信的时候,需要验证证书的合法性,从而实现验证身份的目的。通常情况我们要验证证书的合法性就需要证书颁发机构的公钥来对证书解密,因为证书在颁发的时候,里面的公钥是通过颁发机构的私钥对其进行加密的。只要我们能够用颁发机构的公钥解开证书,那么就说明这个证书就是一个合法的证书,至少它证明了这个证书是权威机构(我们信任的)CA颁发的。同理通信双方要进行加密通信也是通过证书来获取密钥的。具体过程是这样的,客户端向服务端发起通信请求,服务端发送证书给客户端,客户端拿到证书进行解密,如果能够用信任CA机构的公钥解开,说明服务器发送过来的证书没有问题,然后把服务端公钥给存起来。客户端有了服务端的公钥后就可以向服务端发送用服务端的公钥加密的数据了,但是服务端没有客户端的公钥,它不能够用自己的私钥来加密数据发送给客户端,因为它的公钥是公开的,不光客户端上有服务端的公钥,中间人也有。所以为了确保数据的安全,客户端需要随机生成一个密码,然后通过服务器的公钥,把随机生成的密码加密后发送给服务端,服务端收到客户端发来的加密数据后,用自己的私钥解开,从而拿到客户端发来的随机密码,有了这个随机密码后,服务端就拿这个随机密码对称加密数据,然后发送给客户端。客户端收到服务端发送过来的加密报文,用刚才发送给服务端的随机密码解密,从而得到真正的数据。后续双方就是通过这个随机密码来加密解密传输数据。这里还需要说明的是,这个随机密码不是一直不变的,每隔一段时间后,客户端和服务端就会协商,重复上面的过程,生成新的随机密码进行加密解密通信。
从上面的通信过程我们可以知道,证书的作用就是为了验证其服务器的真实合法性,以及传输服务端的公钥的作用。而服务器的公钥就是用来客户端向服务端发送随机密码,用来加密随机密码的作用,从而实现,只有服务端可以拿到这个随机密码的作用,实现安全加密通信。
四、CA服务器的实现
1、安装openssl软件
[root@test ~]# yum install openssl -y
说明:通常情况下openssl是系统默认安装的有,如果没有需要安装。
2、查看配置文件,以及匹配策略
36 [ ca ] 37 default_ca = CA_default # The default ca section 38 39 #################################################################### 40 [ CA_default ] 41 42 dir = /etc/pki/CA # Where everything is kept 43 certs = $dir/certs # Where the issued certs are kept 44 crl_dir = $dir/crl # Where the issued crl are kept 45 database = $dir/index.txt # database index file. 46 #unique_subject = no # Set to 'no' to allow creation of 47 # several ctificates with same subject. 48 new_certs_dir = $dir/newcerts # default place for new certs. 49 50 certificate = $dir/cacert.pem # The CA certificate 51 serial = $dir/serial # The current serial number 52 crlnumber = $dir/crlnumber # the current crl number 53 # must be commented out to leave a V1 CRL 54 crl = $dir/crl.pem # The current CRL 55 private_key = $dir/private/cakey.pem# The private key 56 RANDFILE = $dir/private/.rand # private random number file 57 58 x509_extensions = usr_cert # The extentions to add to the cert 59 60 # Comment out the following two lines for the "traditional" 61 # (and highly broken) format. 62 name_opt = ca_default # Subject Name options 63 cert_opt = ca_default # Certificate field options 64 65 # Extension copying option: use with caution. 66 # copy_extensions = copy 67 68 # Extensions to add to a CRL. Note: Netscape communicator chokes on V2 CRLs 69 # so this is commented out by default to leave a V1 CRL. 70 # crlnumber must also be commented out to leave a V1 CRL. 71 # crl_extensions = crl_ext 72 73 default_days = 365 # how long to certify for 74 default_crl_days= 30 # how long before next CRL 75 default_md = sha256 # use SHA-256 by default 76 preserve = no # keep passed DN ordering 77 78 # A few difference way of specifying how similar the request should look 79 # For type CA, the listed attributes must be the same, and the optional 80 # and supplied fields are just that :-) 81 policy = policy_match 82 83 # For the CA policy 84 [ policy_match ] 85 countryName = match 86 stateOrProvinceName = match 87 organizationName = match 88 organizationalUnitName = optional 89 commonName = supplied 90 emailAddress = optional 91 92 # For the 'anything' policy 93 # At this point in time, you must list all acceptable 'object' 94 # types. 95 [ policy_anything ] 96 countryName = optional 97 stateOrProvinceName = optional 98 localityName = optional 99 organizationName = optional 100 organizationalUnitName = optional 101 commonName = supplied 102 emailAddress = optional 103 104 ####################################################################
说明:可看到openssl默认配置里面指定了证书存放相关文件的路径,和CA默认匹配策略,其中国家名称、省州名称、组织名称是必须同CA设置的信息一致,当然这些匹配是否和CA设置的一样,是通过配置文件来判断的可自行设置。通用名称是必须要填写的,其他都是可选。
3、创建CA自签名证书
3.1、生成私钥
[root@test ~]# cd /etc/pki/CA/
[root@test CA]# tree
.
├── certs
├── crl
├── newcerts
└── private
4 directories, 0 files
[root@test CA]# (umask 077;openssl genrsa -out /etc/pki/CA/private/cakey.pem 2048)
Generating RSA private key, 2048 bit long modulus
..............................+++
............+++
e is 65537 (0x10001)
[root@test CA]# tree
.
├── certs
├── crl
├── newcerts
└── private
└── cakey.pem
4 directories, 1 file
[root@test CA]# cat private/cakey.pem
-----BEGIN RSA PRIVATE KEY-----
MIIEogIBAAKCAQEAmM8gDY90zksYI2myhqsGgMBGAPnlLbIBwiqYnte2PJZRnEJv
aYRzCgw9wSca9oI5rUGu1wLOk8NlAkE6W4hXu6JaAp/eMZcqzYVU2a6VhxPQLBP3
5dvfZT4vps737OR+l8gcJRX2VPcfJuMU+r4KbBT4F3gP79hz/JxwK0yShlIGCnPP
cCK5xS6jKBH3ezdLsRy0ZCRUwX+ivlAJ8zJ/bV4m2OesiDW1LFPrvotRo+aBwexI
1vk01Yww1x/DUnxiYCrOPS0V3wWpSS6r2qXVv0FyZGS1ZP/+Jf1ZfbvL2w9kcmlQ
0wadHkx3M4HJyvWinOEpMsrTr3p9RK67oNs48QIDAQABAoIBADUWQBx16i6BCDHF
VrBSWkAAjFFqf6QQY2wBQGRurHEAB/oxWmNeEFk9R3cDDur08vSuDP/Fid7r0vul
jZCfHVuiW4Lt51NzIPulhoTZkjkLORcXGNhSOpoBsKxS2u8BsrkoXB7GMn3yHHB2
E6PIwfYqksYUf/TjTehEsPNZ9s2Sx/ioscHfnIRd7Uct0Gu5mI5C6qP/7BhEyNRb
bnFGGB0dSFDtFPqGUIfTeWApJUH1/vUTUXrrZLH4FEubMuf4k0ZIV3cGyvdZVVQ+
iyoWTTetPOhFbRMnKtqgJ+yVhck7uEAgIB/JrMI3x768JoJpyAgxGlZFmxS86mdr
TzDzZcECgYEAxwv/Jcrb3E5gGC77qSEWlq+IVomAgHRVU4M81byw6YV7wAssW10t
X8pm84H3G8yJMuxGYdHdXpl9PzxwXaS7Qh82uZVQbGALiWyhHloEIoI+oH9pGtXf
uWqQKmrYURtq8AoULhALn03zCjJINGfY9/WlYX6qi32UpnKg6snmDD8CgYEAxIhA
u+By9YazW/YVgEHoh5UmWL0yfX8rBEn1fRwwhjfhQtfs50zoL83SVKpKY8VtfR/r
/YcIaWx8+R5g+g/aAYDeKHO1x+uW2yqWMdXjdkY/kzoM0G7gPvSC7F3vr6dWuHUC
6v4839EElIKHyCK0NMumnPvoUUDrbP1YlJ1cLs8CgYBsGU/QLoOI+eemOp3iFF44
J8xbcwGewY81c6iuS3Oo3x1+BpNoawohY8LVrFePeV1pkngG1/rpTWJ/3UsJEFXC
a0FFOJocwWyCjcRSv4BPXXy1nXxvXofKIt14q94e7kz9X/vlqEEnmyXK+9PK4jsr
LvVKJYhpiSIZ41cRK+UL8QKBgF0S3f1b3XWTtkt97k7QZ8wWAZQS/d9bI0cjs4Pt
nrlhq2eZlNMxo+BHzC1WfGZlsGWKgZuOoJg0zba5AVpLuYXuvsdPjS5Bzy66K2ks
j02LFT6nRjxL1h1adMp17jY0vKgcmiYqAzBH77BZZO6OKOO78orz7eDVKulxzcqL
/4UXAoGAKk1Yfa8ZVJGlzjZHl/imvce2B+78ALJItw8hUAOxjU3780vzuppyG5o/
Zg25XbW9FbOUXt+8Tyd3/yFBBGdZ1OvL9YSngtGyLX7X3aWbg9xwR7fz8bheI+J7
QcLouNuHoUis+3EHbQIcQM9CTrP7sjFMM2LxPzxz7qPuV0ru2bg=
-----END RSA PRIVATE KEY-----
[root@test CA]#
说明:为了创建的私钥的安全,建议把其权限修改成600。当然创建私钥的时候也可以用对称加密算法对其私钥加密,这样更加安全。需要注意的是加密后的私钥,我们要用的时候就需要对其输入对称加密的口令。如果需要把私钥用对称加密算法加密,需要指定其加密算法即可。生成的私钥名称必须同配置文件中的名称相同。
3.2、签发自签名证书
[root@test CA]# openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -out /etc/pki/CA/cacert.pem -days 1000You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:SICHUAN
Locality Name (eg, city) [Default City]:GUANGYUAN
Organization Name (eg, company) [Default Company Ltd]:TEST
Organizational Unit Name (eg, section) []:DEVOPS
Common Name (eg, your name or your server's hostname) []:ca.test.com
Email Address []:
[root@test CA]# tree
.
├── cacert.pem
├── certs
├── crl
├── newcerts
└── private
└── cakey.pem
4 directories, 2 files
[root@test CA]# cat cacert.pem
-----BEGIN CERTIFICATE-----
MIIDpTCCAo2gAwIBAgIJANCoyQ6AYK/SMA0GCSqGSIb3DQEBCwUAMGkxCzAJBgNV
BAYTAkNOMRAwDgYDVQQIDAdTSUNIVUFOMRIwEAYDVQQHDAlHVUFOR1lVQU4xDTAL
BgNVBAoMBFRFU1QxDzANBgNVBAsMBkRFVk9QUzEUMBIGA1UEAwwLY2EudGVzdC5j
b20wHhcNMjAwMTI5MTAzNjM2WhcNMjIxMDI1MTAzNjM2WjBpMQswCQYDVQQGEwJD
TjEQMA4GA1UECAwHU0lDSFVBTjESMBAGA1UEBwwJR1VBTkdZVUFOMQ0wCwYDVQQK
DARURVNUMQ8wDQYDVQQLDAZERVZPUFMxFDASBgNVBAMMC2NhLnRlc3QuY29tMIIB
IjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAmM8gDY90zksYI2myhqsGgMBG
APnlLbIBwiqYnte2PJZRnEJvaYRzCgw9wSca9oI5rUGu1wLOk8NlAkE6W4hXu6Ja
Ap/eMZcqzYVU2a6VhxPQLBP35dvfZT4vps737OR+l8gcJRX2VPcfJuMU+r4KbBT4
F3gP79hz/JxwK0yShlIGCnPPcCK5xS6jKBH3ezdLsRy0ZCRUwX+ivlAJ8zJ/bV4m
2OesiDW1LFPrvotRo+aBwexI1vk01Yww1x/DUnxiYCrOPS0V3wWpSS6r2qXVv0Fy
ZGS1ZP/+Jf1ZfbvL2w9kcmlQ0wadHkx3M4HJyvWinOEpMsrTr3p9RK67oNs48QID
AQABo1AwTjAdBgNVHQ4EFgQUQ/0tcuVAvzoOA13SD2x8W9Brx0EwHwYDVR0jBBgw
FoAUQ/0tcuVAvzoOA13SD2x8W9Brx0EwDAYDVR0TBAUwAwEB/zANBgkqhkiG9w0B
AQsFAAOCAQEAAl/gUsSCgKjeSq5K2TyLc3VUP2KN1m+Wu9qWKAgXiaMxY8iWj3I8
AxfNkTAqNGz66BpXh9G4hDL844spvnomjdUbCufFlNLnrkxCIyWPNVKk69fCa61T
ANzgvTbIfh/xfdfyctZpU3q9Ptcra9ksYUg7mY7209xJ+emqsBnKwYKigCCrQTT3
dxvRHFOV3Z0wJgHCtTetMI25OcpEXk3Tk75k+ayEmiTdMp2Zdk00qmOtZfCmtHO9
KdHVTAOCAOaQtd4aOZMsgADBWXVP2NPmosUm2onvrKTFB6tYXXhj5j6tPVFunCZE
R2w2VMa+Q+Pgmmt5AeqoALQaBdR31IFj0Q==
-----END CERTIFICATE-----
[root@test CA]#
说明:颁发的证书默认是没法用cat命令来查看证书里面的信息的,我们可以通过把证书导出到windows上查看,也可以通过openssl来查看。ca的私钥和证书存放路径需要参考其配置文件中的定义来指定存放。
在windows上查看办法的证书



说明:在Windows上查看,需要把其后缀更改为.crt才可以双击查看。之所以它提示我们说此CA根目录证书不受信用,是因为windows上没有将其证书导入,没有改根CA的信息。默认情况下,Windows里面内置了一些权威CA的证书,所以我们在权威的CA下申请的证书,放在windows上就不会报不信任的CA证书了。
用openssl查看证书
[root@test CA]# openssl x509 -in cacert.pem -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
d0:a8:c9:0e:80:60:af:d2
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=CN, ST=SICHUAN, L=GUANGYUAN, O=TEST, OU=DEVOPS, CN=ca.test.com
Validity
Not Before: Jan 29 10:36:36 2020 GMT
Not After : Oct 25 10:36:36 2022 GMT
Subject: C=CN, ST=SICHUAN, L=GUANGYUAN, O=TEST, OU=DEVOPS, CN=ca.test.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:98:cf:20:0d:8f:74:ce:4b:18:23:69:b2:86:ab:
06:80:c0:46:00:f9:e5:2d:b2:01:c2:2a:98:9e:d7:
b6:3c:96:51:9c:42:6f:69:84:73:0a:0c:3d:c1:27:
1a:f6:82:39:ad:41:ae:d7:02:ce:93:c3:65:02:41:
3a:5b:88:57:bb:a2:5a:02:9f:de:31:97:2a:cd:85:
54:d9:ae:95:87:13:d0:2c:13:f7:e5:db:df:65:3e:
2f:a6:ce:f7:ec:e4:7e:97:c8:1c:25:15:f6:54:f7:
1f:26:e3:14:fa:be:0a:6c:14:f8:17:78:0f:ef:d8:
73:fc:9c:70:2b:4c:92:86:52:06:0a:73:cf:70:22:
b9:c5:2e:a3:28:11:f7:7b:37:4b:b1:1c:b4:64:24:
54:c1:7f:a2:be:50:09:f3:32:7f:6d:5e:26:d8:e7:
ac:88:35:b5:2c:53:eb:be:8b:51:a3:e6:81:c1:ec:
48:d6:f9:34:d5:8c:30:d7:1f:c3:52:7c:62:60:2a:
ce:3d:2d:15:df:05:a9:49:2e:ab:da:a5:d5:bf:41:
72:64:64:b5:64:ff:fe:25:fd:59:7d:bb:cb:db:0f:
64:72:69:50:d3:06:9d:1e:4c:77:33:81:c9:ca:f5:
a2:9c:e1:29:32:ca:d3:af:7a:7d:44:ae:bb:a0:db:
38:f1
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
43:FD:2D:72:E5:40:BF:3A:0E:03:5D:D2:0F:6C:7C:5B:D0:6B:C7:41
X509v3 Authority Key Identifier:
keyid:43:FD:2D:72:E5:40:BF:3A:0E:03:5D:D2:0F:6C:7C:5B:D0:6B:C7:41
X509v3 Basic Constraints:
CA:TRUE
Signature Algorithm: sha256WithRSAEncryption
02:5f:e0:52:c4:82:80:a8:de:4a:ae:4a:d9:3c:8b:73:75:54:
3f:62:8d:d6:6f:96:bb:da:96:28:08:17:89:a3:31:63:c8:96:
8f:72:3c:03:17:cd:91:30:2a:34:6c:fa:e8:1a:57:87:d1:b8:
84:32:fc:e3:8b:29:be:7a:26:8d:d5:1b:0a:e7:c5:94:d2:e7:
ae:4c:42:23:25:8f:35:52:a4:eb:d7:c2:6b:ad:53:00:dc:e0:
bd:36:c8:7e:1f:f1:7d:d7:f2:72:d6:69:53:7a:bd:3e:d7:2b:
6b:d9:2c:61:48:3b:99:8e:f6:d3:dc:49:f9:e9:aa:b0:19:ca:
c1:82:a2:80:20:ab:41:34:f7:77:1b:d1:1c:53:95:dd:9d:30:
26:01:c2:b5:37:ad:30:8d:b9:39:ca:44:5e:4d:d3:93:be:64:
f9:ac:84:9a:24:dd:32:9d:99:76:4d:34:aa:63:ad:65:f0:a6:
b4:73:bd:29:d1:d5:4c:03:82:00:e6:90:b5:de:1a:39:93:2c:
80:00:c1:59:75:4f:d8:d3:e6:a2:c5:26:da:89:ef:ac:a4:c5:
07:ab:58:5d:78:63:e6:3e:ad:3d:51:6e:9c:26:44:47:6c:36:
54:c6:be:43:e3:e0:9a:6b:79:01:ea:a8:00:b4:1a:05:d4:77:
d4:81:63:d1
[root@test CA]#
4、在客户端创建证书申请
4.1、生成私钥信息
[root@test-node3 ~]# mkdir ssl [root@test-node3 ~]# cd ssl/ [root@test-node3 ssl]# (umask 077;openssl genrsa -out /root/ssl/app.key 2048) Generating RSA private key, 2048 bit long modulus .............................................................+++ .........................+++ e is 65537 (0x10001) [root@test-node3 ssl]# ls app.key [root@test-node3 ssl]# cat app.key -----BEGIN RSA PRIVATE KEY----- MIIEpQIBAAKCAQEA6XtScxyxgI7gC+1xYQFSXIF9RqCTAZ4WpWGQYzs30XLT1cxl /hJ8McxMQ137H1g+PeEFbNV3oyBjEt3feCck5sb9TP4tsIhT6Lt3Zt6PIqOfDZ8k OxWDJp/DNXHwuC8ME/mfv3CleJbL5Clyb9ovYeZkEQPK9TgG7pCHU0AxTw0r7ELP A29Ugd/lFGQNTJt39Kmy7uBOPhKEQ+fHVaMqtmy1q/SpnM92vGvR40xRgl+HJ17A 0ACAEjbf3wK+qoQ/WBCCpMkeTLoFEn/Sa7SmZZt2F0k2cTyxSzVKadPQUlrpWVHb zX4IDI/ssS9weiDsLL5eScj/CWWRFhKu7z98YQIDAQABAoIBAQDKu6RqA741DNqK QNC0FHu5i06GJyO+wdCUJdVD9MWQ/o3mFSdyqAZjDywhStek7fCNtngJeon5gUPF vBYwtHycTqjfU83EfXuumCkjj5jl0QFoyIijLRjGTu8n1xnYNDHenmAR0PQ9c2Lz aPHPIbsG3RCCnbJ7nvyV5bU7mn+2TOb41csMVjLJoK2N91QEljkAn+4oqpTVJgJa TnUKvafBjCn+ctZDKcsZ0H/yFhGbt0ZFEXql3WFM5AOE5tBmlmqrQY/4CzeqlPCX zYpuUCHQBj9UYj58SfVUEoaN+gNX82amUqBOablJMpGR0vDh0CxsAxnPYF7O1o6P hXIjjmPJAoGBAPg74aMUMoG3o91NpoedLdRrMOYcYBdd3H7KwPyXzHMoYHQjfHEm hJKqZgE53U+TfxdFr8EJcR8aoDzDLp3+5F1ANCZD2FgvWptAyABx+I09J0OES0VB M3hhp0pOYot1ylBbFrvGGANFa8WAnO+yyNU91CFUhp7kmQ5TuUUHt2kzAoGBAPDJ SiXn30hQO8zVCHXzCrcltKfSnU4LiceI0jhneHfW8b42/tEegXVTEOIBiPmhLA8x 8xeIC/fS1B0ih7Uus9MUBJUN7RhlWSxGPcxA//JAxffGJwmxoYxYFkwvoTyTQrJE igBmE6+PdSb7JOB4c3nt/YwPYvjQOieNolRMIwwbAoGBAOoNhA2AwLKAVVgXnBoo QIsV2pBNVukRThKa1+YStuopuvAmeXIysDOdyPoE9j/OwblOso2fenKqZ0WDf1Pn fqjSHZmqxLU5SQQzy6Bn1cROUdQeS95rwL0TzmmIiPAXyv+DM2cvO3ryHNCnGNIF T8mIN5iJmzj8L7hLhteok+3zAoGAbot7RzvU/tYXHksPv1b9rGfbMNE49wPFFZ5z JQIcBKjiA3osMsXWmY6xSZF62WBtYeyEtmD3XaelSlr4Au6WEGo4UFY8a97bub/l z0hoOUgTm1WVxpWOnWgzlHaph630CPP+h4BVuVwbZPIYVBX4rhndNdg6kBDJIi+c PydVT9ECgYEAwF5U/YS9IIb8n1NXARXA3nWmfqdJM2JcYwh33ILFB0+2gm4nr4Ie xb14BlFMl8mYVKqykHpdE73/LYZWu/inkti8APmHyP3+7QHMWagpCucCHxGzagWy sdo8HSqbkcQJoB0pTLPZGHEGuLMzzAII6fc+sZsHPi2NLbZZFPGdWjk= -----END RSA PRIVATE KEY----- [root@test-node3 ssl]#
4.2、生成证书申请文件
[root@test-node3 ssl]# ll total 4 -rw------- 1 root root 1679 Jan 29 18:55 app.key [root@test-node3 ssl]# openssl req -new -key app.key -out app.csr You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:SICHUAN Locality Name (eg, city) [Default City]:CHENGDU Organization Name (eg, company) [Default Company Ltd]:TEST Organizational Unit Name (eg, section) []:DEVOPS Common Name (eg, your name or your server's hostname) []:www.test.org Email Address []: Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []: [root@test-node3 ssl]# ll total 8 -rw-r--r-- 1 root root 1005 Jan 29 19:02 app.csr -rw------- 1 root root 1679 Jan 29 18:55 app.key [root@test-node3 ssl]
4.3、把文件传给CA,在CA上进行证书颁发
[root@test CA]# rz
rz waiting to receive.
zmodem trl+C ȡ
100% 1005 bytes 1005 bytes/s 00:00:01 0 Errors
[root@test CA]# ls
app.csr cacert.pem certs crl newcerts private
[root@test CA]# openssl ca -in app.csr -out /etc/pki/CA/certs/app.crt -days 365
Using configuration from /etc/pki/tls/openssl.cnf
/etc/pki/CA/index.txt: No such file or directory
unable to open '/etc/pki/CA/index.txt'
140645247747984:error:02001002:system library:fopen:No such file or directory:bss_file.c:402:fopen('/etc/pki/CA/index.txt','r')
140645247747984:error:20074002:BIO routines:FILE_CTRL:system lib:bss_file.c:404:
[root@test CA]# touch /etc/pki/CA/index.txt
[root@test CA]# openssl ca -in app.csr -out /etc/pki/CA/certs/app.crt -days 365
Using configuration from /etc/pki/tls/openssl.cnf
/etc/pki/CA/serial: No such file or directory
error while loading serial number
140572255938448:error:02001002:system library:fopen:No such file or directory:bss_file.c:402:fopen('/etc/pki/CA/serial','r')
140572255938448:error:20074002:BIO routines:FILE_CTRL:system lib:bss_file.c:404:
[root@test CA]# echo 00 > /etc/pki/CA/serial
[root@test CA]# openssl ca -in app.csr -out /etc/pki/CA/certs/app.crt -days 365
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 0 (0x0)
Validity
Not Before: Jan 29 11:06:08 2020 GMT
Not After : Jan 28 11:06:08 2021 GMT
Subject:
countryName = CN
stateOrProvinceName = SICHUAN
organizationName = TEST
organizationalUnitName = DEVOPS
commonName = www.test.org
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
AE:E9:31:DE:B1:86:4F:68:AB:D7:BB:E3:1B:74:AD:7A:44:D2:60:BB
X509v3 Authority Key Identifier:
keyid:43:FD:2D:72:E5:40:BF:3A:0E:03:5D:D2:0F:6C:7C:5B:D0:6B:C7:41
Certificate is to be certified until Jan 28 11:06:08 2021 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[root@test CA]# tree
.
├── app.crs
├── cacert.pem
├── certs
│ └── app.crt
├── crl
├── index.txt
├── index.txt.attr
├── index.txt.old
├── newcerts
│ └── 00.pem
├── private
│ └── cakey.pem
├── serial
└── serial.old
4 directories, 10 files
[root@test CA]#
说明:在跟客户端颁发证书的时候需要依赖两个文件/etc/pki/CA/index.txt和/etc/pki/CA/serial,前者文件主要存放已经颁发的证书信息,后者存放下一个将要颁发的证书的序列号。这里说一下/etc/pki/CA下的各个文件和目录的作用吧,certs目录存放颁发证书的目录,crl存放吊销证书列表文件的目录,index.txt.attr存放证书subject信息是否唯一的配置信息,index.txt.old存放上一次颁发证书的信息,newcerts目录存放已经颁发的证书,并且以序列号命名的证书,每颁发一次证书,在我们指定的路径下生成指定名称的证书后,newcerts目录下会自动生成一个以序列号为名称的证书,这个证书同我们指定路径下存放的证书信息一模一样。private目录存放私钥文件。serial.old存放上一次颁发证书的序列号。
4.4、查看颁发证书的信息
Windows上查看
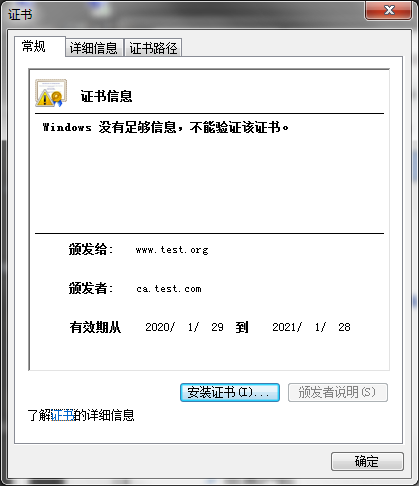
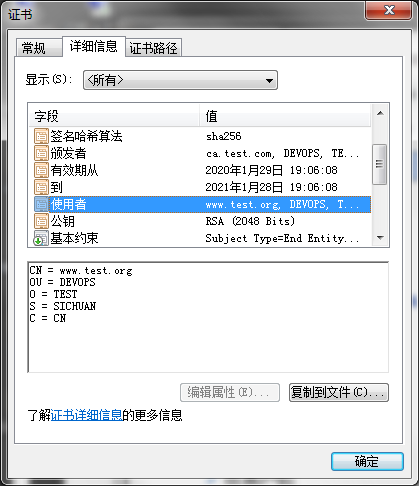

Linux上查看
[root@test CA]# openssl x509 -in certs/app.crt -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 0 (0x0)
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=CN, ST=SICHUAN, L=GUANGYUAN, O=TEST, OU=DEVOPS, CN=ca.test.com
Validity
Not Before: Jan 29 11:06:08 2020 GMT
Not After : Jan 28 11:06:08 2021 GMT
Subject: C=CN, ST=SICHUAN, O=TEST, OU=DEVOPS, CN=www.test.org
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:e9:7b:52:73:1c:b1:80:8e:e0:0b:ed:71:61:01:
52:5c:81:7d:46:a0:93:01:9e:16:a5:61:90:63:3b:
37:d1:72:d3:d5:cc:65:fe:12:7c:31:cc:4c:43:5d:
fb:1f:58:3e:3d:e1:05:6c:d5:77:a3:20:63:12:dd:
df:78:27:24:e6:c6:fd:4c:fe:2d:b0:88:53:e8:bb:
77:66:de:8f:22:a3:9f:0d:9f:24:3b:15:83:26:9f:
c3:35:71:f0:b8:2f:0c:13:f9:9f:bf:70:a5:78:96:
cb:e4:29:72:6f:da:2f:61:e6:64:11:03:ca:f5:38:
06:ee:90:87:53:40:31:4f:0d:2b:ec:42:cf:03:6f:
54:81:df:e5:14:64:0d:4c:9b:77:f4:a9:b2:ee:e0:
4e:3e:12:84:43:e7:c7:55:a3:2a:b6:6c:b5:ab:f4:
a9:9c:cf:76:bc:6b:d1:e3:4c:51:82:5f:87:27:5e:
c0:d0:00:80:12:36:df:df:02:be:aa:84:3f:58:10:
82:a4:c9:1e:4c:ba:05:12:7f:d2:6b:b4:a6:65:9b:
76:17:49:36:71:3c:b1:4b:35:4a:69:d3:d0:52:5a:
e9:59:51:db:cd:7e:08:0c:8f:ec:b1:2f:70:7a:20:
ec:2c:be:5e:49:c8:ff:09:65:91:16:12:ae:ef:3f:
7c:61
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
AE:E9:31:DE:B1:86:4F:68:AB:D7:BB:E3:1B:74:AD:7A:44:D2:60:BB
X509v3 Authority Key Identifier:
keyid:43:FD:2D:72:E5:40:BF:3A:0E:03:5D:D2:0F:6C:7C:5B:D0:6B:C7:41
Signature Algorithm: sha256WithRSAEncryption
46:94:4f:ab:6f:43:43:fb:0d:d1:e2:71:ff:5d:5b:0e:39:59:
c2:3f:92:47:88:84:2f:80:e4:00:a1:94:86:9a:bc:19:bb:22:
22:e1:2f:93:d1:1b:19:92:5f:de:46:47:30:e4:f5:b7:d8:b4:
e7:62:37:9c:17:cc:e7:8c:f4:b7:8a:cc:09:62:fd:6f:56:e3:
a3:22:1d:d8:01:e2:34:87:45:86:04:be:c7:91:b4:e9:49:f6:
39:c9:c4:67:6a:f7:8b:96:09:2f:d3:d4:a4:e5:a3:f0:d9:1d:
e6:dc:28:65:da:70:27:9b:70:5a:6a:a5:5a:77:c3:51:e0:54:
b0:7f:e4:a1:9a:4c:b5:d2:82:84:d9:3f:c8:57:dd:25:0a:80:
81:61:c6:a4:d1:5b:19:21:5d:19:1e:7d:b4:4f:a2:54:f4:bf:
f9:d0:2e:ba:4a:94:f1:93:be:54:cc:3b:19:7a:ae:fd:bd:4a:
b5:e3:55:a3:2a:a0:69:0e:08:78:9d:91:d5:df:02:bd:ec:c9:
cc:d2:6e:68:bf:48:3c:73:df:e9:62:92:8f:6c:9d:2f:2c:32:
85:46:a7:30:22:22:9c:2d:af:d0:cf:02:e0:21:3b:1d:6a:a3:
f7:81:0b:63:10:8c:f1:30:4a:05:08:4b:52:ad:4a:1d:14:9c:
0c:64:2b:71
[root@test CA]#
到此私有CA服务器的搭建、证书的申请和颁发就完成了,后续使用证书,就需要把证书放到对应的应用目录,配置其应用服务来使用其证书即可。通常申请证书不用在客户端申请,在服务端创建私钥,创建申请证书文件,然后签发证书,生成证书文件,然后把私钥和证书发给客户端即可。
5、吊销证书
[root@test CA]# openssl x509 -in certs/app.crt -noout -serial -subject serial=00 subject= /C=CN/ST=SICHUAN/O=TEST/OU=DEVOPS/CN=www.test.org [root@test CA]#
说明:以上命令是对要吊销的证书获取其序列号和subject信息,这个操作一般是客户端上查看,然后把信息发送给CA
[root@test CA]# openssl ca -revoke /etc/pki/CA/newcerts/00.pem Using configuration from /etc/pki/tls/openssl.cnf Revoking Certificate 00. Data Base Updated [root@test CA]#
说明:在CA上,根据客户端提交的serial与subject信息,对比检验是否与index.txt文件的信息一致,然后在进行吊销证书操作
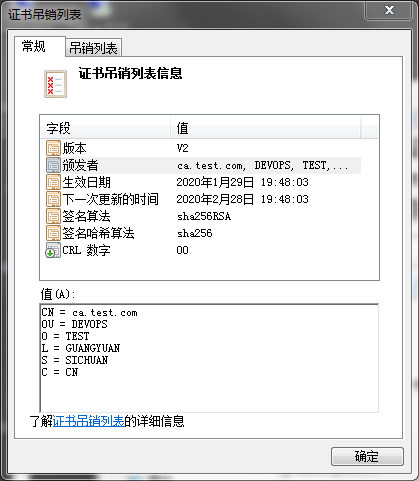
6、更新证书吊销列表crl文件
[root@test CA]# openssl ca -gencrl -out /etc/pki/CA/crl.pem
Using configuration from /etc/pki/tls/openssl.cnf
/etc/pki/CA/crlnumber: No such file or directory
error while loading CRL number
140437997475728:error:02001002:system library:fopen:No such file or directory:bss_file.c:402:fopen('/etc/pki/CA/crlnumber','r')
140437997475728:error:20074002:BIO routines:FILE_CTRL:system lib:bss_file.c:404:
[root@test CA]# echo 00 > /etc/pki/CA/crlnumber
[root@test CA]# openssl ca -gencrl -out /etc/pki/CA/crl.pem
Using configuration from /etc/pki/tls/openssl.cnf
[root@test CA]#
说明:第一次更新证书吊销列表,它会提示我们说缺少crlnumber文件,这个文件同serial的作用类似,都是存放的是版本号,我们需要创建其文件,并写一个16进制的编号,通常是从00或者01开始。(这个文件同serial一样都会自动增长,一般后续不需要怎么维护它)
[root@test CA]# openssl crl -in /etc/pki/CA/crl.pem -noout -text
Certificate Revocation List (CRL):
Version 2 (0x1)
Signature Algorithm: sha256WithRSAEncryption
Issuer: /C=CN/ST=SICHUAN/L=GUANGYUAN/O=TEST/OU=DEVOPS/CN=ca.test.com
Last Update: Jan 29 11:48:03 2020 GMT
Next Update: Feb 28 11:48:03 2020 GMT
CRL extensions:
X509v3 CRL Number:
0
Revoked Certificates:
Serial Number: 00
Revocation Date: Jan 29 11:41:28 2020 GMT
Signature Algorithm: sha256WithRSAEncryption
87:12:f8:b2:ec:b7:77:94:4b:bc:e4:ea:69:03:27:78:d3:b5:
43:8d:45:c5:a4:50:53:d7:3b:81:48:a1:cf:5d:43:4e:13:01:
91:5e:a2:f2:87:44:87:84:16:b2:1d:0e:28:81:88:d4:1a:c2:
a4:55:22:9f:d0:b9:6b:3c:80:e2:6e:98:fb:c3:18:3e:d3:a0:
49:a3:0e:19:64:2f:03:51:4b:ec:32:1c:c8:41:62:46:e8:4f:
8c:ec:a2:07:1c:fc:4b:20:61:ca:04:0e:31:8b:b9:4e:ce:42:
81:66:d6:09:3e:1e:15:44:76:33:27:07:fd:17:10:6d:d0:12:
cf:4f:ce:cb:3d:b4:6d:68:f1:5a:1a:4f:44:a6:65:cd:f6:3b:
4e:2e:3f:6d:2a:f8:d5:8a:52:5a:b0:8d:b1:8f:73:08:50:9c:
89:d3:c0:97:0e:13:89:37:cc:13:ad:d9:db:61:06:6d:4f:0a:
6b:58:a0:53:0a:2b:e8:23:18:cd:3b:0c:5d:9e:77:c3:85:3e:
e3:3c:ab:ad:45:9e:3c:18:7a:85:b0:51:7e:4d:8e:c6:18:e7:
fc:4d:f1:01:ac:b3:89:2c:eb:f7:0e:f9:3c:ea:5a:42:ff:43:
6b:98:9f:a0:89:59:28:92:c9:ed:d3:59:87:ca:04:8c:8c:92:
c0:a1:72:8a
[root@test CA]# cat /etc/pki/CA/index.txt
R 210128110608Z 200129114128Z 00 unknown /C=CN/ST=SICHUAN/O=TEST/OU=DEVOPS/CN=www.test.org
[root@test CA]# cat /etc/pki/CA/crlnumber
01
[root@test CA]#
说明:证书吊销后其index.txt里的信息会发生变化,R表示该证书已经被吊销,V表示该证书未吊销。
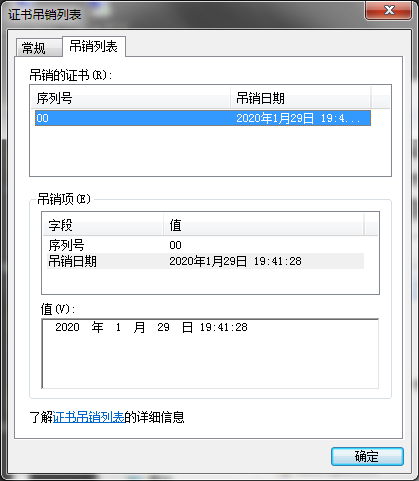
在windows上查看证书吊销列表crl文件