1.修改用户复杂度的2个文件
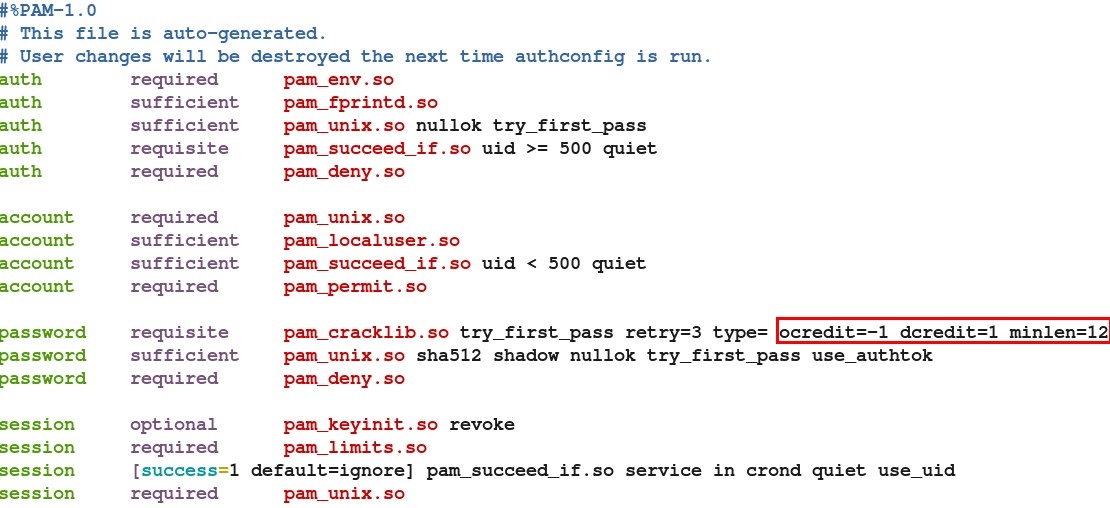

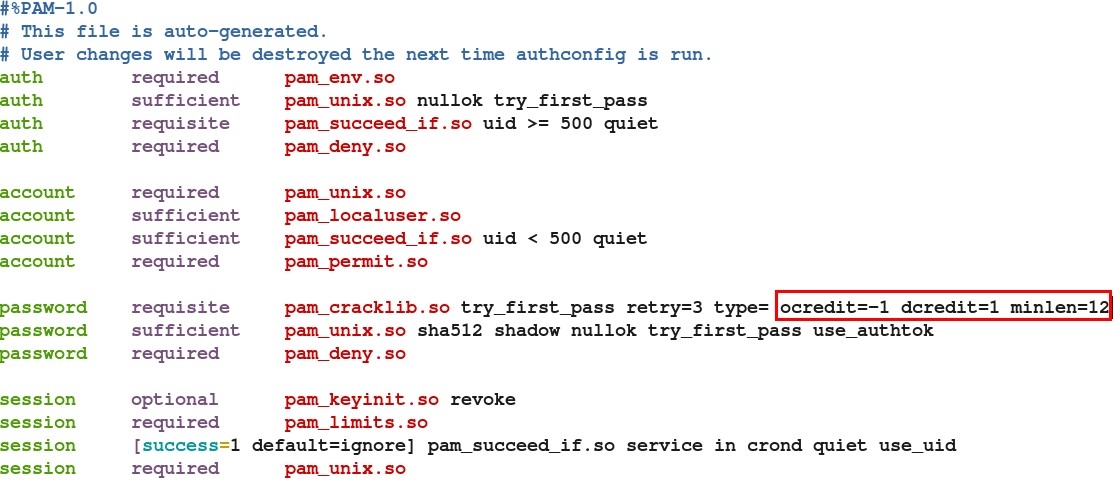
PAM服务文件
1、# more /etc/pam.d/login
auth required pam_securetty.so
auth required pam_stack.so service=system-auth
auth required pam_nologin.so
account required pam_stack.so service=system-auth
password required pam_stack.so service=system-auth
session required pam_stack.so service=system-auth
session optional pam_console.so
PAM服务文件的格式(四部分)
| Module-type |
control-flag |
module-path |
arguments |
Module-type: auth、account、session、password
Control-flag:required、requisite、sufficient、optional
eg:
| auth |
required |
pam_securety.so |
| auth |
required |
pam_stack.so service=system_auth |
Module-type(属于认证里面的第一部分,主要是分配权限)
auth:认证、授权(检查用户的名字、密码正确与否);
account:检查用户的帐户是否到期、禁用等。
session:控制会话
password:控制用户修改密码过程
Control-flag (属于认证里面的第二部分,控制标识位)
required:必须通过此认证,否则不再往下认证下去,直接退出;
requisite:必须通过认证,但以后还有机会,可以往下认证;
sufficient:一经通过,后面的不再认证(只要通过这个条件则直接通过);
optional:可选的,通不通过均可。
常用的PAM服务文件
1)、login ---- /etc/pam.d/login 2)、ipop3d --- /etc/pam.d/pop
3)、ftp ---- /etc/pam.d/ftp 或 vsftpd -- /etc/pam.d/vsftpd
4)、sshd--- /etc/pam.d/sshd 5)、su --- /etc/pam.d/su 6)、imap--- /etc/pam.d/imcp
认证堆栈
①、auth required pam_securety.so
②、auth required pam_stack.so service=system-auth
③、auth required pam_nologin.so
如果①号认证结束,则在后面有个结束标志,转到下一个认证即②号认证,依次类推,相同类型的认证会放在一起进行。
其中pam_stack.so调用一个子模块服务,通过这个服务再调用一个第三方的模块进行认证授权。
常用PAM模块
1)、pam_access.so 控制访问者的地址与帐号的名称
2)、pam_listfile.so 控制访问者的帐号名称或登陆位置
3)、pam_limits.so 控制为用户分配的资源
4)、pam_rootok.so 对管理员(uid=0)无条件通过
5)、pam_userdb.so 设定独立用户帐号数据库认证
如下:
[root@localhost root]# cd /etc/pam.d/
[root@localhost pam.d]# more login
#%PAM-1.0
auth required pam_securetty.so
auth required pam_stack.so service=system-auth
auth required pam_nologin.so
account required pam_stack.so service=system-auth
password required pam_stack.so service=system-auth
session required pam_stack.so service=system-auth
session optional pam_console.so
[root@localhost pam.d]# cd /usr/share/doc/pam-0.75/txts/
[root@localhost txts]# ls
pam_appl.txt README.pam_ftp README.pam_shells
pam_modules.txt README.pam_limits README.pam_stack
pam.txt README.pam_listfile README.pam_stress
README README.pam_localuser README.pam_tally
README.pam_access README.pam_mail README.pam_time
README.pam_chroot README.pam_nologin README.pam_timestamp
README.pam_console README.pam_permit README.pam_unix
README.pam_cracklib README.pam_pwdb README.pam_userdb
README.pam_deny README.pam_rhosts README.pam_warn
README.pam_env README.pam_rootok README.pam_wheel
README.pam_filter README.pam_securetty README.pam_xauth
[root@localhost txts]# more README.pam_securetty
pam_securetty:
Allows root logins only if the user is logging in on a
"secure" tty, as defined by the listing in /etc/securetty
Also checks to make sure that /etc/securetty is a plain
file and not world writable.
- Elliot Lee , Red Hat Software.
July 25, 1996.
[root@localhost txts]# more /etc/securetty
console
vc/1
vc/2
vc/3
vc/4
vc/5
vc/6
vc/7
vc/8
vc/9
vc/10
vc/11
tty1
tty2
tty3
tty4
tty5
tty6
tty7
tty8
tty9
tty10
tty11
[root@localhost txts]# more /etc/pam.d/system-auth
#%PAM-1.0
# This file is auto-generated.
# User changes will be destroyed the next time authconfig is run.
auth required /lib/security/$ISA/pam_env.so
auth sufficient /lib/security/$ISA/pam_unix.so likeauth nullok
auth required /lib/security/$ISA/pam_deny.so
account required /lib/security/$ISA/pam_unix.so
password required /lib/security/$ISA/pam_cracklib.so retry=3 type=
password sufficient /lib/security/$ISA/pam_unix.so nullok use_authtok md5 shadow
password required /lib/security/$ISA/pam_deny.so
session required /lib/security/$ISA/pam_limits.so
session required /lib/security/$ISA/pam_unix.so
[root@localhost txts]# pwd
/usr/share/doc/pam-0.75/txts
[root@localhost txts]# more README.pam_nologin
# $Id: README,v 1.1.1.1 2000/06/20 22:11:46 agmorgan Exp $
#
This module always lets root in; it lets other users in only if the file
/etc/nologin doesn't exist. In any case, if /etc/nologin exists, it's
contents are displayed to the user.
module services provided:
auth _authentication and _setcred (blank)
Michael K. Johnson
[root@localhost txts]# touch /etc/nologin
[root@localhost txts]# useradd leekwen
[root@localhost txts]# passwd leekwen
Changing password for user leekwen.
New password:
Retype new password:
passwd: all authentication tokens updated successfully.
[root@localhost txts]# ssh leekwen@192.168.0.188
leekwen@192.168.0.188's password:
Permission denied, please try again.
leekwen@192.168.0.188's password:
Permission denied, please try again.
leekwen@192.168.0.188's password:
Permission denied (publickey,password,keyboard-interactive).
[root@localhost txts]# rm /etc/nologin
rm: remove regular empty file `/etc/nologin'? y
[root@localhost txts]# ssh leekwen@192.168.0.188
leekwen@192.168.0.188's password:
[leekwen@localhost leekwen]$ pwd
/home/leekwen
[leekwen@localhost leekwen]$ exit
logout
Connection to 192.168.0.188 closed.
[root@localhost txts]# cd /etc/pam.d/
[root@localhost pam.d]# more login
#%PAM-1.0
auth required pam_securetty.so
auth required pam_stack.so service=system-auth
auth required pam_nologin.so
account required pam_stack.so service=system-auth
password required pam_stack.so service=system-auth
session required pam_stack.so service=system-auth
session optional pam_console.so
[root@localhost pam.d]# tty
/dev/pts/2
[root@localhost pam.d]# ls /dev/tty1
/dev/tty1