Linux 如何打开端口 - lclc - 博客园 https://www.cnblogs.com/lcword/p/5869522.html
linux如何查看端口相关信息_百度经验 https://jingyan.baidu.com/article/fdbd4277fba4dab89e3f48ab.html
[root@bigdata-server-01 sysconfig]# find / | grep iptables
/usr/sbin/iptables-restore
/usr/sbin/iptables
/usr/sbin/iptables-save
/usr/share/doc/iptables-1.4.21
/usr/share/doc/iptables-1.4.21/COPYING
/usr/share/doc/iptables-1.4.21/INCOMPATIBILITIES
/usr/share/man/man1/iptables-xml.1.gz
/usr/share/man/man8/iptables.8.gz
/usr/share/man/man8/iptables-extensions.8.gz
/usr/share/man/man8/iptables-restore.8.gz
/usr/share/man/man8/iptables-save.8.gz
/usr/share/mime/text/x-iptables.xml
/usr/bin/iptables-xml
/etc/sysconfig/iptables-config
/etc/selinux/targeted/active/modules/100/iptables
/etc/selinux/targeted/active/modules/100/iptables/hll
/etc/selinux/targeted/active/modules/100/iptables/cil
/etc/selinux/targeted/active/modules/100/iptables/lang_ext
/var/lib/yum/yumdb/i/b65e29d0ee30309c2cf4ba3ab0cce299f698651c-iptables-1.4.21-18.2.el7_4-x86_64
/var/lib/yum/yumdb/i/b65e29d0ee30309c2cf4ba3ab0cce299f698651c-iptables-1.4.21-18.2.el7_4-x86_64/from_repo
/var/lib/yum/yumdb/i/b65e29d0ee30309c2cf4ba3ab0cce299f698651c-iptables-1.4.21-18.2.el7_4-x86_64/checksum_data
/var/lib/yum/yumdb/i/b65e29d0ee30309c2cf4ba3ab0cce299f698651c-iptables-1.4.21-18.2.el7_4-x86_64/origin_url
/var/lib/yum/yumdb/i/b65e29d0ee30309c2cf4ba3ab0cce299f698651c-iptables-1.4.21-18.2.el7_4-x86_64/var_uuid
/var/lib/yum/yumdb/i/b65e29d0ee30309c2cf4ba3ab0cce299f698651c-iptables-1.4.21-18.2.el7_4-x86_64/changed_by
/var/lib/yum/yumdb/i/b65e29d0ee30309c2cf4ba3ab0cce299f698651c-iptables-1.4.21-18.2.el7_4-x86_64/var_infra
/var/lib/yum/yumdb/i/b65e29d0ee30309c2cf4ba3ab0cce299f698651c-iptables-1.4.21-18.2.el7_4-x86_64/from_repo_revision
/var/lib/yum/yumdb/i/b65e29d0ee30309c2cf4ba3ab0cce299f698651c-iptables-1.4.21-18.2.el7_4-x86_64/checksum_type
/var/lib/yum/yumdb/i/b65e29d0ee30309c2cf4ba3ab0cce299f698651c-iptables-1.4.21-18.2.el7_4-x86_64/reason
/var/lib/yum/yumdb/i/b65e29d0ee30309c2cf4ba3ab0cce299f698651c-iptables-1.4.21-18.2.el7_4-x86_64/command_line
/var/lib/yum/yumdb/i/b65e29d0ee30309c2cf4ba3ab0cce299f698651c-iptables-1.4.21-18.2.el7_4-x86_64/from_repo_timestamp
/var/lib/yum/yumdb/i/b65e29d0ee30309c2cf4ba3ab0cce299f698651c-iptables-1.4.21-18.2.el7_4-x86_64/installed_by
/var/lib/yum/yumdb/i/b65e29d0ee30309c2cf4ba3ab0cce299f698651c-iptables-1.4.21-18.2.el7_4-x86_64/releasever
[root@bigdata-server-01 sysconfig]#
service iptables start/stop
安装
解决CentOS7关闭/开启防火墙出现Unit iptables.service failed to load: No such file or directory. - CSDN博客 http://blog.csdn.net/c233728461/article/details/52679558
# yum install iptables
[root@bigdata-server-01 sysconfig]# systemctl enable iptables
Created symlink from /etc/systemd/system/basic.target.wants/iptables.service to /usr/lib/systemd/system/iptables.service.
[root@bigdata-server-01 sysconfig]# vim /etc/sysconfig/iptables
# sample configuration for iptables service
# you can edit this manually or use system-config-firewall
# please do not ask us to add additional ports/services to this default configuration
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -p icmp -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT
-A INPUT -j REJECT --reject-with icmp-host-prohibited
-A FORWARD -j REJECT --reject-with icmp-host-prohibited
COMMIT
:set nu
: 11,11 copy 11
复制已有的22端口行,改为5000,为flask准备
重启
iptables
systemctl restart iptables
[root@hadoop3 ~]# find / | grep iptables
/home/data/xl_tmp/C/Users/Administrator.PC-201707311140/Desktop/desk/manual-master.tar/html/tutorial/configure-linux-iptables-firewall.html
/home/data/xl_tmp/C/Users/Administrator.PC-201707311140/Desktop/manual-master.tar/html/tutorial/configure-linux-iptables-firewall.html
/etc/sysconfig/iptables-config
/etc/sysconfig/iptables
/etc/selinux/targeted/modules/active/modules/iptables.pp
/var/lib/yum/yumdb/i/fb1ea5f54bb511b515a25d6b6de76a796fcf68b2-iptables-1.4.21-16.el7-x86_64
/var/lib/yum/yumdb/i/fb1ea5f54bb511b515a25d6b6de76a796fcf68b2-iptables-1.4.21-16.el7-x86_64/from_repo
/var/lib/yum/yumdb/i/fb1ea5f54bb511b515a25d6b6de76a796fcf68b2-iptables-1.4.21-16.el7-x86_64/reason
/var/lib/yum/yumdb/i/fb1ea5f54bb511b515a25d6b6de76a796fcf68b2-iptables-1.4.21-16.el7-x86_64/releasever
/var/lib/yum/yumdb/i/fb1ea5f54bb511b515a25d6b6de76a796fcf68b2-iptables-1.4.21-16.el7-x86_64/var_uuid
/var/lib/yum/yumdb/i/fb1ea5f54bb511b515a25d6b6de76a796fcf68b2-iptables-1.4.21-16.el7-x86_64/checksum_type
/var/lib/yum/yumdb/i/fb1ea5f54bb511b515a25d6b6de76a796fcf68b2-iptables-1.4.21-16.el7-x86_64/checksum_data
/var/lib/yum/yumdb/i/fb1ea5f54bb511b515a25d6b6de76a796fcf68b2-iptables-1.4.21-16.el7-x86_64/from_repo_revision
/var/lib/yum/yumdb/i/fb1ea5f54bb511b515a25d6b6de76a796fcf68b2-iptables-1.4.21-16.el7-x86_64/from_repo_timestamp
/var/lib/yum/yumdb/i/fb1ea5f54bb511b515a25d6b6de76a796fcf68b2-iptables-1.4.21-16.el7-x86_64/installed_by
/usr/bin/iptables-xml
/usr/sbin/iptables
/usr/sbin/iptables-restore
/usr/sbin/iptables-save
/usr/share/doc/iptables-1.4.21
/usr/share/doc/iptables-1.4.21/COPYING
/usr/share/doc/iptables-1.4.21/INCOMPATIBILITIES
/usr/share/man/man1/iptables-xml.1.gz
/usr/share/man/man8/iptables-extensions.8.gz
/usr/share/man/man8/iptables-restore.8.gz
/usr/share/man/man8/iptables-save.8.gz
/usr/share/man/man8/iptables.8.gz
/usr/share/mime/text/x-iptables.xml
[root@hadoop3 ~]#
https://www.howtogeek.com/177621/the-beginners-guide-to-iptables-the-linux-firewall/
iptables is a command-line firewall utility that uses policy chains to allow or block traffic. When a connection tries to establish itself on your system, iptables looks for a rule in its list to match it to. If it doesn’t find one, it resorts to the default action.
iptables almost always comes pre-installed on any Linux distribution. To update/install it, just retrieve the iptables package:
There are GUI alternatives to iptables like Firestarter, but iptables isn’t really that hard once you have a few commands down. You want to be extremely careful when configuring iptables rules, particularly if you’re SSH’d into a server, because one wrong command can permanently lock you out until it’s manually fixed at the physical machine.
Types of Chains
iptables uses three different chains: input, forward, and output.
Input – This chain is used to control the behavior for incoming connections. For example, if a user attempts to SSH into your PC/server, iptables will attempt to match the IP address and port to a rule in the input chain.
Forward – This chain is used for incoming connections that aren’t actually being delivered locally. Think of a router – data is always being sent to it but rarely actually destined for the router itself; the data is just forwarded to its target. Unless you’re doing some kind of routing, NATing, or something else on your system that requires forwarding, you won’t even use this chain.
There’s one sure-fire way to check whether or not your system uses/needs the forward chain.
[root@hadoop3 ~]# /usr/sbin/iptables -h
iptables v1.4.21
Usage: iptables -[ACD] chain rule-specification [options]
iptables -I chain [rulenum] rule-specification [options]
iptables -R chain rulenum rule-specification [options]
iptables -D chain rulenum [options]
iptables -[LS] [chain [rulenum]] [options]
iptables -[FZ] [chain] [options]
iptables -[NX] chain
iptables -E old-chain-name new-chain-name
iptables -P chain target [options]
iptables -h (print this help information)
Commands:
Either long or short options are allowed.
--append -A chain Append to chain
--check -C chain Check for the existence of a rule
--delete -D chain Delete matching rule from chain
--delete -D chain rulenum
Delete rule rulenum (1 = first) from chain
--insert -I chain [rulenum]
Insert in chain as rulenum (default 1=first)
--replace -R chain rulenum
Replace rule rulenum (1 = first) in chain
--list -L [chain [rulenum]]
List the rules in a chain or all chains
--list-rules -S [chain [rulenum]]
Print the rules in a chain or all chains
--flush -F [chain] Delete all rules in chain or all chains
--zero -Z [chain [rulenum]]
Zero counters in chain or all chains
--new -N chain Create a new user-defined chain
--delete-chain
-X [chain] Delete a user-defined chain
--policy -P chain target
Change policy on chain to target
--rename-chain
-E old-chain new-chain
Change chain name, (moving any references)
Options:
--ipv4 -4 Nothing (line is ignored by ip6tables-restore)
--ipv6 -6 Error (line is ignored by iptables-restore)
[!] --protocol -p proto protocol: by number or name, eg. `tcp'
[!] --source -s address[/mask][...]
source specification
[!] --destination -d address[/mask][...]
destination specification
[!] --in-interface -i input name[+]
network interface name ([+] for wildcard)
--jump -j target
target for rule (may load target extension)
--goto -g chain
jump to chain with no return
--match -m match
extended match (may load extension)
--numeric -n numeric output of addresses and ports
[!] --out-interface -o output name[+]
network interface name ([+] for wildcard)
--table -t table table to manipulate (default: `filter')
--verbose -v verbose mode
--wait -w [seconds] wait for the xtables lock
--line-numbers print line numbers when listing
--exact -x expand numbers (display exact values)
[!] --fragment -f match second or further fragments only
--modprobe=<command> try to insert modules using this command
--set-counters PKTS BYTES set the counter during insert/append
[!] --version -V print package version.
[root@hadoop3 ~]#
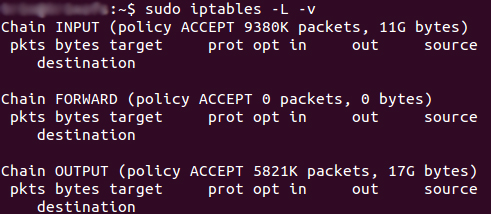
The screenshot above is of a server that’s been running for a few weeks and has no restrictions on incoming or outgoing connections. As you can see, the input chain has processed 11GB of packets and the output chain has processed 17GB. The forward chain, on the other hand, has not needed to process a single packet. This is because the server isn’t doing any kind of forwarding or being used as a pass-through device.
Output – This chain is used for outgoing connections. For example, if you try to ping howtogeek.com, iptables will check its output chain to see what the rules are regarding ping and howtogeek.com before making a decision to allow or deny the connection attempt.
The caveat
Even though pinging an external host seems like something that would only need to traverse the output chain, keep in mind that to return the data, the input chain will be used as well. When using iptables to lock down your system, remember that a lot of protocols will require two-way communication, so both the input and output chains will need to be configured properly. SSH is a common protocol that people forget to allow on both chains.
Policy Chain Default Behavior
Before going in and configuring specific rules, you’ll want to decide what you want the default behavior of the three chains to be. In other words, what do you want iptables to do if the connection doesn’t match any existing rules?
To see what your policy chains are currently configured to do with unmatched traffic, run the iptables -L command.
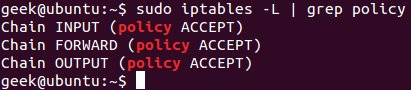
As you can see, we also used the grep command to give us cleaner output. In that screenshot, our chains are currently figured to accept traffic.
More times than not, you’ll want your system to accept connections by default. Unless you’ve changed the policy chain rules previously, this setting should already be configured. Either way, here’s the command to accept connections by default:
iptables --policy INPUT ACCEPTiptables --policy OUTPUT ACCEPTiptables --policy FORWARD ACCEPT
By defaulting to the accept rule, you can then use iptables to deny specific IP addresses or port numbers, while continuing to accept all other connections. We’ll get to those commands in a minute.
If you would rather deny all connections and manually specify which ones you want to allow to connect, you should change the default policy of your chains to drop. Doing this would probably only be useful for servers that contain sensitive information and only ever have the same IP addresses connect to them.
iptables --policy INPUT DROPiptables --policy OUTPUT DROPiptables --policy FORWARD DROP
Connection-specific Responses
With your default chain policies configured, you can start adding rules to iptables so it knows what to do when it encounters a connection from or to a particular IP address or port. In this guide, we’re going to go over the three most basic and commonly used “responses”.
Accept – Allow the connection.
Drop – Drop the connection, act like it never happened. This is best if you don’t want the source to realize your system exists.
Reject – Don’t allow the connection, but send back an error. This is best if you don’t want a particular source to connect to your system, but you want them to know that your firewall blocked them.
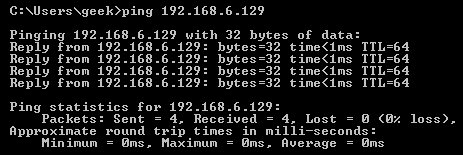
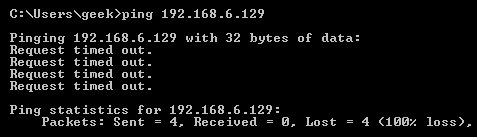
The best way to show the difference between these three rules is to show what it looks like when a PC tries to ping a Linux machine with iptables configured for each one of these settings.
Allowing the connection:
Dropping the connection:
Rejecting the connection:
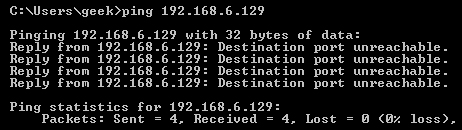
Allowing or Blocking Specific Connections
With your policy chains configured, you can now configure iptables to allow or block specific addresses, address ranges, and ports. In these examples, we’ll set the connections to DROP, but you can switch them to ACCEPT or REJECT, depending on your needs and how you configured your policy chains.
Note: In these examples, we’re going to use iptables -A to append rules to the existing chain. iptables starts at the top of its list and goes through each rule until it finds one that it matches. If you need to insert a rule above another, you can use iptables -I [chain] [number] to specify the number it should be in the list.
Connections from a single IP address
This example shows how to block all connections from the IP address 10.10.10.10.
iptables -A INPUT -s 10.10.10.10 -j DROP
Connections from a range of IP addresses
This example shows how to block all of the IP addresses in the 10.10.10.0/24 network range. You can use a netmask or standard slash notation to specify the range of IP addresses.
iptables -A INPUT -s 10.10.10.0/24 -j DROP
or
iptables -A INPUT -s 10.10.10.0/255.255.255.0 -j DROP
Connections to a specific port
This example shows how to block SSH connections from 10.10.10.10.
iptables -A INPUT -p tcp --dport ssh -s 10.10.10.10 -j DROP
You can replace “ssh” with any protocol or port number. The -p tcp part of the code tells iptables what kind of connection the protocol uses. If you were blocking a protocol that uses UDP rather than TCP, then -p udp would be necessary instead.
This example shows how to block SSH connections from any IP address.
iptables -A INPUT -p tcp --dport ssh -j DROP
Connection States
As we mentioned earlier, a lot of protocols are going to require two-way communication. For example, if you want to allow SSH connections to your system, the input and output chains are going to need a rule added to them. But, what if you only want SSH coming into your system to be allowed? Won’t adding a rule to the output chain also allow outgoing SSH attempts?
That’s where connection states come in, which give you the capability you’d need to allow two way communication but only allow one way connections to be established. Take a look at this example, where SSH connections FROM 10.10.10.10 are permitted, but SSH connections TO 10.10.10.10 are not. However, the system is permitted to send back information over SSH as long as the session has already been established, which makes SSH communication possible between these two hosts.
iptables -A INPUT -p tcp --dport ssh -s 10.10.10.10 -m state --state NEW,ESTABLISHED -j ACCEPT
iptables -A OUTPUT -p tcp --sport 22 -d 10.10.10.10 -m state --state ESTABLISHED -j ACCEPT
Saving Changes
The changes that you make to your iptables rules will be scrapped the next time that the iptables service gets restarted unless you execute a command to save the changes. This command can differ depending on your distribution:
Ubuntu:
sudo /sbin/iptables-save
Red Hat / CentOS:
/sbin/service iptables save
Or
/etc/init.d/iptables save
Other Commands
List the currently configured iptables rules:
iptables -L
Adding the -v option will give you packet and byte information, and adding -n will list everything numerically. In other words – hostnames, protocols, and networks are listed as numbers.
To clear all the currently configured rules, you can issue the flush command.
iptables -F
windows 打开关闭防火墙 对比
C:Userssas>ping 192.168.2.160
正在 Ping 192.168.2.160 具有 32 字节的数据:
请求超时。
请求超时。
请求超时。
请求超时。
192.168.2.160 的 Ping 统计信息:
数据包: 已发送 = 4,已接收 = 0,丢失 = 4 (100% 丢失),
C:Userssas>ping 192.168.2.160
正在 Ping 192.168.2.160 具有 32 字节的数据:
来自 192.168.2.160 的回复: 字节=32 时间=1ms TTL=128
来自 192.168.2.160 的回复: 字节=32 时间<1ms TTL=128
来自 192.168.2.160 的回复: 字节=32 时间<1ms TTL=128
来自 192.168.2.160 的回复: 字节=32 时间<1ms TTL=128
192.168.2.160 的 Ping 统计信息:
数据包: 已发送 = 4,已接收 = 4,丢失 = 0 (0% 丢失),
往返行程的估计时间(以毫秒为单位):
最短 = 0ms,最长 = 1ms,平均 = 0ms
防火墙已经关闭
但是仍然
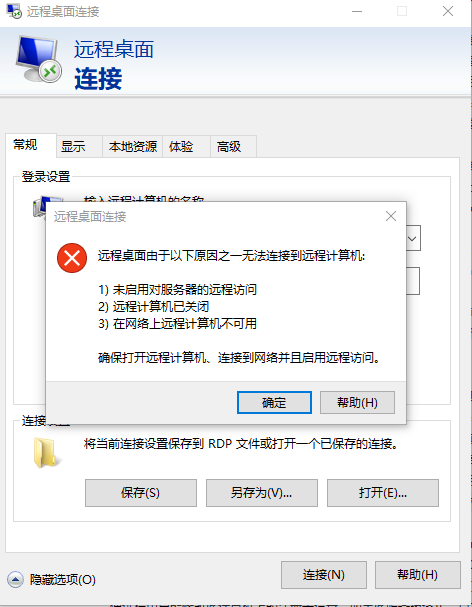
逐条检查
启用对远程服务器的访问
https://jingyan.baidu.com/album/8065f87f816f5323312498a1.html?picindex=5
注册表检查
打开注册表
C:Windows egedit.exe
计算机HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlTerminal Server
AllowRemoteRPC 设为1 允许
计算机HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlTerminal ServerWinStationsRDP-Tcp
检测端口是否被占用 netstat -at
设置3389为远程连接端口
PortNumber d3d 16进制 3389 =13+3*16+13*256 = 3328+61
SELinux_百度百科 https://baike.baidu.com/item/SELinux/8865268?fr=aladdin
【进程只能访问那些在他的任务中所需要文件】
systemctl stop firewalld.service
systemctl disable firewalld.service
Linux 如何开放端口和关闭端口
一、查看哪些端口被打开 netstat -anp
二、关闭端口号:
iptables -A OUTPUT -p tcp --dport 端口号-j DROP
1
三、打开端口号:
iptables -A INPUT -ptcp --dport 端口号-j ACCEPT
1
四、保存设置
service iptables save
1
五、以下是linux打开端口命令的使用方法。
nc -lp 23 &(打开23端口,即telnet)
netstat -an | grep 23 (查看是否打开23端口)
六、linux打开端口命令每一个打开的端口,都需要有相应的监听程序才可以
Centos防火墙设置与端口开放的方法
https://www.jianshu.com/p/3930b998ac2e
Centos升级到7之后,内置的防火墙已经从iptables变成了firewalld。所以,端口的开启还是要从两种情况来说明的,即iptables和firewalld。更多关于CentOs防火墙的最新内容,请参考Redhat官网。
一、iptables
1.打开/关闭/重启防火墙
开启防火墙(重启后永久生效):chkconfig iptables on
关闭防火墙(重启后永久生效):chkconfig iptables off
开启防火墙(即时生效,重启后失效):service iptables start
关闭防火墙(即时生效,重启后失效):service iptables stop
重启防火墙:service iptables restartd
2.查看打开的端口
/etc/init.d/iptables status
3.打开某个端口(以8080为例)
(1)开启端口
iptables -A INPUT -p tcp --dport 8080 -j ACCEPT
(2)保存并重启防火墙
/etc/rc.d/init.d/iptables save /etc/init.d/iptables restart
4.打开49152~65534之间的端口
iptables -A INPUT -p tcp --dport 49152:65534 -j ACCEPT
同样,这里需要对设置进行保存,并重启防火墙。
5.其他打开方式
我们还可以通过修改/etc/sysconfig/iptables文件的方式开启端口,如下
vi /etc/sysconfig/iptables
然后在文件中增加一行
-A RH-Firewall-1-INPUT -m state –state NEW -m tcp -p tcp –dport 8080 -j ACCEPT
参数说明:
–A 参数就看成是添加一条规则
–p 指定是什么协议,我们常用的tcp 协议,当然也有udp,例如53端口的DNS
–dport 就是目标端口,当数据从外部进入服务器为目标端口
–sport 数据从服务器出去,则为数据源端口使用
–j 就是指定是 ACCEPT -接收 或者 DROP 不接收
二、firewalld
Centos7默认安装了firewalld,如果没有安装的话,可以使用 yum install firewalld firewalld-config进行安装。
1.启动防火墙
systemctl start firewalld
2.禁用防火墙
systemctl stop firewalld
3.设置开机启动
systemctl enable firewalld
4.停止并禁用开机启动
sytemctl disable firewalld
5.重启防火墙
firewall-cmd --reload
6.查看状态
systemctl status firewalld或者 firewall-cmd --state
7.查看版本
firewall-cmd --version
8.查看帮助
firewall-cmd --help
9.查看区域信息
firewall-cmd --get-active-zones
10.查看指定接口所属区域信息
firewall-cmd --get-zone-of-interface=eth0
11.拒绝所有包
firewall-cmd --panic-on
12.取消拒绝状态
firewall-cmd --panic-off
13.查看是否拒绝
firewall-cmd --query-panic
14.将接口添加到区域(默认接口都在public)
firewall-cmd --zone=public --add-interface=eth0(永久生效再加上 --permanent 然后reload防火墙)
15.设置默认接口区域
firewall-cmd --set-default-zone=public(立即生效,无需重启)
16.更新防火墙规则
firewall-cmd --reload或firewall-cmd --complete-reload(两者的区别就是第一个无需断开连接,就是firewalld特性之一动态 添加规则,第二个需要断开连接,类似重启服务)
17.查看指定区域所有打开的端口
firewall-cmd --zone=public --list-ports
18.在指定区域打开端口(记得重启防火墙)
firewall-cmd --zone=public --add-port=80/tcp(永久生效再加上 --permanent)
说明:
–zone 作用域
–add-port=8080/tcp 添加端口,格式为:端口/通讯协议
–permanent #永久生效,没有此参数重启后失效