背景信息:
Windows AD Version: Windows Server 2012 R2 zh-cn

计算机全名:hlm12r2n1.hlm.com
域:hlm.com
域控管理员:stone
普通用户:abc; bcd
普通组:hlmgroup,用户bcd在该组下
IP:10.0.0.6
Linux服务器:
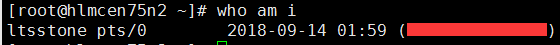
具有root权限的用户:ltsstone
操作步骤:
安装所需包文件:
yum install -y krb5-workstation realmd sssd samba-common adcli oddjob oddjob-mkhomedir samba samba-common-tools
编辑/etc/resolve.conf文件,将DNS指向DC
[root@hlmcen75n2 ~]# cat /etc/resolv.conf ; generated by /usr/sbin/dhclient-script search lqvi3agp2gsunp1mlkwv0vudne.ax.internal.chinacloudapp.cn nameserver 10.0.0.6
编辑/etc/hosts文件,添加DC的IP及域的对应关系
[root@hlmcen75n2 ~]# cat /etc/hosts 127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4 ::1 localhost localhost.localdomain localhost6 localhost6.localdomain6 10.0.0.6 hlm12r2n1.hlm.com
将Linux机器加入域
[root@hlmcen75n2 ~]# realm join hlm12r2n1.hlm.com -U stone Password for stone:
发现可以成功发现域了
[root@hlmcen75n2 ~]# realm list hlm.com type: kerberos realm-name: HLM.COM domain-name: hlm.com configured: kerberos-member server-software: active-directory client-software: sssd required-package: oddjob required-package: oddjob-mkhomedir required-package: sssd required-package: adcli required-package: samba-common-tools login-formats: %U@hlm.com login-policy: allow-permitted-logins permitted-logins: permitted-groups: hlmgroup@hlm.com
将组hlmgroup加入域
[root@hlmcen75n2 sudoers.d]# realm permit -g hlmgroup@hlm.com
可以看到用户stone,abc,bcd可以被成功发现
[root@hlmcen75n2 ~]# id stone@hlm.com uid=1744400500(stone) gid=1744400513(domain users) groups=1744400513(domain users),1744400520(group policy creator owners),1744400512(domain admins),1744400518(schema admins),1744400572(denied rodc password replication group),1744400519(enterprise admins) [root@hlmcen75n2 ~]# id abc@hlm.com uid=1744401605(abc) gid=1744400513(domain users) groups=1744400513(domain users) [root@hlmcen75n2 ~]# id bcd@hlm.com uid=1744401608(bcd) gid=1744400513(domain users) groups=1744400513(domain users),1744401602(hlmgroup)
为使用户不需用带域名就可以被识别,需要修改配置文件/etc/sssd/sssd.conf,将use_fully_qualified_names行的True值修改为False
[root@hlmcen75n2 ~]# cat /etc/sssd/sssd.conf [sssd] domains = hlm.com config_file_version = 2 services = nss, pam [domain/hlm.com] ad_server = hlm12r2n1.hlm.com ad_domain = hlm.com krb5_realm = HLM.COM realmd_tags = manages-system joined-with-adcli cache_credentials = True id_provider = ad krb5_store_password_if_offline = True default_shell = /bin/bash ldap_id_mapping = True use_fully_qualified_names = False fallback_homedir = /home/%u@%d access_provider = simple simple_allow_groups = hlmgroup@hlm.com
重启sssd服务,重新列出预控信息
[root@hlmcen75n2 ~]# systemctl restart sssd [root@hlmcen75n2 ~]# realm list hlm.com type: kerberos realm-name: HLM.COM domain-name: hlm.com configured: kerberos-member server-software: active-directory client-software: sssd required-package: oddjob required-package: oddjob-mkhomedir required-package: sssd required-package: adcli required-package: samba-common-tools login-formats: %U login-policy: allow-permitted-logins permitted-logins: permitted-groups: hlmgroup@hlm.com
发现不加域信息,Linux服务器也可以识别域用户
[root@hlmcen75n2 ~]# id stone uid=1744400500(stone) gid=1744400513(domain users) groups=1744400513(domain users),1744400520(group policy creator owners),1744400512(domain admins),1744400518(schema admins),1744400572(denied rodc password replication group),1744400519(enterprise admins) [root@hlmcen75n2 ~]# id abc uid=1744401605(abc) gid=1744400513(domain users) groups=1744400513(domain users) [root@hlmcen75n2 ~]# id bcd uid=1744401608(bcd) gid=1744400513(domain users) groups=1744400513(domain users),1744401602(hlmgroup)
尝试切换到域用户,发现无法进入root管理员权限,提示
[root@hlmcen75n2 ~]# su - abc Last login: Mon Sep 17 07:53:38 UTC 2018 on pts/0 [abc@hlmcen75n2 ~]$ sudo su - root We trust you have received the usual lecture from the local System Administrator. It usually boils down to these three things: #1) Respect the privacy of others. #2) Think before you type. #3) With great power comes great responsibility. [sudo] password for abc: abc is not in the sudoers file. This incident will be reported. [abc@hlmcen75n2 ~]$
编辑 /etc/sudoers.d/waagent 文件,将需要root权限的用户加入到其下
[root@hlmcen75n2 ~]# vim /etc/sudoers.d/waagent [root@hlmcen75n2 ~]# cat /etc/sudoers.d/waagent ltsstone ALL=(ALL) ALL abc ALL=(ALL) ALL
重新尝试切换root用户,发现已经可以
[root@hlmcen75n2 ~]# sudo su - abc Last login: Tue Sep 18 02:26:30 UTC 2018 on pts/0 [abc@hlmcen75n2 ~]$ sudo su - root [sudo] password for abc: Last login: Tue Sep 18 02:25:50 UTC 2018 on pts/0 [root@hlmcen75n2 ~]#
备注:
执行命令:realm join hlm12r2n1.hlm.com -U stone,messages日志发现加入域的认证过程如下:
Sep 17 09:16:53 hlmcen75n2 realmd: * Resolving: _ldap._tcp.hlm12r2n1.hlm.com Sep 17 09:16:53 hlmcen75n2 realmd: * Resolving: hlm12r2n1.hlm.com Sep 17 09:16:53 hlmcen75n2 realmd: * Performing LDAP DSE lookup on: 10.0.0.6 Sep 17 09:16:53 hlmcen75n2 realmd: * Successfully discovered: hlm.com Sep 17 09:16:58 hlmcen75n2 realmd: * Required files: /usr/sbin/oddjobd, /usr/libexec/oddjob/mkhomedir, /usr/sbin/sssd, /usr/sbin/adcli Sep 17 09:16:58 hlmcen75n2 realmd: * LANG=C /usr/sbin/adcli join --verbose --domain hlm.com --domain-realm HLM.COM --domain-controller 10.0.0.6 --login-type user --login-user stone --stdin-password Sep 17 09:16:58 hlmcen75n2 realmd: * Using domain name: hlm.com Sep 17 09:16:58 hlmcen75n2 realmd: * Calculated computer account name from fqdn: HLMCEN75N2 Sep 17 09:16:58 hlmcen75n2 realmd: * Using domain realm: hlm.com Sep 17 09:16:58 hlmcen75n2 realmd: * Sending netlogon pings to domain controller: cldap://10.0.0.6 Sep 17 09:16:58 hlmcen75n2 realmd: * Received NetLogon info from: hlm12r2n1.hlm.com Sep 17 09:16:58 hlmcen75n2 realmd: * Wrote out krb5.conf snippet to /var/cache/realmd/adcli-krb5-zqaVb2/krb5.d/adcli-krb5-conf-N3Soi1 Sep 17 09:16:58 hlmcen75n2 realmd: * Authenticated as user: stone@HLM.COM Sep 17 09:16:58 hlmcen75n2 realmd: * Looked up short domain name: HLM Sep 17 09:16:58 hlmcen75n2 realmd: * Using fully qualified name: hlmcen75n2 Sep 17 09:16:58 hlmcen75n2 realmd: * Using domain name: hlm.com Sep 17 09:16:58 hlmcen75n2 realmd: * Using computer account name: HLMCEN75N2 Sep 17 09:16:58 hlmcen75n2 realmd: * Using domain realm: hlm.com Sep 17 09:16:58 hlmcen75n2 realmd: * Calculated computer account name from fqdn: HLMCEN75N2 Sep 17 09:16:58 hlmcen75n2 realmd: * Generated 120 character computer password Sep 17 09:16:58 hlmcen75n2 realmd: * Using keytab: FILE:/etc/krb5.keytab Sep 17 09:16:58 hlmcen75n2 realmd: * Found computer account for HLMCEN75N2$ at: CN=HLMCEN75N2,CN=Computers,DC=hlm,DC=com Sep 17 09:16:58 hlmcen75n2 realmd: * Sending netlogon pings to domain controller: cldap://10.0.0.6 Sep 17 09:17:00 hlmcen75n2 realmd: * Received NetLogon info from: hlm12r2n1.hlm.com Sep 17 09:17:00 hlmcen75n2 realmd: * Set computer password Sep 17 09:17:00 hlmcen75n2 realmd: * Retrieved kvno '4' for computer account in directory: CN=HLMCEN75N2,CN=Computers,DC=hlm,DC=com Sep 17 09:17:00 hlmcen75n2 realmd: * Modifying computer account: userAccountControl Sep 17 09:17:00 hlmcen75n2 realmd: * Modifying computer account: operatingSystemVersion, operatingSystemServicePack Sep 17 09:17:00 hlmcen75n2 realmd: * Modifying computer account: userPrincipalName Sep 17 09:17:00 hlmcen75n2 realmd: ! Couldn't set service principals on computer account CN=HLMCEN75N2,CN=Computers,DC=hlm,DC=com: 00002083: AtrErr: DSID-03151337, #1: Sep 17 09:17:00 hlmcen75n2 realmd: #0110: 00002083: DSID-03151337, problem 1006 (ATT_OR_VALUE_EXISTS), data 0, Att 90303 (servicePrincipalName) Sep 17 09:17:00 hlmcen75n2 realmd: Sep 17 09:17:00 hlmcen75n2 realmd: * Discovered which keytab salt to use Sep 17 09:17:00 hlmcen75n2 realmd: * Added the entries to the keytab: HLMCEN75N2$@HLM.COM: FILE:/etc/krb5.keytab Sep 17 09:17:00 hlmcen75n2 realmd: * Added the entries to the keytab: host/HLMCEN75N2@HLM.COM: FILE:/etc/krb5.keytab Sep 17 09:17:01 hlmcen75n2 realmd: * Added the entries to the keytab: host/hlmcen75n2@HLM.COM: FILE:/etc/krb5.keytab Sep 17 09:17:01 hlmcen75n2 realmd: * Added the entries to the keytab: RestrictedKrbHost/HLMCEN75N2@HLM.COM: FILE:/etc/krb5.keytab Sep 17 09:17:01 hlmcen75n2 realmd: * Added the entries to the keytab: RestrictedKrbHost/hlmcen75n2@HLM.COM: FILE:/etc/krb5.keytab Sep 17 09:17:01 hlmcen75n2 realmd: * /usr/bin/systemctl enable sssd.service Sep 17 09:17:01 hlmcen75n2 realmd: Created symlink from /etc/systemd/system/multi-user.target.wants/sssd.service to /usr/lib/systemd/system/sssd.service. Sep 17 09:17:01 hlmcen75n2 systemd: Reloading. Sep 17 09:17:01 hlmcen75n2 realmd: * /usr/bin/systemctl restart sssd.service Sep 17 09:17:01 hlmcen75n2 systemd: Starting System Security Services Daemon... Sep 17 09:17:01 hlmcen75n2 sssd: Starting up Sep 17 09:17:01 hlmcen75n2 sssd[be[hlm.com]]: Starting up Sep 17 09:17:02 hlmcen75n2 sssd[nss]: Starting up Sep 17 09:17:02 hlmcen75n2 sssd[pam]: Starting up Sep 17 09:17:02 hlmcen75n2 systemd: Started System Security Services Daemon. Sep 17 09:17:02 hlmcen75n2 realmd: * /usr/bin/sh -c /usr/sbin/authconfig --update --enablesssd --enablesssdauth --enablemkhomedir --nostart && /usr/bin/systemctl enable oddjobd.service && /usr/bin/systemctl start oddjobd.service Sep 17 09:17:02 hlmcen75n2 systemd: Reloading. Sep 17 09:17:03 hlmcen75n2 systemd: Reloading. Sep 17 09:17:03 hlmcen75n2 realmd: * Successfully enrolled machine in realm
执行命令:realm list列出域的相关信息,messages日志发现相应的记录信息如下:
Sep 17 09:18:10 hlmcen75n2 dbus[531]: [system] Activating via systemd: service name='org.freedesktop.realmd' unit='realmd.service' Sep 17 09:18:10 hlmcen75n2 systemd: Starting Realm and Domain Configuration... Sep 17 09:18:10 hlmcen75n2 dbus[531]: [system] Successfully activated service 'org.freedesktop.realmd' Sep 17 09:18:10 hlmcen75n2 systemd: Started Realm and Domain Configuration.
执行命令:realm leave hlm.com,messages日志发现脱域的相关记录如下:
Sep 17 09:26:39 hlmcen75n2 python: 2018/09/17 09:26:39.018384 INFO Event: name=WALinuxAgent, op=HeartBeat, message=, duration=0 Sep 17 09:26:51 hlmcen75n2 realmd: * Removing entries from keytab for realm Sep 17 09:26:52 hlmcen75n2 realmd: * /usr/sbin/sss_cache --users --groups --netgroups --services --autofs-maps Sep 17 09:26:52 hlmcen75n2 realmd: * Removing domain configuration from sssd.conf Sep 17 09:26:52 hlmcen75n2 realmd: * /usr/sbin/authconfig --update --disablesssdauth --nostart Sep 17 09:26:53 hlmcen75n2 systemd: Reloading. Sep 17 09:26:53 hlmcen75n2 realmd: * /usr/bin/systemctl disable sssd.service Sep 17 09:26:53 hlmcen75n2 realmd: Removed symlink /etc/systemd/system/multi-user.target.wants/sssd.service. Sep 17 09:26:53 hlmcen75n2 systemd: Reloading. Sep 17 09:26:53 hlmcen75n2 realmd: * /usr/bin/systemctl stop sssd.service Sep 17 09:26:53 hlmcen75n2 systemd: Stopping System Security Services Daemon... Sep 17 09:26:53 hlmcen75n2 sssd[nss]: Shutting down Sep 17 09:26:53 hlmcen75n2 sssd[be[hlm.com]]: Shutting down Sep 17 09:26:53 hlmcen75n2 sssd[pam]: Shutting down Sep 17 09:26:53 hlmcen75n2 systemd: Stopped System Security Services Daemon. Sep 17 09:26:53 hlmcen75n2 realmd: * Successfully unenrolled machine from realm
在测试时,发现加域的命令为 "realm join hlm.com -U stone" 时,可以成功加入域,但无法设别DC下的用户,需要在域名前加上DC的主机名,正确加域的命令为 "realm join hlm12r2n1.hlm.com -U stone"