Re
pypy
- 题目所给的时Python字节码,如下
4 0 LOAD_GLOBAL 0 (input)
2 LOAD_CONST 1 ('give me your flag:
')
4 CALL_FUNCTION 1
6 STORE_FAST 0 (raw_flag)
5 8 LOAD_GLOBAL 1 (list)
10 LOAD_FAST 0 (raw_flag)
12 LOAD_CONST 2 (6)
14 LOAD_CONST 3 (-1)
16 BUILD_SLICE 2
18 BINARY_SUBSCR
20 CALL_FUNCTION 1
22 STORE_FAST 1 (cipher)
6 24 LOAD_GLOBAL 2 (len)
26 LOAD_FAST 1 (cipher)
28 CALL_FUNCTION 1
30 STORE_FAST 2 (length)
8 32 LOAD_GLOBAL 3 (range)
34 LOAD_FAST 2 (length)
36 LOAD_CONST 4 (2)
38 BINARY_FLOOR_DIVIDE
40 CALL_FUNCTION 1
42 GET_ITER
>> 44 FOR_ITER 54 (to 100)
46 STORE_FAST 3 (i)
9 48 LOAD_FAST 1 (cipher)
50 LOAD_CONST 4 (2)
52 LOAD_FAST 3 (i)
54 BINARY_MULTIPLY
56 LOAD_CONST 5 (1)
58 BINARY_ADD
60 BINARY_SUBSCR
62 LOAD_FAST 1 (cipher)
64 LOAD_CONST 4 (2)
66 LOAD_FAST 3 (i)
68 BINARY_MULTIPLY
70 BINARY_SUBSCR
72 ROT_TWO
74 LOAD_FAST 1 (cipher)
76 LOAD_CONST 4 (2)
78 LOAD_FAST 3 (i)
80 BINARY_MULTIPLY
82 STORE_SUBSCR
84 LOAD_FAST 1 (cipher)
86 LOAD_CONST 4 (2)
88 LOAD_FAST 3 (i)
90 BINARY_MULTIPLY
92 LOAD_CONST 5 (1)
94 BINARY_ADD
96 STORE_SUBSCR
98 JUMP_ABSOLUTE 44
12 >> 100 BUILD_LIST 0
102 STORE_FAST 4 (res)
13 104 LOAD_GLOBAL 3 (range)
106 LOAD_FAST 2 (length)
108 CALL_FUNCTION 1
110 GET_ITER
>> 112 FOR_ITER 26 (to 140)
114 STORE_FAST 3 (i)
14 116 LOAD_FAST 4 (res)
118 LOAD_METHOD 4 (append)
120 LOAD_GLOBAL 5 (ord)
122 LOAD_FAST 1 (cipher)
124 LOAD_FAST 3 (i)
126 BINARY_SUBSCR
128 CALL_FUNCTION 1
130 LOAD_FAST 3 (i)
132 BINARY_XOR
134 CALL_METHOD 1
136 POP_TOP
138 JUMP_ABSOLUTE 112
15 >> 140 LOAD_GLOBAL 6 (bytes)
142 LOAD_FAST 4 (res)
144 CALL_FUNCTION 1
146 LOAD_METHOD 7 (hex)
148 CALL_METHOD 0
150 STORE_FAST 4 (res)
16 152 LOAD_GLOBAL 8 (print)
154 LOAD_CONST 6 ('your flag: ')
156 LOAD_FAST 4 (res)
158 BINARY_ADD
160 CALL_FUNCTION 1
162 POP_TOP
164 LOAD_CONST 0 (None)
166 RETURN_VALUE
# your flag: 30466633346f59213b4139794520572b45514d61583151576638643a
- 将字节码翻译为Python代码,参考
raw_flag = input('give me your flag:
')
cipher = list(raw_flag[6:-1])
length = len(cipher)
for i in range(length // 2):
cipher[2*i], cipher[2*i + 1] = cipher[2*i + 1], cipher[2*i]
rse = []
for i in range(length):
res.append(ord(cipher[i]) ^ i)
res = bytes(res).hex()
print('your flag: ', res)
# your flag: 30466633346f59213b4139794520572b45514d61583151576638643a
- 解密代码为
res = '30466633346f59213b4139794520572b45514d61583151576638643a'
res_b = bytes.fromhex(res)
print(res_b)
cipher = []
for i in range(len(res_b)):
cipher.append(chr(res_b[i] ^ i))
print(cipher)
for i in range(len(cipher) // 2):
cipher[2*i], cipher[2*i + 1] = cipher[2*i + 1], cipher[2*i]
print(cipher)
flag = ""
for i in cipher:
flag += i
print(flag)
- 结果为
G00dj0&_H3r3-I$Y@Ur_$L@G!~!~
Crypto
まひと
- 下载文件并打开,时morse电码,解码得到
86/109/108/110/90/87/53/108/99/109/85/116/84/71/108/114/97/84/112/57/86/109/116/116/100/107/112/105/73/84/70/89/100/69/70/52/90/83/70/111/99/69/48/120/101/48/48/114/79/88/104/120/101/110/74/85/84/86/57/79/97/110/53/106/85/109/99/48/101/65/61/61
VmlnZW5lcmUtTGlraTp9VmttdkpiITFYdEF4ZSFocE0xe00rOXhxenJUTV9Oan5jUmc0eA==
Vigenere-Liki:}VkmvJb!1XtAxe!hpM1{M+9xqzrTM_Nj~cRg4x
- 维吉尼亚加密,且密钥为Liki,解密
}KccnYt!1NlPpu!zeE1{C+9pfrhLB_Fz~uGy4n
- 因为明文中是包含hgame的,因此必有移位,遍历以下移位后结果中包含hgame的
def caesar(c, n):
tmp = ""
for i in c:
if 'a' <= i <= 'z':
if ord(i) + n > ord('z'):
tmp += chr((ord(i) - ord('a') + n) % 26 + ord('a'))
else:
tmp += chr(ord(i) + n)
elif 'A' <= i <= 'Z':
if ord(i) + n > ord('Z'):
tmp += chr((ord(i) - ord('A') + n) % 26 + ord('A'))
else:
tmp += chr(ord(i) + n)
else:
tmp += i
return tmp
c = "}KccnYt!1NlPpu!zeE1{C+9pfrhLB_Fz~uGy4n"
for i in range(2, 26):
res = caesar(c, i)
if 'h' in res and 'g' in res and 'a' in res and 'm' in res and 'e' in res:
print(i, res)
结果为移位13时包含,字符串为}XppaLg!1AyCch!mrR1{P+9cseuYO_Sm~hTl4a
6. 根据括号的位置可以判断还有一层栅栏密码,尝试发现每组字数6,得到}!!Pu~X1m+YhpAr9OTpyRc_laC1sS4Lc{emagh字符串反转一下得到flag
hgame{cL4Ss1Cal_cRypTO9rAphY+m1X~uP!!}
WhitegiveRSA
确实白给
- 先大数分解得到p和q分别为857504083339712752489993810777和1029224947942998075080348647219
- python代码如下
import gmpy2
from Crypto.Util.number import long_to_bytes
e = 65537
c = 747831491353896780365654517748216624798517769637260742155527
n = 882564595536224140639625987659416029426239230804614613279163
p = 857504083339712752489993810777
q = 1029224947942998075080348647219
phn = (p-1) * (q-1)
d = gmpy2.invert(e, phn)
print(d)
m = pow(c, d, n)
print(long_to_bytes(m)
hgame{w0w~yOU_kNoW+R5@!}
MISC
Week-1
不起眼压缩包的养成的方法
- 下载得到一个jpg文件,用010Editor打开,发现末尾有
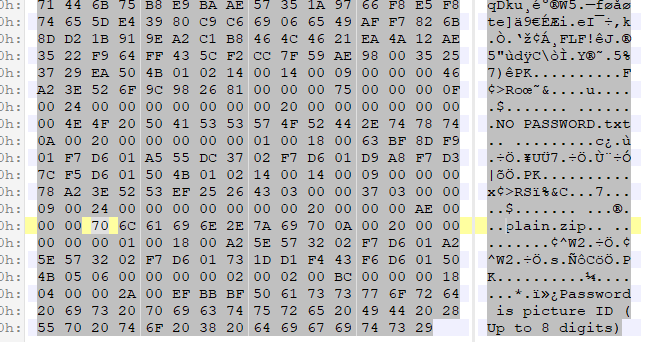
- 因此推测jpg中包含zip文件,且口令为8位数字
- 用
foremost分离出zip文件,并使用Advanced Archive Password Recovery暴力破解,得到口令为70415155

- 成功解压缩,得到两个文件
- 发现plain.zip中还有个NO PASSWORD.txt且没有更多的提示,因此应该是利用这个文本文件进行已知明文攻击,参考
- 在ARCHPR中添加待解密的文件和我们自己压缩的文件,最初在此遇到了报错
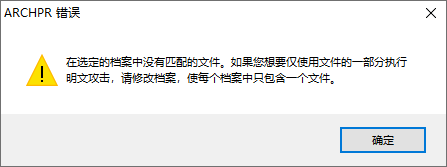
- 因此换成winRAR进行压缩,在压缩前查看了已有的待破解压缩包的属性有
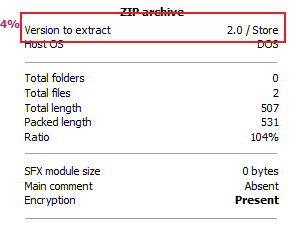
- 因此将NO PASSWORD.txt以同样的方式进行压缩
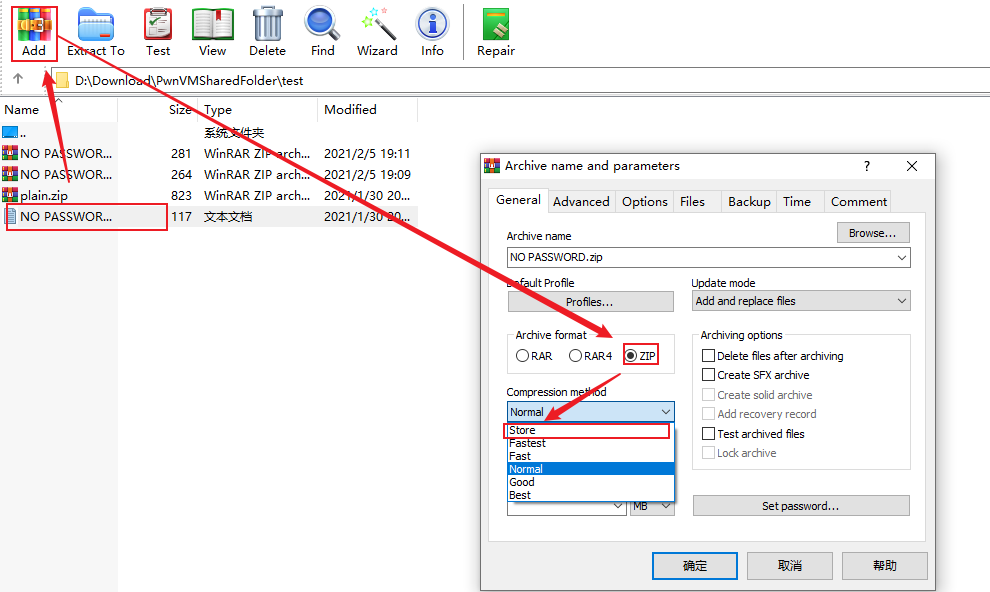
- 现在可以成功开始
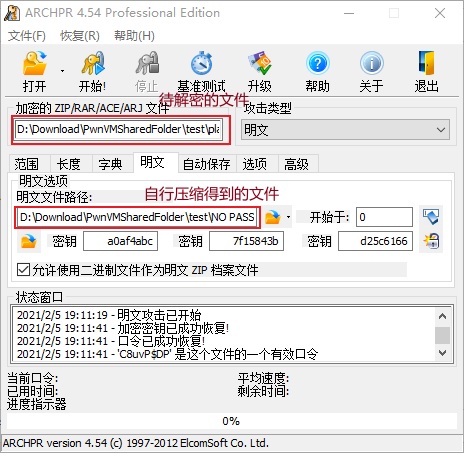
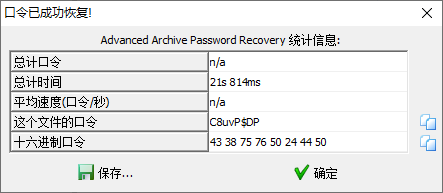
- 最终得到口令为
C8uvP$DP
- 解压plain.zip得到其中的flag.zip,由于没有更多的提示,所以用010Editor查看以下,得到以下信息
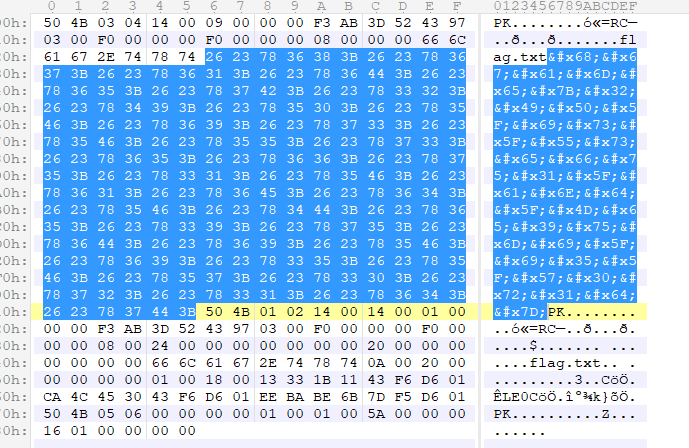
- 将这段值复制出来转成ASCII即可得到flag为
hgame{2IP_is_Usefu1_and_Me9umi_i5_W0r1d}
Galaxy
- 下载pcapng文件,拖到wireshark看下,根据提示有一张星空壁纸,所以先搜索有无png
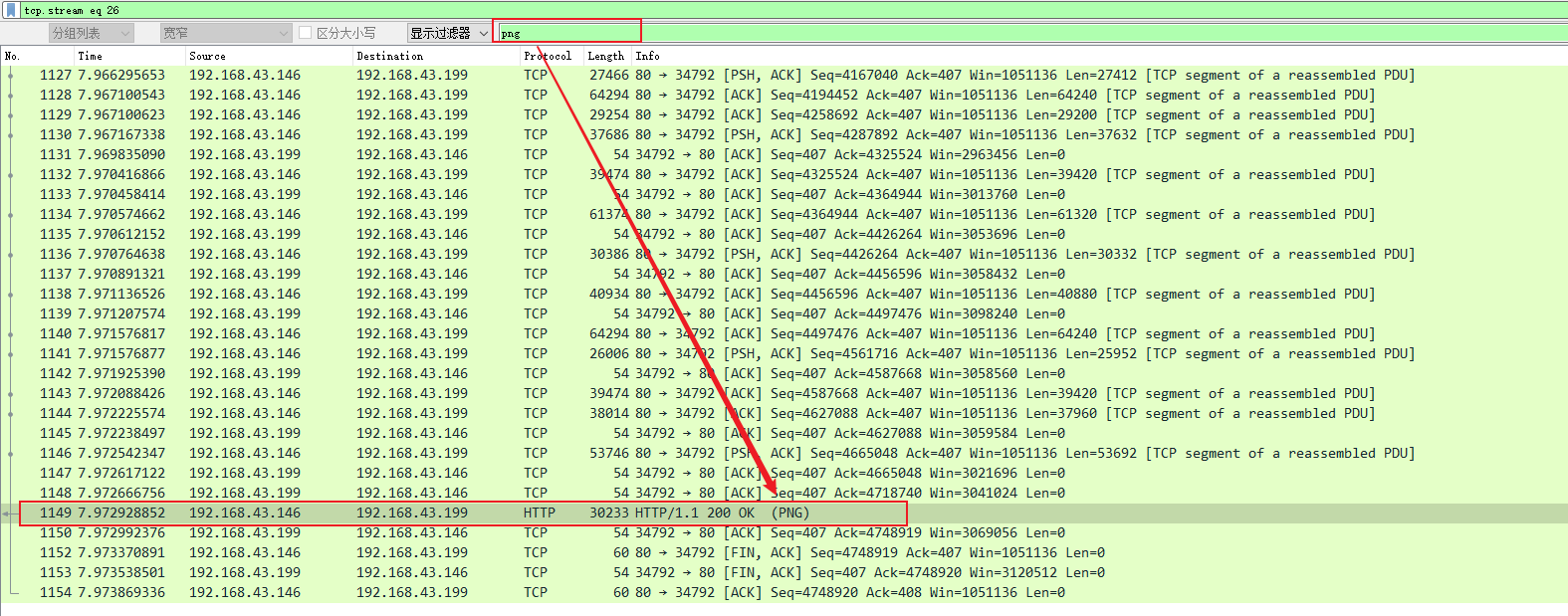
- 双击这条,然后找到PNG文件流所在位置,复制hex流
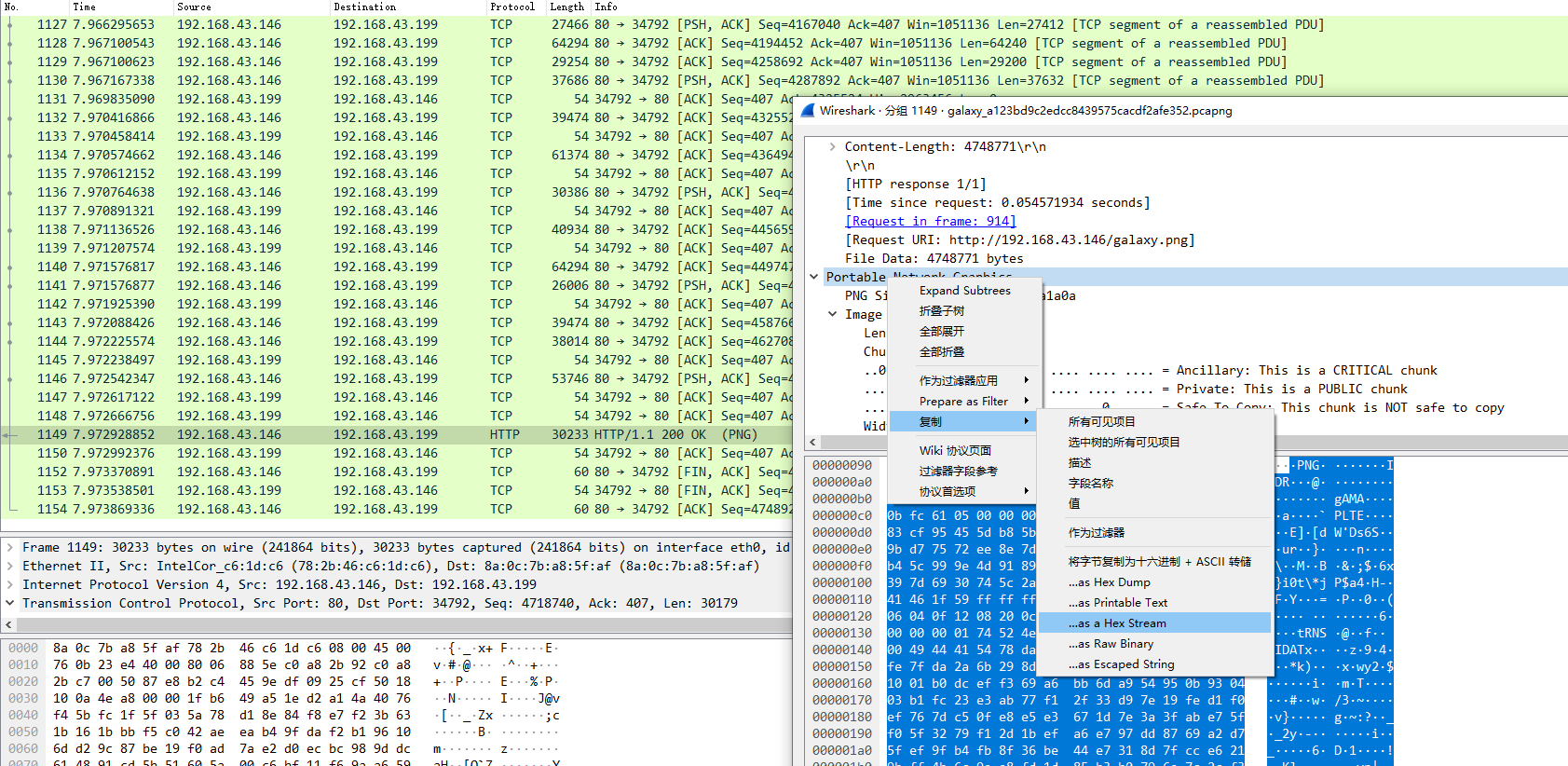
- 用Python将其转为文件
import binascii
m= '将复制好的hex流粘贴至此'
f=open('flag.png', 'wb')
f.write(binascii.a2b_hex(m))
- 打开得到的png文件却提示
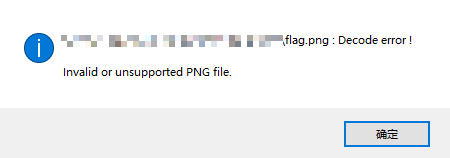
- 用010Editor打开提示CRC校验错误,看一下图片宽高,因此可能是高度有错,通过CRC爆破即可,这里参考以前的一篇博客,只需改下图片名即可
import struct
import binascii
from Crypto.Util.number import bytes_to_long
img = open("flag.png", "rb").read()
for i in range(0xFFFF):
stream = img[12:20] + struct.pack('>i', i) + img[24:29]
crc = binascii.crc32(stream)
if crc == bytes_to_long(img[29:33]):
print(hex(i))
- 输出结果1000,因此将高度改为1000即可看到flag

hgame{Wh4t_A_W0nderfu1_Wa11paper}
Word RE:MASTER
- 解压缩发现两个文件,maimai.docx需要口令,因此推测first中有关键信息
查看文件属性也可以发现提示

- binwalk查看
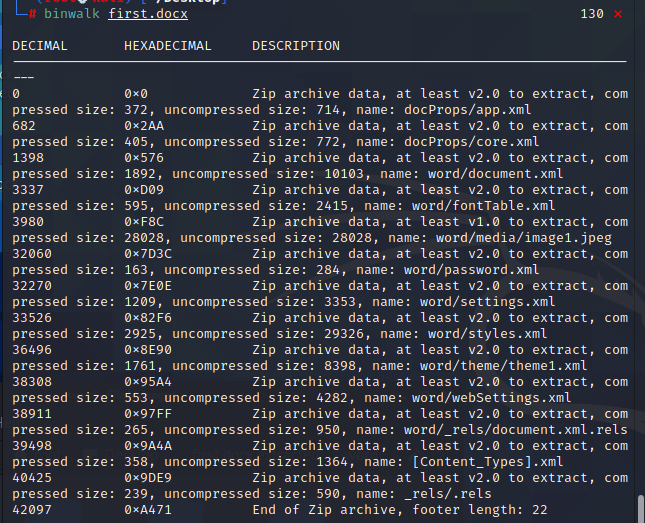
binwalk -e first.docx分离文件,发现有个password.xml
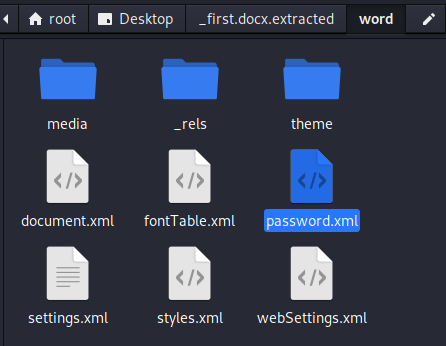
- 打开后得到

+++++ +++[- >++++ ++++< ]>+++ +.<++ +[->+ ++<]> ++.<+ ++[-> +++<] >+.<+ ++[-> ---<] >-.++ ++++. <+++[ ->--- <]>-. +++.+ .++++ ++++. <+++[ ->--- <]>-- ----. +.--- --..+ .++++ +++++ .<+++ [->-- -<]>- ----- .<
- Brainfuck解密,得到
DOYOUKNOWHIDDEN? - 用其成功打开maimai.docx

- 请教大佬,发现是snow隐写参考
- 将docx导出txt文件
SNOW.EXE -C maimai.txt

hgame{Cha11en9e_Whit3_P4ND0R4_P4R4D0XXX}
Week-2
Hallucigenia
- 用Stegsolve打开,发现了一个被反色的QR二维码

- 保存这个二维码并反色,得到

- 扫描得到
gmBCrkRORUkAAAAA+jrgsWajaq0BeC3IQhCEIQhCKZw1MxTzSlNKnmJpivW9IHVPrTjvkkuI3sP7bWAEdIHWCbDsGsRkZ9IUJC9AhfZFbpqrmZBtI+ZvptWC/KCPrL0gFeRPOcI2WyqjndfUWlNj+dgWpe1qSTEcdurXzMRAc5EihsEflmIN8RzuguWq61JWRQpSI51/KHHT/6/ztPZJ33SSKbieTa1C5koONbLcf9aYmsVh7RW6p3SpASnUSb3JuSvpUBKxscbyBjiOpOTq8jcdRsx5/IndXw3VgJV6iO1+6jl4gjVpWouViO6ih9ZmybSPkhaqyNUxVXpV5cYU+Xx5sQTfKystDLipmqaMhxIcgvplLqF/LWZzIS5PvwbqOvrSlNHVEYchCEIQISICSZJijwu50rRQHDyUpaF0y///p6FEDCCDFsuW7YFoVEFEST0BAACLgLOrAAAAAggUAAAAtAAAAFJESEkNAAAAChoKDUdOUIk=