1、官网下载strongswan
2020/03/29, size 7'282'749 bytes, pgp-signature,
md5: d97e8eeb4fc0223f0d6fb331c4d2bcce
链接:https://www.strongswan.org/download.html
2、编译和安装
tar -zxvf strongswan-5.8.4.tar.gz ./configure --prefix=/usr/ --sysconfdir=/etc/ make make install
3、配置
以下官网链接有各种配置方案。
https://www.strongswan.org/testing/testresults/swanctl/index.html
我在两台Ubuntu虚拟机上的进行了配置。
机器IP:192.168.103.126
文件名称:ipsec.conf
config setup charondebug="all" uniqueids=yes strictcrlpolicy=no conn %default conn tunnel # left=192.168.103.119 leftsubnet=192.168.103.0/24 right=192.168.103.126 rightsubnet=192.168.103.0/24 ike=aes256-sha2_256-modp1024! esp=aes256-sha2_256! keyingtries=0 ikelifetime=1h lifetime=8h dpddelay=30 dpdtimeout=120 dpdaction=restart authby=secret auto=start keyexchange=ikev2 type=tunnel rekey=no
文件名称:ipsec.secrets
# ipsec.secrets - strongSwan IPsec secrets file 192.168.103.119 192.168.103.126 : PSK "wzg123456"
机器IP:192.168.103.119
文件名称:ipsec.conf
config setup charondebug="all" uniqueids=yes strictcrlpolicy=no conn %default conn tunnel # left=192.168.103.119 leftsubnet=192.168.103.0/24 right=192.168.103.126 rightsubnet=192.168.103.0/24 ike=aes256-sha2_256-modp1024! esp=aes256-sha2_256! keyingtries=0 ikelifetime=1h lifetime=8h dpddelay=30 dpdtimeout=120 dpdaction=restart authby=secret auto=start keyexchange=ikev2 type=tunnel rekey=no
文件名称:ipsec.secrets
# ipsec.secrets - strongSwan IPsec secrets file 192.168.103.126 192.168.103.119 : PSK "wzg123456"
4、启动
两台机器均执行:
ipsec start
然后执行如下指令查看状态:
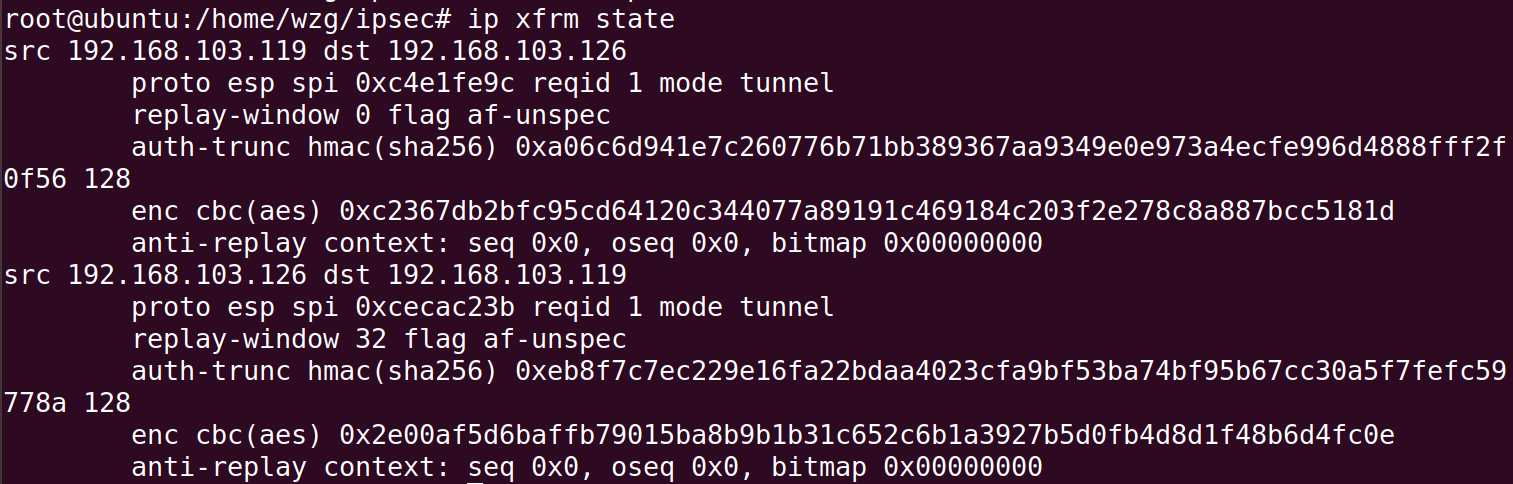
ip xfrm state
ipsec statusall
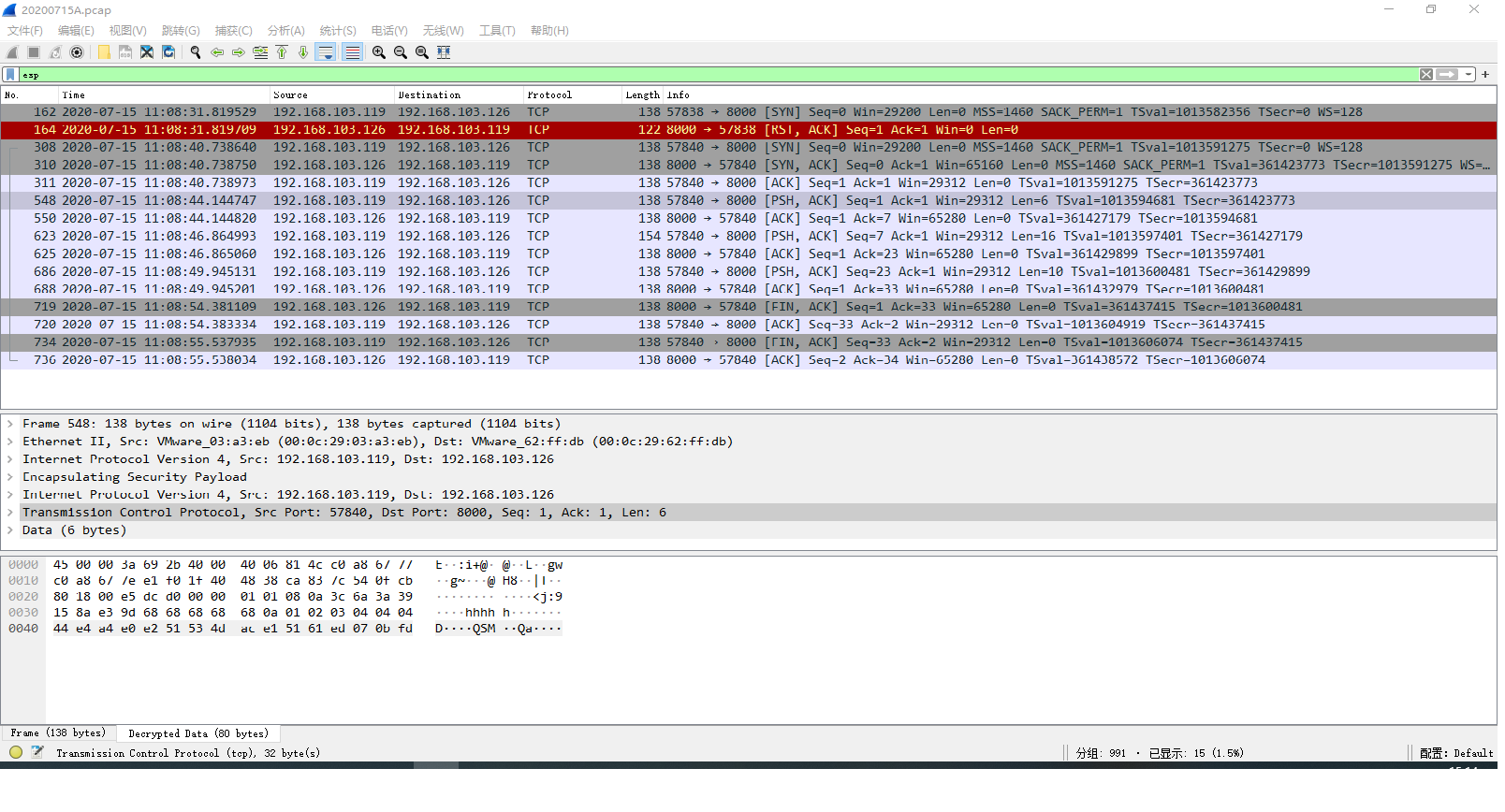
5、测试
使用ping或者nc测试,tcpdum进行捕包。
例如:
nc -nvl 8000
nc 192.168.103.126 8000
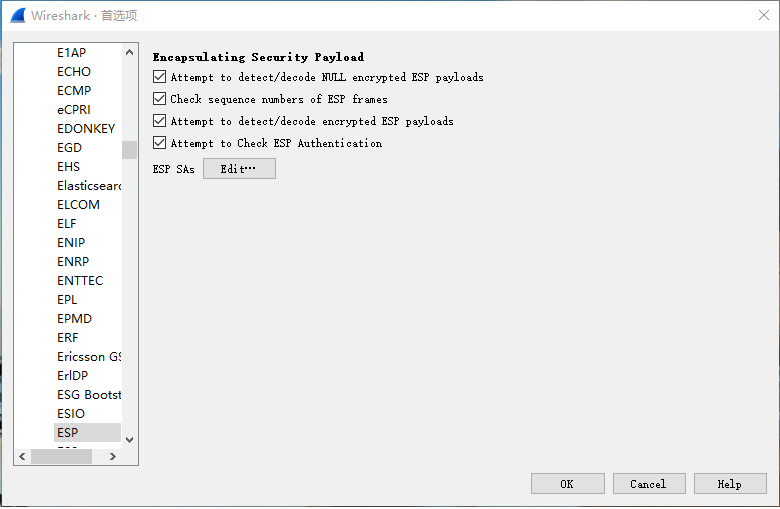
使用wireshark,输入sa信息,进行数据包解密:
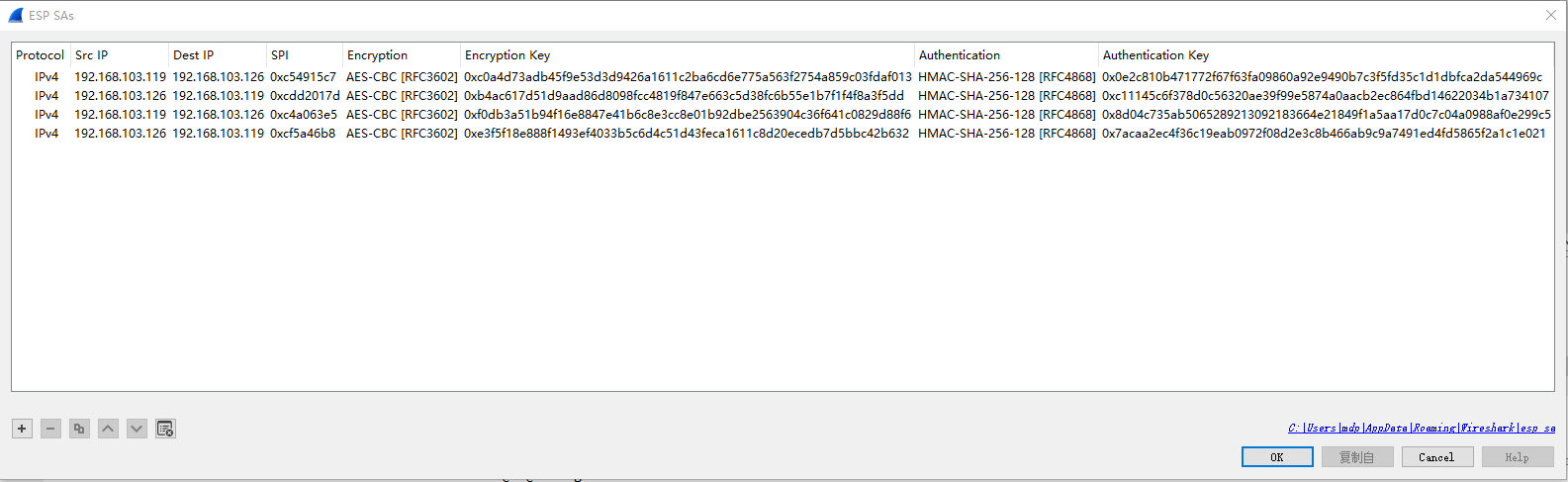
如下所示,解密数据成功: