一、最简单的misc-y1ng
题目下载下来是带密码的 secret.zip压缩包,怀疑伪加密,拖到 kali 看一眼,直接可以提取出 secret 文件,winhex 看一下有 IHDR(文件头数据块)

应该是 png 文件但是缺少了文件头,winhex 补一下 89 50 4E 47
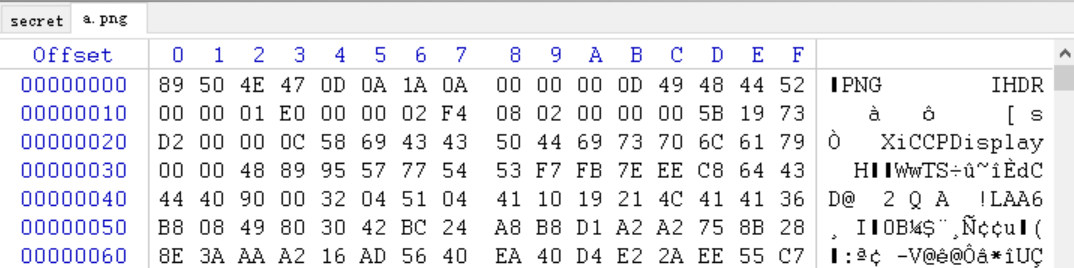
可以成功打开图片,看到一串十六进制 424A447B79316E677A756973687561697D,十六进制转字符串得到 BJD{y1ngzuishuai}

二、A_Beautiful_Picture
下载下来是 png 图片,拖到 kali 看一下,很明显的 CRC 问题,这种情况要么是计算出正确的 CRC ,要么是根据CRC 修改图片宽高了
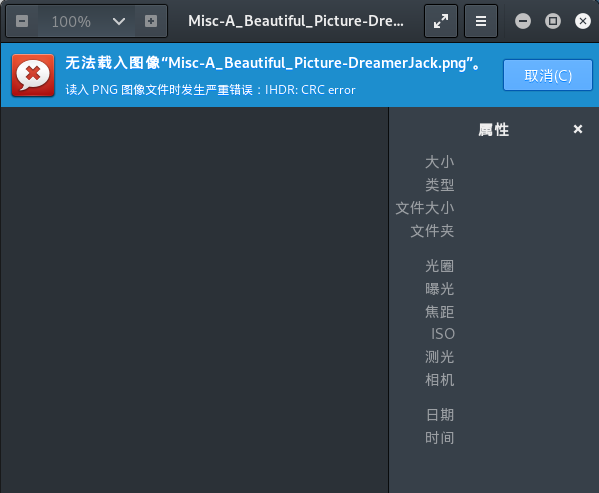
直接尝试根据 CRC 修复图片高度

CRC修改图片高度脚本:
# -*- coding: utf-8 -*- import binascii import struct crc32key = 0xC2C143B3 for i in range(0, 65535): height = struct.pack('>i', i) #CRC: C2C143B3 data = 'x49x48x44x52x00x00x03xE8' + height + 'x08x02x00x00x00' crc32result = binascii.crc32(data) & 0xffffffff if crc32result == crc32key: print ''.join(map(lambda c: "%02X" % ord(c), height))
跑出结果:000003E8,在 winhex 修改对应位置得到 flag
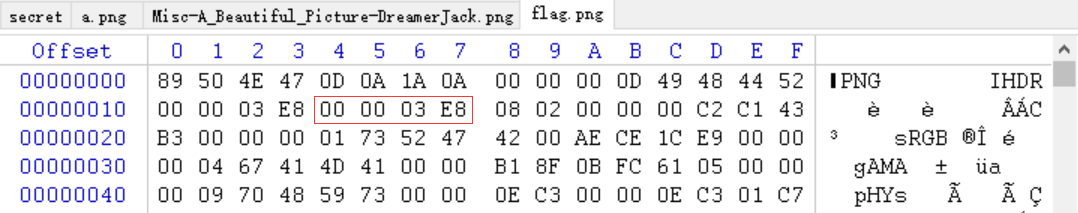

三、Real_EasyBaBa
下载下来的图片 ezbb_r.png 拖到 kali 分析一下,可以看到是 jpeg 格式的图片,并且有 zip 文件尾,应该是在图片尾部藏了一个压缩包,但是缺少压缩包的头标识

winhex 打开图片,搜索 jpeg 的文件尾标识 FF D9 ,然后把剩下的部分复制出来保存为压缩包文件,再补充好 zip 文件头标识 50 4B 03 04
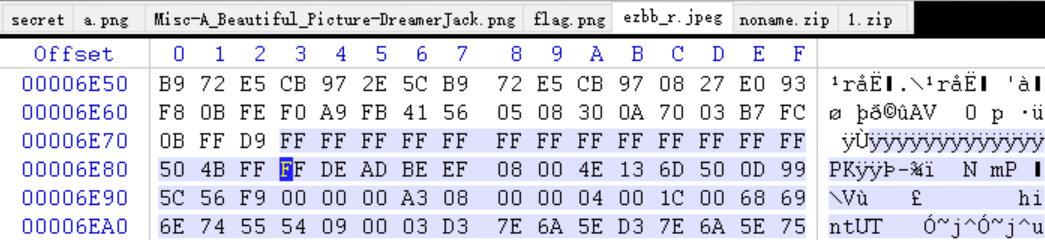
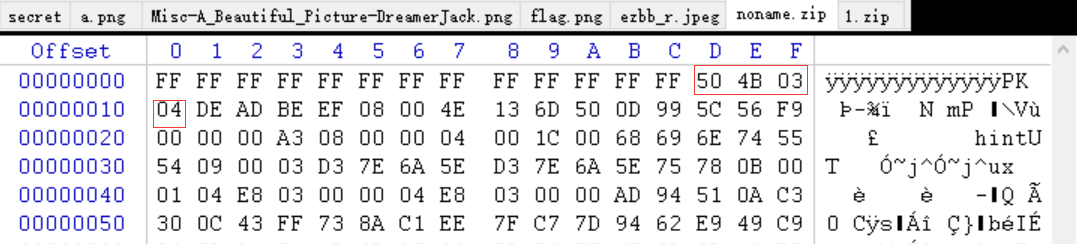
压缩包解压后发现 hint 文件,很明显是一个二维码

然后我用的方式就比较笨了,不知道师傅们有什么更聪明的方式,我把 # 替换成1,空格替换成0,然后发现这个图案虽然看着是正方形,但是实际是29行58列,再把每一行复制一下,得到58行58列的01字符串,再用01字符串转二维码的脚本跑一下,得到拼接出的二维码图片
from PIL import Image length = 58 img = Image.new('RGB', (length*5, length*5)) #黑点为1白点为0 data = "1111111111111100001100000011000011111111110011111111111111111111111111110000110000001100001111111111001111111111111111000000000011001111001111001111110011000000110000000000111100000000001100111100111100111111001100000011000000000011110011111100110000111111000000110000110000001100111111001111001111110011000011111100000011000011000000110011111100111100111111001100111100110011000000110000000011001111110011110011111100110011110011001100000011000000001100111111001111001111110011000000110011000000110011110000110011111100111100111111001100000011001100000011001111000011001111110011110000000000110011001100000000111100000000001100000000001111000000000011001100110000000011110000000000110000000000111111111111111100110011001100110011001100110011111111111111111111111111110011001100110011001100110011001111111111111100000000000000000000000011000011000000001100000000000000000000000000000000000000001100001100000000110000000000000000111111111100111111111100111100110011001111110011001100110011111111110011111111110011110011001100111111001100110011001100001111000011001100000011000011001111110011111111111111110000111100001100110000001100001100111111001111111111111111110000001111110011001111001111000011000011000011110011001111000000111111001100111100111100001100001100001111001100111111001111000011111111000011111100000000111111111100110011111100111100001111111100001111110000000011111111110011001111001111111100001100110011001111110000000000000011111100111100111111110000110011001100111111000000000000001111110011110000001100111111110011001100110011110011111111110011111111000000110011111111001100110011001111001111111111001111000011111111110011000000001100110000000011110011000011110000001111111111001100000000110011000000001111001100001111001111111111000011110011001100001100001111110000110011001100111111111100001111001100110000110000111111000011001100110011111100001111000000000011110011001111000000000000111100001111110000111100000000001111001100111100000000000011110000111111110000000011000000001111000000111111001100111100111111111111000000001100000000111100000011111100110011110011111100110011111111000000111100001100001100000000000000000000110011001111111100000011110000110000110000000000000000000011000011000000110000001100000011110011111100111100110000111100001100000011000000110000001111001111110011110011000011110011110000111100000011000000001111111111111111111111001111001111000011110000001100000000111111111111111111111100110000000000000000111100001111000011111100110000001100111111000000000000000011110000111100001111110011000000110011111111111111111111001111110000111111000000111100110011000000001111111111111100111111000011111100000011110011001100000000110000000000110000111100111100110000001111000000110000000011000000000011000011110011110011000000111100000011000000001100111111001100111100001100111100111100111111111111111111110011111100110011110000110011110011110011111111111111111111001111110011001100000000000000000000000011000000000011111100111111001100110000000000000000000000001100000000001111110011111100110011111111110000110000000000111100111100110011001111110011001111111111000011000000000011110011110011001100000000001100111111110000110011000011110011001100001100110000000000110011111111000011001100001111001100110000110011111111111111001111111100000011111111110011110011001100001111111111111100111111110000001111111111001111001100110000" for x in range(length): for y in range(length): if data[x*length+y] == '1': for xx in range(x*5, x*5+5): for yy in range(y*5, y*5+5): img.putpixel([xx, yy], (0,0,0)) else: for xx in range(x*5, x*5+5): for yy in range(y*5, y*5+5): img.putpixel([xx, yy], (255,255,255)) img.save('out.png')

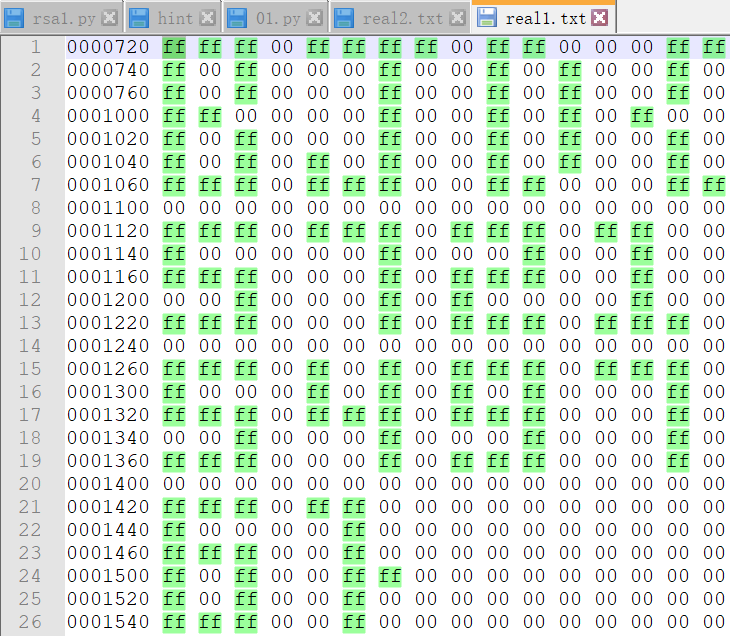
扫描后得到结果 od -vtx1 ./draw.png | head -56 | tail -28 把 draw.png 换成 ezbb_r.png 跑一下,乍一看以为又是一个二维码呢,把 ff 高亮一下显示发现并不是二维码,直接显示的是 flag 的图像了,结果是 BJD{572154976}

四、圣火昭昭-y1ng
在图片属性备注里可以看到
新佛曰:諸壽隸僧壽降吽壽諸壽陀壽摩隸僧缽薩願心壽咤壽囉寂壽闍諸壽哆壽慧壽聞壽色吽愍壽所壽蜜如
找网站 http://hi.pcmoe.net/buddha.html 翻译一下得到 gemlovecom ,公告说 key 中 com 是多余的
所以应该是用什么工具加密的信息,密码是 gemlove,根据经验试了下 outguess
命令:
outguess -k gemlove -r sheng_huo_zhao_zhao.jpg -t flag.txt
得到 flag
五、小姐姐-y1ng
直接能搜出来
