假设现在有两台服务器client1,client2,他们直接不能直接相互通信,但是他们均能连接上第三台服务器balance,我们可以在client1,client2和balance三台机器之间建立ssh隧道来让client1和client2实现通信。
ssh端口转发有三种实现方式:本地转发,远程转发,和动态转发。
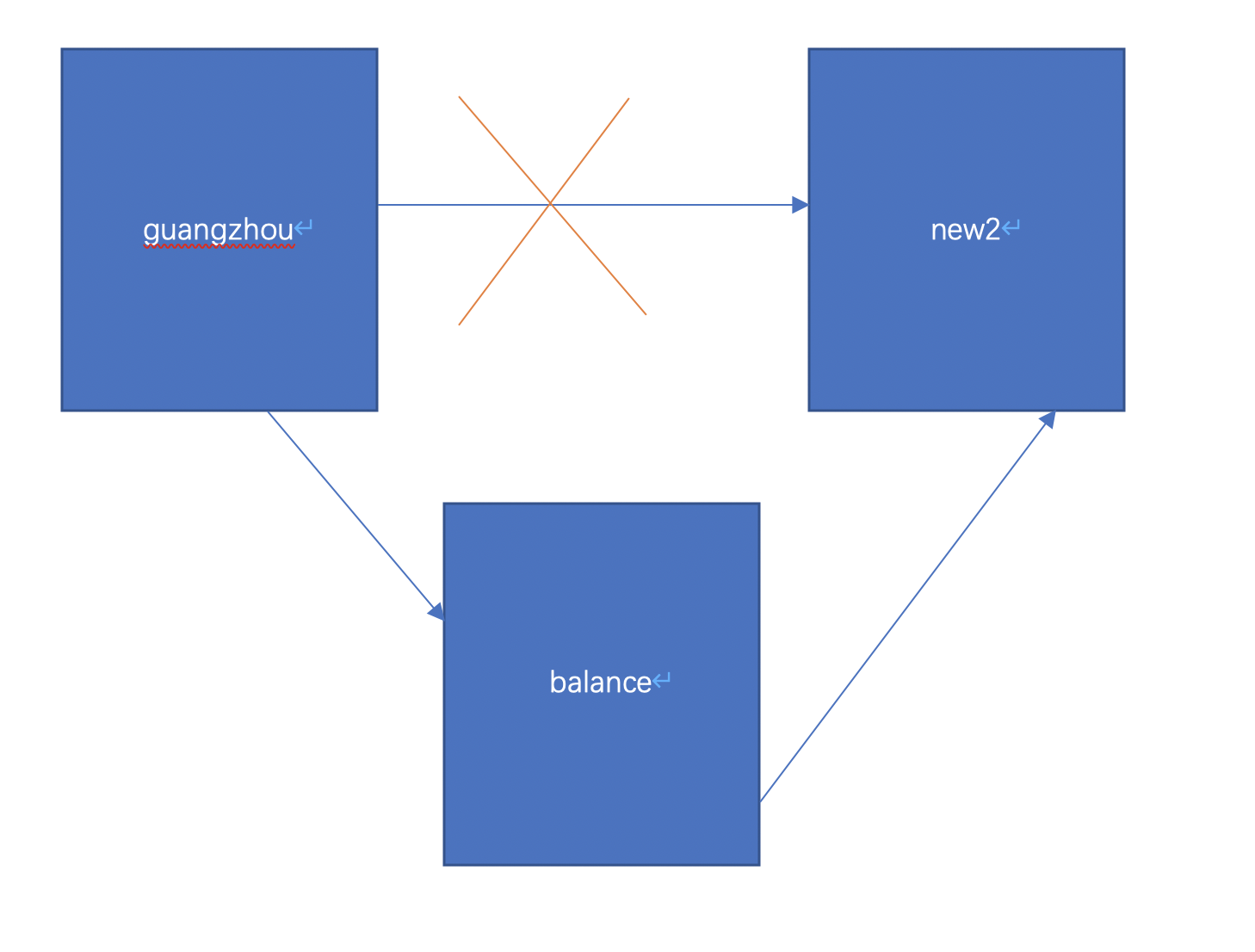
定义简称:发起请求的服务器(简称"startServer"),最终目标服务器(简称“targetServer”),连接startServer和targetServer的服务器(简称“bridgeServer”)
一. 准备工作
实现目标: startServer能访问bridgeServer但不能直接访问targetServer,bridgeServer可以访问targetServer;startServer通过bridgeServer做端口转发可以间接访问targetServer。
1.1 服务器IP:
startServer:服务器guangzhou-IP 106.55.241.99
targetServer:服务器new2-IP 106.55.171.53
bridgeServer:服务器balance-IP 124.156.143.168
1.2 服务器间通信状态
服务器guangzhou:
#可访问new2
[root@guangzhou ~]# telnet 106.55.171.53 22
Trying 106.55.171.53...
Connected to 106.55.171.53.
Escape character is '^]'.
SSH-2.0-OpenSSH_7.4
#可访问balance
[root@guangzhou ~]# telnet 124.156.143.168 22
Trying 124.156.143.168...
Connected to 124.156.143.168.
Escape character is '^]'.
SSH-2.0-OpenSSH_7.4
服务器balance:
#可访问new2
[root@Balance ~]# telnet 106.55.241.99 22 Trying 106.55.241.99... Connected to 106.55.241.99. Escape character is '^]'. SSH-2.0-OpenSSH_7.4
现在上new2防火墙添加禁止guangzhou访问并重启firewalld服务:
[root@new2 ~]# firewall-cmd --permanent --add-rich-rule='rule family=ipv4 source address="106.55.241.99" drop'
success
[root@new2 ~]# firewall-cmd --reload
success
登陆guangzhou服务器执行命令: telnet 106.55.171.53 22 ,结果无响应,说明防火墙禁止访问设置成功。
目前guangzhou无法直连new2,可连接balance,balance可连接new2.
二. 配置端口转发
2.1 本地转发
命令:-L localport:remotehost:remotehostport sshserver
说明:localport 本机开启的端口号
remotehost 最终连接机器的IP地址
remotehostport 转发机器的端口号
sshserver 转发机器的IP地址
# -L startServerIp:targetServerIp:targetServerPort bridgeServerUser@bridgeServerIp
[root@guangzhou ~]# ssh -L 9001:106.55.171.53:22 root@124.156.143.168 root@124.156.143.168's password: Last failed login: Thu Oct 8 19:29:00 CST 2020 from 61.135.223.109 on ssh:notty There were 8 failed login attempts since the last successful login. Last login: Thu Oct 8 19:26:38 2020 from 106.55.241.99 [root@Balance ~]#
新开窗口打开guangzhou服务器:
[root@guangzhou ~]# ssh -p 9001 root@127.0.0.1
The authenticity of host '[127.0.0.1]:9001 ([127.0.0.1]:9001)' can't be established.
ECDSA key fingerprint is SHA256:huOuuKbfM9TN6+rpCMjB2Hk0HI4GSF1WCj7gIVyu48I.
ECDSA key fingerprint is MD5:0f:55:88:04:62:82:fc:8b:6a:f5:9e:5c:56:e1:0b:cc.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '[127.0.0.1]:9001' (ECDSA) to the list of known hosts.
root@127.0.0.1's password:
Last failed login: Thu Oct 8 19:29:28 CST 2020 from 213.154.70.102 on ssh:notty
There were 832 failed login attempts since the last successful login.
Last login: Thu Oct 8 18:41:46 2020 from 106.55.241.99
[root@new2 ~]#
上面可见后面新开窗口通过访问9001端口可以连接上new2服务器。
2.2 远程转发
命令:-R sshserverport:remotehost:remotehostport sshserver
说明:sshserverport 被转发机器开启的端口号
remotehost 最终连接机器的IP地址
remotehostport 被转发机器的端口号
sshserver 被转发机器的IP地址
#balance服务器上开启端口转发服务
# -R startServerPort:targetServerIp:targetServerPort -fN startServerIp
[root@Balance ~]# ssh -R 9100:106.55.171.53:22 -fN 106.55.241.99 root@106.55.241.99's password: [root@Balance ~]#
#guangzhou服务器上查看balance端口转发开启的9100端口
[root@guangzhou ~]# ss -ntl State Recv-Q Send-Q Local Address:Port Peer Address:Port LISTEN 0 128 *:27017 *:* LISTEN 0 511 *:6379 *:* LISTEN 0 128 *:9100 *:* LISTEN 0 128 *:111 *:* LISTEN 0 128 *:4369 *:* LISTEN 0 128 *:22 *:* LISTEN 0 80 :::3306 :::* LISTEN 0 511 :::6379 :::* LISTEN 0 128 :::111 :::* LISTEN 0 128 :::4369 :::* #连接9100端口,确认可以连接上new2服务器
[root@guangzhou ~]# ssh -p 9100 root@127.0.0.1 The authenticity of host '[127.0.0.1]:9100 ([127.0.0.1]:9100)' can't be established. ECDSA key fingerprint is SHA256:huOuuKbfM9TN6+rpCMjB2Hk0HI4GSF1WCj7gIVyu48I. ECDSA key fingerprint is MD5:0f:55:88:04:62:82:fc:8b:6a:f5:9e:5c:56:e1:0b:cc. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '[127.0.0.1]:9100' (ECDSA) to the list of known hosts. root@127.0.0.1's password: Last failed login: Fri Oct 9 11:28:02 CST 2020 from 61.7.235.211 on ssh:notty There were 3 failed login attempts since the last successful login. Last login: Fri Oct 9 11:26:16 2020 from 117.136.79.20 [root@new2 ~]#
远程转发就是做了一层请求代理服务,将指定客户端IP和客户端端口的请求转发到指定第三方服务器IP和端口。
2.3动态转发
命令:-D localhost:localport -fN sshserver
# -D startServerPort -fN bridgeServerIp
#guangzhou服务器上关掉所有ssh连接
[root@guangzhou ~]# killall ssh
[root@guangzhou ~]# ssh -D 9200 -fN 124.156.143.168
root@124.156.143.168's password:
[root@guangzhou ~]# curl --socks5 127.0.0.1:9200 http://106.55.171.53
hello~
以上通过设置guangzhou服务器9200端口转发已经可以正常请求new2服务器上的web服务。
三. 使用实践
假设guangzhou服务器访问new2服务器的mysql服务,mysql端口为3306,同之前一样new2防火墙增加IP禁止guangzhou访问。
以下是php实现的例子。
#guangzhou服务器使用9001端口通过balance连接new2的3306端口,这里以本地转发为例
[root@guangzhou ~]# ssh -L 9001:106.55.171.53:3306 root@124.156.143.168
root@124.156.143.168's password:
Last failed login: Fri Oct 9 16:10:57 CST 2020 from 124.65.143.22 on ssh:notty
There were 476 failed login attempts since the last successful login.
Last login: Fri Oct 9 15:49:20 2020 from 117.136.79.20
#guangzhou服务器新开窗口mysql命令行链接测试下
[root@guangzhou ~]# mysql -h127.0.0.1 -P9001 -utest1 -p123456
Welcome to the MariaDB monitor. Commands end with ; or g.
Your MariaDB connection id is 19
Server version: 10.2.31-MariaDB-log MariaDB Server
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or 'h' for help. Type 'c' to clear the current input statement.
MariaDB [(none)]>
[root@guangzhou ~]# cat pdo.php
<?php
$host = "127.0.0.1";
$port = "9001";
$username = "root";
$password = "123456";
$dbname = "test";
$charset = "utf8mb4";
$dsn = "mysql:dbname=$dbname;host=$host";
try{
$pdo = new Pdo($dsn, $username, $password);
$pdo->setAttribute(PDO::ATTR_ERRMODE, PDO::ERRMODE_EXCEPTION); // 设置sql语句查询如果出现问题 就会抛出异常
set_exception_handler("cus_exception_handler");
} catch(PDOException $e){
die("连接失败: ".$e->getMessage());
}
function cus_exception_handler($e)
{
die("sql 异常: ".$e->getMessage());
}
//查询数据
$state = $pdo->query("select * from home limit 1");
// query执行一条SQL语句,如果通过,则返回一个PDOStatement对象,可以直接遍历这个返回的记录集 (query用于select)
$res = $state->fetch(PDO::FETCH_ASSOC); // 获取结果集中的一行数据
print_r($res);
[root@guangzhou ~]# php pdo.php
Array
(
[home_id] => 34
[profile] => test
[scope] => no
[product] => no
[cooperate] => no
[extension] => n
)
| 优点 | 缺点 | |
| 本地转发 | 不用占用bridgeServer机器上新开端口(默认使用22端口) | 占用startServer端口,bridgeServer的IP+端口,更换startServer后需要再次执行ssh命令 |
| 远程转发 | 不限制startServer的IP,bridgeServer执行一次可一直使用转发服务 | 需要bridgeServer持续提供服务的话要启用常住进程,占用bridgeServer机I/O资源 |
| 动态转发 | 不需要bridgeServer提供常住进程服务,无需bridgeServer和targetServer指定端口 | 需要startServer占用端口,更换startServer后需要再次执行ssh命令 |
总的来说,三种转发各有优缺点,本地转发和远程转发需要时刻保证ssh隧道可用,动态转发则不需要,可以按照自己需求设置即可。
至此,三种ssh端口转发方式实践完毕。