网上有很多关于dashboard的部署,但是可能是时间太久远了,yaml文件运行之后不是镜像拉不下来就是各种运行报错,经过了多番尝试,我找到了一个比较合适的yaml分享给大家。
这个dashboard的namespace是用的kubernetes-dashboard,如果你你想改成kube-system也可以的,不会有影响,这里的镜像我已经替大家替换过了
image: kubernetesui/dashboard:v2.0.0-beta4 这个是一个私人的镜像
vim dashboard.yaml
# Copyright 2017 The Kubernetes Authors. # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # http://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: Namespace metadata: name: kubernetes-dashboard --- apiVersion: v1 kind: ServiceAccount metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard --- kind: Service apiVersion: v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard spec: type: NodePort ports: - port: 443 targetPort: 8443 nodePort: 30001 selector: k8s-app: kubernetes-dashboard --- apiVersion: v1 kind: Secret metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-certs namespace: kubernetes-dashboard type: Opaque --- apiVersion: v1 kind: Secret metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-csrf namespace: kubernetes-dashboard type: Opaque data: csrf: "" --- apiVersion: v1 kind: Secret metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-key-holder namespace: kubernetes-dashboard type: Opaque --- kind: ConfigMap apiVersion: v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-settings namespace: kubernetes-dashboard --- kind: Role apiVersion: rbac.authorization.k8s.io/v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard rules: # Allow Dashboard to get, update and delete Dashboard exclusive secrets. - apiGroups: [""] resources: ["secrets"] resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs", "kubernetes-dashboard-csrf"] verbs: ["get", "update", "delete"] # Allow Dashboard to get and update 'kubernetes-dashboard-settings' config map. - apiGroups: [""] resources: ["configmaps"] resourceNames: ["kubernetes-dashboard-settings"] verbs: ["get", "update"] # Allow Dashboard to get metrics. - apiGroups: [""] resources: ["services"] resourceNames: ["heapster", "dashboard-metrics-scraper"] verbs: ["proxy"] - apiGroups: [""] resources: ["services/proxy"] resourceNames: ["heapster", "http:heapster:", "https:heapster:", "dashboard-metrics-scraper", "http:dashboard-metrics-scraper"] verbs: ["get"] --- kind: ClusterRole apiVersion: rbac.authorization.k8s.io/v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard rules: # Allow Metrics Scraper to get metrics from the Metrics server - apiGroups: ["metrics.k8s.io"] resources: ["pods", "nodes"] verbs: ["get", "list", "watch"] --- apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard roleRef: apiGroup: rbac.authorization.k8s.io kind: Role name: kubernetes-dashboard subjects: - kind: ServiceAccount name: kubernetes-dashboard namespace: kubernetes-dashboard --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: kubernetes-dashboard namespace: kubernetes-dashboard roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: kubernetes-dashboard subjects: - kind: ServiceAccount name: kubernetes-dashboard namespace: kubernetes-dashboard --- kind: Deployment apiVersion: apps/v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard spec: replicas: 1 revisionHistoryLimit: 10 selector: matchLabels: k8s-app: kubernetes-dashboard template: metadata: labels: k8s-app: kubernetes-dashboard spec: containers: - name: kubernetes-dashboard image: kubernetesui/dashboard:v2.0.0-beta4 imagePullPolicy: Always ports: - containerPort: 8443 protocol: TCP args: - --auto-generate-certificates - --namespace=kubernetes-dashboard # Uncomment the following line to manually specify Kubernetes API server Host # If not specified, Dashboard will attempt to auto discover the API server and connect # to it. Uncomment only if the default does not work. # - --apiserver-host=http://my-address:port volumeMounts: - name: kubernetes-dashboard-certs mountPath: /certs # Create on-disk volume to store exec logs - mountPath: /tmp name: tmp-volume livenessProbe: httpGet: scheme: HTTPS path: / port: 8443 initialDelaySeconds: 30 timeoutSeconds: 30 volumes: - name: kubernetes-dashboard-certs secret: secretName: kubernetes-dashboard-certs - name: tmp-volume emptyDir: {} serviceAccountName: kubernetes-dashboard # Comment the following tolerations if Dashboard must not be deployed on master tolerations: - key: node-role.kubernetes.io/master effect: NoSchedule --- kind: Service apiVersion: v1 metadata: labels: k8s-app: dashboard-metrics-scraper name: dashboard-metrics-scraper namespace: kubernetes-dashboard spec: ports: - port: 8000 targetPort: 8000 selector: k8s-app: dashboard-metrics-scraper --- kind: Deployment apiVersion: apps/v1 metadata: labels: k8s-app: dashboard-metrics-scraper name: dashboard-metrics-scraper namespace: kubernetes-dashboard spec: replicas: 1 revisionHistoryLimit: 10 selector: matchLabels: k8s-app: dashboard-metrics-scraper template: metadata: labels: k8s-app: dashboard-metrics-scraper spec: containers: - name: dashboard-metrics-scraper image: kubernetesui/metrics-scraper:v1.0.1 ports: - containerPort: 8000 protocol: TCP livenessProbe: httpGet: scheme: HTTP path: / port: 8000 initialDelaySeconds: 30 timeoutSeconds: 30 volumeMounts: - mountPath: /tmp name: tmp-volume serviceAccountName: kubernetes-dashboard # Comment the following tolerations if Dashboard must not be deployed on master tolerations: - key: node-role.kubernetes.io/master effect: NoSchedule volumes: - name: tmp-volume emptyDir: {}
运行pod
kubectl apply -f dashboard.yaml
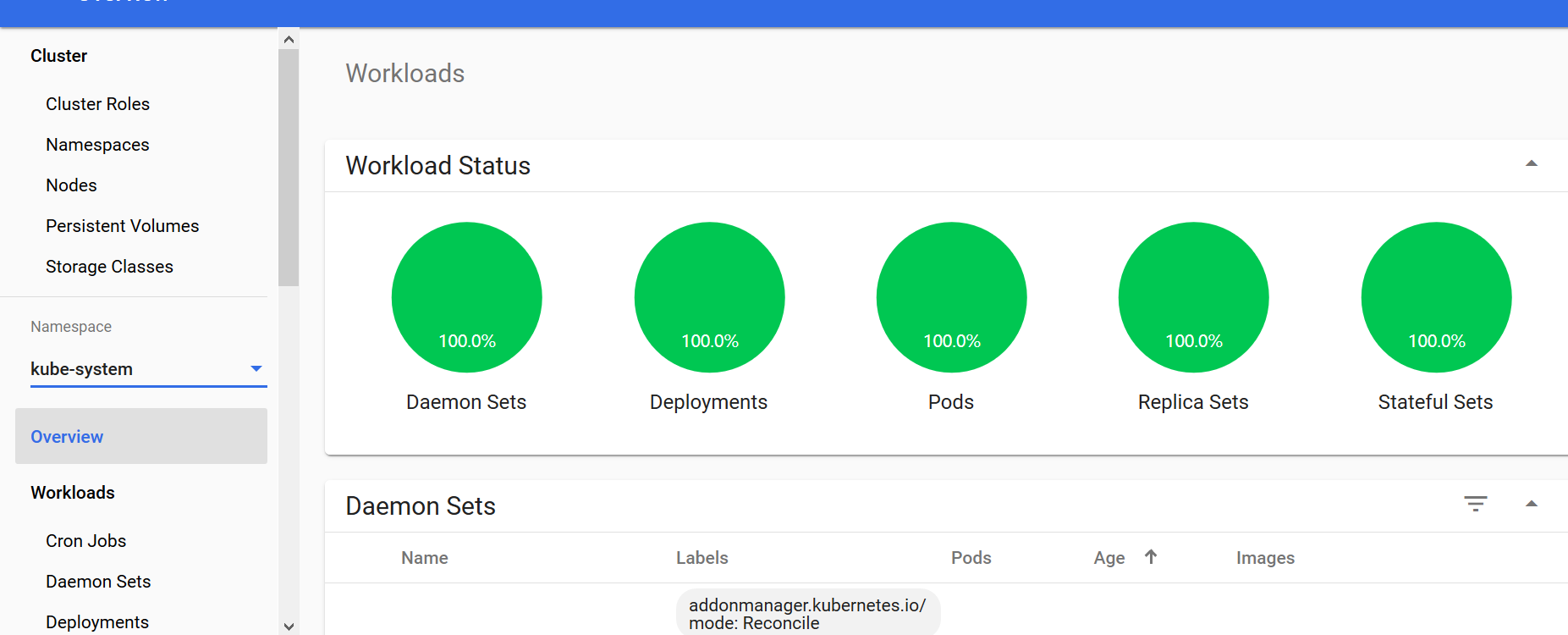
查看pod的运行情况
kubectl get pods -n kubernetes-dashboard
(base) [root@test-bd-k8s01 nfs]# kubectl get pods -n kube-system
NAME READY STATUS RESTARTS AGE
calico-node-b5f8c 2/2 Running 4 20d
calico-node-kjttm 2/2 Running 2 20d
calico-node-q6hqq 2/2 Running 2 20d
coredns-5c98db65d4-szrbq 1/1 Running 2 20d
coredns-5c98db65d4-xfccf 1/1 Running 2 20d
dashboard-metrics-scraper-fb986f88d-nd9d6 1/1 Running 0 47h
etcd-test-bd-k8s01 1/1 Running 2 20d
kube-apiserver-test-bd-k8s01 1/1 Running 2 20d
kube-controller-manager-test-bd-k8s01 1/1 Running 5 7d6h
kube-proxy-w557n 1/1 Running 2 20d
kube-proxy-z9m7r 1/1 Running 2 20d
kube-proxy-zp4jf 1/1 Running 3 20d
kube-scheduler-test-bd-k8s01 1/1 Running 4 7d6h
1/1 Running 2 47h
nfs-client-provisioner-67ddcf968c-hsqhz 1/1 Running 0 2d4h
node-exporter-46djx 1/1 Running 0 6d6h
node-exporter-nhfk2 1/1 Running 0 6d6h
prometheus-0 2/2 Running 0 2d4h
如果处于running状态,要在看一下他的log日志
kubectl logs -f kubernetes-dashboard-cdbc9547c-7sb2n -n kubernetes-dashboard
kubectl logs -f dashboard-metrics-scraper-fb986f88d-nd9d6 -n kubernetes-dashboard
如果两个日志里都没有报错在去查看一下端口号
kubectl get svc -n kube-system (base) [root@test-bd-k8s01 nfs]# kubectl get svc -n kube-system NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE calico-typha ClusterIP 10.107.187.43 <none> 5473/TCP 20d dashboard-metrics-scraper ClusterIP 10.99.80.90 <none> 8000/TCP 47h kube-dns ClusterIP 10.96.0.10 <none> 53/UDP,53/TCP,9153/TCP 20d kube-state-metrics ClusterIP 10.108.232.162 <none> 8080/TCP,8081/TCP 4d kubernetes-dashboard NodePort 10.99.23.34 <none> 443:30001/TCP 47h prometheus NodePort 10.103.233.151 <none> 9090:30090/TCP 2d4h
然后再看一下30001端口是否存在
(base) [root@test-bd-k8s01 nfs]# netstat -nlp |grep 30001 tcp6 0 0 :::30001 :::* LISTEN 3322/kube-proxy
以上工作都完成了说明基本上可以启动了
要用https://IP:30001 输入火狐浏览器
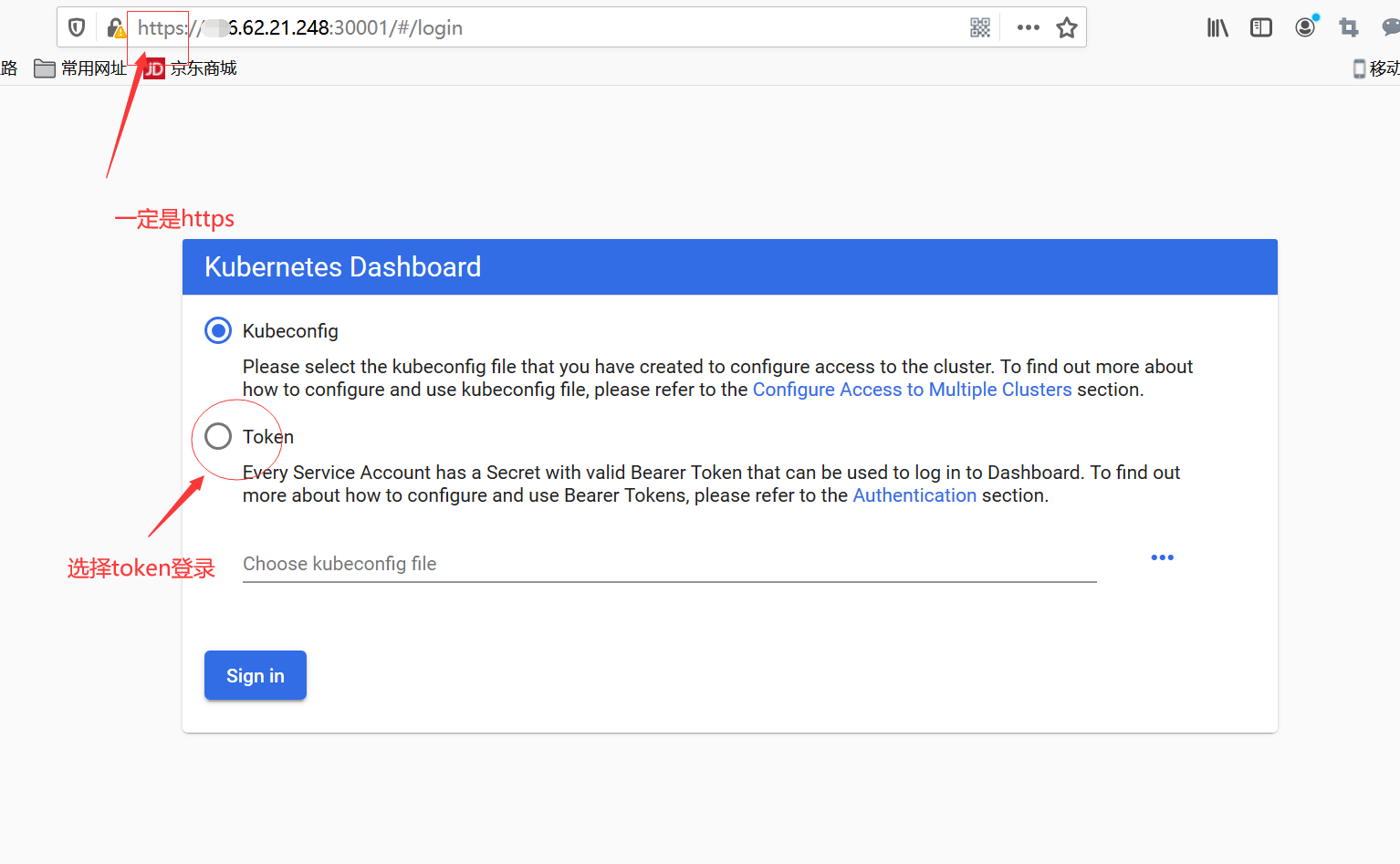
获取token的步骤
创建一个账户
vim k8s-admin.yaml
apiVersion: v1 kind: ServiceAccount metadata: name: dashboard-admin namespace: kube-system --- kind: ClusterRoleBinding apiVersion: rbac.authorization.k8s.io/v1beta1 metadata: name: dashboard-admin subjects: - kind: ServiceAccount name: dashboard-admin namespace: kube-system roleRef: kind: ClusterRole name: cluster-admin apiGroup: rbac.authorization.k8s.io kubectl get secret -n kube-system |grep dashboard-admin
kubectl apply -f k8s-admin.yaml
kubectl get secret -n kube-system |grep dashboard-admin
(base) [root@test-bd-k8s01 nfs]# kubectl get secret -n kube-system |grep dashboard-admin dashboard-admin-token-nhrx9 kubernetes.io/service-account-token 3 4d3h istio.dashboard-admin istio.io/key-and-cert 3 4d3h (base) [root@test-bd-k8s01 nfs]# kubectl describe secret dashboard-admin-token-nhrx9 -n kube-system Name: dashboard-admin-token-nhrx9 Namespace: kube-system Labels: <none> Annotations: kubernetes.io/service-account.name: dashboard-admin kubernetes.io/service-account.uid: 04a05717-ce9a-4403-a14b-5e2f1c8b2f75 Type: kubernetes.io/service-account-token Data ==== ca.crt: 1025 bytes namespace: 11 bytes token: eyJhbGciOiJSUaI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tbmhyeDkiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiMDRhMDU3MTctY2U5YS00NDAzLWExNGItNWUyZjFjOGIyZjc1Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.Krd2HTgQJiKIiRWMqDIVCRKTdEnTS8IPwGbTi_unzrwY-9Da8SQ1HaYxiomA_m4AtyRXGQ-S9Tnh02PFzQdjlFmSpWy0LqofYSLiaR3OeA19nVEFnx-61K1w9rTTmBjT-eqUPALOw44n352YOQnGyPfAhaovzegvMrY4qQi1uQ74FsZWrtIq0DZWGU3guKDjcJZC5PAl9_1wqRF7__OpEA_3EeINxBPyhcIZZtyDrQznlDRkYlHClVy_SwKqRtwOfD5IH7xj0hKT0p9u0aigx3Xj4RiJhmC-4e1HYJp-XYQTwYpdhBMys93RnKhVQgJe8psL7bifT-2mDX7JkTCAQw
然后把获得的token复制到web页面中就完成了