一、SSH 端口转发能够提供两大功能:
1.加密SSH Client 端至SSH Server 端之间的通讯数据
2.突破防火墙的限制完成一些之前无法建立的TCP 连接 (隧道功能)
二:SSH端口本地转发
运用场景图:
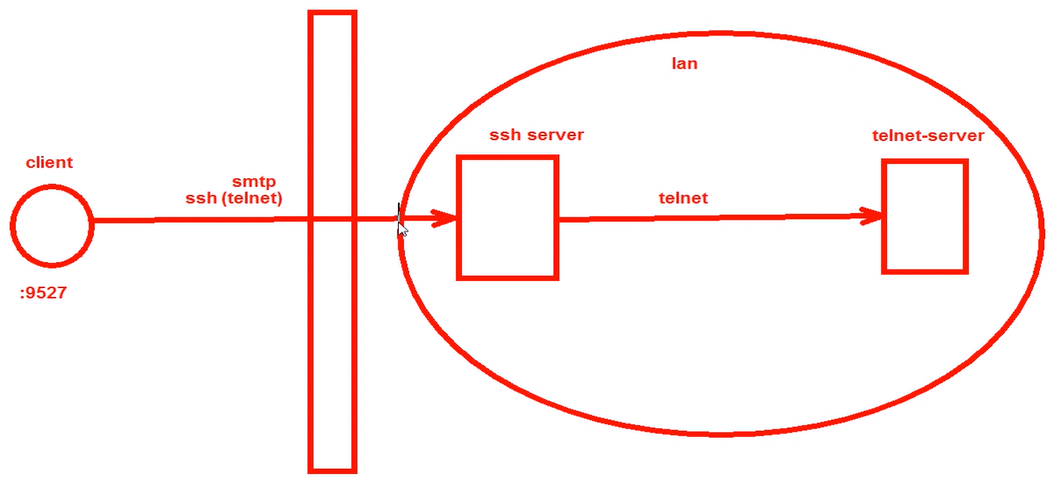
-L localport:remotehost:remotehostportsshserver
选项: -f 后台启用 -N 不打开远程shell,处于等待状态 -g 启用网关功能
比如:
ssh –L 9527:telnetsrv:23 -N sshsrv
telnet 127.0.0.1 9527
当访问本机的9527的端口时,被加密后转发到sshsrv的ssh服务,再解密被转发到telnetsrv:23
data < >localhost:9527 < > localhost:XXXXX < > sshsrv:22 < > sshrv:yyyyy < > telnetsrv:23
[root@telnetserver ~]# iptables -A INPUT -s 192.168.40.132 -j REJECT
[root@telnetserver ~]# yum install -y telnet-server
[root@telnetserver ~]# systemctl start telnet.socket
[root@telnetserver ~]# systemctl start telnet.socket
[root@sshserver ~]# yum install -y telnet-server.x86_64
[root@sshserver ~]# systemctl start telnet.socket
[root@client ~]# ssh -L 9527:192.168.40.155:23 192.168.40.211 (自己给自己搭建隧道)
The authenticity of host '192.168.40.211 (192.168.40.211)' can't be established.
ECDSA key fingerprint is SHA256:pNJw/K2ipf4PO9OZtkTmisNZ+ctpN02yRIMxTvNGlrA.
ECDSA key fingerprint is MD5:42:0a:fb:3f:74:1f:12:fc:f1:6a:20:00:43:0a:0f:c3.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.40.211' (ECDSA) to the list of known hosts.
root@192.168.40.211's password:
Last login: Sun Oct 6 12:58:31 2019 from 192.168.40.1
The authenticity of host '192.168.40.211 (192.168.40.211)' can't be established.
ECDSA key fingerprint is SHA256:pNJw/K2ipf4PO9OZtkTmisNZ+ctpN02yRIMxTvNGlrA.
ECDSA key fingerprint is MD5:42:0a:fb:3f:74:1f:12:fc:f1:6a:20:00:43:0a:0f:c3.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.40.211' (ECDSA) to the list of known hosts.
root@192.168.40.211's password:
Last login: Sun Oct 6 12:58:31 2019 from 192.168.40.1
[root@sshserver ~]# ss -nt
State Recv-Q Send-Q Local Address:Port Peer Address:Port
ESTAB 0 0 192.168.40.211:22 192.168.40.1:50804
ESTAB 0 0 192.168.40.211:22 192.168.40.132:46418
State Recv-Q Send-Q Local Address:Port Peer Address:Port
ESTAB 0 0 192.168.40.211:22 192.168.40.1:50804
ESTAB 0 0 192.168.40.211:22 192.168.40.132:46418
[root@sshserver ~]# yum install -y telnet (安装telnet命令)
[root@client ~]# telnet 127.0.0.1 9527 (本地转发)
Trying 127.0.0.1...
Connected to 127.0.0.1.
Escape character is '^]'.
Kernel 3.10.0-693.el7.x86_64 on an x86_64
telnetserver login: aa
Password:
[aa@telnetserver ~]$ (登录成功)
[root@client ~]# telnet 127.0.0.1 9527 (本地转发)
Trying 127.0.0.1...
Connected to 127.0.0.1.
Escape character is '^]'.
Kernel 3.10.0-693.el7.x86_64 on an x86_64
telnetserver login: aa
Password:
[aa@telnetserver ~]$ (登录成功)
[root@client ~]# ssh -L 9527:192.168.40.155:23 -Nf 192.168.40.211 (更方便)
root@192.168.40.211's password:
[root@client ~]#
[root@sshserver ~]# ss -nt
State Recv-Q Send-Q Local Address:Port Peer Address:Port
ESTAB 0 52 192.168.40.211:22 192.168.40.1:50804
ESTAB 0 0 192.168.40.211:22 192.168.40.132:46448
root@192.168.40.211's password:
[root@client ~]#
[root@sshserver ~]# ss -nt
State Recv-Q Send-Q Local Address:Port Peer Address:Port
ESTAB 0 52 192.168.40.211:22 192.168.40.1:50804
ESTAB 0 0 192.168.40.211:22 192.168.40.132:46448
三:SSH端口远程转发
运用场景图:
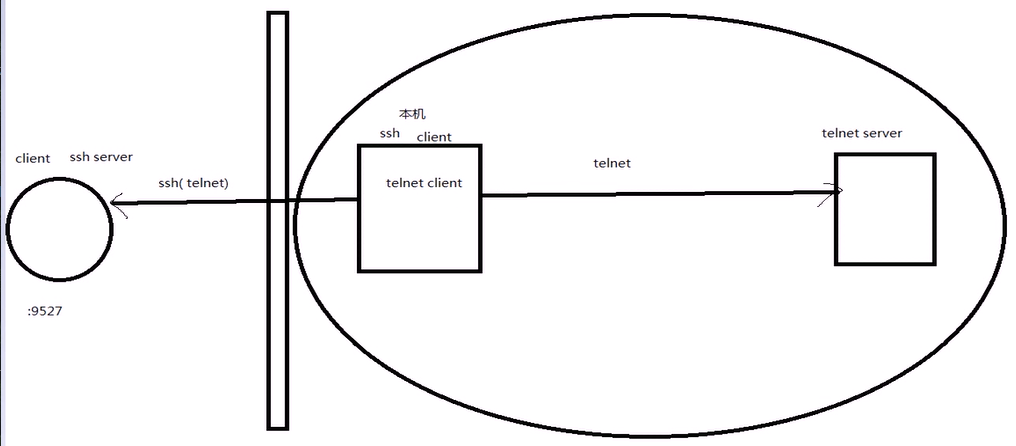
远程转发机制:
-R sshserverport:remotehost:remotehostportsshserver
例如:ssh–R 9527:telnetsrv:23 –N sshsrv
让ssh机子侦听9527端口的访问,如有访问,就加密后通过ssh服务转发请求到本机ssh客户端,再由本机解密后转发到telnet:23
Data < > internet:9527 < > internet:22 < > ssh:XXXXX < > ssh:YYYYY< >telnetsrv:23
[root@lanserver ~]# ssh -R 9527:192.168.40.155:23 192.168.40.211 (给internet搭建隧道)
root@192.168.40.211's password:
Last login: Sun Oct 6 13:45:44 2019 from 192.168.40.1
root@192.168.40.211's password:
Last login: Sun Oct 6 13:45:44 2019 from 192.168.40.1
[root@internet ~]# ss -ntl
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 128 *:22 *:*
LISTEN 0 128 127.0.0.1:9527 *:*
LISTEN 0 100 127.0.0.1:25 *:*
LISTEN 0 128 :::22 :::*
LISTEN 0 128 ::1:9527 :::*
LISTEN 0 100 ::1:25
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 128 *:22 *:*
LISTEN 0 128 127.0.0.1:9527 *:*
LISTEN 0 100 127.0.0.1:25 *:*
LISTEN 0 128 :::22 :::*
LISTEN 0 128 ::1:9527 :::*
LISTEN 0 100 ::1:25
[root@internet ~]# telnet 127.0.0.1 9527
Trying 127.0.0.1...
Connected to 127.0.0.1.
Escape character is '^]'.
telnetserver login: aa
Password:
Last login: Sun Oct 6 01:21:13 from localhost
[aa@telnetserver ~]$
Trying 127.0.0.1...
Connected to 127.0.0.1.
Escape character is '^]'.
telnetserver login: aa
Password:
Last login: Sun Oct 6 01:21:13 from localhost
[aa@telnetserver ~]$
[root@telnetserver ~]# ss -nt (服务端察觉不到是internet在连接)
State Recv-Q Send-Q Local Address:Port Peer Address:Port
ESTAB 0 52 192.168.40.155:22 192.168.40.1:50809
ESTAB 0 0 ::ffff:192.168.40.155:23 ::ffff:192.168.40.211:36364
State Recv-Q Send-Q Local Address:Port Peer Address:Port
ESTAB 0 52 192.168.40.155:22 192.168.40.1:50809
ESTAB 0 0 ::ffff:192.168.40.155:23 ::ffff:192.168.40.211:36364
四:SSH动态端口转发
运用场景图: (翻墙,ss国外服务器做代理)
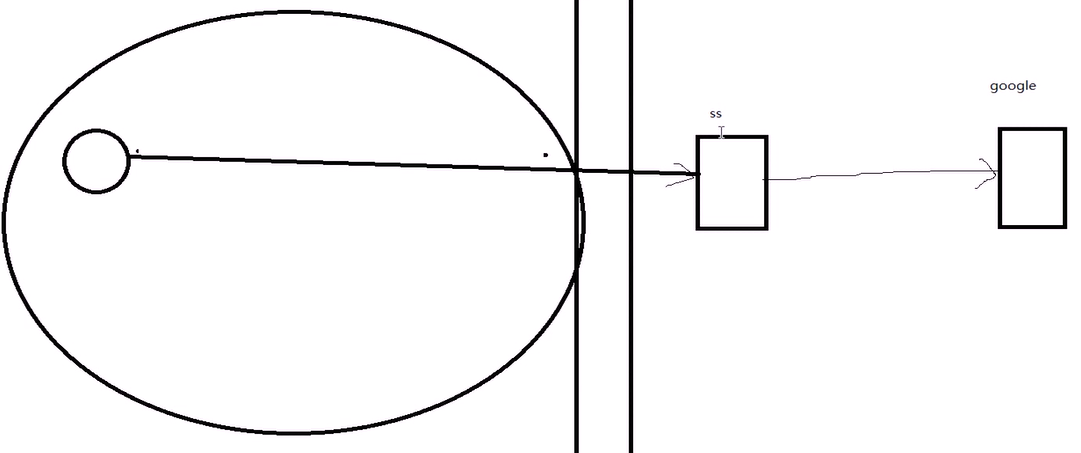
原理:
当用firefox访问internet时,本机的1080端口做为代理服务器,firefox的访问请求被转发到sshserver上,由sshserver替之 访问internet
动态转发机制:
ssh-D 1080 root@sshserver
在本机firefox设置代理socket proxy:127.0.0.1:1080
测试:
curl --socks5 127.0.0.1:1080 http://zangfans.com
在企业内部或者网络中,基于安全策略不能随便访问互联网某些站点
[root@google ~]# echo www.google.com > /var/www/html/index.html
[root@google ~]# systemctl restart httpd
[root@google ~]# systemctl restart httpd
[root@google ~]# iptables -vnL
Chain INPUT (policy ACCEPT 78337 packets, 18M bytes)
pkts bytes target prot opt in out source destination
3 252 REJECT all -- * * 192.168.40.132 0.0.0.0/0 reject-with icmp-port-unreachable (挡住132)
[root@internet ~]# ssh -D 1080 root@192.168.40.211 (自己给自己搭建隧道)
root@192.168.40.211's password:
Last login: Sun Oct 6 14:31:08 2019 from 192.168.40.1
[root@proxy ~]#
Chain INPUT (policy ACCEPT 78337 packets, 18M bytes)
pkts bytes target prot opt in out source destination
3 252 REJECT all -- * * 192.168.40.132 0.0.0.0/0 reject-with icmp-port-unreachable (挡住132)
[root@internet ~]# ssh -D 1080 root@192.168.40.211 (自己给自己搭建隧道)
root@192.168.40.211's password:
Last login: Sun Oct 6 14:31:08 2019 from 192.168.40.1
[root@proxy ~]#
[root@internet ~机子配置火狐代理省略
# curl --socks5 127.0.0.1:1080 192.168.40.155 #默认端口就是1080,可以不写
www.google.comhttps://mp.weixin.qq.com/s/SX88e_4B96jiUuqF5joGcQ 有待整理!!!
https://blog.csdn.net/fdipzone/article/details/23000201 ssh远程执行命令并自动退出