为什么,要写这篇论文?
是因为,目前科研的我,正值研三,致力于网络安全、大数据、机器学习研究领域!
论文方向的需要,同时不局限于真实物理环境机器实验室的攻防环境、也不局限于真实物理机器环境实验室的大数据集群平台。在此,为了需要的博友们,能在自己虚拟机里(我这里是CentOS6.5)来搭建部署snort+barnyard2+base的入侵检测系统。分享与交流是进步的阶梯!
同时,本人还尝试过在Ubuntu14.04里搭建这入侵检测系统的环境。同时,还尝试过在win7win10里搭建这入侵检测系统的环境。
同时,也欢迎做报警数据方向的烟酒僧留言评论加好友交流。欢迎指正!谢谢。
base和acid的关系

同时,
最佳安全工具100款
http://www.92to.com/bangong/2016/04-08/2996883.html
用于分析Snort 警报的网页形式的引擎 Basic Analysis and Security Engine (BASE)可免费获得。
原来,这里面也有base。
VMware下OSSIM 5.2.0的下载、安装和初步使用(图文详解)
在Ubuntu和CentOS里,用base居多。
在windows里,用acid居多。但是,我这篇博客,acid和base都演示。(反而我更喜欢用base)
见
基于Windows7下snort+apache+php 7 + acid(或者base) + adodb + jpgraph的入侵检测系统的搭建(图文详解)(博主推荐)
一、准备工作
安装CentOS-6.5-x86_64-bin-DVD1.iso(用CentOS7后面配置base会报错),给系统设置IP和dns让系统可以联网.

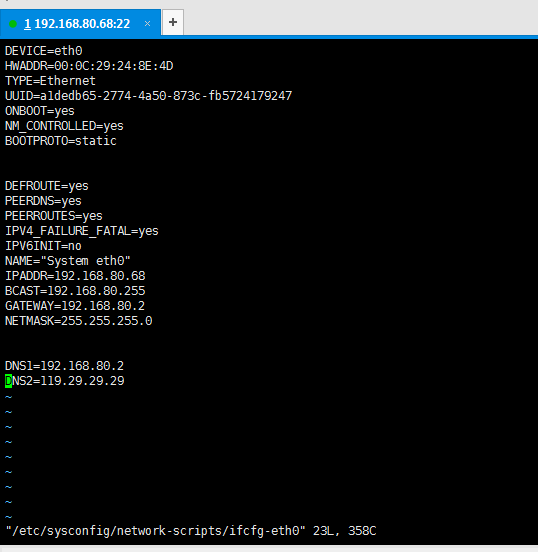
DEVICE=eth0 HWADDR=00:0C:29:24:8E:4D TYPE=Ethernet UUID=a1dedb65-2774-4a50-873c-fb5724179247 ONBOOT=yes NM_CONTROLLED=yes BOOTPROTO=static DEFROUTE=yes PEERDNS=yes PEERROUTES=yes IPV4_FAILURE_FATAL=yes IPV6INIT=no NAME="System eth0" IPADDR=192.168.80.68 BCAST=192.168.80.255 GATEWAY=192.168.80.2 NETMASK=255.255.255.0 DNS1=192.168.80.2 DNS2=119.29.29.29
注意,以下操作,都是在root用户下进行。
1. 安装wget
[root@datatest ~]# yum install wget -y
2. 更换源
更换成阿里云源,更新系统、下载软件速度快
[root@datatest ~]# mv /etc/yum.repos.d/CentOS-Base.repo /etc/yum.repos.d/CentOS-Base.repo.backup
[root@datatest ~]# wget -O /etc/yum.repos.d/CentOS-Base.repo http://mirrors.aliyun.com/repo/Centos-6.repo
[root@datatest ~]# yum clean all
[root@datatest ~]# yum makecache
3.更新系统
[root@datatest ~]# yum -y update
4.安装epel源
[root@datatest ~]# yum install -y epel-release
5.下载安装文件
把网盘里的安装文件下载到CentOS里备用(可以利用附件中的FTPServer.exe传输),这里放到/root
相关文件下载:http://pan.baidu.com/s/1mgzYhO8(感谢这位贡献者)
二、安装配置LMAP
1.安装LMAP组件
[root@datatest ~]# yum install -y httpd mysql-server php php-mysql php-mbstring php-mcrypt mysql-devel php-gd
2.安装php插件
[root@datatest ~]# yum install -y mcrypt libmcrypt libmcrypt-devel
3.安装pear插件
[root@datatest ~]# yum install -y php-pear
[root@datatest ~]# pear upgrade pear
[root@datatest ~]# pear channel-update pear.php.net
[root@datatest ~]# pear install mail
[root@datatest ~]# pear install Image_Graph-alpha Image_Canvas-alpha Image_Color Numbers_Roman
[root@datatest ~]# pear install mail_mime
4.安装adodb
[root@datatest ~]# tar zxvf adodb519.tar.gz -C /var/www/html
[root@datatest ~]# mv /var/www/html/adodb5 /var/www/html/adodb
5.安装base
[root@datatest ~]# tar zxvf base-1.4.5.tar.gz -C /var/www/html
[root@datatest ~]# mv /var/www/html/base-1.4.5 /var/www/html/base
6.修改php.ini
[root@datatest ~]# vi /etc/php.ini
error_reporting = E_ALL & ~E_NOTICE
7.设置html目录权限
[root@datatest ~]# chown -R apache:apache /var/www/html
8.设置adodb权限
[root@datatest ~]# chmod 755 /var/www/html/adodb
9.配置mysql
解压barnyard2(这里因为,后面我们要用里面的文件创mysql表)
[root@datatest ~]# tar zxvf barnyard2-1.9.tar.gz
启动mysql
[root@datatest ~]# service mysqld start
设置root密码为root
[root@datatest ~]# mysqladmin -u root -p password root
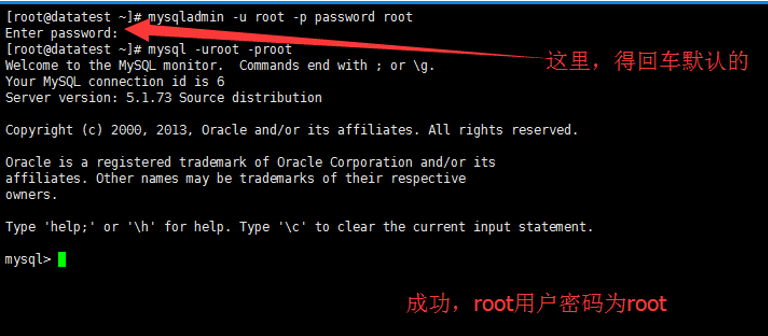
以root登陆mysql
[root@datatest ~]# mysql -uroot -proot
创建名为snort的数据库
[root@datatest ~]# create database snort;
创建名为snort、密码为snort的数据库用户并赋予名为snort数据库权限
> grant create,select,update,insert,delete on snort.* to snort@localhost identified by 'snort';
> exit
创建数据库表
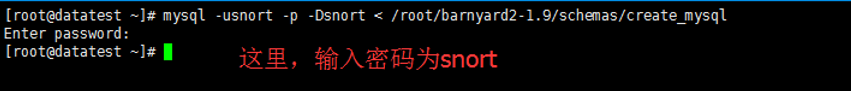
[root@datatest ~]# mysql -usnort -p -Dsnort < /root/barnyard2-1.9/schemas/create_mysql
10.配置base
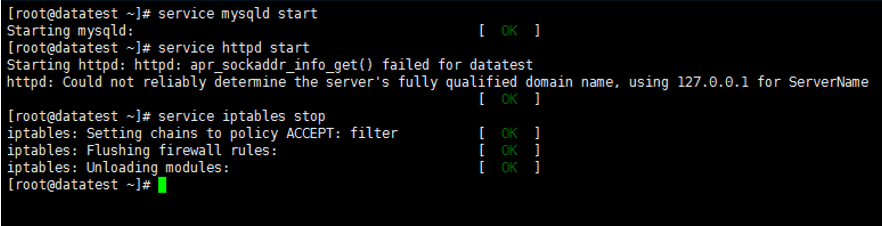
#service mysqld start 启动mysql
#service httpd start 启动apache
#service iptables stop 关闭防火墙
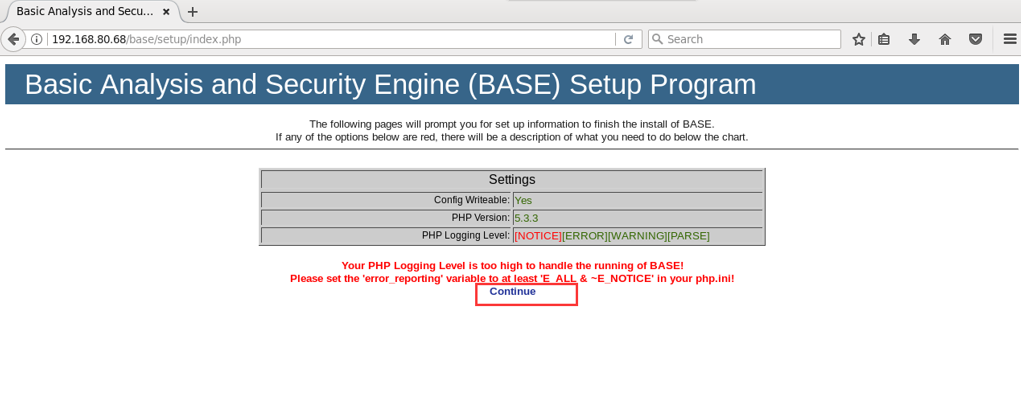
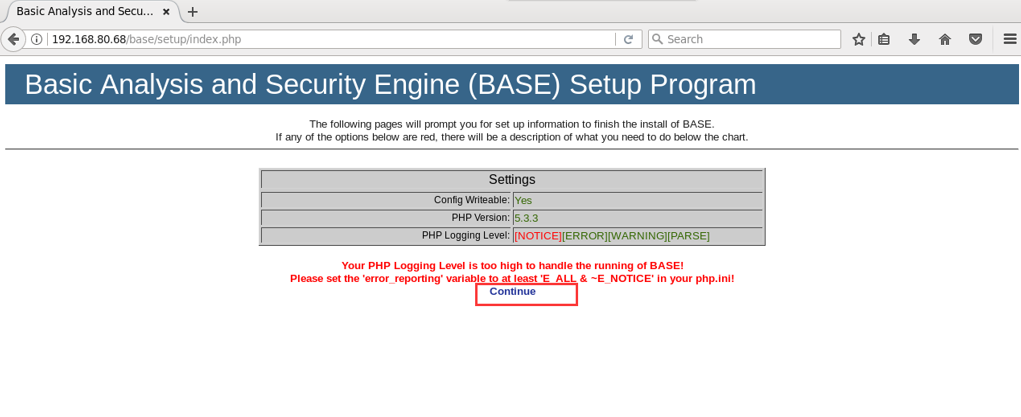
用Centos里的浏览器或者windows里的浏览器。都可以,打开http://192.168.80.68/base/setup/index.php(IP换成你自己的)
1.点击Continuue(如下,我CentOS里的浏览器和windows里的浏览器,都截图给大家展示)
2.选择显示语言,设置adodb路径
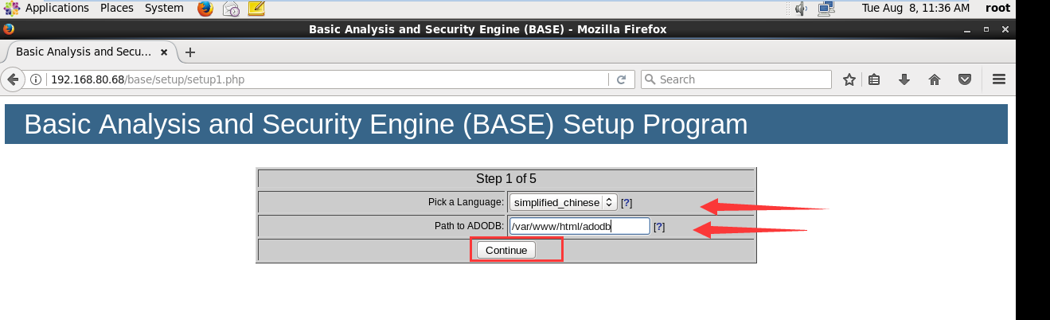
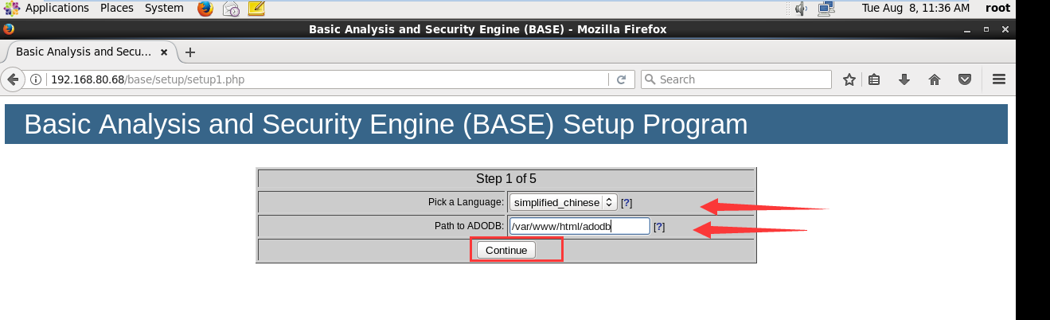
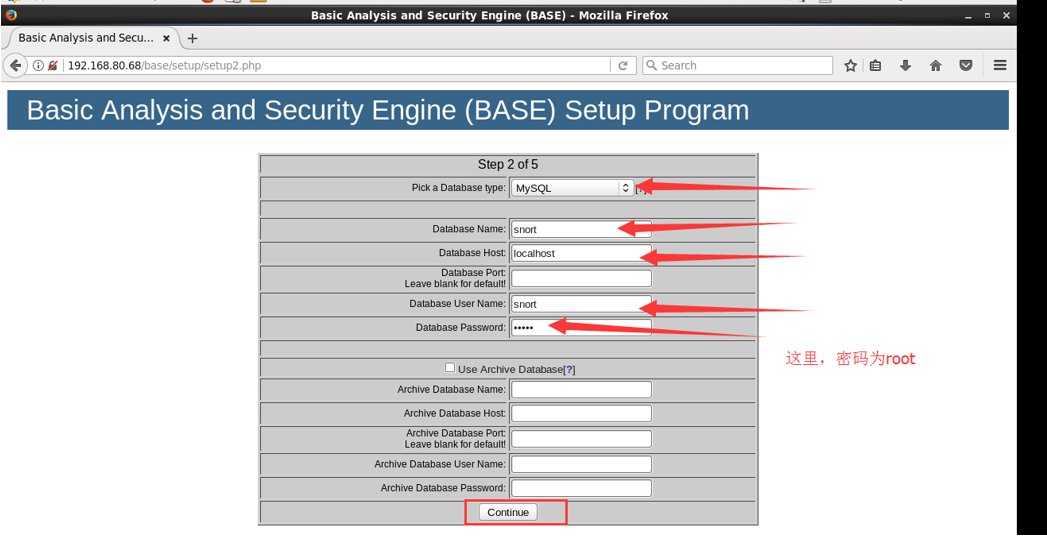
3.配置数据库

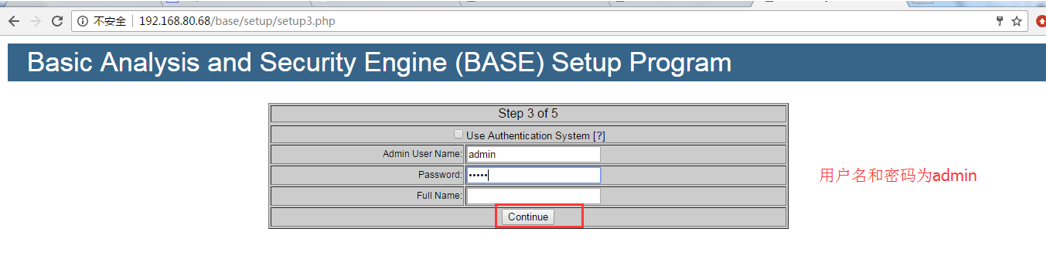
4.设置admin用户和密码(这里应该是设置admin的用户和密码,我这里是admin)

5.点击“Createe BASE AG”
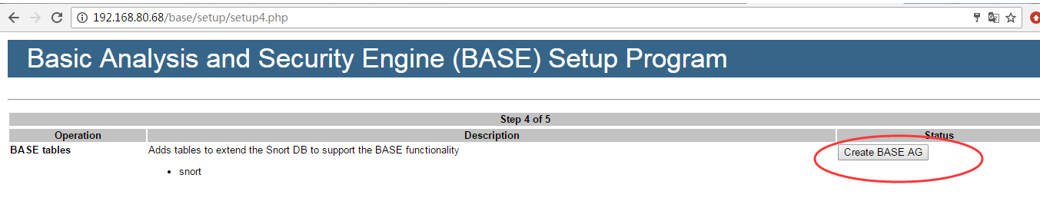
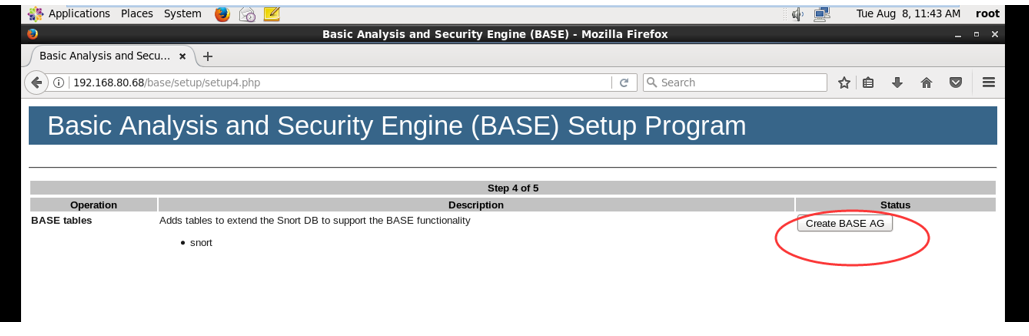
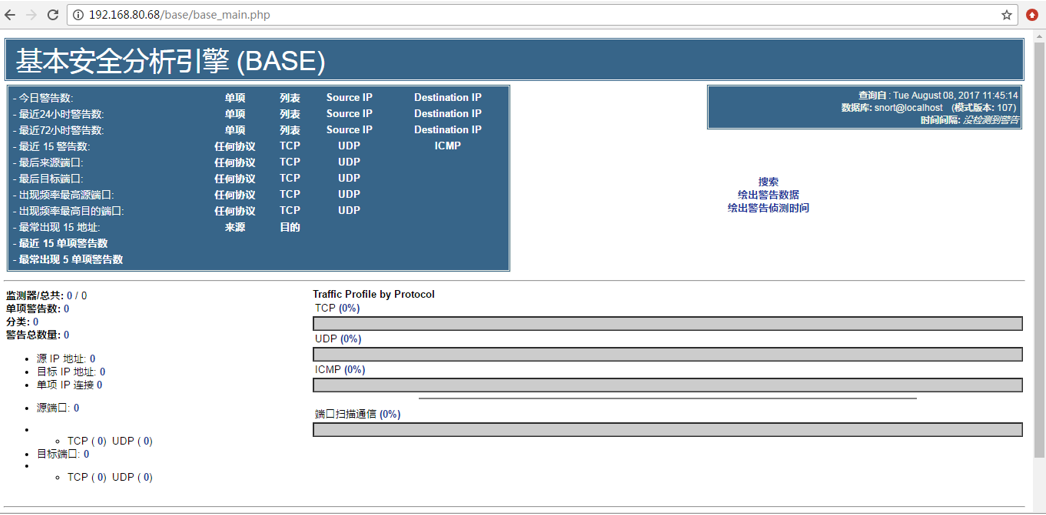
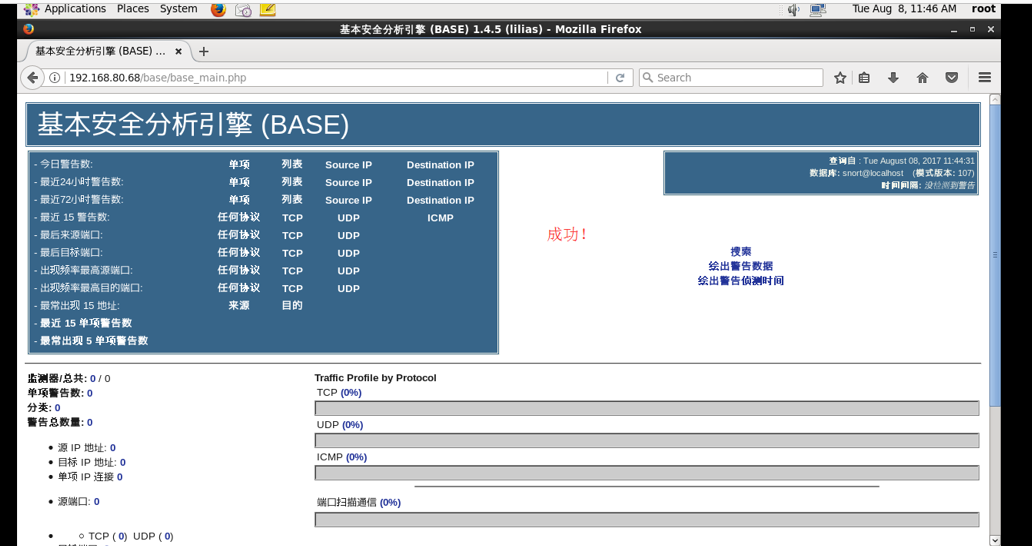
6.成功的话会有红色successfilly created字样,如下图(Centos7没有,原因未知),点击“step 5”


7.安装成功
三、安装配置snort+barnyard2
1.安装依赖包
[root@datatest ~]# yum install -y gcc flex bison zlib libpcap tcpdump gcc-c++ pcre* zlib* libdnet libdnet-devel
2.安装libdnet(这里必须是这个版本)
[root@datatest ~]# tar zxvf libdnet-1.12.tgz
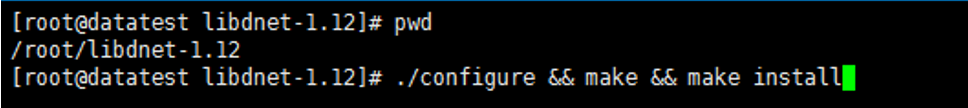
[root@datatest ~]# cd libdnet-1.12
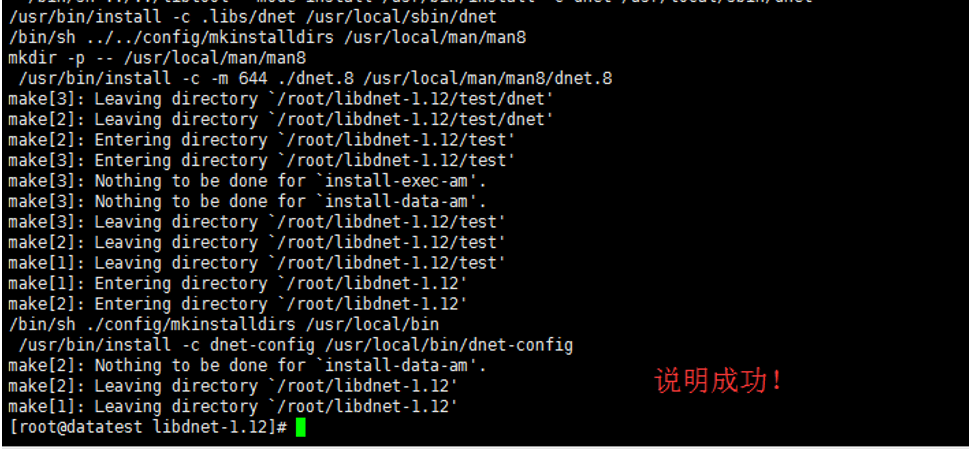
[root@datatest ~]# ./configure && make && make install
3.安装libpcap
[root@datatest ~]# wget http://www.tcpdump.org/release/libpcap-1.0.0.tar.gz
[root@datatest ~]# tar zxvf libpcap-1.0.0.tar.gz
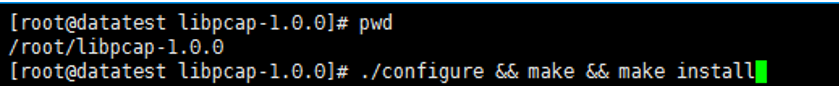
[root@datatest ~]# cd libpcap-1.0.0
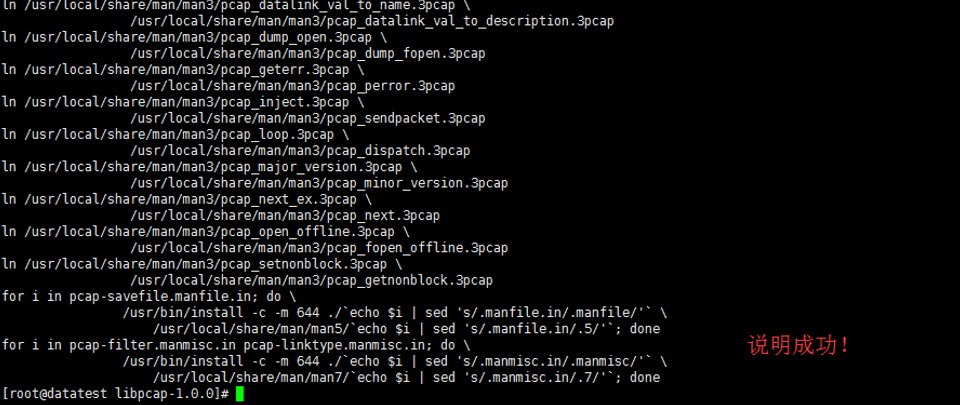
[root@datatest ~]# ./configure && make && make install
4.安装DAQ
[root@datatest ~]# tar zxvf daq-2.0.4.tar.gz
[root@datatest ~]# cd daq-2.0.4
[root@datatest ~]# ./configure && make && make install

5.安装snort
[root@datatest ~]# tar zxvf snort-2.9.7.0.tar.gz
[root@datatest ~]# cd snort-2.9.7.0
[root@datatest ~]# ./configure && make && make install
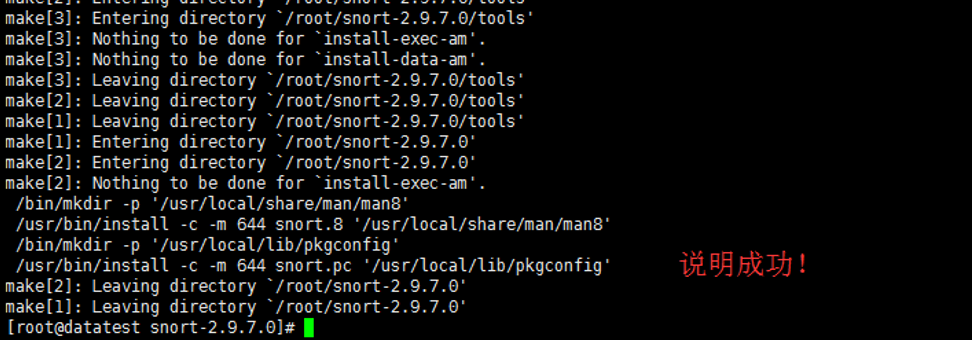
6.配置snort
创建需要的文件和目录
[root@datatest ~]# mkdir /etc/snort
[root@datatest ~]# mkdir /var/log/snort
[root@datatest ~]# mkdir /usr/local/lib/snort_dynamicrules
[root@datatest ~]# mkdir /etc/snort/rules
[root@datatest ~]# touch /etc/snort/rules/white_list.rules /etc/snort/rules/black_list.rules
[root@datatest ~]# cp /root/snort-2.9.7.0/etc/gen-msg.map /root/snort-2.9.7.0/etc/threshold.conf /root/snort-2.9.7.0/etc/classification.config /root/snort-2.9.7.0/etc/reference.config /root/snort-2.9.7.0/etc/unicode.map /root/snort-2.9.7.0/etc/snort.conf /etc/snort/ cp: overwrite `/etc/snort/gen-msg.map'? y cp: overwrite `/etc/snort/threshold.conf'? y cp: overwrite `/etc/snort/classification.config'? y cp: overwrite `/etc/snort/reference.config'? y cp: overwrite `/etc/snort/unicode.map'? y

编辑配置文件
[root@datatest ~]# vi /etc/snort/snort.conf
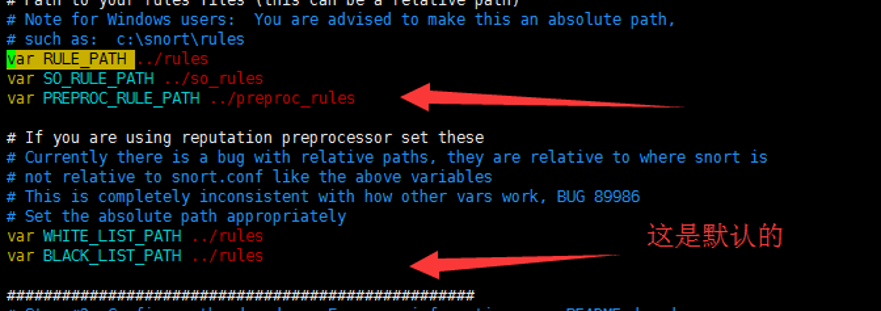
修改路径变量
var RULE_PATH /etc/snort/rules var SO_RULE_PATH /etc/snort/so_rules var PREPROC_RULE_PATH /etc/snort/preproc_rules var WHITE_LIST_PATH /etc/snort/rules var BLACK_LIST_PATH /etc/snort/rules

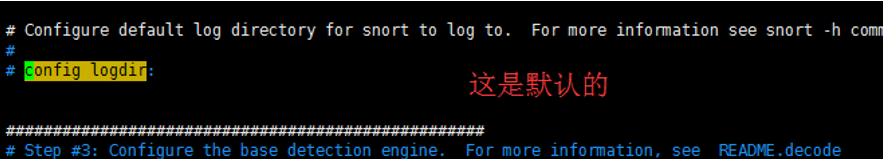
设置log目录
config logdir:/var/log/snort

配置输出插件
output unified2:filename snort.log,limit 128
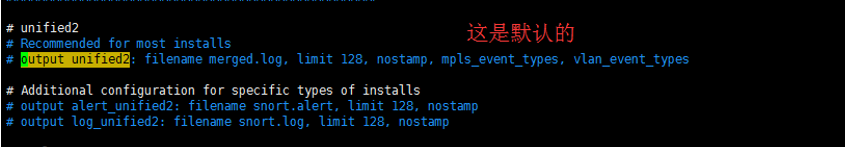
#output unified2: filename merged.log, limit 128, nostamp, mpls_event_types, vlan_event_types
改为

7.配置默认规则
[root@datatest ~]# tar zxvf snortrules-snapshot-2970.tar.gz -C /etc/snort/
如果没有,用snortrules-snapshot-2980.tar.gz 或者 snortrules-snapshot-2990.tar.gz。
然后,执行
cp /etc/snort/etc/sid-msg.map /etc/snort/
8.测试snort
[root@datatest ~]# snort -T -i eth0 -c /etc/snort/snort.conf
因为,之前,我配置的是eth0网卡。
参数解释:
-T 指定启动模式:测试
-i 指定网络接口
-c 指定配置文件
如果出现“success”的字样说明配置好了。
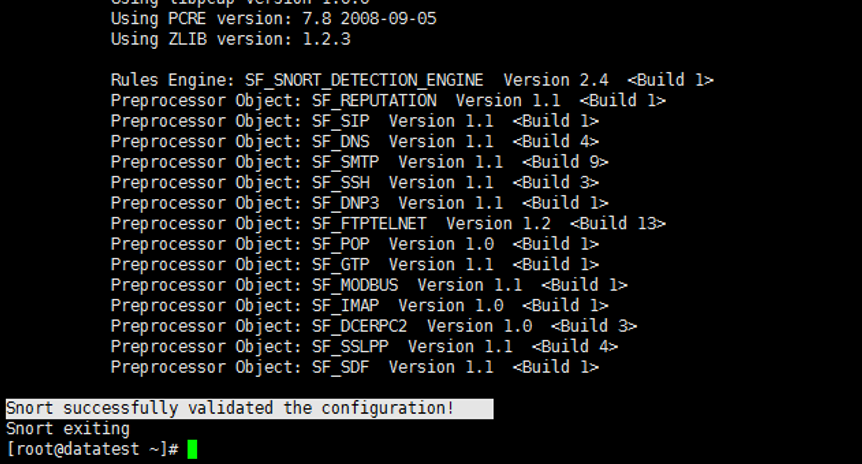
按ctrl+c终止snort测试就好。
9.安装barnyard2
[root@datatest ~]# cd /root/barnyard2-1.9
[root@datatest ~]# ./configure --with-mysql --with-mysql-libraries=/usr/lib64/mysql/
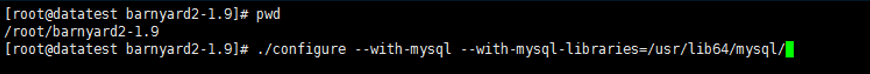
然后,执行
[root@datatest ~]# make && make install
10.配置barnyard2
创建需要的文件和目录
[root@datatest ~]# mkdir /var/log/barnyard2
[root@datatest ~]# touch /var/log/snort/barnyard2.waldo
[root@datatest ~]# cp /root/barnyard2-1.9/etc/barnyard2.conf /etc/snort
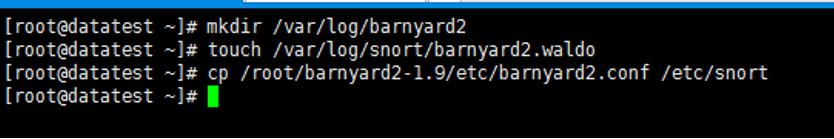
修改配置文件
[root@datatest ~]# vi /etc/snort/barnyard2.conf
[root@datatest ~]# config logdir:/var/log/barnyard2

config hostname:localhost
config interface:eth0
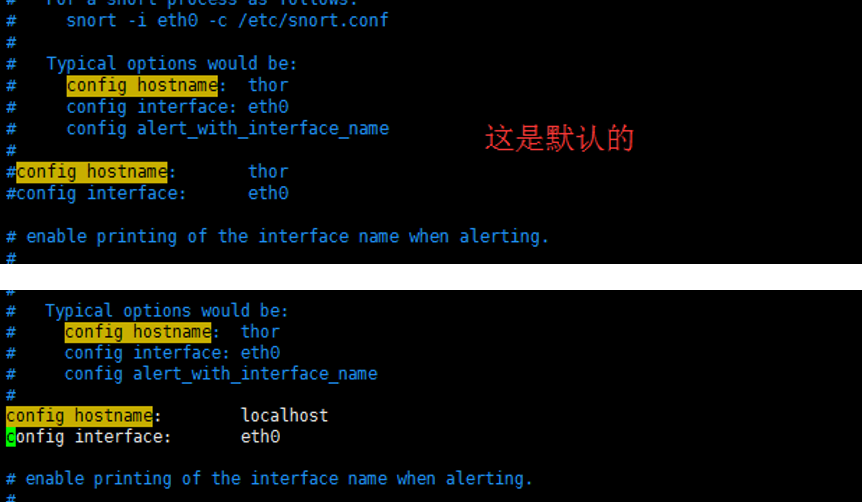
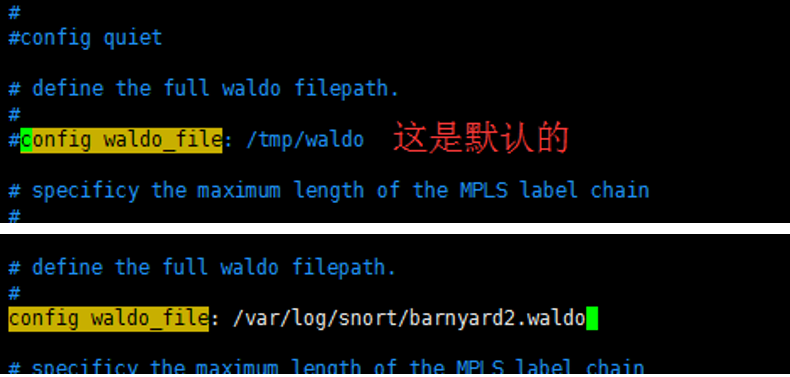
config waldo_file:/var/log/snort/barnyard2.waldo
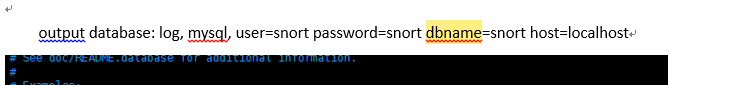
output database: log, mysql, user=snort password=snort dbname=snort host=localhost

11.测试barnyard2
[root@datatest ~]# barnyard2 -c /etc/snort/barnyard2.conf -d /var/log/snort -f snort.log -w /var/log/snort/barnyard2.waldo
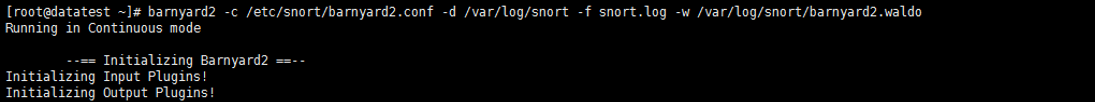
参数解释:
-c 指定配置文件
-d 指定log目录
-f 指定log文件
-w 指定waldo文件
如果出现“Waiting for new spool file”字样则表示barnyard2配置成功
按ctrl+c终止测试
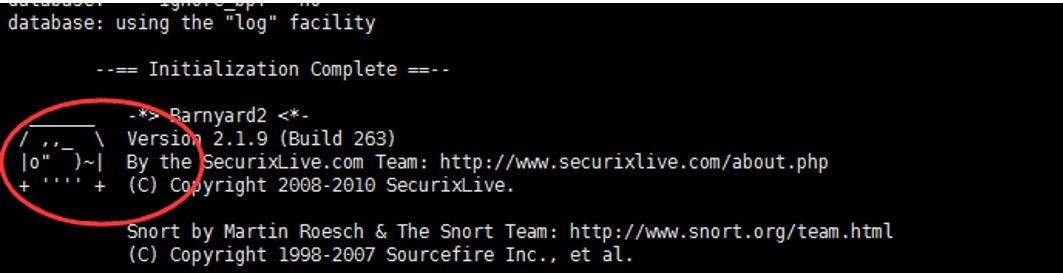
这是头小猪,哈哈哈!!!
四、测试IDS是否正常工作
1.添加测试规则
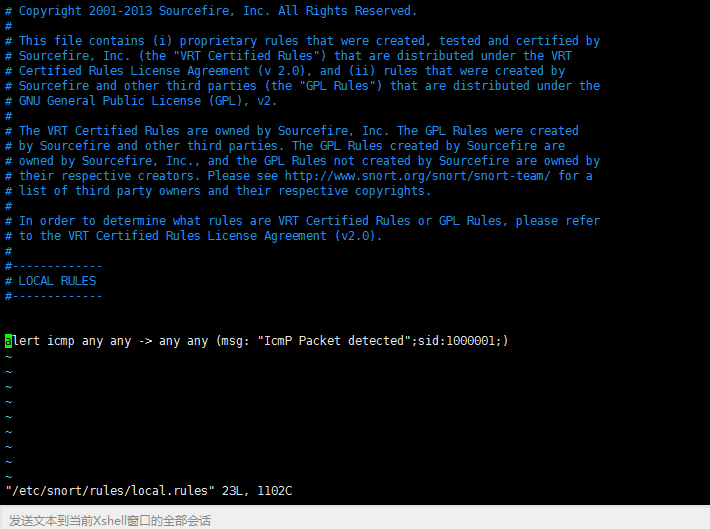
[root@datatest ~]# vi /etc/snort/rules/local.rules
# Copyright 2001-2013 Sourcefire, Inc. All Rights Reserved. # # This file contains (i) proprietary rules that were created, tested and certified by # Sourcefire, Inc. (the "VRT Certified Rules") that are distributed under the VRT # Certified Rules License Agreement (v 2.0), and (ii) rules that were created by # Sourcefire and other third parties (the "GPL Rules") that are distributed under the # GNU General Public License (GPL), v2. # # The VRT Certified Rules are owned by Sourcefire, Inc. The GPL Rules were created # by Sourcefire and other third parties. The GPL Rules created by Sourcefire are # owned by Sourcefire, Inc., and the GPL Rules not created by Sourcefire are owned by # their respective creators. Please see http://www.snort.org/snort/snort-team/ for a # list of third party owners and their respective copyrights. # # In order to determine what rules are VRT Certified Rules or GPL Rules, please refer # to the VRT Certified Rules License Agreement (v2.0). # #------------- # LOCAL RULES #-------------
这是个测试规则的配置文件。
添加一条检查ping包的规则
alert icmp any any -> any any (msg: "IcmP Packet detected";sid:1000001;)
规则注解:
alert 触发规则后做出的动作
icmp 协议类型
第一个any 源IP(网段),any表示任意
第二个any 源端口,any表示任意
-> 表示方向
第三个any 目标IP(网段),any表示任意
第四个any 目标端口,any表示任意
Msg字符 告警名称
Sid id号,个人编写的规则使用1,000,000以上
ID: 报警序号
特征: 报警名称 对应Msg字段
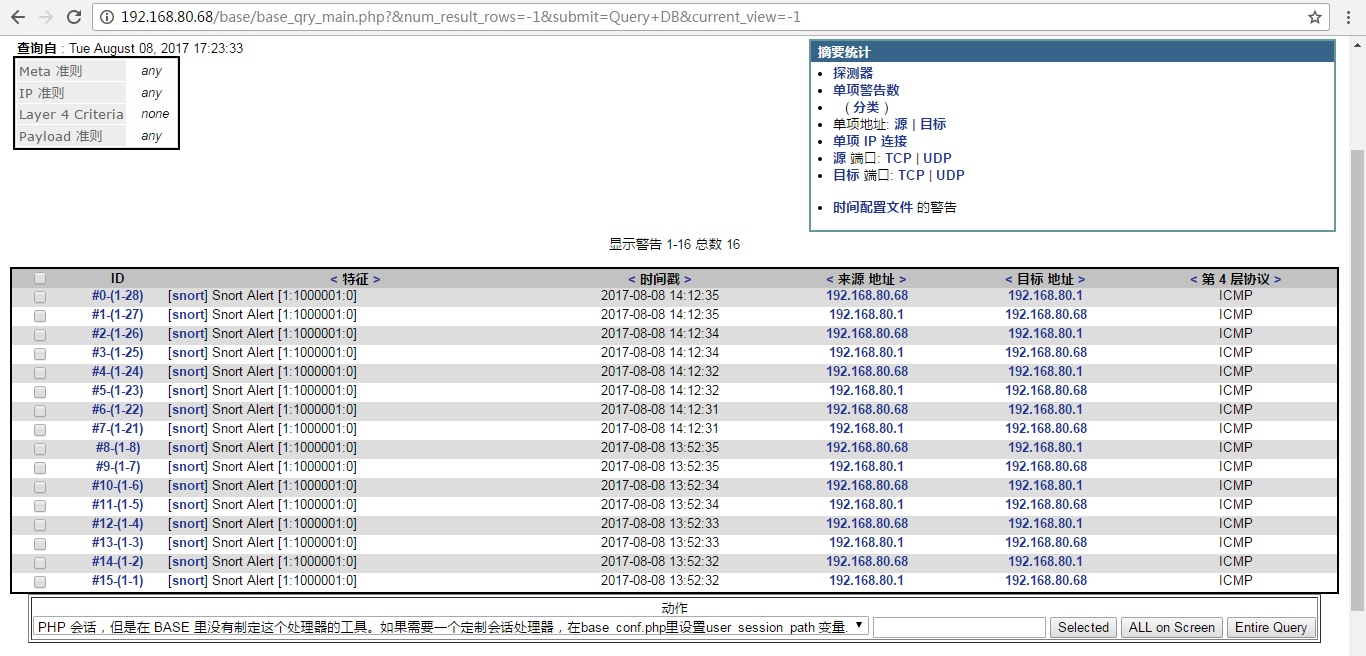
2.配置IDS启动脚本
配置启动脚本(如果大家不会自己写这个idsctl脚本的话)
[root@datatest ~]# cp idsctl /sbin
[root@datatest ~]# chmod 755 /sbin/idsct

3.启动IDS
#service mysqld start 启动mysql
#service httpd start 启动apache
#service iptables stop 关闭防火墙
使用脚本启动ids(都可以的)(因为前面,我扔到了/sbin下了,所以在任何路径下都可以执行了)
[root@datatest ~]# idsctl start
这个地方启动有点慢,大概一分钟吧。
或者手动运行ids(2条命令先后运行,脚本启动失效可选)(都可以)
[root@datatest ~]# barnyard2 -c /etc/snort/barnyard2.conf -d /var/log/snort -f snort.log -w /var/log/snort/barnyard2.waldo -D
[root@datatest ~]# snort -c /etc/snort/snort.conf -i eth0 -D
(-D选项用来让命令转入后台运行,其他选项意义上文已有解释)
idsctl脚本内容是

核心是:
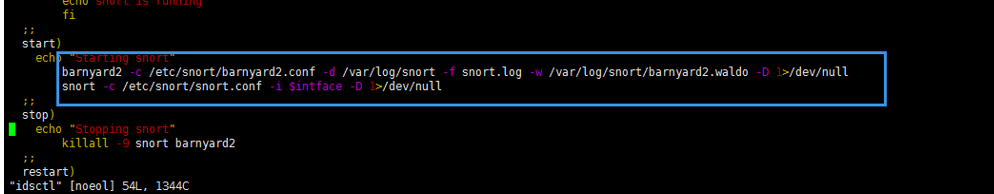
#!/bin/bash ########################################################### # runing shell script For IDS # description: IDS by CentOS 6.6,snort-2.9.7.0,barnyard2-1.9 # Edit by qiubibi # QQ Group:187553731 # Versions : 1.0 ########################################################### intface=eth0 case "$1" in stat) sn=`ps -ef | grep snort | grep -v grep |awk '{print $2}'` if [ "${sn}" = "" ] then echo snortt is not runing else echo snort is running fi ;; start) echo "Starting snort" barnyard2 -c /etc/snort/barnyard2.conf -d /var/log/snort -f snort.log -w /var/log/snort/barnyard2.waldo -D 1>/dev/null snort -c /etc/snort/snort.conf -i $intface -D 1>/dev/null ;; stop) echo "Stopping snort" killall -9 snort barnyard2 ;; restart) echo "Stopping snort" killall -9 snort barnyard2 echo "Starting snort" barnyard2 -c /etc/snort/barnyard2.conf -d /var/log/snort -f snort.log -w /var/log/snort/barnyard2.waldo -D 1>/dev/null snort -c /etc/snort/snort.conf -i $intface -D 1>/dev/null ;; help) cat <<HELP stop -- stops snort service start -- starts snort service stat -- displays status of snort service restart -- stops and restarts snort HELP ;; *) echo "Usage: $0 {start|stop|restart|stat|help}" exit 1 ;; esac exit 0
4、测试IDS
向IDS的IP发送ping包,base的页面会出现ICMP告警。

由
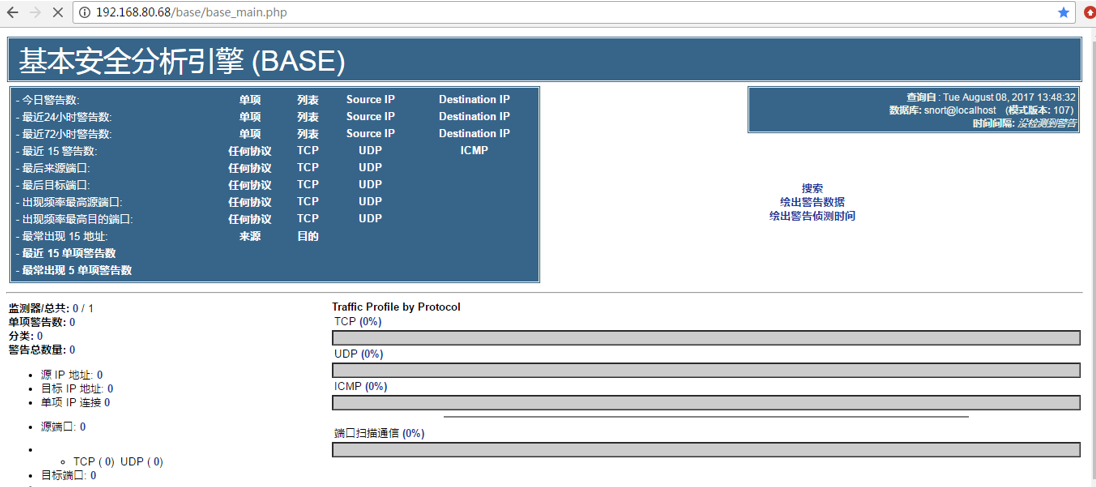
变成
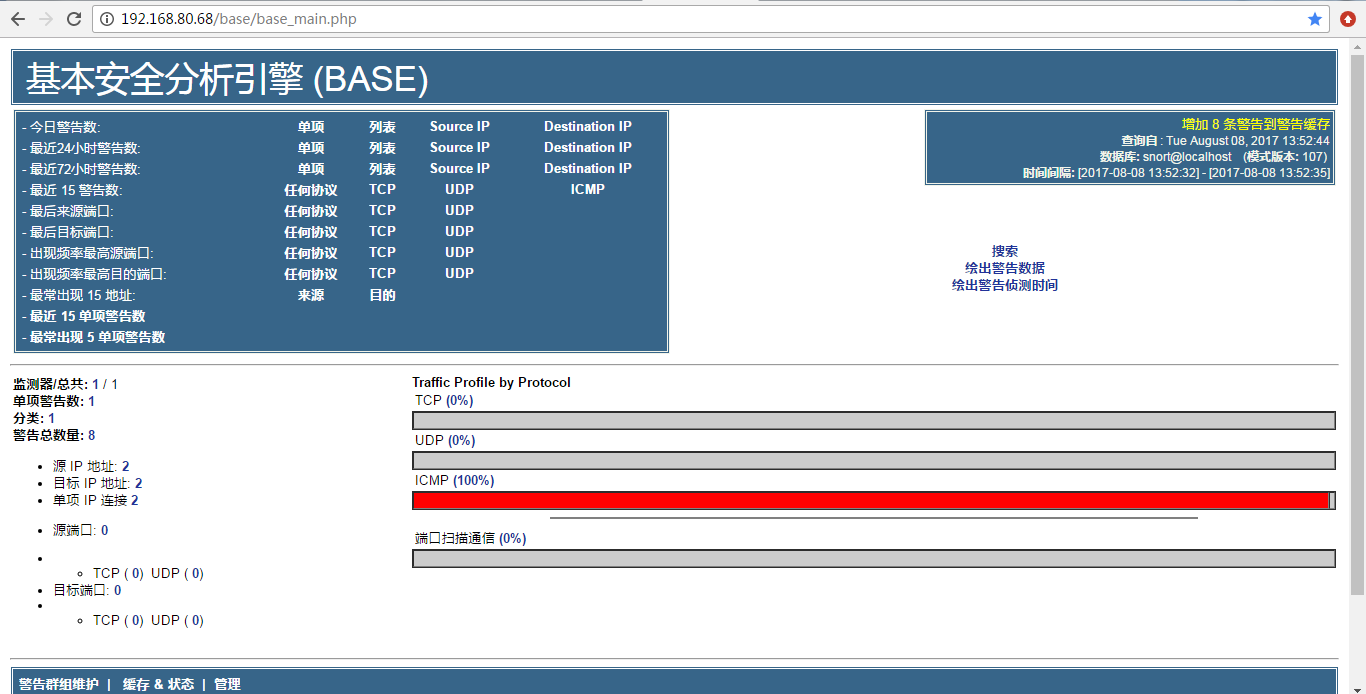
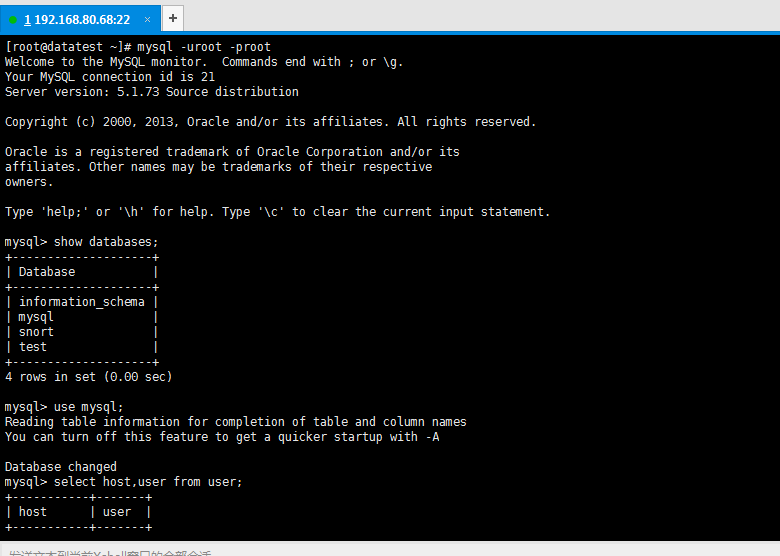
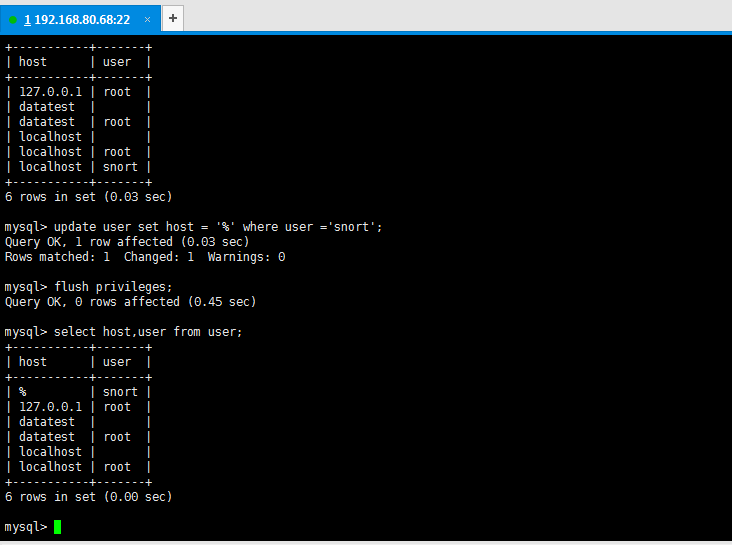
[root@datatest ~]# mysql -uroot -proot Welcome to the MySQL monitor. Commands end with ; or g. Your MySQL connection id is 21 Server version: 5.1.73 Source distribution Copyright (c) 2000, 2013, Oracle and/or its affiliates. All rights reserved. Oracle is a registered trademark of Oracle Corporation and/or its affiliates. Other names may be trademarks of their respective owners. Type 'help;' or 'h' for help. Type 'c' to clear the current input statement. mysql> show databases; +--------------------+ | Database | +--------------------+ | information_schema | | mysql | | snort | | test | +--------------------+ 4 rows in set (0.00 sec) mysql> use mysql; Reading table information for completion of table and column names You can turn off this feature to get a quicker startup with -A Database changed mysql> select host,user from user; +-----------+-------+ | host | user | +-----------+-------+ | 127.0.0.1 | root | | datatest | | | datatest | root | | localhost | | | localhost | root | | localhost | snort | +-----------+-------+ 6 rows in set (0.03 sec) mysql> update user set host = '%' where user ='snort'; Query OK, 1 row affected (0.03 sec) Rows matched: 1 Changed: 1 Warnings: 0 mysql> flush privileges; Query OK, 0 rows affected (0.45 sec) mysql> select host,user from user; +-----------+-------+ | host | user | +-----------+-------+ | % | snort | | 127.0.0.1 | root | | datatest | | | datatest | root | | localhost | | | localhost | root | +-----------+-------+ 6 rows in set (0.00 sec) mysql>
mysql> exit;
Bye
[root@datatest ~]#
然后,大家还要授权,参考我写的下面这篇博客
http://www.cnblogs.com/zlslch/p/6700695.html
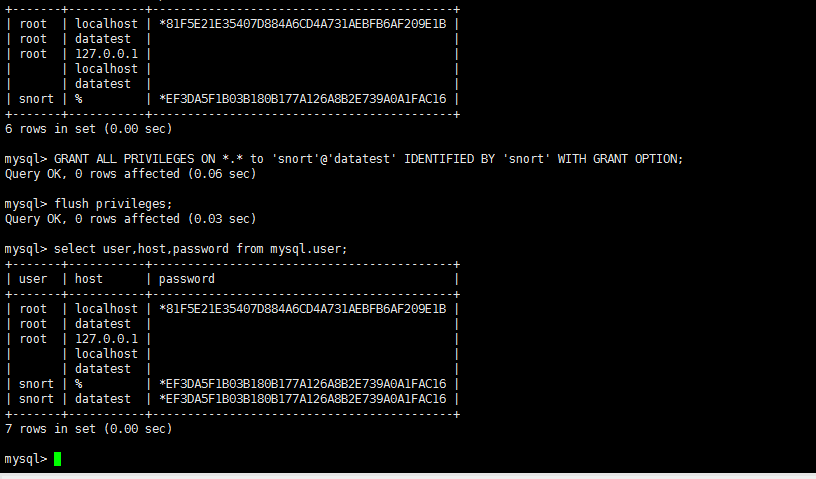
mysql> select user,host,password from mysql.user; +-------+-----------+-------------------------------------------+ | user | host | password | +-------+-----------+-------------------------------------------+ | root | localhost | *81F5E21E35407D884A6CD4A731AEBFB6AF209E1B | | root | datatest | | | root | 127.0.0.1 | | | | localhost | | | | datatest | | | snort | % | *EF3DA5F1B03B180B177A126A8B2E739A0A1FAC16 | +-------+-----------+-------------------------------------------+ 6 rows in set (0.00 sec) mysql> GRANT ALL PRIVILEGES ON *.* to 'snort'@'datatest' IDENTIFIED BY 'snort' WITH GRANT OPTION; Query OK, 0 rows affected (0.06 sec) mysql> flush privileges; Query OK, 0 rows affected (0.03 sec) mysql> select user,host,password from mysql.user; +-------+-----------+-------------------------------------------+ | user | host | password | +-------+-----------+-------------------------------------------+ | root | localhost | *81F5E21E35407D884A6CD4A731AEBFB6AF209E1B | | root | datatest | | | root | 127.0.0.1 | | | | localhost | | | | datatest | | | snort | % | *EF3DA5F1B03B180B177A126A8B2E739A0A1FAC16 | | snort | datatest | *EF3DA5F1B03B180B177A126A8B2E739A0A1FAC16 | +-------+-----------+-------------------------------------------+ 7 rows in set (0.00 sec) mysql>
然后
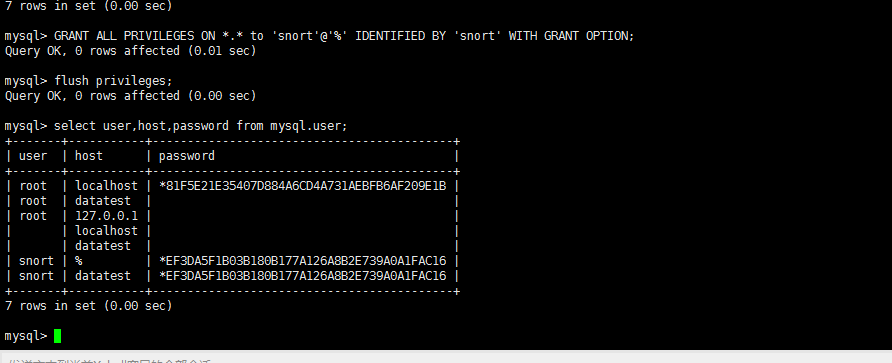
mysql> GRANT ALL PRIVILEGES ON *.* to 'snort'@'%' IDENTIFIED BY 'snort' WITH GRANT OPTION; Query OK, 0 rows affected (0.01 sec) mysql> flush privileges; Query OK, 0 rows affected (0.00 sec) mysql> select user,host,password from mysql.user; +-------+-----------+-------------------------------------------+ | user | host | password | +-------+-----------+-------------------------------------------+ | root | localhost | *81F5E21E35407D884A6CD4A731AEBFB6AF209E1B | | root | datatest | | | root | 127.0.0.1 | | | | localhost | | | | datatest | | | snort | % | *EF3DA5F1B03B180B177A126A8B2E739A0A1FAC16 | | snort | datatest | *EF3DA5F1B03B180B177A126A8B2E739A0A1FAC16 | +-------+-----------+-------------------------------------------+ 7 rows in set (0.00 sec) mysql>
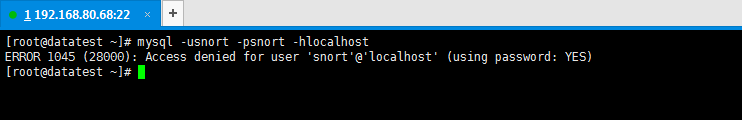
因为我的是,如下
也许大家,这里
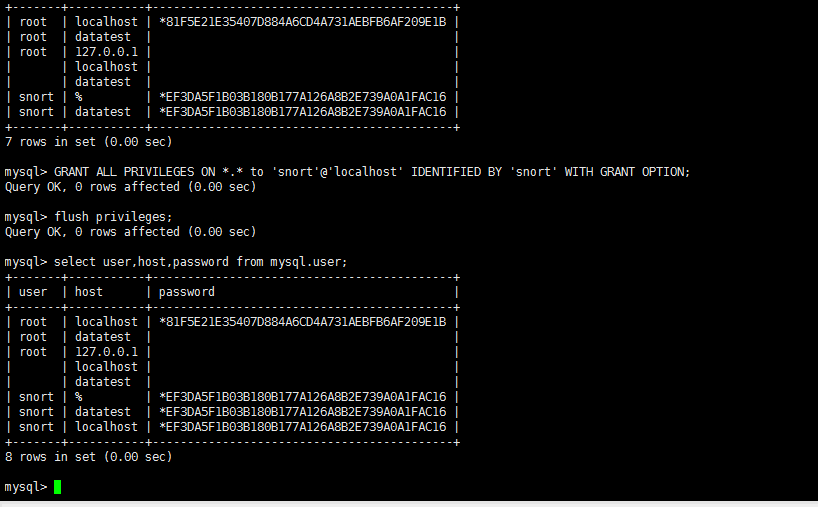
解决办法
+-------+-----------+-------------------------------------------+
| root | localhost | *81F5E21E35407D884A6CD4A731AEBFB6AF209E1B |
| root | datatest | |
| root | 127.0.0.1 | |
| | localhost | |
| | datatest | |
| snort | % | *EF3DA5F1B03B180B177A126A8B2E739A0A1FAC16 |
| snort | datatest | *EF3DA5F1B03B180B177A126A8B2E739A0A1FAC16 |
+-------+-----------+-------------------------------------------+
7 rows in set (0.00 sec)
mysql> GRANT ALL PRIVILEGES ON *.* to 'snort'@'localhost' IDENTIFIED BY 'snort' WITH GRANT OPTION;
Query OK, 0 rows affected (0.00 sec)
mysql> flush privileges;
Query OK, 0 rows affected (0.00 sec)
mysql> select user,host,password from mysql.user;
+-------+-----------+-------------------------------------------+
| user | host | password |
+-------+-----------+-------------------------------------------+
| root | localhost | *81F5E21E35407D884A6CD4A731AEBFB6AF209E1B |
| root | datatest | |
| root | 127.0.0.1 | |
| | localhost | |
| | datatest | |
| snort | % | *EF3DA5F1B03B180B177A126A8B2E739A0A1FAC16 |
| snort | datatest | *EF3DA5F1B03B180B177A126A8B2E739A0A1FAC16 |
| snort | localhost | *EF3DA5F1B03B180B177A126A8B2E739A0A1FAC16 |
+-------+-----------+-------------------------------------------+
8 rows in set (0.00 sec)
mysql>
测试下。成功!
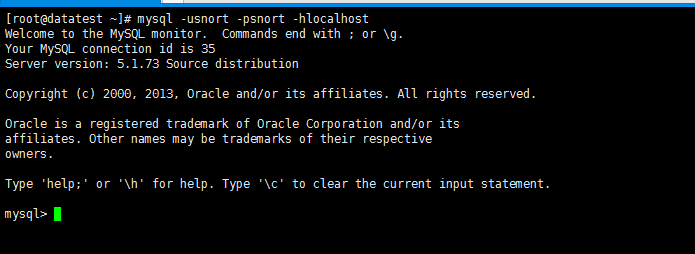
MySQL客户端的展示
推荐大家用:


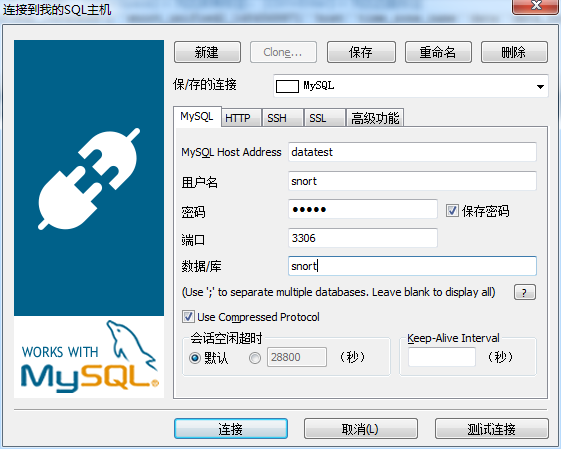
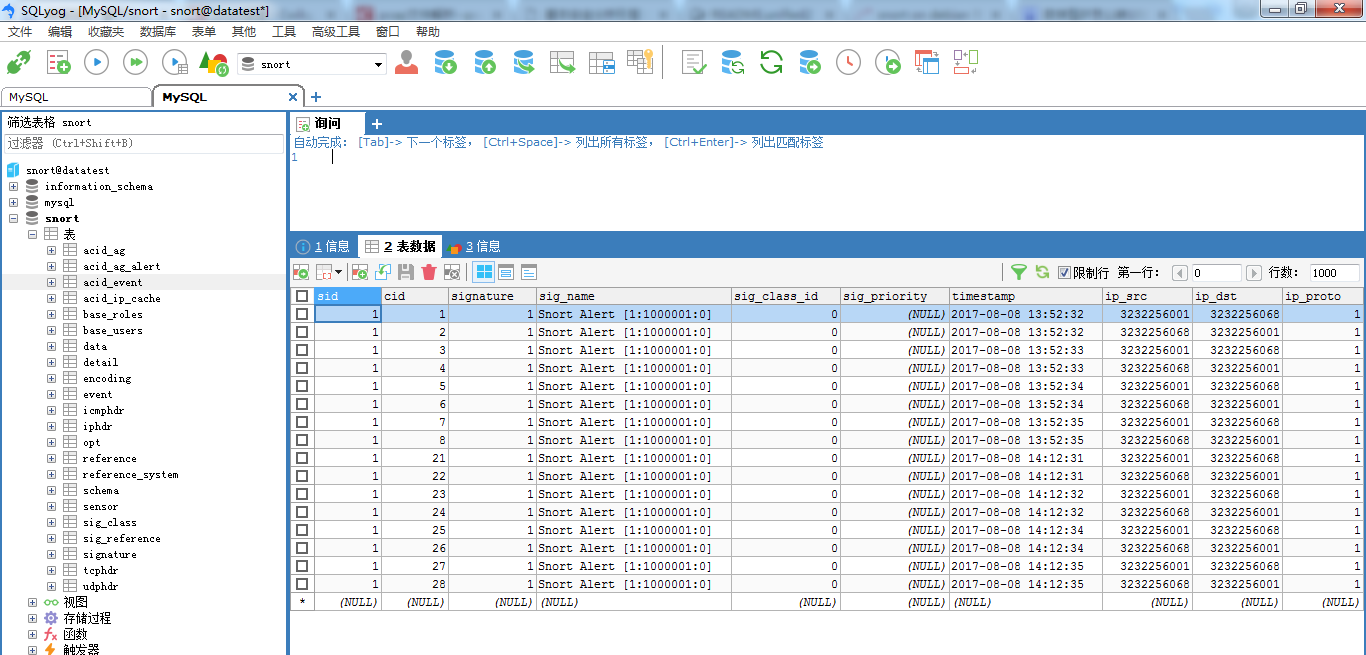
或者
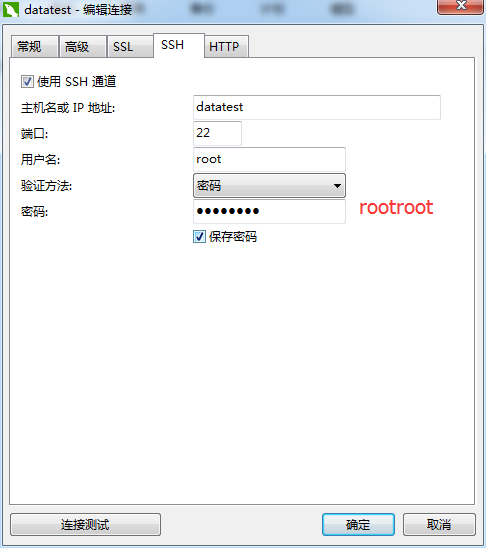
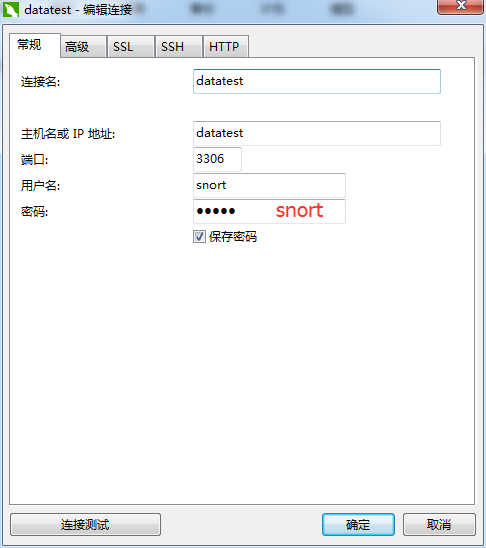
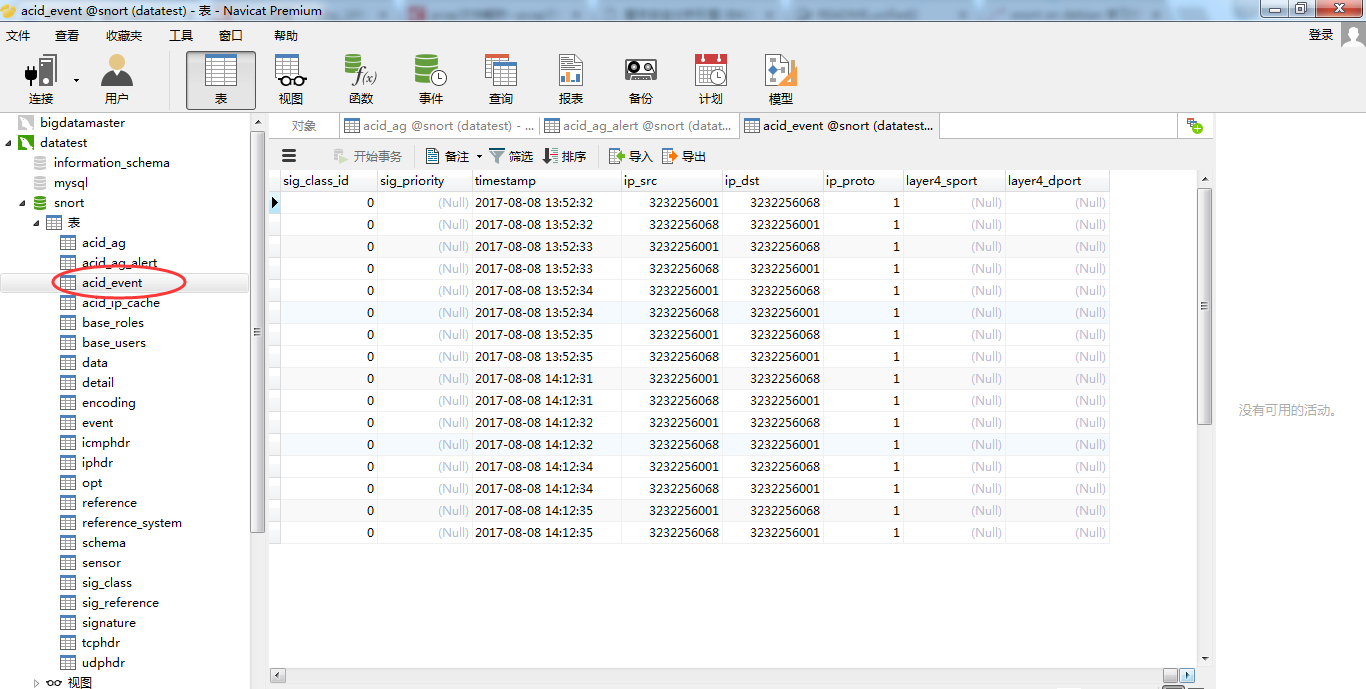
一个一个打开来看看
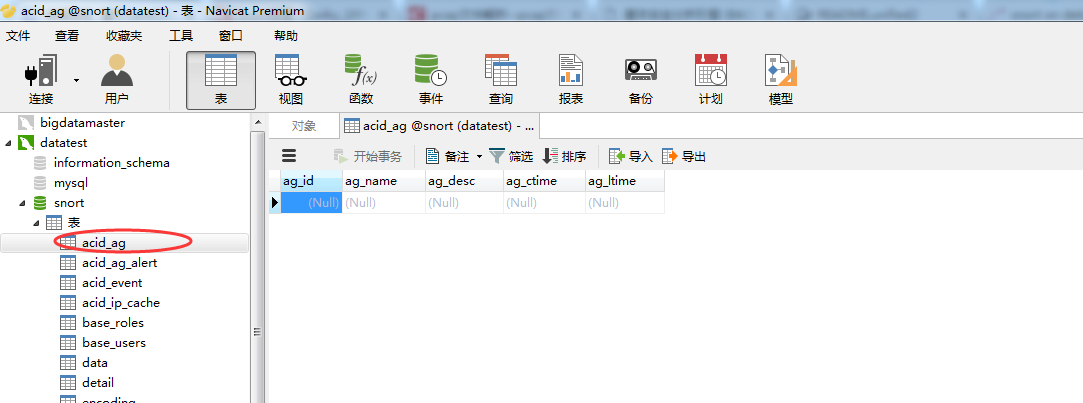
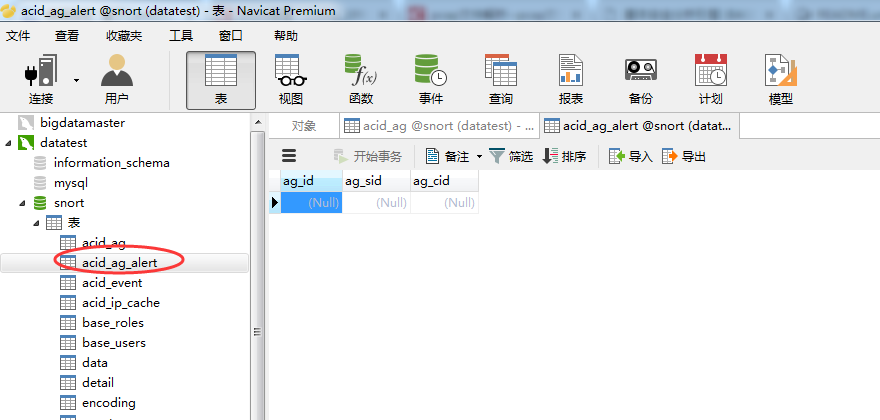
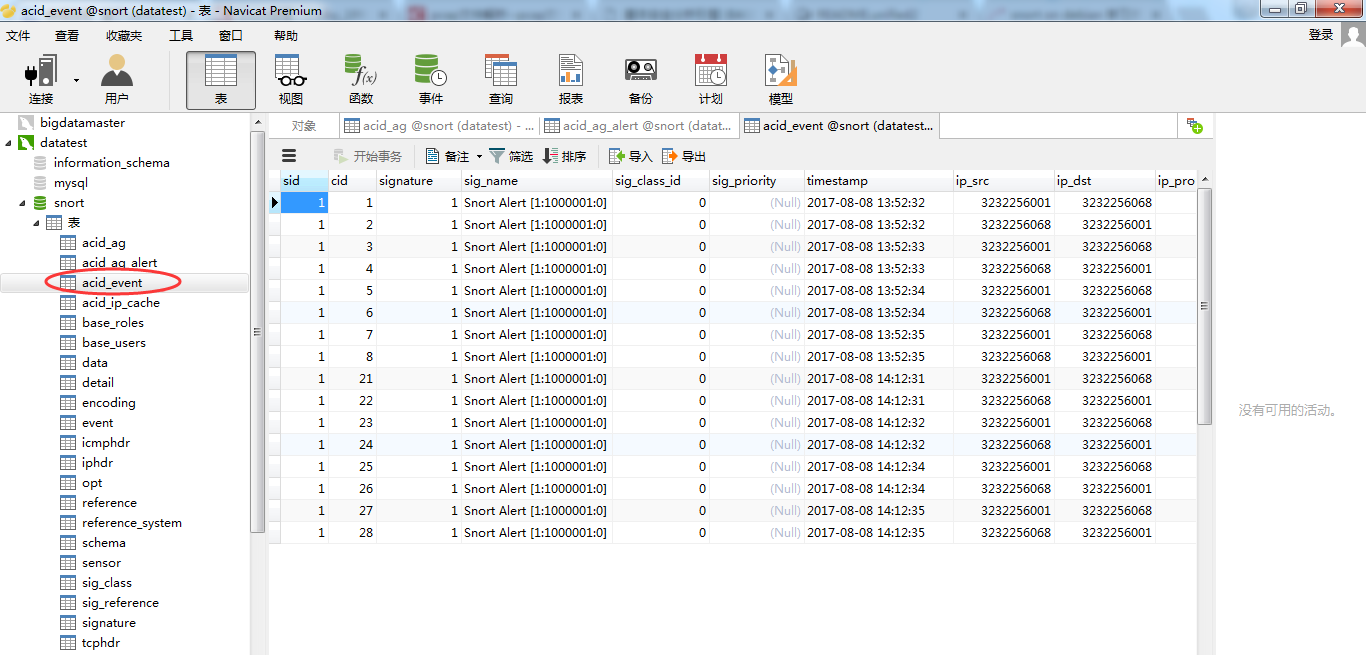
数据库里面存储的IP都是数字型的。




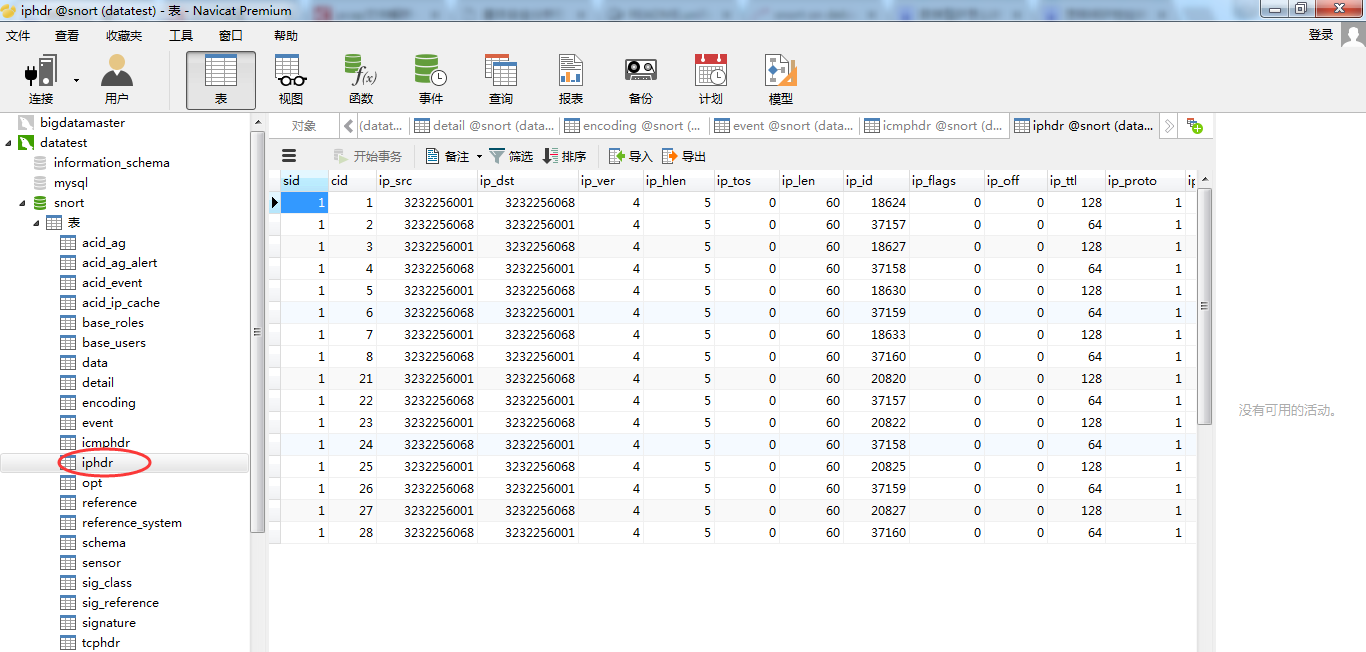
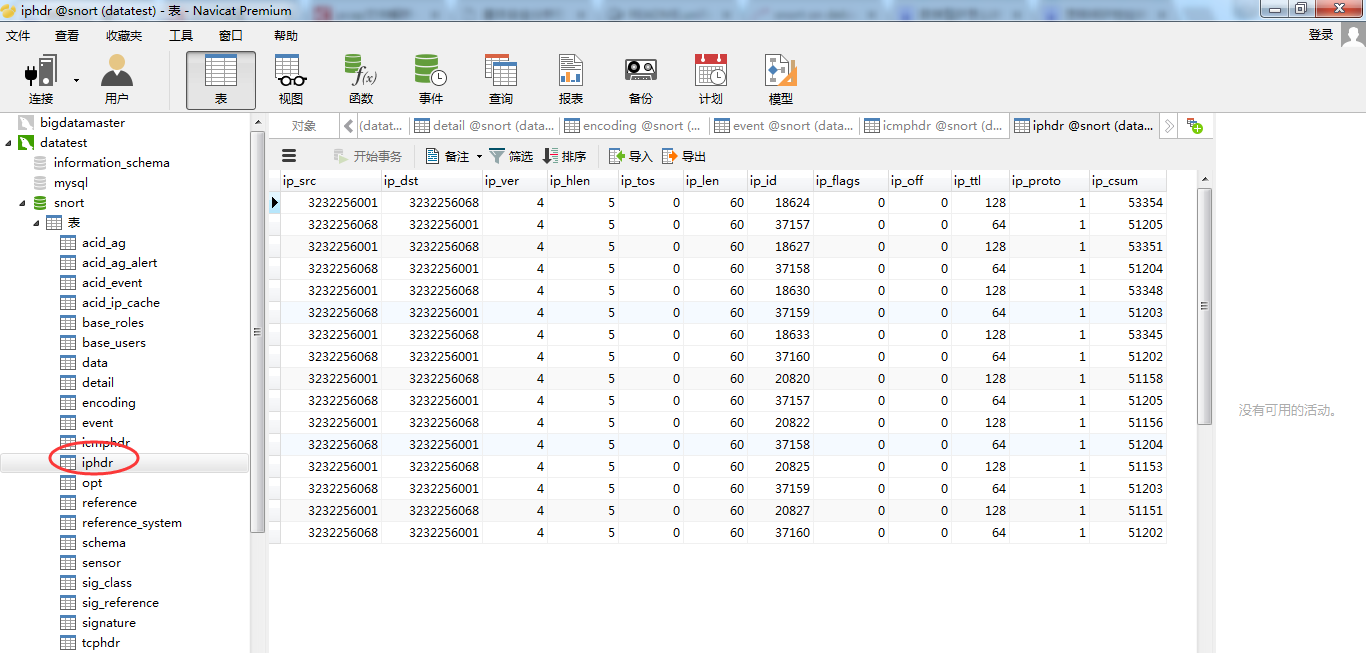


5.停止IDS
使用脚本停止IDS(因为前面,我扔到了/sbin下了,所以在任何路径下都可以执行了)
[root@datatest ~]# idsctl stop
手动停止IDS(都可以)
[root@datatest ~]# killall -9 snort barnyard2
6、停止base
因为,我们安装的时候,把base放在/var/www/html,即apache服务。
[root@datatest ~]# service httpd stop
即可,就是停止了base。
下次用时,开启再访问
http://192.168.80.68/base/base_main.php
注意:
这里个非常不好用的规则,事实上,也许是最差的规则,但是它可以很好的检测Snort是否正常工作,并可以产生告警:
alert ip any any -> any any (msg: "IP Packet detected";)
你可以在你第一次安装Snort的时候在snort.conf的末尾加上这条规则,这个规则可以使每当捕获一个IP包都产生告警信息,如果你就这样离开的话,你的硬盘空间很快就会被填满。这个规则之所以不可用,是因为它不信任任何信息。难道你用一个永久规则的目的就是为了检测Snort是否在工作吗?它应该是用来在你安装完Snort后做测试,以确定其工作正常,然后就去掉这条规则。
当然,若是真实物理机器搭建的入侵检测系统环境,一般是不建议频繁开启关闭的。这个道理,跟打架玩大数据集群,是一样的!
OK,就写这么多吧!欢迎交流。想玩大数据的朋友,请移步,见我下面的博客。
大数据领域两大最主流集群管理工具Ambari和Cloudera Manger
CentOS6.5下Ambari安装搭建部署大数据集群(图文分五大步详解)(博主强烈推荐)
CentOS6.5下Cloudera安装搭建部署大数据集群(图文分五大步详解)(博主强烈推荐)
关于在真实物理机器上用cloudermanger或ambari搭建大数据集群注意事项总结、经验和感悟心得(图文详解)
Ubuntu14.04下Cloudera安装搭建部署大数据集群(图文分五大步详解)(博主强烈推荐)(在线或离线)
Ubuntu14.04下Ambari安装搭建部署大数据集群(图文分五大步详解)(博主强烈推荐)
参考
http://www.secbox.cn/skill/8796.html (感谢!)
基于CentOS平台的Snort+Barnyard安装步骤(感谢!)
同时,大家可以关注我的个人博客:
http://www.cnblogs.com/zlslch/ 和 http://www.cnblogs.com/lchzls/ http://www.cnblogs.com/sunnyDream/
详情请见:http://www.cnblogs.com/zlslch/p/7473861.html
人生苦短,我愿分享。本公众号将秉持活到老学到老学习无休止的交流分享开源精神,汇聚于互联网和个人学习工作的精华干货知识,一切来于互联网,反馈回互联网。
目前研究领域:大数据、机器学习、深度学习、人工智能、数据挖掘、数据分析。 语言涉及:Java、Scala、Python、Shell、Linux等 。同时还涉及平常所使用的手机、电脑和互联网上的使用技巧、问题和实用软件。 只要你一直关注和呆在群里,每天必须有收获
对应本平台的讨论和答疑QQ群:大数据和人工智能躺过的坑(总群)(161156071)