反汇编测试
作者:20191322wyl
源代码:
int g(int x){
return x+3;
}
int f(int x){
int i = 22;
return g(x)+i;
}
int main(void){
return f(8)+1;
}
安装库
sudo apt-get install libc6-dev-i386
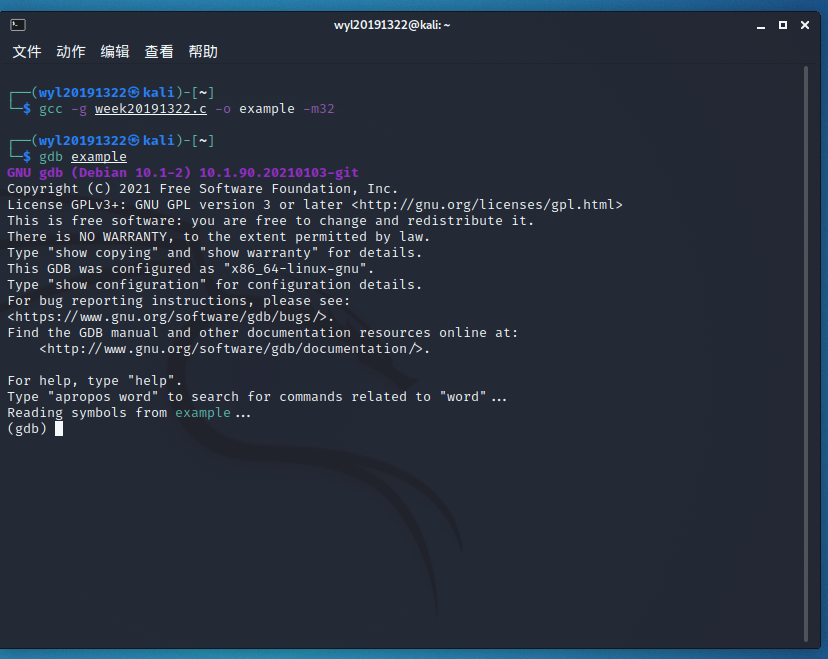
编译
gcc -g week20191322.c -o example -m32
在64位的机器上产生32位汇编,然后使用gdb example指令进入gdb调试器
分析过程
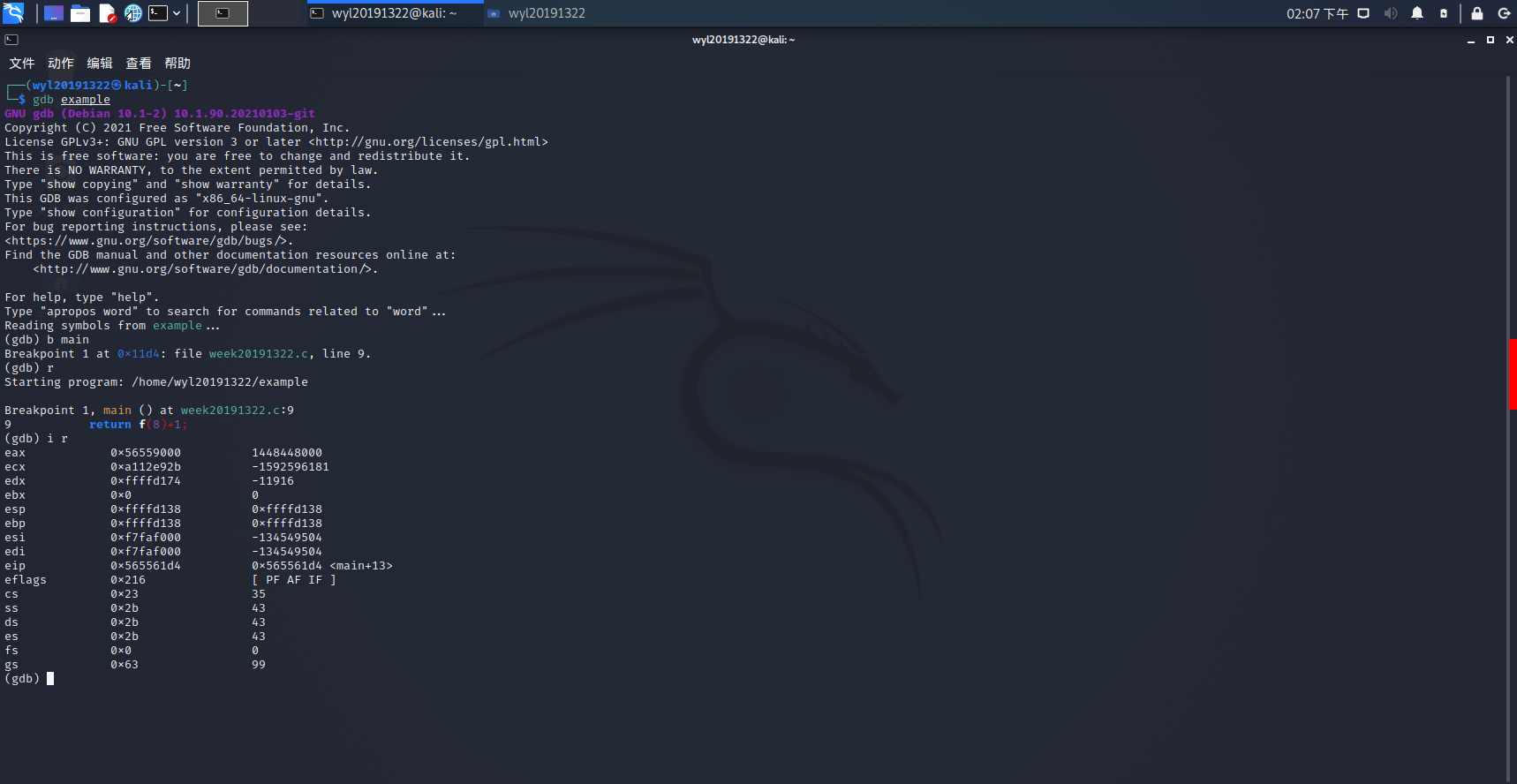
- 在main函数处设置一个断点
b main,在r一下,使用disassemble
获取汇编代码,用i(info) r(registers)指令查看各寄存器的值:
-
使用命令
display /i $pc设置每次都显示当前执行的命令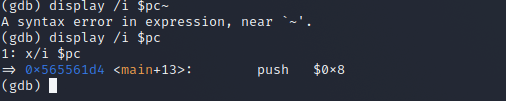
-
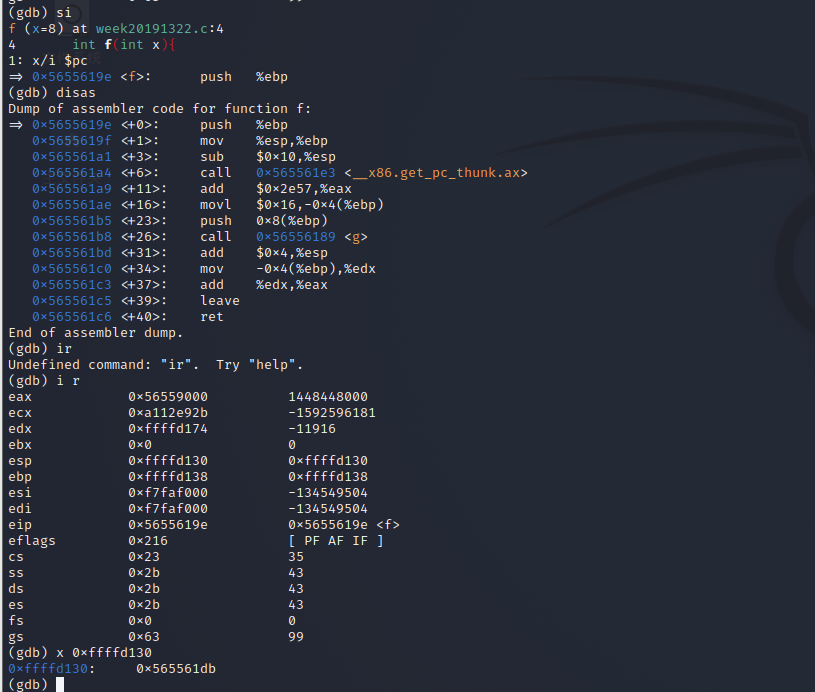
push
-
mov
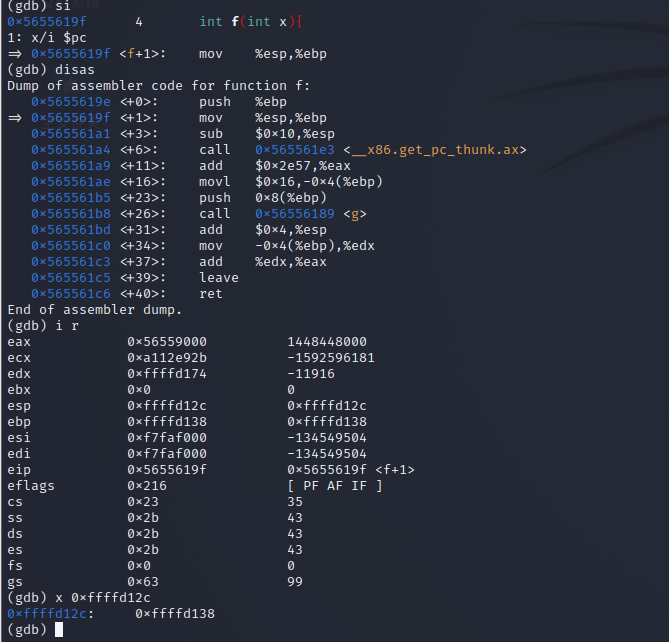
-
sub
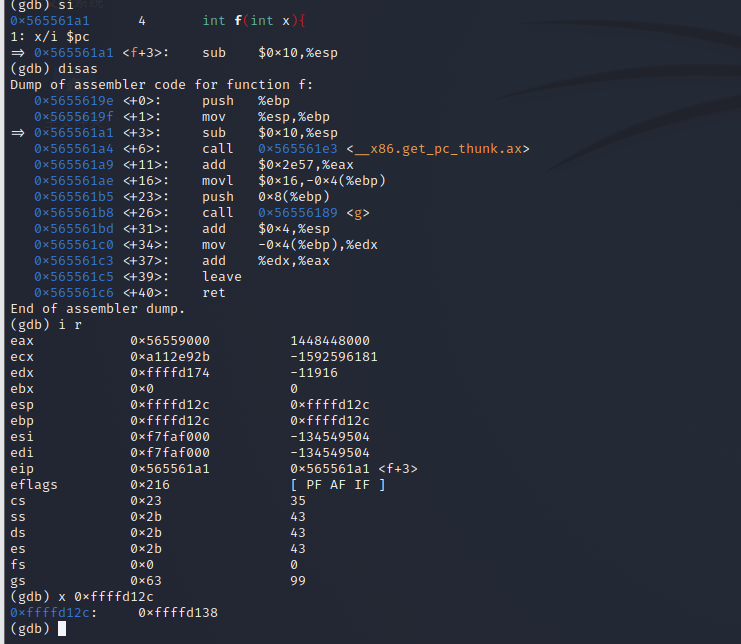
-
call
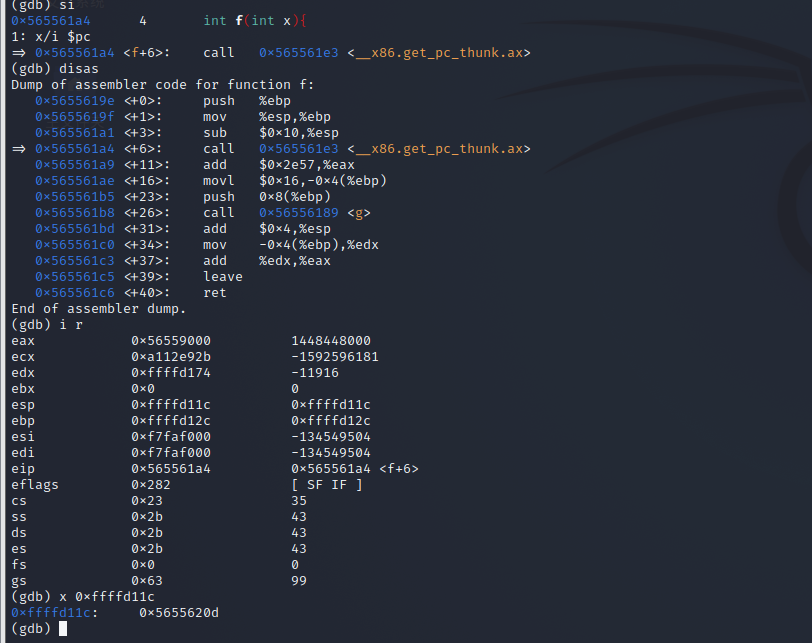
-
add

-
movl
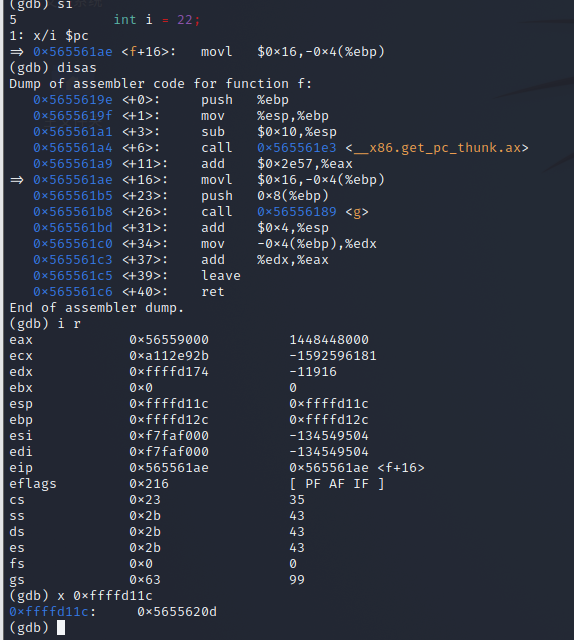
-
push
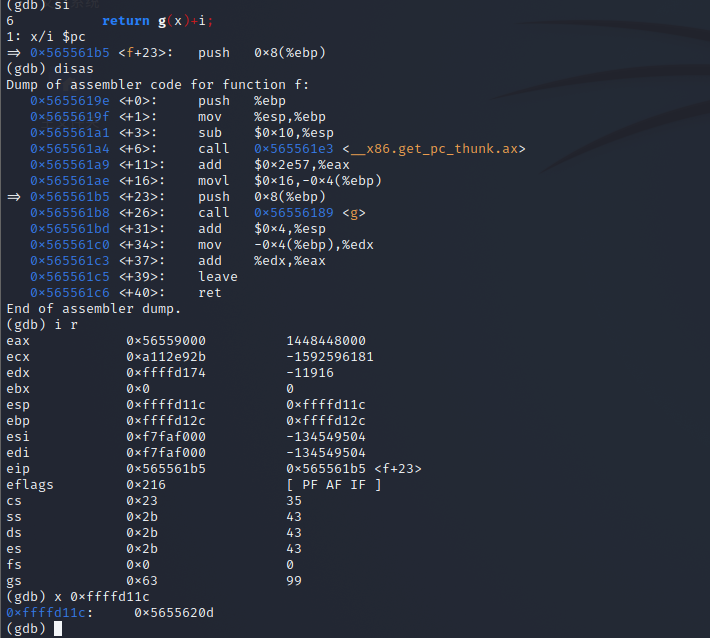
-
call
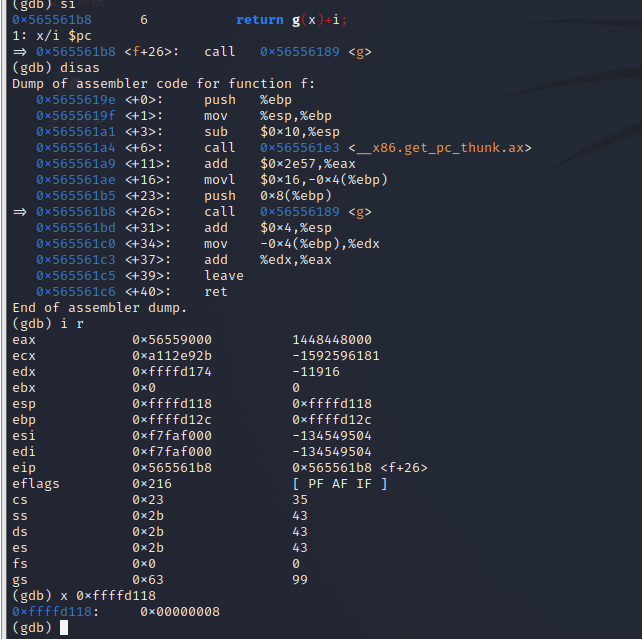
-
add
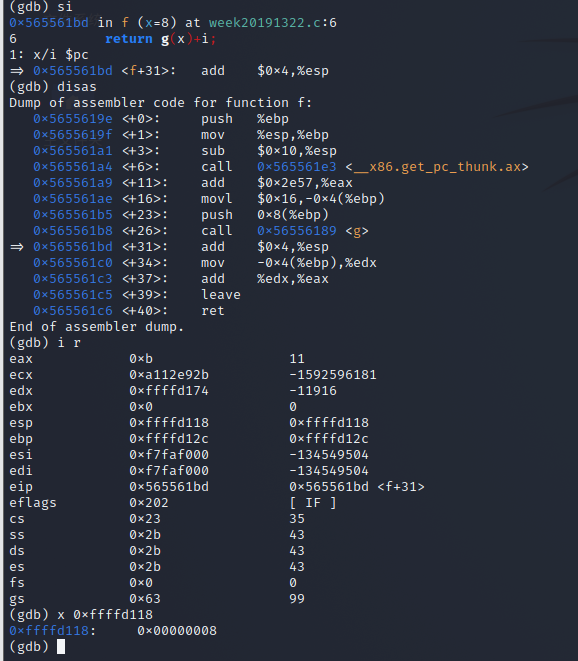
-
mov
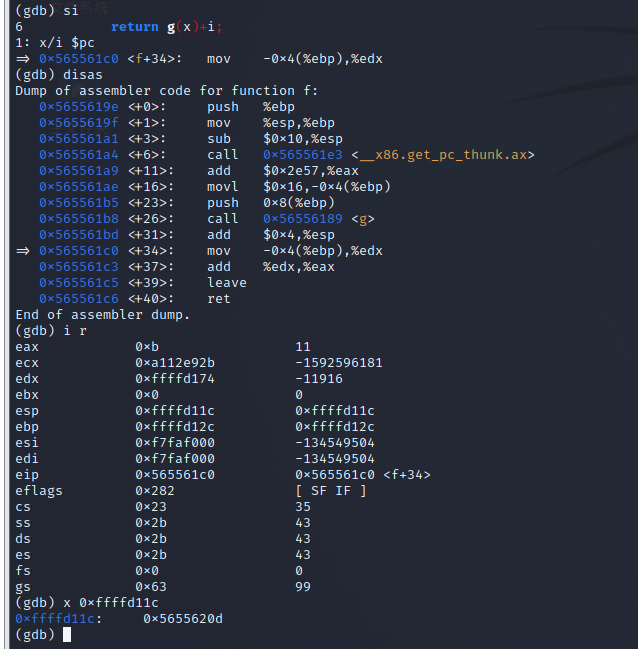
-
add
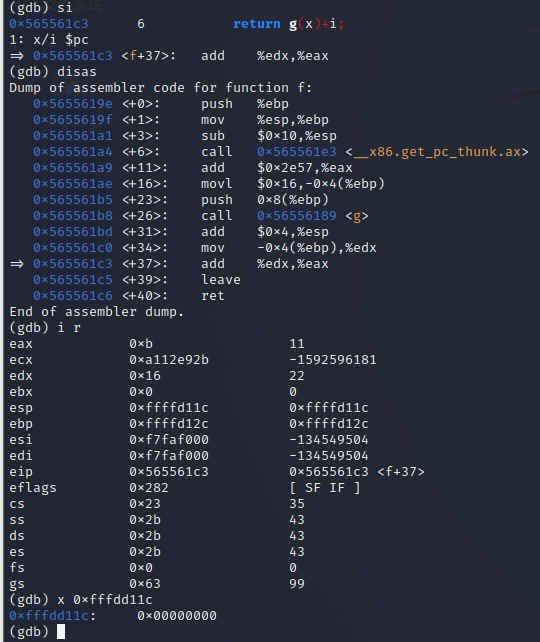
-
leave
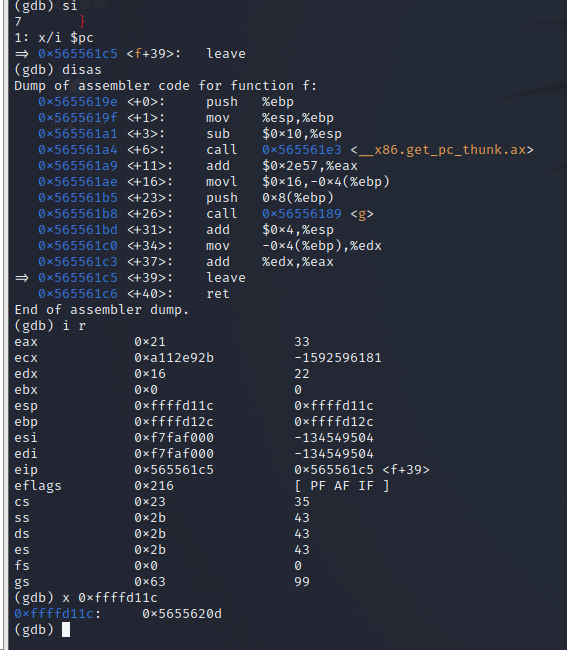
-
ret

变化情况
| 20191322wyl | eax | ebp | esp | eip | 栈 |
|---|---|---|---|---|---|
| push | 0x56559000 | 0xffffd138 | 0xffffd130 | 0x5655619e | 0x565561db |
| move | 0x56559000 | 0xffffd138 | 0xffffd12c | 0x5655619f | 0xfffd138 |
| sub | 0x56559000 | 0xffffd12c | 0xffffd12c | 0x565561a1 | 0xffffd138 |
| call | 0x56559000 | 0xffffd12c | 0xffffd11c | 0x565561a4 | 0x5655620d |
| add | 0x565561a9 | 0xffffd12c | 0xffffd11c | 0x565561a9 | 0x5655620d |
| movl | 0x56559000 | 0xffffd12c | 0xffffd11c | 0x565561ae | 0x5655620d |
| push | 0x56559000 | 0xffffd12c | 0xffffd11c | 0x565561b5 | 0x5655620d |
| call | 0x56559000 | 0xffffd12c | 0xffffd118 | 0x565561b8 | 0x8 |
| add | 0xb | 0xffffd12c | 0xffffd118 | 0x565561bd | 0x8 |
| mov | 0xb | 0xffffd12c | 0xffffd11c | 0x565561c0 | 0x5655620d |
| add | 0xb | 0xffffd12c | 0xffffd11c | 0x565561c3 | 0x0 |
| leave | 0x21 | 0xffffd12c | 0xffffd11c | 0x565561c5 | 0x5655620d |
| ret | 0x21 | 0xffffd138 | 0xffffd130 | 0x565561c6 | 0x565561db |