系统 : Windows xp
程序 : keyfileme
程序下载地址 :http://pan.baidu.com/s/1qYVfvu0
要求 : 编写KeyFile
使用工具 : OD
可在看雪论坛中查找关于此程序的破文:传送门
趁着小长假还没结束,赶紧来个CM暖暖手。废话不多说,直接用DIE查看程序。
提示MASM编写,没有保护壳。
再用OD载入,发现关键子串:no keyfile found!
0040113E . E8 F0010000 call 00401333
00401143 . 803D 2C604000>cmp byte ptr [40602C], 1
0040114A . 74 20 je short 0040116C
0040114C . 803D 2C604000>cmp byte ptr [40602C], 2
00401153 . 74 2C je short 00401181
00401155 . 803D 2C604000>cmp byte ptr [40602C], 3
0040115C . 74 38 je short 00401196
0040115E . 803D 2C604000>cmp byte ptr [40602C], 4
00401165 . 74 44 je short 004011AB
00401167 . E9 C1010000 jmp 0040132D
0040116C > 68 51624000 push 00406251 ; /no keyfile found!
00401171 . FF35 76604000 push dword ptr [406076] ; |hWnd = NULL
00401177 . E8 5A030000 call <jmp.&user32.SetWindowTextA> ; SetWindowTextA
0040117C . E9 AC010000 jmp 0040132D
00401181 > 68 63624000 push 00406263 ; /wrong size!
00401186 . FF35 76604000 push dword ptr [406076] ; |hWnd = NULL
0040118C . E8 45030000 call <jmp.&user32.SetWindowTextA> ; SetWindowTextA
00401191 . E9 97010000 jmp 0040132D
00401196 > 68 6F624000 push 0040626F ; /invalid keyfile!
0040119B . FF35 76604000 push dword ptr [406076] ; |hWnd = NULL
004011A1 . E8 30030000 call <jmp.&user32.SetWindowTextA> ; SetWindowTextA
004011A6 . E9 82010000 jmp 0040132D
004011AB > 68 09604000 push 00406009 ; /registered! good job!
004011B0 . FF35 76604000 push dword ptr [406076] ; |hWnd = NULL
004011B6 . E8 1B030000 call <jmp.&user32.SetWindowTextA> ; SetWindowTextA
可见结果是由Call直接产生,右击Call指令,选择Follow:
00401333 /$ 6A 00 push 0 ; /hTemplateFile = NULL
00401335 |. 68 80000000 push 80 ; |Attributes = NORMAL
0040133A |. 6A 03 push 3 ; |Mode = OPEN_EXISTING
0040133C |. 6A 00 push 0 ; |pSecurity = NULL
0040133E |. 6A 01 push 1 ; |ShareMode = FILE_SHARE_READ
00401340 |. 68 00000080 push 80000000 ; |Access = GENERIC_READ
00401345 |. 68 32604000 push 00406032 ; |keyfile.dat
0040134A |. E8 93010000 call <jmp.&kernel32.CreateFileA> ; CreateFileA
0040134F |. A3 62604000 mov dword ptr [406062], eax
00401354 |. 83F8 FF cmp eax, -1
00401357 |. 0F84 DB000000 je 00401438
0040135D |. 6A 00 push 0 ; /pFileSizeHigh = NULL
0040135F |. FF35 62604000 push dword ptr [406062] ; |hFile = NULL
00401365 |. E8 8A010000 call <jmp.&kernel32.GetFileSize> ; GetFileSize
0040136A |. 83F8 20 cmp eax, 20 ; 长度一定要是32个字符
0040136D |. 0F85 CE000000 jnz 00401441 ; ↓读取前十六个字符
00401373 |. 6A 00 push 0 ; /pOverlapped = NULL
00401375 |. 68 48634000 push 00406348 ; |pBytesRead = keyfilem.00406348
0040137A |. 6A 10 push 10 ; |BytesToRead = 10 (16.)
0040137C |. 68 3E604000 push 0040603E ; |Buffer = keyfilem.0040603E
00401381 |. FF35 62604000 push dword ptr [406062] ; |hFile = NULL
00401387 |. E8 86010000 call <jmp.&kernel32.ReadFile> ; ReadFile
0040138C |. FF35 62604000 push dword ptr [406062] ; /hObject = NULL
00401392 |. E8 45010000 call <jmp.&kernel32.CloseHandle> ; CloseHandle
00401397 |. 33C9 xor ecx, ecx
00401399 |. 33D2 xor edx, edx
0040139B |. BA 0F000000 mov edx, 0F
004013A0 |> 0FBE8A 3E6040>/movsx ecx, byte ptr [edx+40603E] ; 循环迭代字符串
004013A7 |. 4A |dec edx
004013A8 |. 83F9 20 |cmp ecx, 20 ; 是否是空格?
004013AB |. 75 09 |jnz short 004013B6 ; 发现不是空格则跳转
004013AD |. C682 3F604000>|mov byte ptr [edx+40603F], 0
004013B4 |.^ EB EA jmp short 004013A0
004013B6 |> E9 A1000000 jmp 0040145C
004013BB |> 6A 00 push 0 ; /hTemplateFile = NULL
004013BD |. 68 80000000 push 80 ; |Attributes = NORMAL
004013C2 |. 6A 03 push 3 ; |Mode = OPEN_EXISTING
004013C4 |. 6A 00 push 0 ; |pSecurity = NULL
004013C6 |. 6A 01 push 1 ; |ShareMode = FILE_SHARE_READ
004013C8 |. 68 00000080 push 80000000 ; |Access = GENERIC_READ
004013CD |. 68 32604000 push 00406032 ; |keyfile.dat
004013D2 |. E8 0B010000 call <jmp.&kernel32.CreateFileA> ; CreateFileA
004013D7 |. A3 62604000 mov dword ptr [406062], eax ; ↓读取文件后半部分
004013DC |. 68 A7624000 push 004062A7 ; /pOverlapped = keyfilem.004062A7
004013E1 |. 68 48634000 push 00406348 ; |pBytesRead = keyfilem.00406348
004013E6 |. 6A 10 push 10 ; |BytesToRead = 10 (16.)
004013E8 |. 68 4E604000 push 0040604E ; |Buffer = keyfilem.0040604E
004013ED |. FF35 62604000 push dword ptr [406062] ; |hFile = NULL
004013F3 |. E8 1A010000 call <jmp.&kernel32.ReadFile> ; ReadFile
004013F8 |. FF35 62604000 push dword ptr [406062] ; /hObject = NULL
004013FE |. E8 D9000000 call <jmp.&kernel32.CloseHandle> ; CloseHandle
00401403 |. 33C9 xor ecx, ecx
00401405 |. 33D2 xor edx, edx
00401407 |. BA 0F000000 mov edx, 0F
0040140C |> 0FBE8A 4E6040>/movsx ecx, byte ptr [edx+40604E] ; 把多余的空格部分去除
00401413 |. 4A |dec edx
00401414 |. 83F9 20 |cmp ecx, 20
00401417 |. 75 09 |jnz short 00401422
00401419 |. C682 4F604000>|mov byte ptr [edx+40604F], 0
00401420 |.^ EB EA jmp short 0040140C
00401422 |> 68 87624000 push 00406287 ; /String2 = ""
00401427 |. 68 4E604000 push 0040604E ; |String1 = ""
0040142C |. E8 ED000000 call <jmp.&kernel32.lstrcmpA> ; lstrcmpA
00401431 |. 83F8 00 cmp eax, 0
00401434 |. 74 1D je short 00401453
00401436 |. 75 12 jnz short 0040144A
00401438 |> C605 2C604000>mov byte ptr [40602C], 1
0040143F |. EB 63 jmp short 004014A4
00401441 |> C605 2C604000>mov byte ptr [40602C], 2
00401448 |. EB 5A jmp short 004014A4
0040144A |> C605 2C604000>mov byte ptr [40602C], 3
00401451 |. EB 51 jmp short 004014A4
00401453 |> C605 2C604000>mov byte ptr [40602C], 4
0040145A |. EB 48 jmp short 004014A4
0040145C |> 53 push ebx
0040145D |. 57 push edi
0040145E |. 68 3E604000 push 0040603E ; /String = ""
00401463 |. E8 BC000000 call <jmp.&kernel32.lstrlenA> ; lstrlenA
00401468 |. 8BD0 mov edx, eax
0040146A |. 33C9 xor ecx, ecx
0040146C |. 33DB xor ebx, ebx
0040146E |> 0FB681 3E6040>/movzx eax, byte ptr [ecx+40603E] ; 循环迭代字符串
00401475 |. 83C0 0F |add eax, 0F
00401478 |. 83F0 20 |xor eax, 20
0040147B |. 03D8 |add ebx, eax
0040147D |. 41 |inc ecx ; 循环变量自增
0040147E |. 3BCA |cmp ecx, edx ; 是否遍历完毕?
00401480 |.^ 75 EC jnz short 0040146E
00401482 |. 33C9 xor ecx, ecx
00401484 |. 69DB 697A0000 imul ebx, ebx, 7A69
0040148A |. 53 push ebx ; /<%X>
0040148B |. 68 84624000 push 00406284 ; |%x
00401490 |. 68 87624000 push 00406287 ; |s = keyfilem.00406287
00401495 |. E8 0C000000 call <jmp.&user32.wsprintfA> ; wsprintfA
0040149A |. 83C4 0C add esp, 0C
0040149D |. 5F pop edi
0040149E |. 5B pop ebx
0040149F |.^ E9 17FFFFFF jmp 004013BB
004014A4 > C3 retn
KeyFile长度必须为32,前面写着用户名,后面是密码。而CM的计算方式是简单的F(用户名) = 密码。
给出可用的KeyFIle内容:
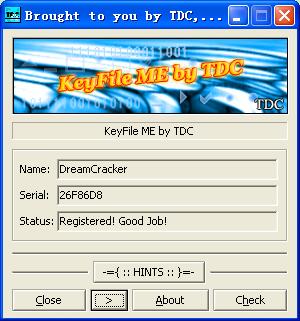
DreamCracker 26F86D8
运行效果: