问题原因:公司监控一直有告警,经排查,发现zookeeper连接监控采集机为SYN_RECV半连接状态 ,而且这个节点已经停止采集,需要释放这个tcp连接,但是尝试了使用lsof命令,无法定位进程号
解决方案:网上查到一个工具 killcx,使用 killcx 工具来关闭TCP连接
killcx是一个在linux下可以关闭TCP连接的 Perl 脚本,厉害之处在于:无论该TCP连接处于什么状态,都可以有效关闭TCP连接。
安装:
去官网 ( http://killcx.sourceforge.net/ ) 下载安装包,以下是官网的使用方法以及介绍,我直接复制下来了
-------------------------------------------------------------------------------------------------开始分割线-------------------------------------------------------------------------------------------
Killcx : close a TCP connection (for Linux)
Killcx is a Perl script to close a TCP connection under Linux, whatever its state is (half-open, established, waiting or closing state).
I - Overview :
Under Windows, closing a TCP connection is quite an easy task (see wKillcx),
but under Linux, it's a bit more complicated : one needs to sniff the
connection and extract the magic Acknowlegment and Sequence numbers from
a TCP packet.
Killcx works by creating a fake SYN packet with a bogus SeqNum, spoofing
the remote client IP/port and sending it to the server. It will fork a
child process that will capture the server response, extract the 2 magic
values from the ACK packet and use them to send a spoofed RST packet.
The connection will then be closed.
Note that the fake SYN packet is sent because even if the connection was
somehow stuck (no incoming/outgoing packets), killcx would still be
able to close it.
II - Parameters :
- syntax : killcx [dest_ip:dest_port] {interface}
dest_ip : remote IP
dest_port : remote port
interface (optional) : network interface (eth0, lo etc).
- example : killcx 120.121.122.123:1234
killcx 120.121.122.123:1234 eth0
III - Perl modules needed :
You need the following modules to run killcx :
* Net::RawIP : needed to create spoofed packets.
* Net::Pcap : needed to capture TCP packets.
* NetPacket::Ethernet : needed to decode TCP/IP packets.
IV - Various :
- interface : the interface parameter is optional. If not given, killcx
will use the first one it can find. Note that in many cases, you will
get much better results by using 'lo' (loopback interface), specially if
the connection is not yet or no longer in the ESTABLISHED state, for
instance SYN_RECV or TIME_WAIT.
- closing connection : killcx will close the connection on both sides,
your server and the remote IP, only if it is in the ESTABLISHED state.
For all other states, the connection will only be closed on your server
side. This doesn't matter too much because if the remote client sent
another TCP packet your server would reply with a RST one anyway, except
if it was a SYN packet of course.
- verboseness : killcx, both the parent and its child, will ouput all operations to the screen.
VI - Download :
killcx.tgz - v1.0.3 - (c) Jerome Bruandet
View source
-------------------------------------------------------------------------------------------------结束分割线-----------------------------------------------------------------------------------------------
官网明确指出需要安装几个perl依赖的库,
You need the following modules to run killcx :
* Net::RawIP : needed to create spoofed packets. * Net::Pcap : needed to capture TCP packets. * NetPacket::Ethernet : needed to decode TCP/IP packets.
如果你的服务器可以联网,那么你只需要做以下操作,利用CPAN安装这几个模块
# perl -MCPAN -e shell cpan> install Net::RawIP cpan> install Net::Pcap cpan> install NetPacket::Ethernet
直接下载也行
cpan -i Net::RawIP Net::Pcap NetPacket::Ethernet
我执行的时候报错,如下
# perl -MCPAN -e shell Can't locate CPAN.pm in @INC (@INC contains: /usr/local/lib64/perl5 /usr/local/share/perl5 /usr/lib64/perl5/vendor_perl /usr/share/perl5/vendor_perl /usr/lib64/perl5 /usr/share/perl5 .). BEGIN failed--compilation aborted.
说明你的服务器没有安装perl-CPAN
yum -y install perl-CPAN
安装成功以后,直接执行以上操作,继续安装即可,但是我的服务器没有网,我们需要去官网给的三个模块的链接手动下载,然后进行源码编译安装
直接去这个网站( https://metacpan.org/ )下载即可,而且官网有安装模块的教程,请自行查看
今天闲来无事,补充一下安装过程,没有连接互联网的情况,其实挺简单的
首先去官网下载三个perl的依赖库

搜索到之后,每个依赖有安装教程,比如这样的
按照别人给的命令安装就行,但是安装Net::Packet 和 Net::Pcap的时候报错了
CPAN installing Net::Pcap and Packet module failed due to lpcap
looking for -lpcap... no - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - You appear to lack the pcap(3) library. If it is installed in a non-standard locatio n, please try setting the LIBS and INC values on the command line. Or get the sources and install the pcap library from http://www.tcpdump.org/ If you install the pcap library using a system package, make sure to also install the corresponding -devel package, which contains the C headers needed to compile this module.
网上查到解决方法
回答1:
The README file for Net::Pcap shows how to tell Makefile.PL where to find the pcap library:
perl Makefile.PL INC=-I/opt/local/include/pcap LIBS='-L/opt/local/lib -lpcap'
(I've inserted your paths into the example.)
However, getting the cpan shell to pass those arguments to Makefile.PL is rather more complicated. You'd have to use the Distroprefs system and create a YAML file to supply the arguments. If you're not already familiar with Distroprefs, it'll probably be easier to just install Net::Pcap by hand.
回答2:
This fixed my issue:
yum -y install perl-Net-Pcap libpcap-devel
回答3:
On Ubuntu, just install libnet-pcap-perl.
第一个是回答原因,第二个是解决方法,需要联网下载 perl-Net-Pcap libpcap-devel
通过 yum --downloadonly --downloaddir 下载,不会的自行百度,需配置epel源
自己去清华的yum源( https://mirrors.tuna.tsinghua.edu.cn/epel/ )下载也行,自己选择方法
下载 killcx 安装包并解压,直接得到 killcx 脚本
----------------------------------分割线-----------------------------------------------
到这里就已经下载并且安装完成,就是使用办法了,官网已经有了
来个全局软链方便使用: ln -s /path_for_killcx /usr/bin/killcx
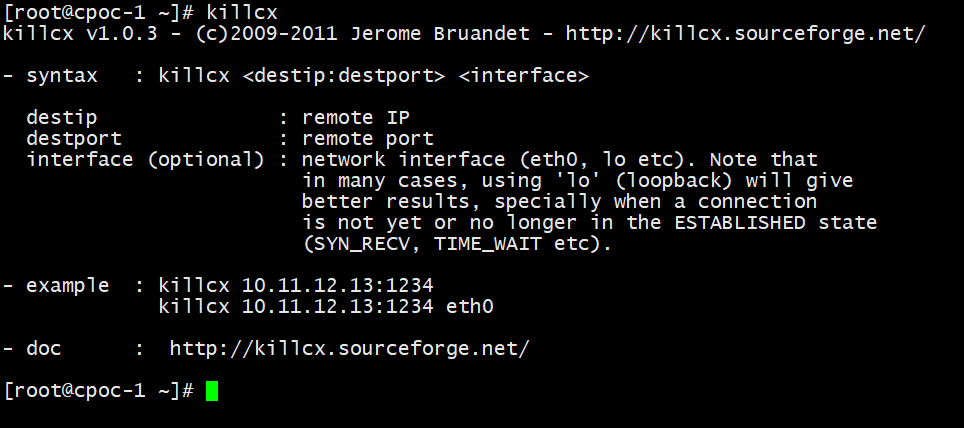
我已经验证了,有用的
参考:
https://www.e-learn.cn/content/wangluowenzhang/334934
http://www.blogdaren.com/post-2466.html