[反汇编练习] 160个CrackMe之037.
本系列文章的目的是从一个没有任何经验的新手的角度(其实就是我自己),一步步尝试将160个CrackMe全部破解,如果可以,通过任何方式写出一个类似于注册机的东西。
其中,文章中按照如下逻辑编排(解决如下问题):
1、使用什么环境和工具
2、程序分析
3、思路分析和破解流程
4、注册机的探索
----------------------------------
提醒各位看客: 如果文章中的逻辑看不明白,那你一定是没有亲手操刀!OD中的跳转提示很强大,只要你跟踪了,不用怎么看代码就理解了!
----------------------------------
1、工具和环境:
WinXP SP3 + 52Pojie六周年纪念版OD + PEID + 汇编金手指。
160个CrackMe的打包文件。
下载地址: http://pan.baidu.com/s/1xUWOY 密码: jbnq
注:
1、Win7系统对于模块和程序开启了随机初始地址的功能,会给分析带来很大的负担,所以不建议使用Win7进行分析。
2、以上工具都是在52PoJie论坛下的原版程序,NOD32不报毒,个人承诺绝对不会进行任何和木马病毒相关内容。
2、程序分析:
想要破解一个程序,必须先了解这个程序。所以,在破解过程中,对最初程序的分析很重要,他可以帮助我们理解作者的目的和意图,特别是对于注册码的处理细节,从而方便我们反向跟踪和推导。
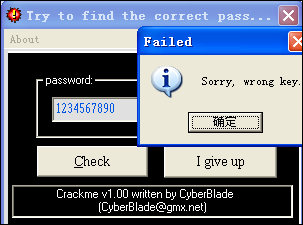
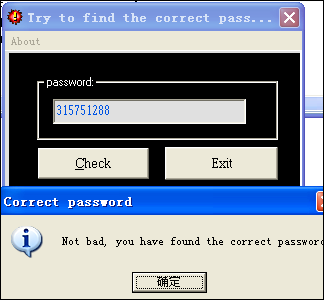
和上一节一样,打开CHM,选择第35个CyberBlade.1.exe,保存下来。运行程序,程序界面如下:
PEID: Microsoft Visual Basic 5.0 / 6.0
3、思路分析和破解流程
直接使用字符串查找,但是又因为他有信息框弹出,所以暂停,Ctrl+K,查看堆栈也可以的。
具体步骤…写的都不想写了!!
直接查看字符串吧! 右键->中文搜索插件->智能搜索:
随意看看,发现文本应该是不能少于9个,有很多的文本提示!
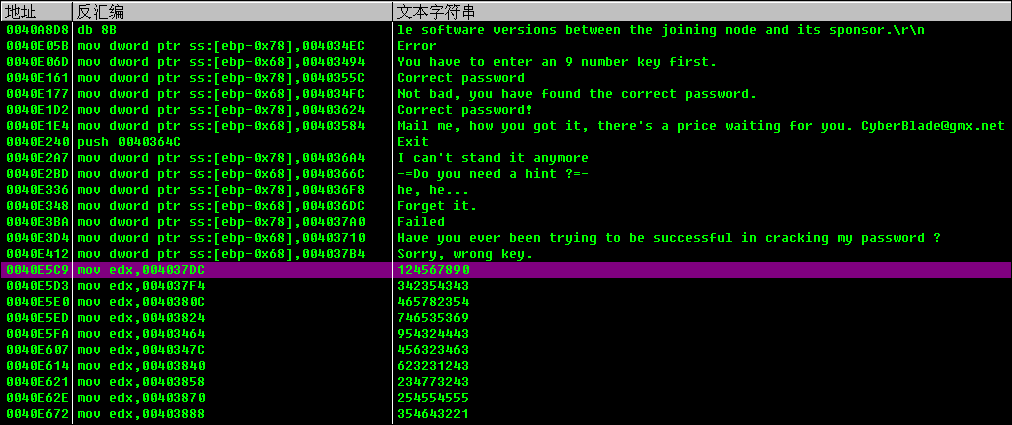
不管是文本查找,随意跟进去一个,或着,暂停,然后堆栈查看都可以找到这一块:
(代码很长,但是都是文本提示的内容)
0040E135 . F7DF neg edi 0040E137 . 66:85FF test di,di 0040E13A . 0F84 2C010000 je 0040E26C 0040E140 . BB 04000280 mov ebx,0x80020004 0040E145 . BF 0A000000 mov edi,0xA 0040E14A . BE 08000000 mov esi,0x8 0040E14F . 8D55 80 lea edx,dword ptr ss:[ebp-0x80] 0040E152 . 8D4D C0 lea ecx,dword ptr ss:[ebp-0x40] 0040E155 . 895D A8 mov dword ptr ss:[ebp-0x58],ebx 0040E158 . 897D A0 mov dword ptr ss:[ebp-0x60],edi 0040E15B . 895D B8 mov dword ptr ss:[ebp-0x48],ebx 0040E15E . 897D B0 mov dword ptr ss:[ebp-0x50],edi 0040E161 . C745 88 5C354>mov dword ptr ss:[ebp-0x78],0040355C ; UNICODE "Correct password" 0040E168 . 8975 80 mov dword ptr ss:[ebp-0x80],esi 0040E16B . FF15 78114100 call dword ptr ds:[<&MSVBVM50.__vbaVarDu>; msvbvm50.__vbaVarDup 0040E171 . 8D55 90 lea edx,dword ptr ss:[ebp-0x70] 0040E174 . 8D4D D0 lea ecx,dword ptr ss:[ebp-0x30] 0040E177 . C745 98 FC344>mov dword ptr ss:[ebp-0x68],004034FC ; UNICODE "Not bad, you have found the correct password." 0040E17E . 8975 90 mov dword ptr ss:[ebp-0x70],esi 0040E181 . FF15 78114100 call dword ptr ds:[<&MSVBVM50.__vbaVarDu>; msvbvm50.__vbaVarDup 0040E187 . 8D55 A0 lea edx,dword ptr ss:[ebp-0x60] 0040E18A . 8D45 B0 lea eax,dword ptr ss:[ebp-0x50] 0040E18D . 52 push edx 0040E18E . 8D4D C0 lea ecx,dword ptr ss:[ebp-0x40] 0040E191 . 50 push eax 0040E192 . 51 push ecx 0040E193 . 8D55 D0 lea edx,dword ptr ss:[ebp-0x30] 0040E196 . 6A 40 push 0x40 0040E198 . 52 push edx 0040E199 . FF15 04114100 call dword ptr ds:[<&MSVBVM50.#595>] ; msvbvm50.rtcMsgBox 0040E19F . 8D45 A0 lea eax,dword ptr ss:[ebp-0x60] 0040E1A2 . 8D4D B0 lea ecx,dword ptr ss:[ebp-0x50] 0040E1A5 . 50 push eax 0040E1A6 . 8D55 C0 lea edx,dword ptr ss:[ebp-0x40] 0040E1A9 . 51 push ecx 0040E1AA . 8D45 D0 lea eax,dword ptr ss:[ebp-0x30] 0040E1AD . 52 push edx 0040E1AE . 50 push eax 0040E1AF . 6A 04 push 0x4 0040E1B1 . FF15 EC104100 call dword ptr ds:[<&MSVBVM50.__vbaFreeV>; msvbvm50.__vbaFreeVarList 0040E1B7 . 897D A0 mov dword ptr ss:[ebp-0x60],edi 0040E1BA . 897D B0 mov dword ptr ss:[ebp-0x50],edi 0040E1BD . 8B3D 78114100 mov edi,dword ptr ds:[<&MSVBVM50.__vbaVa>; msvbvm50.__vbaVarDup 0040E1C3 . 83C4 14 add esp,0x14 0040E1C6 . 8D55 80 lea edx,dword ptr ss:[ebp-0x80] 0040E1C9 . 8D4D C0 lea ecx,dword ptr ss:[ebp-0x40] 0040E1CC . 895D A8 mov dword ptr ss:[ebp-0x58],ebx 0040E1CF . 895D B8 mov dword ptr ss:[ebp-0x48],ebx 0040E1D2 . C745 88 24364>mov dword ptr ss:[ebp-0x78],00403624 ; UNICODE "Correct password!" 0040E1D9 . 8975 80 mov dword ptr ss:[ebp-0x80],esi 0040E1DC . FFD7 call edi ; <&MSVBVM50.__vbaVarDup> 0040E1DE . 8D55 90 lea edx,dword ptr ss:[ebp-0x70] 0040E1E1 . 8D4D D0 lea ecx,dword ptr ss:[ebp-0x30] 0040E1E4 . C745 98 84354>mov dword ptr ss:[ebp-0x68],00403584 ; UNICODE "Mail me, how you got it, there's a price waiting f" 0040E1EB . 8975 90 mov dword ptr ss:[ebp-0x70],esi 0040E1EE . FFD7 call edi 0040E1F0 . 8D4D A0 lea ecx,dword ptr ss:[ebp-0x60] 0040E1F3 . 8D55 B0 lea edx,dword ptr ss:[ebp-0x50] 0040E1F6 . 51 push ecx 0040E1F7 . 8D45 C0 lea eax,dword ptr ss:[ebp-0x40] 0040E1FA . 52 push edx 0040E1FB . 50 push eax 0040E1FC . 8D4D D0 lea ecx,dword ptr ss:[ebp-0x30] 0040E1FF . 6A 40 push 0x40 0040E201 . 51 push ecx 0040E202 . FF15 04114100 call dword ptr ds:[<&MSVBVM50.#595>] ; msvbvm50.rtcMsgBox 0040E208 . 8D55 A0 lea edx,dword ptr ss:[ebp-0x60] 0040E20B . 8D45 B0 lea eax,dword ptr ss:[ebp-0x50] 0040E20E . 52 push edx 0040E20F . 8D4D C0 lea ecx,dword ptr ss:[ebp-0x40] 0040E212 . 50 push eax 0040E213 . 8D55 D0 lea edx,dword ptr ss:[ebp-0x30] 0040E216 . 51 push ecx 0040E217 . 52 push edx 0040E218 . 6A 04 push 0x4 0040E21A . FF15 EC104100 call dword ptr ds:[<&MSVBVM50.__vbaFreeV>; msvbvm50.__vbaFreeVarList 0040E220 . 8B45 08 mov eax,dword ptr ss:[ebp+0x8] 0040E223 . 8B8D 44FFFFFF mov ecx,dword ptr ss:[ebp-0xBC] 0040E229 . 83C4 14 add esp,0x14 0040E22C . 50 push eax 0040E22D . FF91 FC020000 call dword ptr ds:[ecx+0x2FC] 0040E233 . 8D55 E0 lea edx,dword ptr ss:[ebp-0x20] 0040E236 . 50 push eax 0040E237 . 52 push edx 0040E238 . FF15 00114100 call dword ptr ds:[<&MSVBVM50.__vbaObjSe>; msvbvm50.__vbaObjSet 0040E23E . 8BF0 mov esi,eax 0040E240 . 68 4C364000 push 0040364C ; UNICODE "Exit" 0040E245 . 56 push esi 0040E246 . 8B06 mov eax,dword ptr ds:[esi] 0040E248 . FF50 54 call dword ptr ds:[eax+0x54] 0040E24B . 85C0 test eax,eax 0040E24D . 7D 0F jge short 0040E25E 0040E24F . 6A 54 push 0x54 0040E251 . 68 58364000 push 00403658 0040E256 . 56 push esi 0040E257 . 50 push eax 0040E258 . FF15 F8104100 call dword ptr ds:[<&MSVBVM50.__vbaHresu>; msvbvm50.__vbaHresultCheckObj 0040E25E > 8D4D E0 lea ecx,dword ptr ss:[ebp-0x20] 0040E261 . FF15 90114100 call dword ptr ds:[<&MSVBVM50.__vbaFreeO>; msvbvm50.__vbaFreeObj 0040E267 . E9 E5010000 jmp 0040E451 0040E26C > 66:8B43 50 mov ax,word ptr ds:[ebx+0x50] 0040E270 . 66:40 inc ax 0040E272 . 0F80 83020000 jo 0040E4FB 0040E278 . 66:3D 0600 cmp ax,0x6 0040E27C . 66:8943 50 mov word ptr ds:[ebx+0x50],ax 0040E280 . 0F85 0F010000 jnz 0040E395 0040E286 . BB 04000280 mov ebx,0x80020004 0040E28B . BF 0A000000 mov edi,0xA 0040E290 . BE 08000000 mov esi,0x8 0040E295 . 8D55 80 lea edx,dword ptr ss:[ebp-0x80] 0040E298 . 8D4D C0 lea ecx,dword ptr ss:[ebp-0x40] 0040E29B . 895D A8 mov dword ptr ss:[ebp-0x58],ebx 0040E29E . 897D A0 mov dword ptr ss:[ebp-0x60],edi 0040E2A1 . 895D B8 mov dword ptr ss:[ebp-0x48],ebx 0040E2A4 . 897D B0 mov dword ptr ss:[ebp-0x50],edi 0040E2A7 . C745 88 A4364>mov dword ptr ss:[ebp-0x78],004036A4 ; UNICODE "I can't stand it anymore" 0040E2AE . 8975 80 mov dword ptr ss:[ebp-0x80],esi 0040E2B1 . FF15 78114100 call dword ptr ds:[<&MSVBVM50.__vbaVarDu>; msvbvm50.__vbaVarDup 0040E2B7 . 8D55 90 lea edx,dword ptr ss:[ebp-0x70] 0040E2BA . 8D4D D0 lea ecx,dword ptr ss:[ebp-0x30] 0040E2BD . C745 98 6C364>mov dword ptr ss:[ebp-0x68],0040366C ; UNICODE "-=Do you need a hint ?=-" 0040E2C4 . 8975 90 mov dword ptr ss:[ebp-0x70],esi 0040E2C7 . FF15 78114100 call dword ptr ds:[<&MSVBVM50.__vbaVarDu>; msvbvm50.__vbaVarDup 0040E2CD . 8D4D A0 lea ecx,dword ptr ss:[ebp-0x60] 0040E2D0 . 8D55 B0 lea edx,dword ptr ss:[ebp-0x50] 0040E2D3 . 51 push ecx 0040E2D4 . 8D45 C0 lea eax,dword ptr ss:[ebp-0x40] 0040E2D7 . 52 push edx 0040E2D8 . 50 push eax 0040E2D9 . 8D4D D0 lea ecx,dword ptr ss:[ebp-0x30] 0040E2DC . 6A 24 push 0x24 0040E2DE . 51 push ecx 0040E2DF . FF15 04114100 call dword ptr ds:[<&MSVBVM50.#595>] ; msvbvm50.rtcMsgBox 0040E2E5 . 33D2 xor edx,edx 0040E2E7 . 83F8 07 cmp eax,0x7 0040E2EA . 0F94C2 sete dl 0040E2ED . F7DA neg edx 0040E2EF . 8D45 A0 lea eax,dword ptr ss:[ebp-0x60] 0040E2F2 . 8995 5CFFFFFF mov dword ptr ss:[ebp-0xA4],edx 0040E2F8 . 8D4D B0 lea ecx,dword ptr ss:[ebp-0x50] 0040E2FB . 50 push eax 0040E2FC . 8D55 C0 lea edx,dword ptr ss:[ebp-0x40] 0040E2FF . 51 push ecx 0040E300 . 8D45 D0 lea eax,dword ptr ss:[ebp-0x30] 0040E303 . 52 push edx 0040E304 . 50 push eax 0040E305 . 6A 04 push 0x4 0040E307 . FF15 EC104100 call dword ptr ds:[<&MSVBVM50.__vbaFreeV>; msvbvm50.__vbaFreeVarList 0040E30D . 83C4 14 add esp,0x14 0040E310 . 66:83BD 5CFFF>cmp word ptr ss:[ebp-0xA4],0x0 0040E318 . 0F85 72010000 jnz 0040E490 0040E31E . 897D A0 mov dword ptr ss:[ebp-0x60],edi 0040E321 . 897D B0 mov dword ptr ss:[ebp-0x50],edi 0040E324 . 8B3D 78114100 mov edi,dword ptr ds:[<&MSVBVM50.__vbaVa>; msvbvm50.__vbaVarDup 0040E32A . 8D55 80 lea edx,dword ptr ss:[ebp-0x80] 0040E32D . 8D4D C0 lea ecx,dword ptr ss:[ebp-0x40] 0040E330 . 895D A8 mov dword ptr ss:[ebp-0x58],ebx 0040E333 . 895D B8 mov dword ptr ss:[ebp-0x48],ebx 0040E336 . C745 88 F8364>mov dword ptr ss:[ebp-0x78],004036F8 ; UNICODE "he, he..." 0040E33D . 8975 80 mov dword ptr ss:[ebp-0x80],esi 0040E340 . FFD7 call edi ; <&MSVBVM50.__vbaVarDup> 0040E342 . 8D55 90 lea edx,dword ptr ss:[ebp-0x70] 0040E345 . 8D4D D0 lea ecx,dword ptr ss:[ebp-0x30] 0040E348 . C745 98 DC364>mov dword ptr ss:[ebp-0x68],004036DC ; UNICODE "Forget it." 0040E34F . 8975 90 mov dword ptr ss:[ebp-0x70],esi 0040E352 . FFD7 call edi 0040E354 . 8D4D A0 lea ecx,dword ptr ss:[ebp-0x60] 0040E357 . 8D55 B0 lea edx,dword ptr ss:[ebp-0x50] 0040E35A . 51 push ecx 0040E35B . 8D45 C0 lea eax,dword ptr ss:[ebp-0x40] 0040E35E . 52 push edx 0040E35F . 50 push eax 0040E360 . 8D4D D0 lea ecx,dword ptr ss:[ebp-0x30] 0040E363 . 6A 40 push 0x40 0040E365 . 51 push ecx 0040E366 . FF15 04114100 call dword ptr ds:[<&MSVBVM50.#595>] ; msvbvm50.rtcMsgBox 0040E36C . 8D55 A0 lea edx,dword ptr ss:[ebp-0x60] 0040E36F . 8D45 B0 lea eax,dword ptr ss:[ebp-0x50] 0040E372 . 52 push edx 0040E373 . 8D4D C0 lea ecx,dword ptr ss:[ebp-0x40] 0040E376 . 50 push eax 0040E377 . 8D55 D0 lea edx,dword ptr ss:[ebp-0x30] 0040E37A . 51 push ecx 0040E37B . 52 push edx 0040E37C . 6A 04 push 0x4 0040E37E . FF15 EC104100 call dword ptr ds:[<&MSVBVM50.__vbaFreeV>; msvbvm50.__vbaFreeVarList 0040E384 . 8B45 08 mov eax,dword ptr ss:[ebp+0x8] 0040E387 . 83C4 14 add esp,0x14 0040E38A . 66:C740 50 00>mov word ptr ds:[eax+0x50],0x0 0040E390 . E9 BC000000 jmp 0040E451 0040E395 > BF 0A000000 mov edi,0xA 0040E39A . BB 04000280 mov ebx,0x80020004 0040E39F . BE 08000000 mov esi,0x8 0040E3A4 . 66:3D 0300 cmp ax,0x3 0040E3A8 . 897D A0 mov dword ptr ss:[ebp-0x60],edi 0040E3AB . 897D B0 mov dword ptr ss:[ebp-0x50],edi 0040E3AE . 8B3D 78114100 mov edi,dword ptr ds:[<&MSVBVM50.__vbaVa>; msvbvm50.__vbaVarDup 0040E3B4 . 895D A8 mov dword ptr ss:[ebp-0x58],ebx 0040E3B7 . 895D B8 mov dword ptr ss:[ebp-0x48],ebx 0040E3BA . C745 88 A0374>mov dword ptr ss:[ebp-0x78],004037A0 ; UNICODE "Failed" 0040E3C1 . 8975 80 mov dword ptr ss:[ebp-0x80],esi 0040E3C4 . 8D55 80 lea edx,dword ptr ss:[ebp-0x80] 0040E3C7 . 8D4D C0 lea ecx,dword ptr ss:[ebp-0x40] 0040E3CA . 7E 3E jle short 0040E40A 0040E3CC . FFD7 call edi ; <&MSVBVM50.__vbaVarDup> 0040E3CE . 8D55 90 lea edx,dword ptr ss:[ebp-0x70] 0040E3D1 . 8D4D D0 lea ecx,dword ptr ss:[ebp-0x30] 0040E3D4 . C745 98 10374>mov dword ptr ss:[ebp-0x68],00403710 ; UNICODE "Have you ever been trying to be successful in crac" 0040E3DB . 8975 90 mov dword ptr ss:[ebp-0x70],esi 0040E3DE . FFD7 call edi 0040E3E0 . 8D4D A0 lea ecx,dword ptr ss:[ebp-0x60] 0040E3E3 . 8D55 B0 lea edx,dword ptr ss:[ebp-0x50] 0040E3E6 . 51 push ecx 0040E3E7 . 8D45 C0 lea eax,dword ptr ss:[ebp-0x40] 0040E3EA . 52 push edx 0040E3EB . 50 push eax 0040E3EC . 8D4D D0 lea ecx,dword ptr ss:[ebp-0x30] 0040E3EF . 6A 20 push 0x20 0040E3F1 . 51 push ecx 0040E3F2 . FF15 04114100 call dword ptr ds:[<&MSVBVM50.#595>] ; msvbvm50.rtcMsgBox 0040E3F8 . 8D55 A0 lea edx,dword ptr ss:[ebp-0x60] 0040E3FB . 8D45 B0 lea eax,dword ptr ss:[ebp-0x50] 0040E3FE . 52 push edx 0040E3FF . 8D4D C0 lea ecx,dword ptr ss:[ebp-0x40] 0040E402 . 50 push eax 0040E403 . 8D55 D0 lea edx,dword ptr ss:[ebp-0x30] 0040E406 . 51 push ecx 0040E407 . 52 push edx 0040E408 . EB 3C jmp short 0040E446 0040E40A > FFD7 call edi 0040E40C . 8D55 90 lea edx,dword ptr ss:[ebp-0x70] 0040E40F . 8D4D D0 lea ecx,dword ptr ss:[ebp-0x30] 0040E412 . C745 98 B4374>mov dword ptr ss:[ebp-0x68],004037B4 ; UNICODE "Sorry, wrong key." 0040E419 . 8975 90 mov dword ptr ss:[ebp-0x70],esi 0040E41C . FFD7 call edi 0040E41E . 8D45 A0 lea eax,dword ptr ss:[ebp-0x60] 0040E421 . 8D4D B0 lea ecx,dword ptr ss:[ebp-0x50] 0040E424 . 50 push eax 0040E425 . 8D55 C0 lea edx,dword ptr ss:[ebp-0x40] 0040E428 . 51 push ecx 0040E429 . 52 push edx 0040E42A . 8D45 D0 lea eax,dword ptr ss:[ebp-0x30] 0040E42D . 6A 40 push 0x40 0040E42F . 50 push eax 0040E430 . FF15 04114100 call dword ptr ds:[<&MSVBVM50.#595>] ; msvbvm50.rtcMsgBox
根据文本提示,Correct password,找到对应的跳转 0040E13A /0F84 2C010000 je 0040E26C
爆破:
选中 0040E13A /0F84 2C010000 je 0040E26C 右键->Binary-> NOP填充
4、注册机的探索
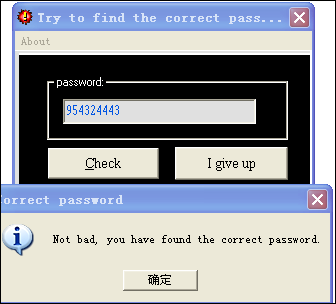
关键跳转附近, 算法处理如下:
0040E0E2 . FF15 F8104100 call dword ptr ds:[<&MSVBVM50.__vbaHresu>; msvbvm50.__vbaHresultCheckObj 0040E0E8 > 8B4D E4 mov ecx,dword ptr ss:[ebp-0x1C] 0040E0EB . 51 push ecx ; /Arg1="123456789" 0040E0EC . FF15 5C114100 call dword ptr ds:[<&MSVBVM50.__vbaR8Str>; \__vbaR8Str 0040E0F2 . DB43 4C fild dword ptr ds:[ebx+0x4C] ; // ST0 = xxx, 压栈后ST0 = 12D1FB78 = 315751288 0040E0F5 . DD9D 38FFFFFF fstp qword ptr ss:[ebp-0xC8] 0040E0FB . DCA5 38FFFFFF fsub qword ptr ss:[ebp-0xC8] ; // 两个数减,315751288 - 123456789 = -192294499 ? 负的? 0040E101 . DFE0 fstsw ax 0040E103 . A8 0D test al,0xD ; // 浮点数错误检测 0040E105 . 0F85 EB030000 jnz 0040E4F6 0040E10B . FF15 14114100 call dword ptr ds:[<&MSVBVM50.__vbaFpR8>>; msvbvm50.__vbaFpR8 0040E111 . DC1D 08104000 fcomp qword ptr ds:[0x401008] ; // 浮点数比较然后出栈 0040E117 . DFE0 fstsw ax 0040E119 . F6C4 40 test ah,0x40 0040E11C . 74 05 je short 0040E123 ; // 这个条件必须成立,否则edi=1就失败了 0040E11E . BF 01000000 mov edi,0x1 0040E123 > 8D4D E4 lea ecx,dword ptr ss:[ebp-0x1C] 0040E126 . FF15 8C114100 call dword ptr ds:[<&MSVBVM50.__vbaFreeS>; msvbvm50.__vbaFreeStr 0040E12C . 8D4D E0 lea ecx,dword ptr ss:[ebp-0x20] 0040E12F . FF15 90114100 call dword ptr ds:[<&MSVBVM50.__vbaFreeO>; msvbvm50.__vbaFreeObj 0040E135 . F7DF neg edi ; // edi = 1 则就失败了 0040E137 . 66:85FF test di,di 0040E13A 0F84 2C010000 je 0040E26C ; // 在这里爆破
核心的一个内容是fcomp命令,其实不是它多难,只是我以前都没见过,然后找啊找啊找!!
看雪论坛找到fcomp问题:
条件 C3 C2 C0
ST(0) > SRC 0 0 0
ST(0) < SRC 0 0 1
ST(0) SRC 1 0 0
无序* 1 1 1
有了。
FPU的状态字呀。貌似弹栈就是把st(0)的数据清除了、
0040E119 . F6C4 40 test ah,0x40
0040E11C . /74 05 je short 0040E123 ; // 这个条件必须成立,否则edi=1就失败了
所以,ST(0) 必须等于[0x401008]的值 315751288
BY 笨笨D幸福