Lab 1-3
Analyze the file Lab01-03.exe.
Questions and Short Answers
-
Upload the Lab01-03.exe file to http://www.VirusTotal.com/. Does it match any existing antivirus definitions?
A: As of this writing, 25 of 43 virus engines identify this sample as malware.
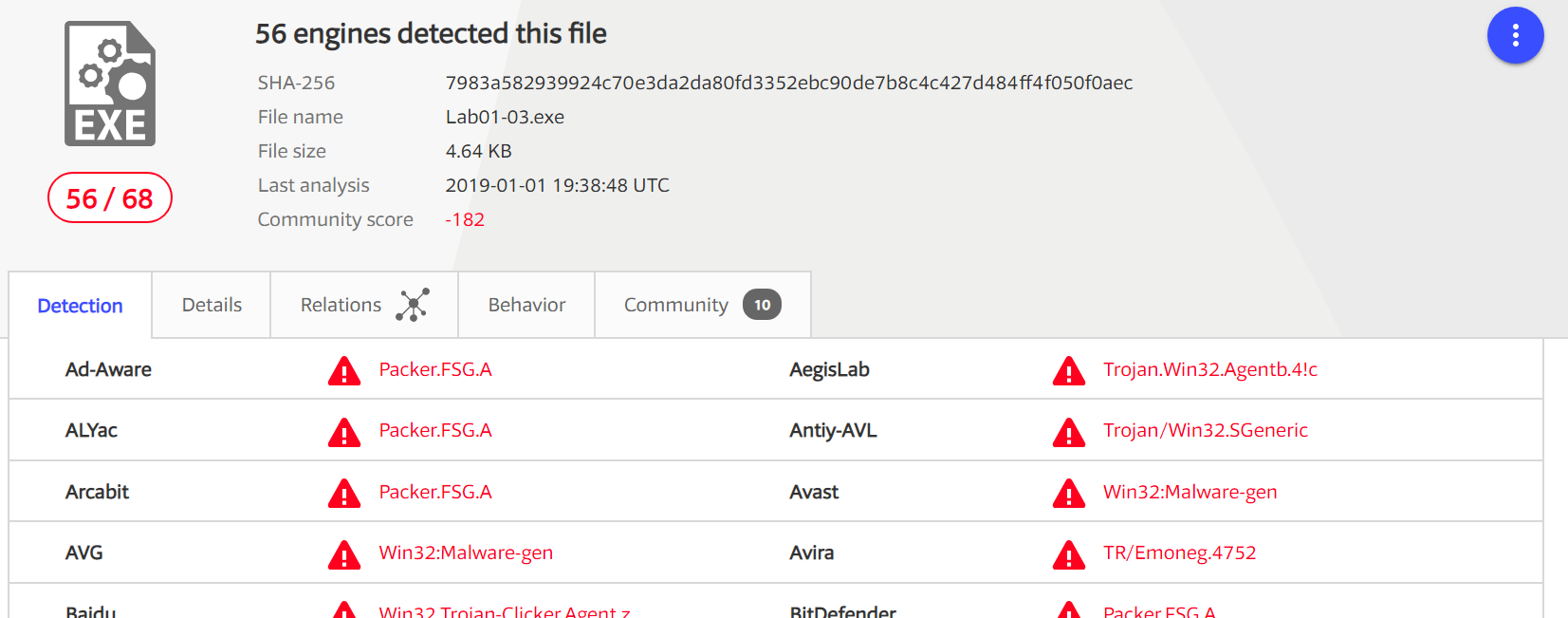
注:在写这篇博客时的数据是 68 反病毒引擎里面 56 个是反病毒签名。
-
Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
A: The file is packed, but we can’t unpack it at this time.
-
Do any imports hint at this program’s functionality? If so, which imports are they and what do they tell you?
A: This question can’t be answered without unpacking the file.
-
What host- or network-based indicators could be used to identify this malware on infected machines?
A: This question can’t be answered without unpacking the file.
Detailed Analysis
For the file Lab01-03.exe, VirusTotal.com reports a variety of different signatures with vague-sounding names. The most common signature is that of a file packed with the FSG packer.
When we open the file in PEview, we see several indications that the file is packed. The first is that the file sections have no names. Next, we see that the first section has a virtual size of 0x3000, but a raw data size of 0. We run PEiD to confirm, and it identifies the packer as FSG 1.0 -> dulek/xt.
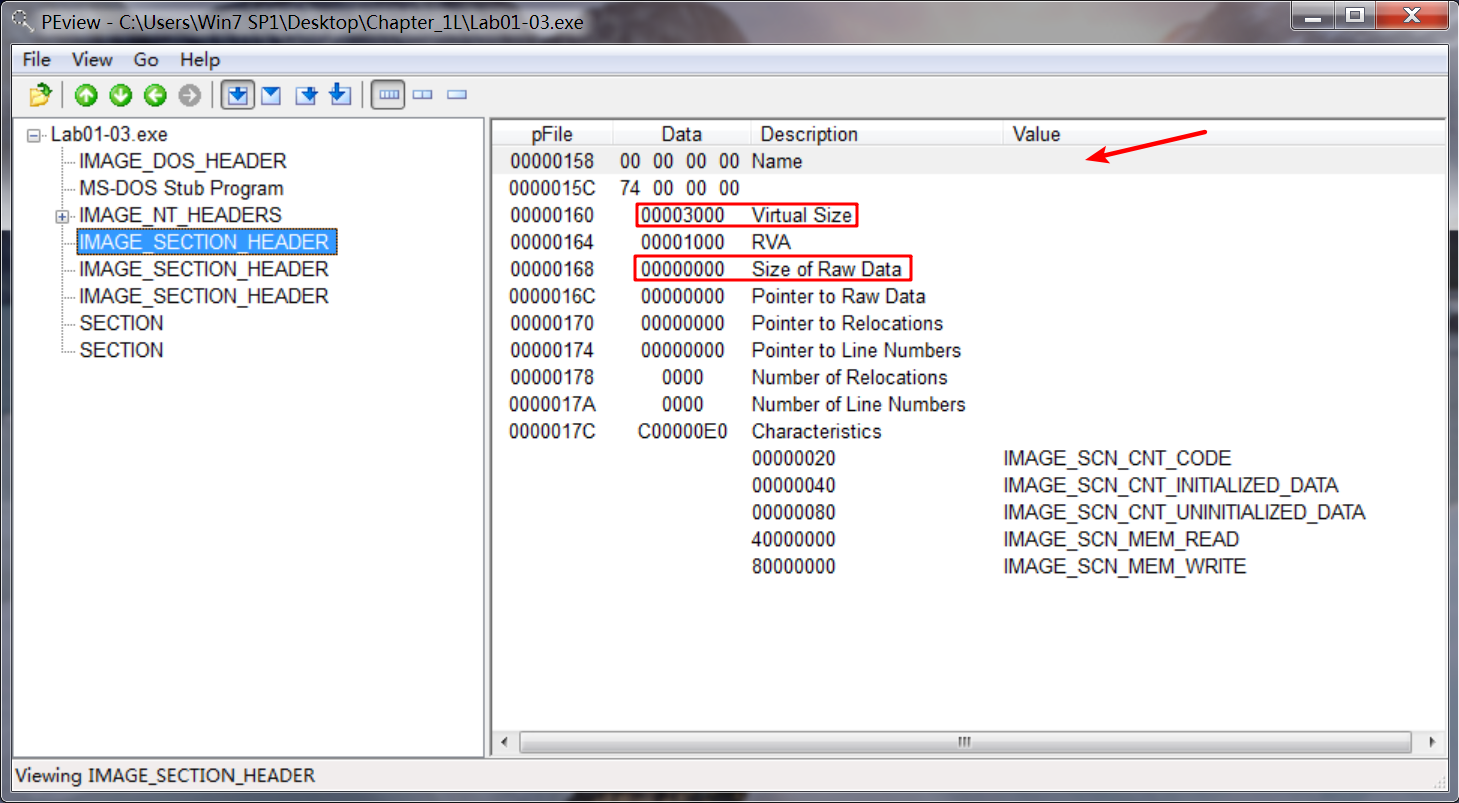
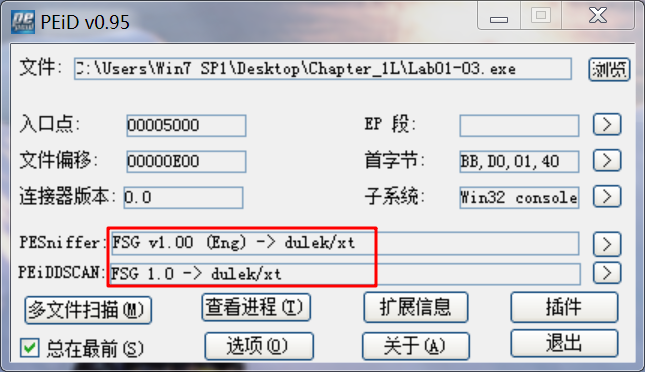
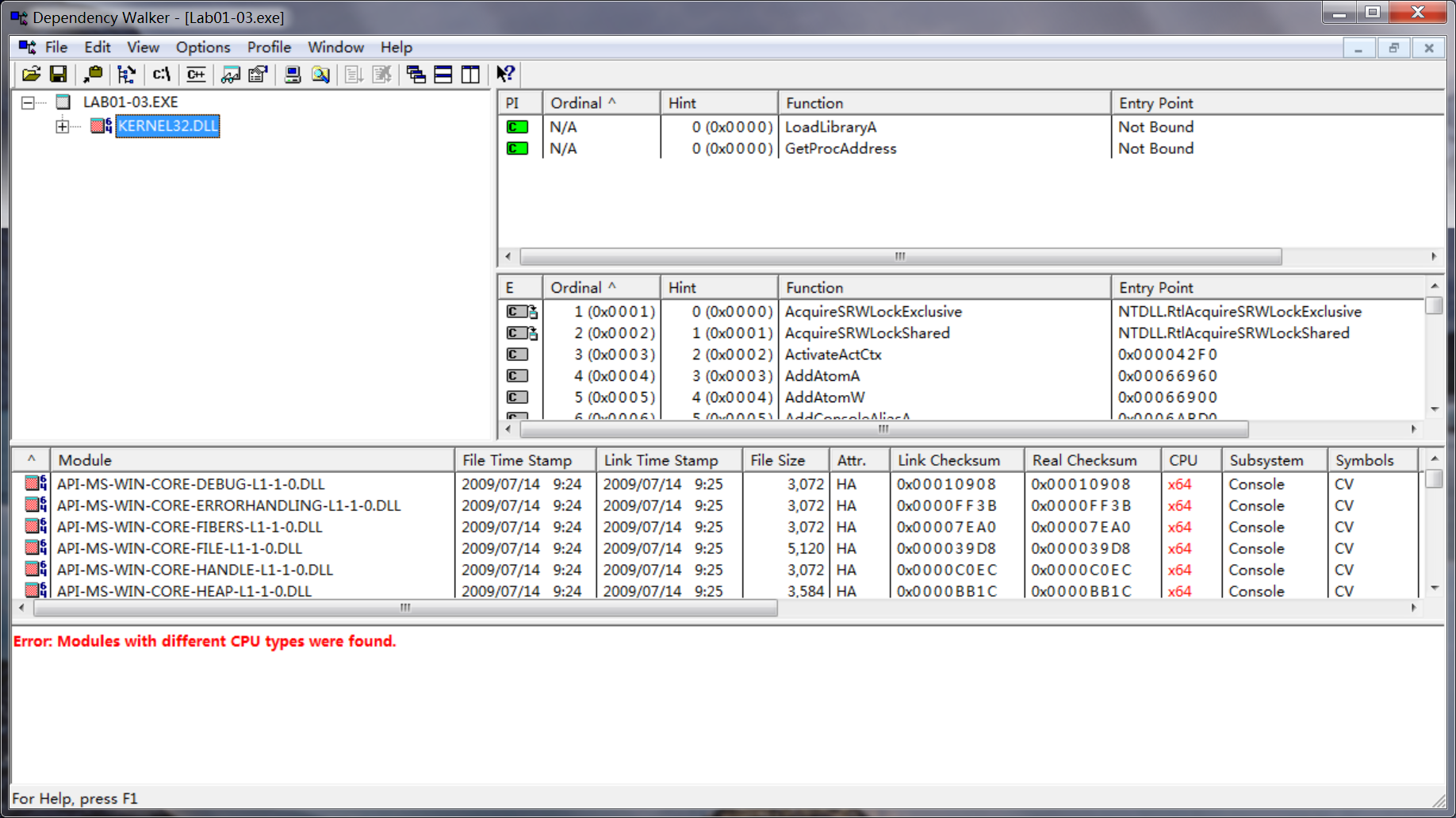
To confirm that the file is packed, we search for the imports, but there doesn’t seem to be an import table. An executable file without an import table is extremely rare, and its absence tells us that we should try another tool, because PEview is having trouble processing this file.
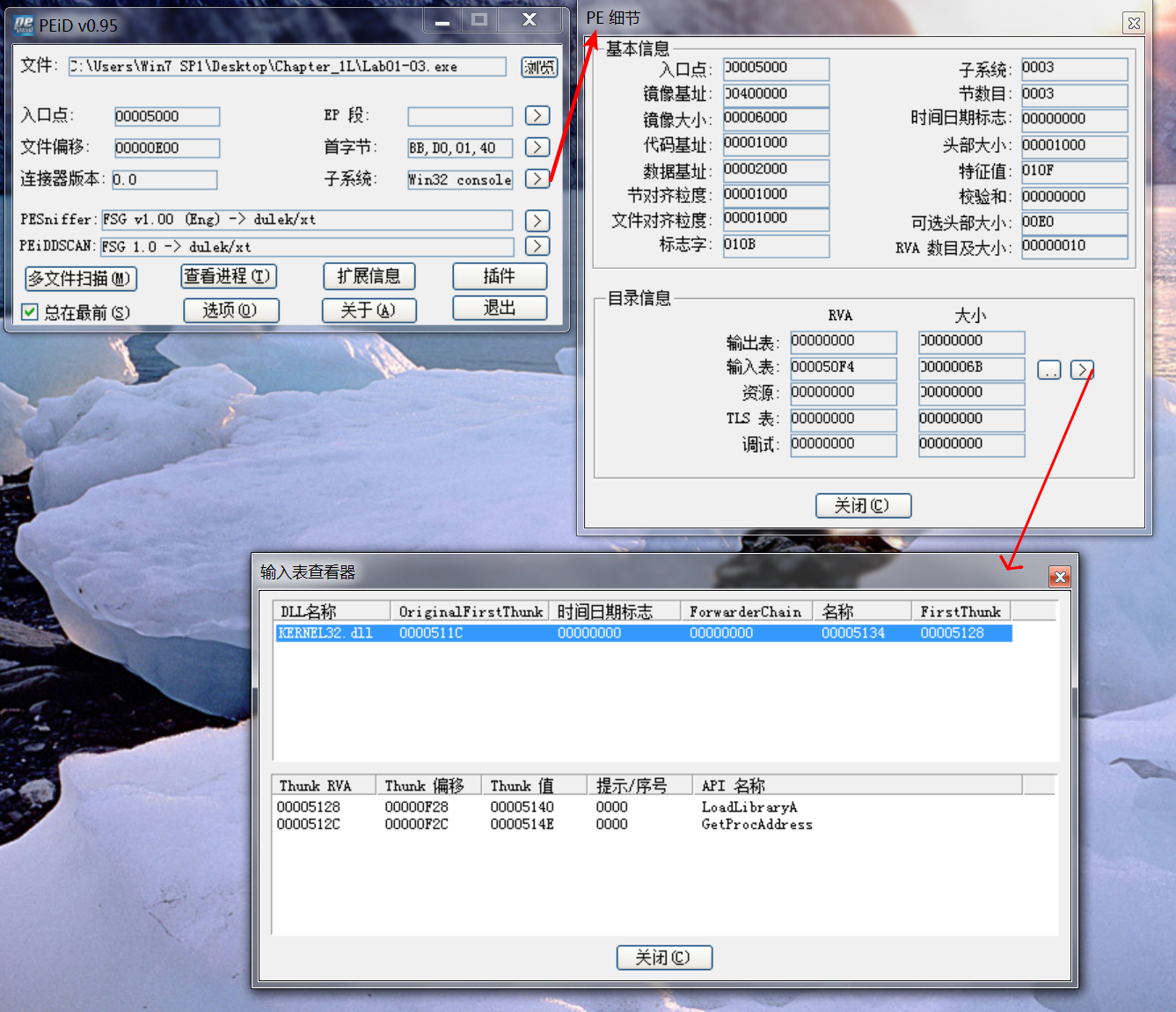
We open the file with Dependency Walker, and see that it does have an import table, but it imports only two functions: LoadLibrary and GetProcAddress. Packed files often import only these two functions, which further indicate that this file is packed. We can try to unpack the file using UPX, but we know that the file is packed with FSG, rather than UPX. We’ll return to this file in Chapter 18, once we have covered the skills to unpack it.