1 - Fidler
python,给了源代码,第一部分为输入密码,直接打印出来
def password_check():
altered_key = 'hiptu'
key = ''.join([chr(ord(x) - 1) for x in altered_key])
print(key)
password_check()
第二部分,胜利后会解密flag,需要传入一个值
def decode_flag(frob):
last_value = frob
encoded_flag = [1135, 1038, 1126, 1028, 1117, 1071, 1094, 1077, 1121, 1087, 1110, 1092, 1072, 1095, 1090, 1027,
1127, 1040, 1137, 1030, 1127, 1099, 1062, 1101, 1123, 1027, 1136, 1054]
decoded_flag = []
for i in range(len(encoded_flag)):
c = encoded_flag[i]
val = (c - ((i%2)*1 + (i%3)*2)) ^ last_value
decoded_flag.append(val)
last_value = c
return ''.join([chr(x) for x in decoded_flag])
往上找发现
target_amount = (2**36) + (2**35)
if current_coins > (target_amount - 2**20):
while current_coins >= (target_amount + 2**20):
current_coins -= 2**20
victory_screen(int(current_coins / 10**8))
return
算出为1030,解密得flag
2 garbage
题目说文件不全,查看一下发现是upx过的程序,用010editor打开,看看数据目录表

第二个结构指向导入表,查看一下RVA为0x1929c处
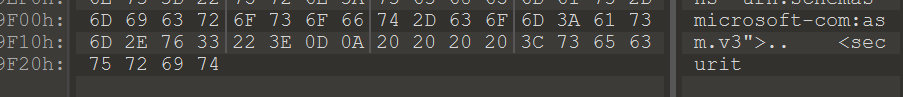
发现后面被删掉了,资源也不全,于是要先想办法重建这里,我直接选择自己写了一个小程序加壳,把资源替换了
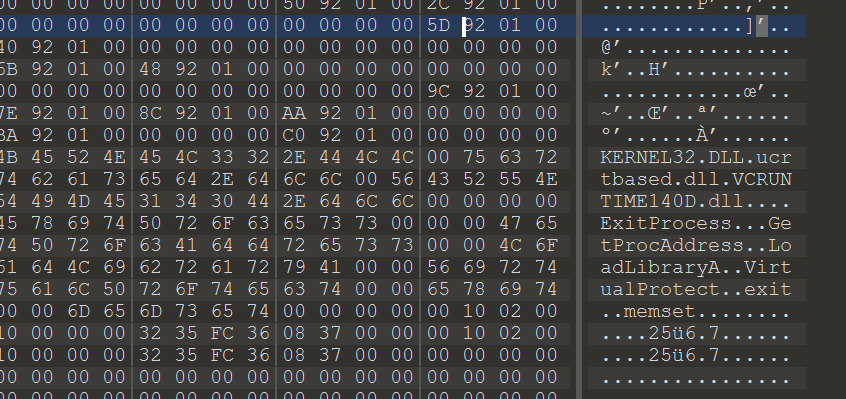
之后要改一下导入表中的RVA,同时把数据目录表第四个DWORD改为0xF0
之后upx脱壳,发现无法运行,拖进ida,根据字符串找到可疑函数
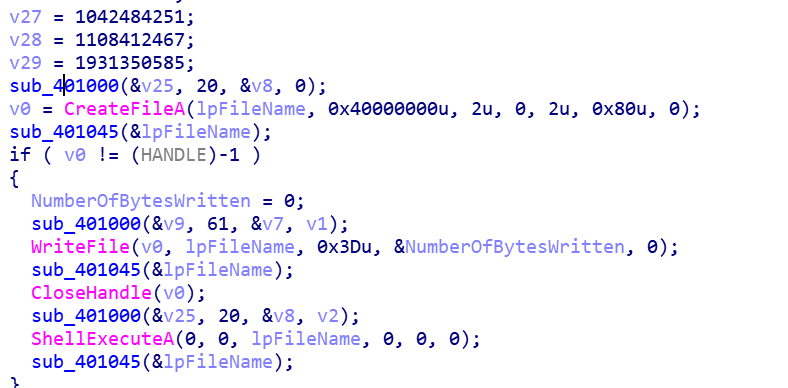
对数据进行了一些处理后放入一个文件中并运行此文件,写个脚本处理数据
v25=[0x38,0x0e,0x02,0x3B,0x19,0x3b,0x1b,0x34,0x1b,0x0c,0x23,0x3E,0x33,0x08,0x11,0x42,0x39,0x12,0x1e,0x73] v8="KglPFOsQDxBPXmclOpmsdLDEPMRWbMDzwhDGOyqAkVMRvnBeIkpZIhFznwVylfjrkqprBPAdPuaiVoVugQAlyOQQtxBNsTdPZgDH " v7="nPTnaGLkIqdcQwvieFQKGcTGOTbfMjDNmvibfBDdFBhoPaBbtfQuuGWYomtqTFqvBSKdUMmciqKSGZaosWCSoZlcIlyQpOwkcAgw " a=[] #for i in range(20): # a.append(hex(v25[i]^ord(v8[i]))) #print(a) v9 =[0x23,0x23,0x33,0x2c, 0x0e,0x3f,0x64,0x49, 0x0a,0x1e,0x0a,0x04, 0x23,0x16,0x02,0x1a, 0x44,0x66,0x08,0x24, 0x32,0x11,0x74,0x2c, 0x2a,0x2d,0x42,0x0f, 0x3e,0x50,0x64,0x0d, 0x5d,0x04,0x1b,0x17, 0x16,0x36,0x03,0x05, 0x34,0x20,0x09,0x08, 0x63,0x21,0x24,0x0e, 0x15,0x14,0x34,0x58, 0x1a,0x29,0x79,0x3a, 0x00,0x00,0x56,0x58, 0x54] for i in range(len(v9)): print(chr(v9[i]^ord(v7[i])),end="")
3 wednesday
游戏,提示只逆mydude.exe,经过一番寻找,判断处为
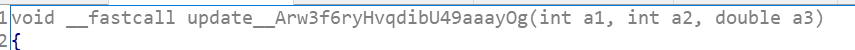

当分数为296时胜利,但如果直接修改分数是无法得到flag的,可以推测,每获得一次分数,会进行一些解密的操作
查看游戏资源,有m的地方要蹲,有f的地方要跳,且每次跳和蹲次序是不变的,可以想到有一张0和1组成的地图,于是寻找
有了地图,第一个想法是控制地图生成,但依然不能获得flag,只好想别的方法
#include<windows.h>
int map[] = {
0,0,1,1,0,0,0,1,0,1,1,1,0,1,0,0,
0,1,0,1,1,1,1,1,0,1,1,0,1,0,0,1,
0,0,1,1,0,1,0,1,0,1,0,1,1,1,1,1,
0,1,1,1,0,1,1,1,
0,1,0,0,0,1,0,1,0,1,1,0,0,1,0,0,
0,1,1,0,1,1,1,0,0,0,1,1,0,0,1,1,
0,1,1,1,0,0,1,1,0,1,1,0,0,1,0,0,
0,0,1,1,0,1,0,0,0,1,1,1,1,0,0,1,
0,1,0,1,1,1,1,1,0,1,1,0,1,1,0,1,
0,1,0,1,1,0,0,1,0,1,0,1,1,1,1,1,
0,1,0,0,0,1,0,0,0,1,1,1,0,1,0,1,
0,1,1,0,0,1,0,0,0,0,1,1,0,0,1,1,
0,1,1,1,0,0,1,1,0,1,0,0,0,0,0,0,
0,1,1,0,0,1,1,0,0,1,1,0,1,1,0,0,
0,1,1,0,0,0,0,1,0,1,1,1,0,0,1,0,
0,1,1,0,0,1,0,1,0,0,1,0,1,1,0,1,
0,1,1,0,1,1,1,1,0,1,1,0,1,1,1,0,
0,0,1,0,1,1,1,0,0,1,1,0,0,0,1,1,
0,1,1,0,1,1,1,1,0,1,1,0,1,1,0,1,
};
void jump(HWND hwnd) {
SendMessage(hwnd, WM_KEYUP, VK_DOWN, NULL);
SendMessage(hwnd, WM_KEYDOWN, VK_UP, NULL);
SendMessage(hwnd, WM_KEYUP, VK_UP, NULL);
}
int main(void) {
int length = sizeof(map) / sizeof(map[0]);
HWND hwnd = FindWindow(NULL, L"Wednesday");
if (hwnd)
{
SendMessage(hwnd, WM_KEYDOWN, VK_DOWN, NULL);
Sleep(2100);
int k = 1360;
for (int i = 0; i < length; i += 2) {
if (map[i] == 0 && map[i + 1] == 0) {
Sleep(k);
Sleep(2750);
}
if (map[i] == 0 && map[i + 1] == 1) {
Sleep(k);
jump(hwnd);
Sleep(800);
SendMessage(hwnd, WM_KEYDOWN, VK_DOWN, NULL);
Sleep(1950);
}
if (map[i] == 1 && map[i + 1] == 0) {
jump(hwnd);
Sleep(800);
SendMessage(hwnd, WM_KEYDOWN, VK_DOWN, NULL);
Sleep(k);
Sleep(1950);
}
if (map[i] == 1 && map[i + 1] == 1) {
jump(hwnd);
Sleep(k);
jump(hwnd);
Sleep(800);
SendMessage(hwnd, WM_KEYDOWN, VK_DOWN, NULL);
Sleep(1950);
}
if (i == 10) k -= 12;
if (i == 20) k -= 26;
if (i == 30) k -= 12;
}
SendMessage(hwnd, WM_KEYUP, VK_DOWN, NULL);
}
return 0;
}
不过失败了,速度总是控制不好,每次到40分左右就死了。。。不过提到速度,我想起了变速齿轮
直接调慢速度,玩出flag