一、数字证书
1、数字证书实际上是存在于计算机上的一个记录,是由CA签发的一个声明,证明证书主体("证书申请者"拥有了证书后即成为"证书主体")与证书中所包含的公钥的惟一对应关系
2、数字证书包含的内容:
- 申请者的名称及相关信息
- 申请者的地址信息
- 申请者的公钥
- 签发证书的CA的名称
- 签发证书的CA的数字签名(用发证机关的私钥加密的特征码)
- 证书有效期
3、x509证书的包含的内容:
- 公钥及其有效期限
- 证书的合法拥有者
- 证书该如何被使用
- CA的信息
- CA签名的校验码
4、CRL:证书吊销列表;CRL中记录的是已经发出去的、没有过期的但已经被撤销的证书
二、PKI
1、PKI:Public Key Infrastructure
2、 PKI的核心就是CA及其信任关系
3、PKI的实现架构
- TLS/SSL:使用x509证书
- OpenGPG
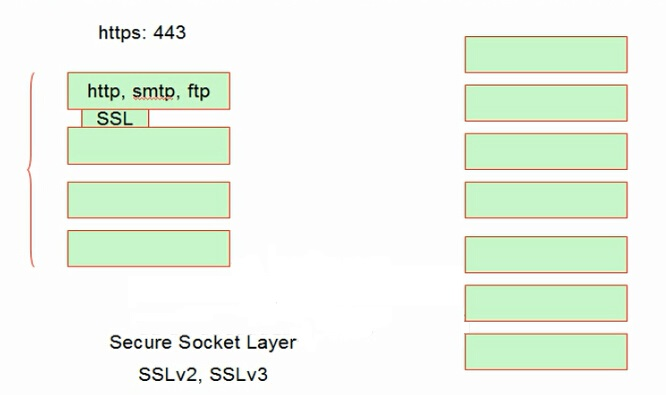
- SSL:Secure Socket Layer,安全的套接字层;只是一个库,可以将http、smtp、ftp等应用层协议封装成https、smtps、ftps等
- TLS:Transport Layer Security,TLSv1版本相当于SSLv3
三、CA
1、 CA(Certificate Authority)是数字证书认证中心的简称,是指发放、管理、废除数据证书的机构
2、CA的作用是检查证书持有者身份的合法性,并签发证书(在证书上签字),以防证书被伪造或篡改,以及对证书和密钥进行管理
四、证书申请及签署步骤
1、生成申请请求
2、RA核验
3、CA签署
4、获取证书
五、openssl
1、对称加密的实现工具有openssl和gpg两种
- openssl:OpenSSL是ssl的开源实现,是一个软件,由三部分组成:
- libcrypto:加密库
- libssl:TLS/SSL协议的实现。基于会话的实现了身份认证、数据机密性和会话完整性的TLS/SSL库
- openssl:多用途命令行工具。能够实现单向加密、对称加密、非对称加密、生成一对密钥、私有证书颁发机构等功能
2、OpenSSL
- 语法:openssl command [ command_opts ] [ command_args ]
- command:
- enc:加密/解密
- -e:加密
- -d:解密
- -new:生成新证书签署请求
- -x509:专用于CA生成自签证书
- -key:生成请求时用到的私钥文件
- -days number:证书的有效期限
- -out /path/to/somecertfile:证书的保存路径
3、x509证书管理:
- -in /path/from/cert_file -noout -text|-subject|-serial #查看证书中的信息
- crl:管理吊销证书列表
- -in /path/from/crl_file.crl -noout -text #查看crl文件
- ca:管理CA
六、使用openssl创建私有CA
1、CA的配置文件:/etc/pki/tls/openssl.cnf
-
[root@localhost ~]# cd /etc/pki/tls/
[root@localhost tls]# vim openssl.cnf
............
# Load default TLS policy configuration
openssl_conf = default_modules
[ default_modules ]
ssl_conf = ssl_module
[ ssl_module ]
system_default = crypto_policy
[ crypto_policy ]
.include /etc/crypto-policies/back-ends/opensslcnf.config
[ new_oids ]
.............
2、使用OpenSSL给CA创建一对密钥
//首先在/etc/pki文件下创建CA目录
[root@localhost ~]# cd /etc/pki/
[root@localhost pki]# mkdir CA
//进入CA目录,首先创建private目录,然后在该目录下创建密钥文件(此步骤必须做)
[root@localhost pki]# cd CA/
[root@localhost CA]# mkdir private
[root@localhost CA]# (umask 077;openssl genrsa -out private/cakey.pem 2048) //OpenSSL生成密钥,括号*必须要*
Generating RSA private key, 2048 bit long modulus (2 primes)
.........................+++++
............+++++
e is 65537 (0x010001)
//创建成功
[root@localhost CA]# ls
cakey.pem
//提取公钥,该步骤是查看公钥,可以不做
[root@localhost CA]# openssl rsa -in private/cakey.pem -pubout
writing RSA key
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAvhWEEfPKL8rtAuEqVdeu
yXRNHCVVHFimq32RD+YtXXJt63Rgl2/jAkTETxBUSlvmqfxL2WN3AKiRzvyqMpxS
skRwda3HHGezWSMNbSbl9VzL+/7KOOgOgmow+HRuFzWzW17MCy98I12eUpldFWFm
BcjOX/rcBynWJP96r/9wFqzsQ8JpJ5cUeDlUul91pyh5NCsXpr3RhMO0ZaITttj7
r3/yDdNmpVHxVtD6o9oGeNF9ihE1/62vgAsDxoPEmsv7xRbouMQPhlugEeXxgc6L
Z+AfvmuycozyhxaKWTDX+XIubcWd7Wv3i21V5IO36D4sSya/WsWU9CZ34QBkrZ6M
8wIDAQAB
-----END PUBLIC KEY-----
3、使用OpenSSL给CA生成自签署证书
//生成自签署证书
[root@localhost CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 365
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN //国家的名称,使用两个字母表示
State or Province Name (full name) []:HB //省份的名称,同样也使用两个字母表示
Locality Name (eg, city) [Default City]:WH //城市的名称,同样使用两个字母表示
Organization Name (eg, company) [Default Company Ltd]:www.qiangge.com //公司的名称(一般设主机名)
Organizational Unit Name (eg, section) []:www.qiangge.com //部门的名称(一般设与公司名称一样)
Common Name (eg, your name or your server's hostname) []:www.qiangge.com //主机的名称,就是自己的网站的域名
Email Address []:123@123.com //自己的邮箱地址
//读取证书内容,该步骤可以不做,只是查看一下
[root@localhost CA]# openssl x509 -text -in cacert.pem
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
1b:7d:ab:b9:fd:4a:03:ab:cc:e5:e1:7f:2b:75:7f:66:7b:1d:49:bb
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = CN, ST = HB, L = WH, O = www.qiangge.com, OU = www.qiangge.com, CN = www.qiangge.com, emailAddress = 123@123.com
Validity
Not Before: Aug 25 09:18:12 2020 GMT
Not After : Aug 25 09:18:12 2021 GMT
Subject: C = CN, ST = HB, L = WH, O = www.qiangge.com, OU = www.qiangge.com, CN = www.qiangge.com, emailAddress = 123@123.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
.............
4、在CA目录下创建certs、newcerts、crl三个目录
[root@localhost CA]# pwd
/etc/pki/CA
[root@localhost CA]# mkdir certs newcerts crl
[root@localhost CA]# ls
cacert.pem certs crl newcerts private
5、在CA目录下创建index.txt和serial并给予序列号
[root@localhost CA]# touch index.txt && echo 01 > serial
[root@localhost CA]# ls
cacert.pem certs crl index.txt newcerts serial private
[root@localhost CA]# cat serial
01
七、使用OpenSSL给客户端生成证书签署
1、使用OpenSSL给客户端(需求者)生成密钥文件(我这使用httpd作客户端)
//首先在/etc/httpd/目录下创建一个ssl目录,用来存放密钥文件
[root@localhost ~]# cd /etc/httpd/
[root@localhost httpd]# mkdir ssl
[root@localhost httpd]# ls
conf conf.d conf.modules.d logs modules run ssl state
//使用OpenSSL创建密钥文件
[root@localhost httpd]# cd ssl
[root@localhost ssl]# (umask 077;openssl genrsa -out httpd.key 2048)
Generating RSA private key, 2048 bit long modulus (2 primes)
............................................................+++++
..............................................................+++++
e is 65537 (0x010001)
[root@localhost ssl]# ls
httpd.key
2、使用OpenSSL给客户端生成证书签署(证书签署来自刚刚创建的CA,由CA颁发数字证书)
[root@localhost ssl]# pwd
/etc/httpd/ssl
[root@localhost ssl]# openssl req -new -key httpd.key -days 365 -out httpd.csr
Ignoring -days; not generating a certificate
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN //跟创建CA自签证书步骤一样
State or Province Name (full name) []:HB
Locality Name (eg, city) [Default City]:WH
Organization Name (eg, company) [Default Company Ltd]:www.qiangge.com
Organizational Unit Name (eg, section) []:www.qiangge.com
Common Name (eg, your name or your server's hostname) []:www.qiangge.com
Email Address []:123@123.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []: //(询问是否创建给证书创建密码);直接回车,不需要加密码
An optional company name []: //直接回车即可
3、客户端把证书签署请求文件发送给CA
发送语法
scp httpd.csr root@CA端IP:/root
由于我自己创建的CA,都是在我本地,所以不需要发送证书请求文件
4、CA签署提交上来的证书请求文件
[root@localhost ssl]# ls
httpd.csr httpd.key
[root@localhost ssl]# openssl ca -in ./httpd.csr -out httpd.crt -days 365
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Aug 25 10:33:13 2020 GMT
Not After : Aug 25 10:33:13 2021 GMT
Subject:
countryName = CN
stateOrProvinceName = HB
organizationName = www.qiangge.com
organizationalUnitName = www.qiangge.com
commonName = www.qiangge.com
emailAddress = 123@123.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
56:87:C5:89:88:3D:23:15:50:4E:12:C0:6D:57:97:7B:A7:47:19:9E
X509v3 Authority Key Identifier:
keyid:76:58:7D:1B:66:AD:A2:99:AD:D5:89:14:BF:79:DB:B1:9E:3A:79:4F
Certificate is to be certified until Aug 25 10:33:13 2021 GMT (365 days)
Sign the certificate? [y/n]:y //确认是否需要签名
1 out of 1 certificate requests certified, commit? [y/n]y //确认证书的请求是否提交
Write out database with 1 new entries
Data Base Updated
5、CA把签署好的数字证书(http.crt)颁发给客户端
颁发语法:
scp httpd.crt root@客户端IP:/etc/httpd/ssl/
由于我是在本地自己给自己颁发证书所以不需要做该步骤
