Prioritization of vulnerabilities
LEVERAGE INFORMATION
- Leveraging information to prepare for exploitation
- Map vulnerabilities to potential exploits
- Look up vulnerabilities found for possible exploits
- Nmap - vulners and vulscan scripts
- Metasploit(search vulnerability)
- Prioritize activities in preparation for penetration test
- Will standard exploits work?
- Will exploits need to be 'tweaked'?
- Additional steps to prepare test?
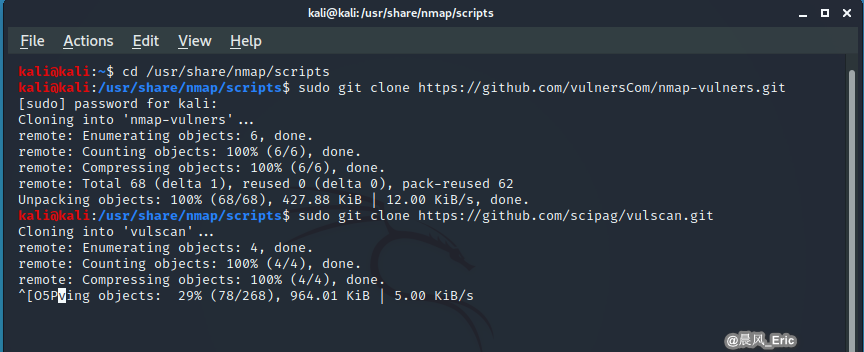
Change the directory over to the location of Namp scripts.
cd /usr/share/nmap/scripts
Clone a git repository.
git clone https://github.com/vulnersCom/nmap-vulners.git
git clone https://github.com/scipag/vulscan.git
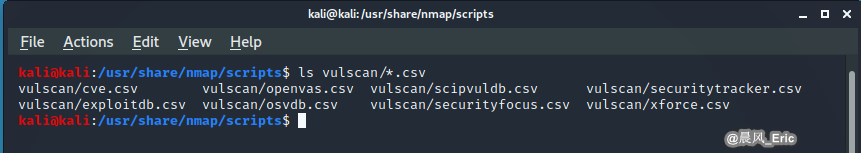
ls vulscan/*.csv
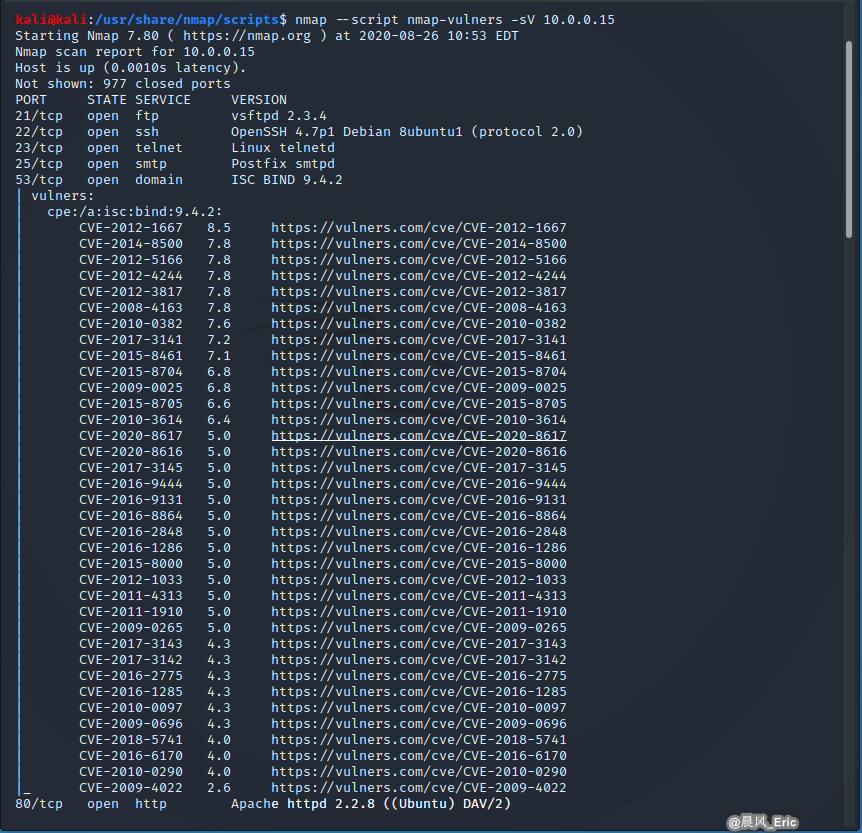
Demo to use Namp script.
nmap --script nmap-vulners -sV 10.0.0.15
nmap --script vulscan -sV 10.0.0.15
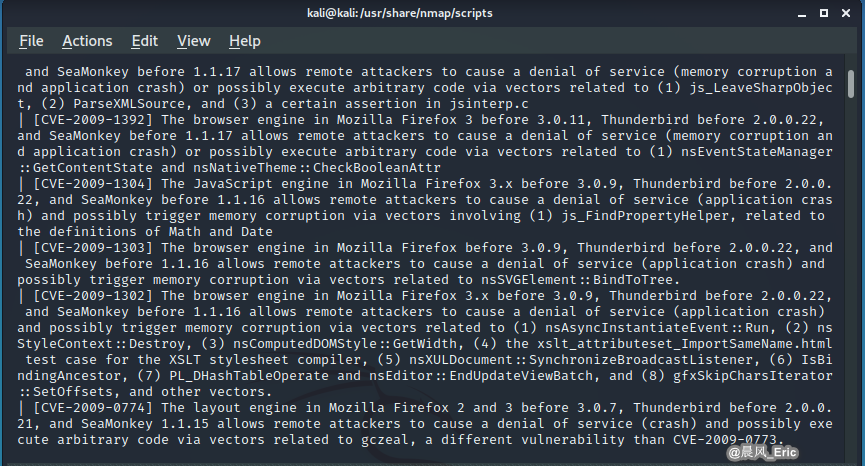
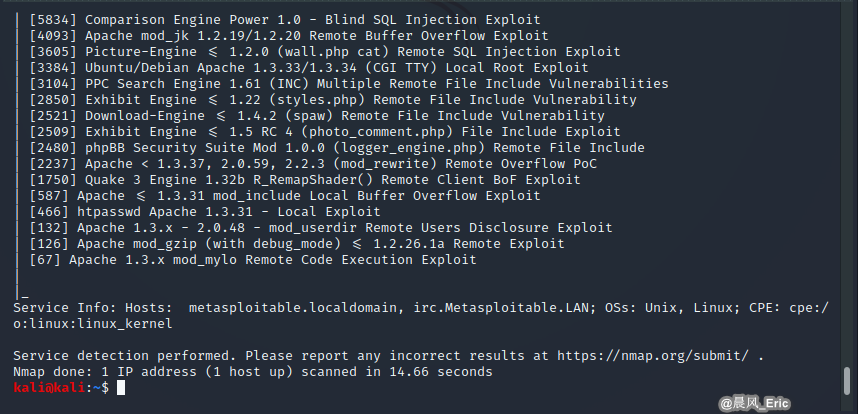
nmap --script vulscan --script-args vulscandb=exploitdb.csv -sV 10.0.0.15
QUICK REVIEW
- A key step in pen test planning is to map vulnerabilities to potential exploits
- Use nmap scripts (vulners and vulscan) to find exploits for detected vulnerabilities
- Use metasploit to search for exploits