Post-exploitation Techniques
POST-EXPLOITATION TECHNIQUES
- What to do once you're in
- Make it easier next time
- Lateral movement
- RPC/DCOM (Remote Procedure Call / Distributed Component Object Model)
- PsExec - Utility that supports executing processes on other systems(i.e. telnet)
- WMI (Windows Management Instrumentation) - Managing devices and applications from remote computers
- Scheduled tasks
- RPC/DCOM (Remote Procedure Call / Distributed Component Object Model)
LATERAL MOVEMENT
- PS remoting/WinRM
- Powershell remoting / Windows Remote Management
- SMB (Server Message Block)
- Protocol for exposing shares to remote computers(Linux, etc. too)
- RDP (Remote Desktop Protocol)
- Ability to access a desktop from a remote computer
- Apple Remote Desktop
- Apple's RDP
- VNC (Virtual Network Computing)
- X-server forwarding
- X-windows access to Linux desktop
- Telnet
- Unsecure remote access(everything in cleartext)
- SSH (Secure Shell)
- More secure remote access to shell
- RSH/Rlogin (Remote Shell / Remote login)
- Legacy secure remote access
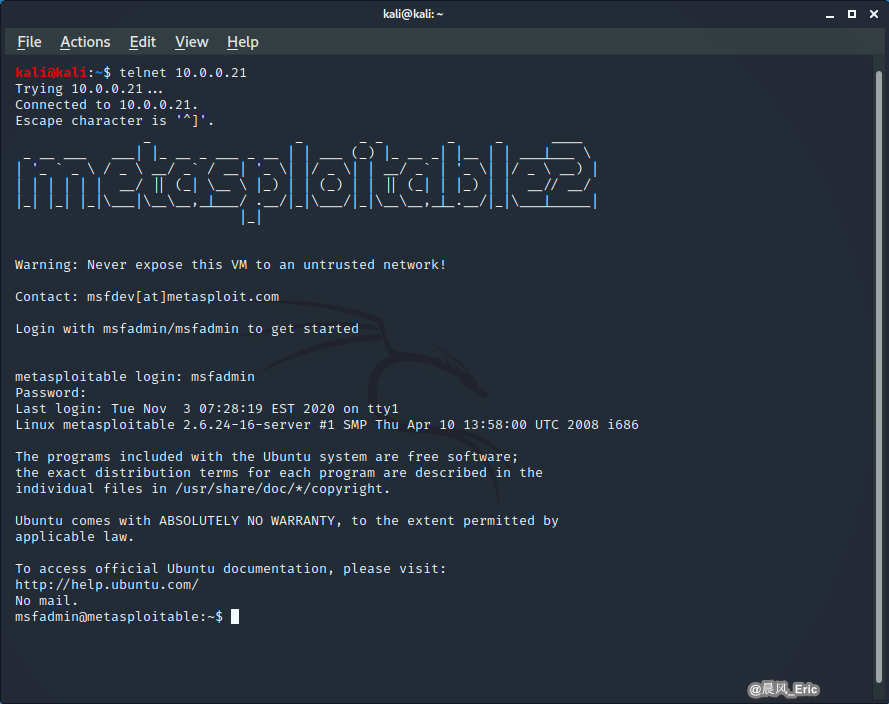
CASE 1 - Telnet login
Keep in mind, Telnet is totally in the clear, so if there was somebody else out there sniffing through this traffic, they would be able to see what I'm about to type.
telnet 10.0.0.21
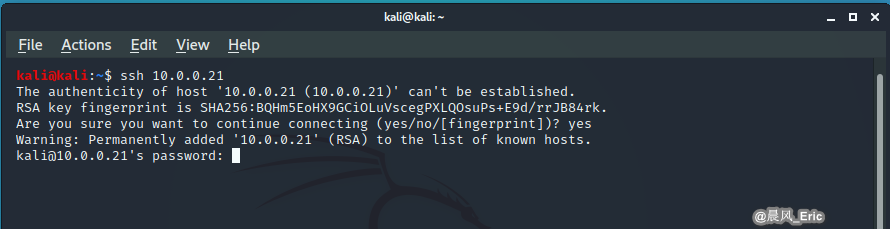
CASE 2 - SSH Login
Logged in in a more secure manner, and all of the things that I type going back and forth are encrypted.
ssh 10.0.0.21
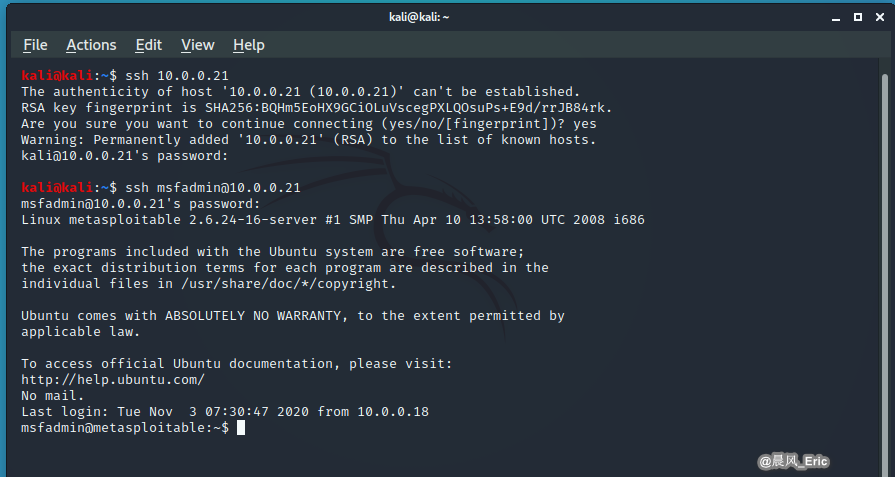
ssh msfadmin@10.0.0.21
QUICK REVIEW
- Don't reinvent the wheel each time - once you're in, make it easier next time.
- Enable remote access if possible
- Use remote access to move laterally within a network
- Telnet can be helpful when connecting to different devices