视频地址:
https://www.bilibili.com/video/BV12D4y1U7D8?p=44
有用到Redis存储JWT,头疼每次找Windows版的
https://github.com/MicrosoftArchive/redis/releases
20.09.29获取的下载地址:
https://github.com/microsoftarchive/redis/releases/download/win-3.2.100/Redis-x64-3.2.100.msi
1、移除之前工程中的Redis配置:
POM依赖移除
<!--<dependency>--> <!-- <groupId>org.springframework.boot</groupId>--> <!-- <artifactId>spring-boot-starter-data-redis</artifactId>--> <!--</dependency>--> <!--<dependency>--> <!-- <groupId>org.apache.commons</groupId>--> <!-- <artifactId>commons-pool2</artifactId>--> <!--</dependency>-->
YML配置移除:
spring:
redis:
host: localhost
Redis配置类移除:
package cn.zeal4j.configuration; import org.springframework.beans.factory.annotation.Autowired; import org.springframework.context.annotation.Bean; import org.springframework.context.annotation.Configuration; import org.springframework.data.redis.connection.RedisConnectionFactory; import org.springframework.security.oauth2.provider.token.TokenStore; import org.springframework.security.oauth2.provider.token.store.redis.RedisTokenStore; /** * @author Administrator * @file Spring-Security + Oauth2 * @create 2020 09 29 17:16 */ @Configuration public class RedisConfiguration { @Autowired private RedisConnectionFactory redisConnectionFactory; @Bean public TokenStore getRedisTokenStore() { return new RedisTokenStore(redisConnectionFactory); } }
数据源注入和Redis存储移除:
package cn.zeal4j.configuration; import org.springframework.beans.factory.annotation.Autowired; import org.springframework.beans.factory.annotation.Qualifier; import org.springframework.context.annotation.Configuration; import org.springframework.security.authentication.AuthenticationManager; import org.springframework.security.core.userdetails.UserDetails; import org.springframework.security.core.userdetails.UserDetailsService; import org.springframework.security.crypto.password.PasswordEncoder; import org.springframework.security.oauth2.config.annotation.configurers.ClientDetailsServiceConfigurer; import org.springframework.security.oauth2.config.annotation.web.configuration.AuthorizationServerConfigurerAdapter; import org.springframework.security.oauth2.config.annotation.web.configuration.EnableAuthorizationServer; import org.springframework.security.oauth2.config.annotation.web.configurers.AuthorizationServerEndpointsConfigurer; import org.springframework.security.oauth2.provider.token.TokenStore; /** * @author Administrator * @file Spring-Security + Oauth2 * @create 2020 09 29 11:48 * @description 授权服务器配置 */ @Configuration @EnableAuthorizationServer public class AuthorizationServerConfiguration extends AuthorizationServerConfigurerAdapter { @Autowired private PasswordEncoder passwordEncoder; @Autowired private AuthenticationManager authenticationManager; @Qualifier("customUserDetailsServiceImpl") @Autowired private UserDetailsService userDetailsService; // @Qualifier("getRedisTokenStore") // @Autowired // private TokenStore tokenStore; /** * 使用密码模式需要的配置方法 * @param endpoints * @throws Exception */ @Override public void configure(AuthorizationServerEndpointsConfigurer endpoints) throws Exception { endpoints. authenticationManager(authenticationManager). userDetailsService(userDetailsService); // tokenStore(tokenStore); } @Override public void configure(ClientDetailsServiceConfigurer clients) throws Exception { clients. inMemory(). withClient("admin"). secret(passwordEncoder.encode("112233")). // accessTokenValiditySeconds(3600). // 令牌有效时间 一小时 redirectUris("http://www.baidu.com"). // 授权成功的跳转 scopes("all"). // 所有范围 // authorizedGrantTypes("authorization_code"); // 授权类型:授权码模式 authorizedGrantTypes("password"); // 授权类型:密码模式 } }
2、编写JWT配置:
package cn.zeal4j.configuration;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.oauth2.provider.token.TokenStore;
import org.springframework.security.oauth2.provider.token.store.JwtAccessTokenConverter;
import org.springframework.security.oauth2.provider.token.store.JwtTokenStore;
/**
* @author Administrator
* @file IntelliJ IDEA Spring-Security + Oauth2
* @create 2020 09 29 22:36
*/
@Configuration
public class JwtTokenStoreConfiguration {
@Bean
public TokenStore getTokenStore(JwtAccessTokenConverter getJwtAccessTokenConverter) {
return new JwtTokenStore(getJwtAccessTokenConverter);
}
@Bean
public JwtAccessTokenConverter getJwtAccessTokenConverter() {
JwtAccessTokenConverter jwtAccessTokenConverter = new JwtAccessTokenConverter();
jwtAccessTokenConverter.setSigningKey("这不是盐【滑稽】 It's not salt [funny]");
return jwtAccessTokenConverter;
}
}
然后更改授权配置类:
package cn.zeal4j.configuration; import org.springframework.beans.factory.annotation.Autowired; import org.springframework.beans.factory.annotation.Qualifier; import org.springframework.context.annotation.Configuration; import org.springframework.security.authentication.AuthenticationManager; import org.springframework.security.core.userdetails.UserDetails; import org.springframework.security.core.userdetails.UserDetailsService; import org.springframework.security.crypto.password.PasswordEncoder; import org.springframework.security.oauth2.config.annotation.configurers.ClientDetailsServiceConfigurer; import org.springframework.security.oauth2.config.annotation.web.configuration.AuthorizationServerConfigurerAdapter; import org.springframework.security.oauth2.config.annotation.web.configuration.EnableAuthorizationServer; import org.springframework.security.oauth2.config.annotation.web.configurers.AuthorizationServerEndpointsConfigurer; import org.springframework.security.oauth2.provider.token.TokenStore; import org.springframework.security.oauth2.provider.token.store.JwtAccessTokenConverter; /** * @author Administrator * @file Spring-Security + Oauth2 * @create 2020 09 29 11:48 * @description 授权服务器配置 */ @Configuration @EnableAuthorizationServer public class AuthorizationServerConfiguration extends AuthorizationServerConfigurerAdapter { @Autowired private PasswordEncoder passwordEncoder; @Autowired private AuthenticationManager authenticationManager; @Qualifier("customUserDetailsServiceImpl") @Autowired private UserDetailsService userDetailsService; @Qualifier("getTokenStore") @Autowired private TokenStore tokenStore; @Qualifier("getJwtAccessTokenConverter") @Autowired private JwtAccessTokenConverter jwtAccessTokenConverter; // @Qualifier("getRedisTokenStore") // @Autowired // private TokenStore tokenStore; /** * 使用密码模式需要的配置方法 * @param endpoints * @throws Exception */ @Override public void configure(AuthorizationServerEndpointsConfigurer endpoints) throws Exception { endpoints. authenticationManager(authenticationManager). userDetailsService(userDetailsService).accessTokenConverter(jwtAccessTokenConverter); // tokenStore(tokenStore); } @Override public void configure(ClientDetailsServiceConfigurer clients) throws Exception { clients. inMemory(). withClient("admin"). secret(passwordEncoder.encode("112233")). // accessTokenValiditySeconds(3600). // 令牌有效时间 一小时 redirectUris("http://www.baidu.com"). // 授权成功的跳转 scopes("all"). // 所有范围 // authorizedGrantTypes("authorization_code"); // 授权类型:授权码模式 authorizedGrantTypes("password"); // 授权类型:密码模式 } }
启动工程,Postman测试:
之前的接口的设置都不需要改变,还是之前的密码模式授权,这里就得到了JWT令牌
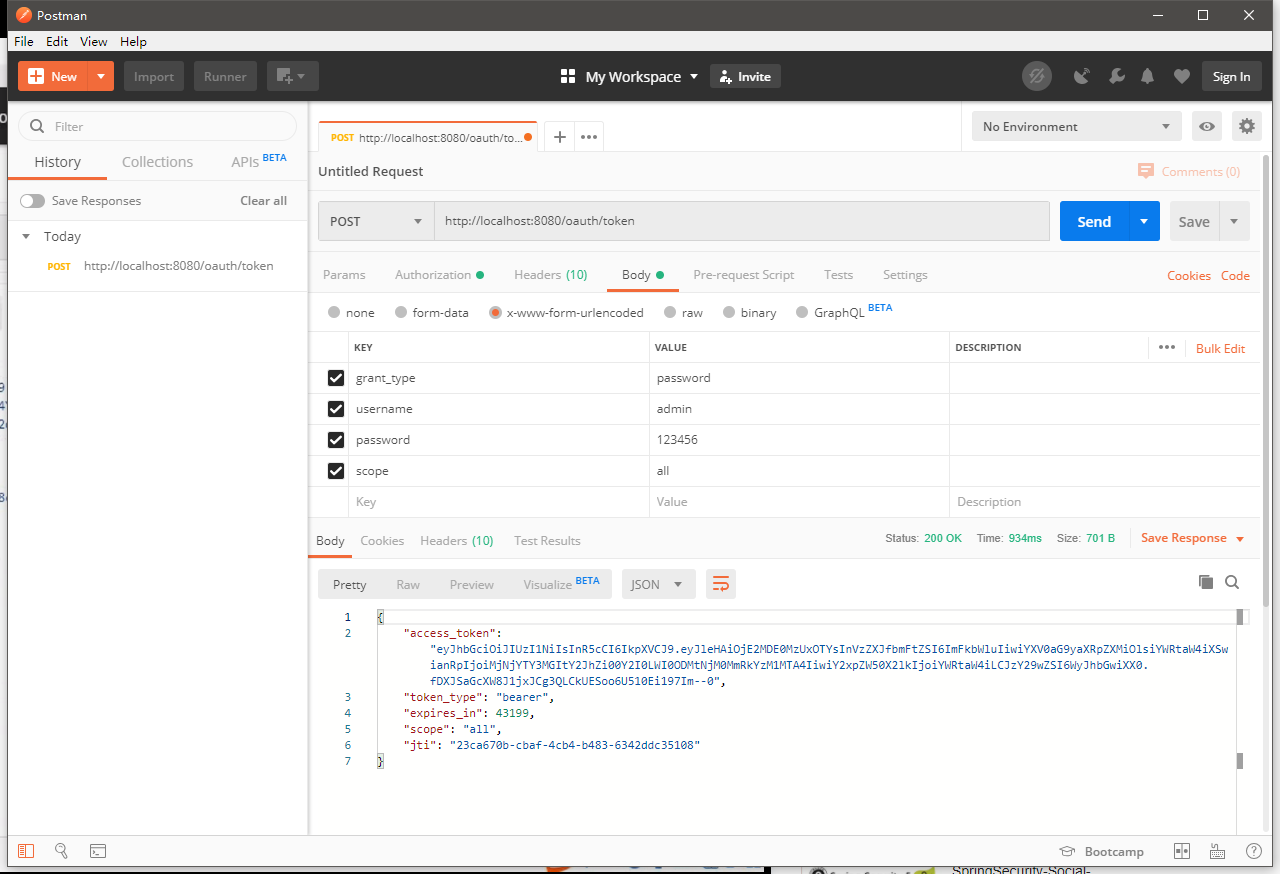
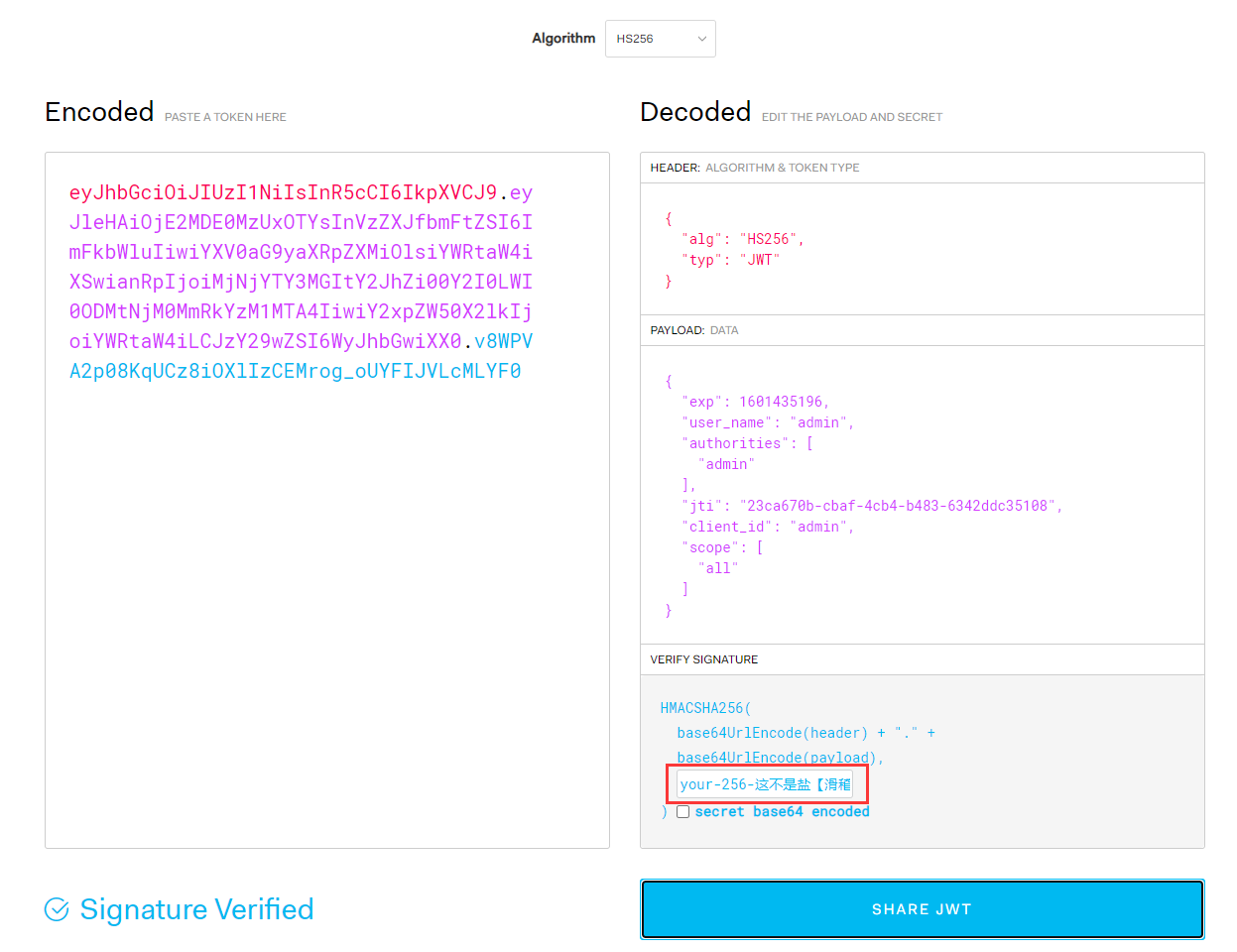
把令牌复制到JWT官网的解析工具进行解析查看:
https://jwt.io/#debugger-io
3、JWT自定义申明内容
package cn.zeal4j.configuration;
import org.springframework.security.oauth2.common.DefaultOAuth2AccessToken;
import org.springframework.security.oauth2.common.OAuth2AccessToken;
import org.springframework.security.oauth2.provider.OAuth2Authentication;
import org.springframework.security.oauth2.provider.token.TokenEnhancer;
import java.util.HashMap;
import java.util.Map;
/**
* @author Administrator
* @file IntelliJ IDEA Spring-Security + Oauth2
* @create 2020 09 29 23:18
*/
public class CustomJwtTokenEnhancer implements TokenEnhancer {
@Override
public OAuth2AccessToken enhance(OAuth2AccessToken oAuth2AccessToken, OAuth2Authentication oAuth2Authentication) {
Map<String, Object> map = new HashMap<String, Object>();
map.put("jwt-key-aaa", "jwt-value-AAA");
map.put("jwt-key-bbb", "jwt-value-BBB");
map.put("jwt-key-ccc", "jwt-value-CCC");
DefaultOAuth2AccessToken defaultOAuth2AccessToken = (DefaultOAuth2AccessToken)oAuth2AccessToken;
defaultOAuth2AccessToken.setAdditionalInformation(map);
return defaultOAuth2AccessToken;
}
}
注入增强实现类:
package cn.zeal4j.configuration; import org.springframework.context.annotation.Bean; import org.springframework.context.annotation.Configuration; import org.springframework.security.oauth2.provider.token.TokenEnhancer; import org.springframework.security.oauth2.provider.token.TokenStore; import org.springframework.security.oauth2.provider.token.store.JwtAccessTokenConverter; import org.springframework.security.oauth2.provider.token.store.JwtTokenStore; /** * @author Administrator * @file IntelliJ IDEA Spring-Security + Oauth2 * @create 2020 09 29 22:36 */ @Configuration public class JwtTokenStoreConfiguration { @Bean public TokenStore getTokenStore(JwtAccessTokenConverter getJwtAccessTokenConverter) { return new JwtTokenStore(getJwtAccessTokenConverter); } @Bean public JwtAccessTokenConverter getJwtAccessTokenConverter() { JwtAccessTokenConverter jwtAccessTokenConverter = new JwtAccessTokenConverter(); jwtAccessTokenConverter.setSigningKey("这不是盐【滑稽】 It's not salt [funny]"); return jwtAccessTokenConverter; } @Bean public TokenEnhancer getJwtTokenEnhancer() { return new CustomJwtTokenEnhancer(); } }
注入增强器和配置增强方法:
package cn.zeal4j.configuration; import org.springframework.beans.factory.annotation.Autowired; import org.springframework.beans.factory.annotation.Qualifier; import org.springframework.context.annotation.Configuration; import org.springframework.security.authentication.AuthenticationManager; import org.springframework.security.core.userdetails.UserDetails; import org.springframework.security.core.userdetails.UserDetailsService; import org.springframework.security.crypto.password.PasswordEncoder; import org.springframework.security.oauth2.config.annotation.configurers.ClientDetailsServiceConfigurer; import org.springframework.security.oauth2.config.annotation.web.configuration.AuthorizationServerConfigurerAdapter; import org.springframework.security.oauth2.config.annotation.web.configuration.EnableAuthorizationServer; import org.springframework.security.oauth2.config.annotation.web.configurers.AuthorizationServerEndpointsConfigurer; import org.springframework.security.oauth2.provider.token.TokenEnhancer; import org.springframework.security.oauth2.provider.token.TokenEnhancerChain; import org.springframework.security.oauth2.provider.token.TokenStore; import org.springframework.security.oauth2.provider.token.store.JwtAccessTokenConverter; import java.util.ArrayList; import java.util.List; /** * @author Administrator * @file Spring-Security + Oauth2 * @create 2020 09 29 11:48 * @description 授权服务器配置 */ @Configuration @EnableAuthorizationServer public class AuthorizationServerConfiguration extends AuthorizationServerConfigurerAdapter { @Autowired private PasswordEncoder passwordEncoder; @Autowired private AuthenticationManager authenticationManager; @Qualifier("customUserDetailsServiceImpl") @Autowired private UserDetailsService userDetailsService; @Qualifier("getTokenStore") @Autowired private TokenStore tokenStore; @Qualifier("getJwtAccessTokenConverter") @Autowired private JwtAccessTokenConverter jwtAccessTokenConverter; @Qualifier("getJwtTokenEnhancer") @Autowired private TokenEnhancer tokenEnhancer; // @Qualifier("getRedisTokenStore") // @Autowired // private TokenStore tokenStore; /** * 使用密码模式需要的配置方法 * @param endpoints * @throws Exception */ @Override public void configure(AuthorizationServerEndpointsConfigurer endpoints) throws Exception { // - - - - - 配置JWT自定义申明增强 Starter - - - - - TokenEnhancerChain tokenEnhancerChain = new TokenEnhancerChain(); List<TokenEnhancer> tokenEnhancerList = new ArrayList<>(); tokenEnhancerList.add(tokenEnhancer); tokenEnhancerList.add(jwtAccessTokenConverter); tokenEnhancerChain.setTokenEnhancers(tokenEnhancerList); // - - - - - 配置JWT自定义申明增强 End - - - - - endpoints. authenticationManager(authenticationManager). userDetailsService(userDetailsService). accessTokenConverter(jwtAccessTokenConverter). tokenEnhancer(tokenEnhancerChain); // tokenStore(tokenStore); } @Override public void configure(ClientDetailsServiceConfigurer clients) throws Exception { clients. inMemory(). withClient("admin"). secret(passwordEncoder.encode("112233")). // accessTokenValiditySeconds(3600). // 令牌有效时间 一小时 redirectUris("http://www.baidu.com"). // 授权成功的跳转 scopes("all"). // 所有范围 // authorizedGrantTypes("authorization_code"); // 授权类型:授权码模式 authorizedGrantTypes("password"); // 授权类型:密码模式 } }
重启项目,进行Postman测试:
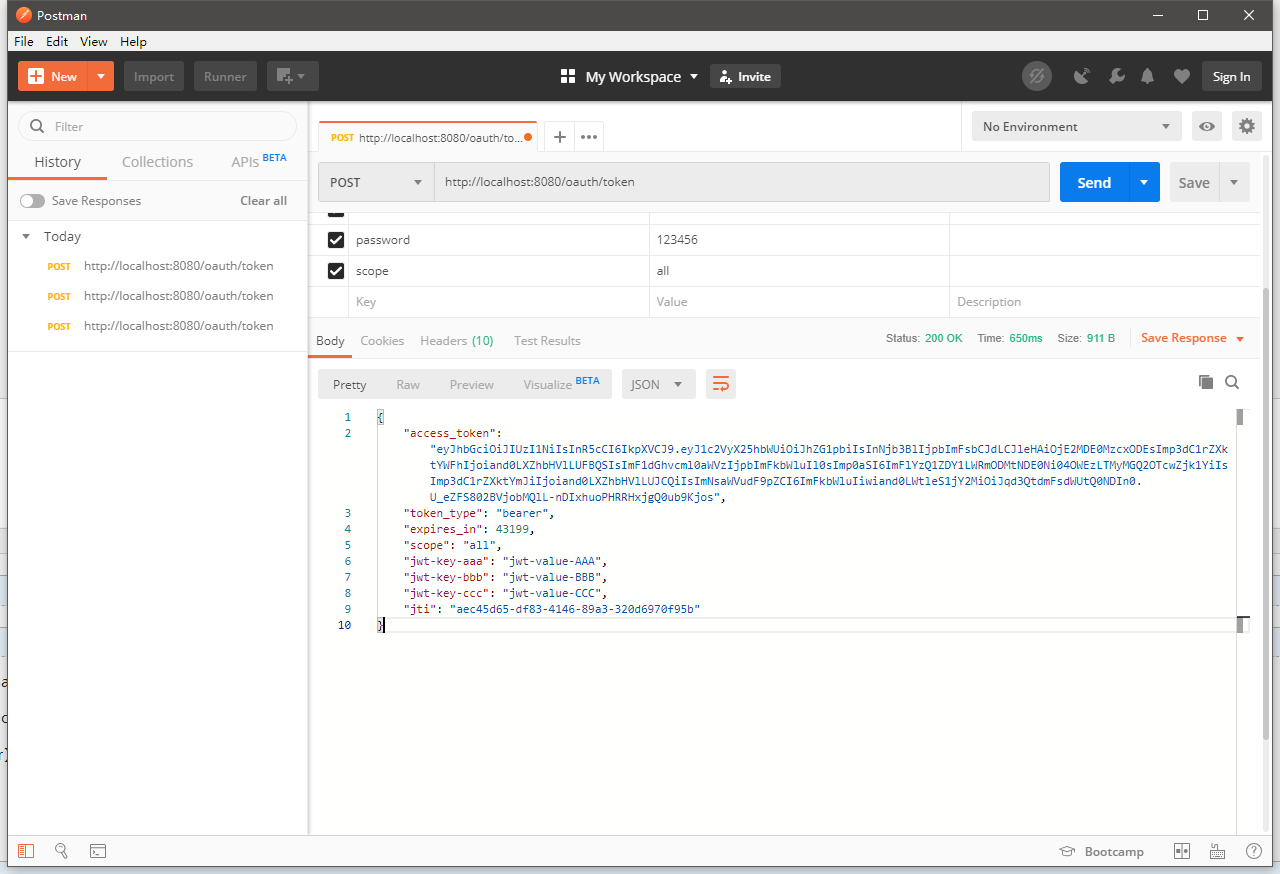
在增强器中设置的申明都在这里传输了:
{ "access_token": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX25hbWUiOiJhZG1pbiIsInNjb3BlIjpbImFsbCJdLCJleHAiOjE2MDE0MzcxODEsImp3dC1rZXktYWFhIjoiand0LXZhbHVlLUFBQSIsImF1dGhvcml0aWVzIjpbImFkbWluIl0sImp0aSI6ImFlYzQ1ZDY1LWRmODMtNDE0Ni04OWEzLTMyMGQ2OTcwZjk1YiIsImp3dC1rZXktYmJiIjoiand0LXZhbHVlLUJCQiIsImNsaWVudF9pZCI6ImFkbWluIiwiand0LWtleS1jY2MiOiJqd3QtdmFsdWUtQ0NDIn0.U_eZFS802BVjobMQlL-nDIxhuoPHRRHxjgQ0ub9Kjos", "token_type": "bearer", "expires_in": 43199, "scope": "all", "jwt-key-aaa": "jwt-value-AAA", "jwt-key-bbb": "jwt-value-BBB", "jwt-key-ccc": "jwt-value-CCC", "jti": "aec45d65-df83-4146-89a3-320d6970f95b" }
在令牌解析中同样也存入了

4、JWT解析:
加入JWT解析组件:
<dependency> <groupId>io.jsonwebtoken</groupId> <artifactId>jjwt</artifactId> <version>0.9.1</version> </dependency>
新加一个资源获取的接口:
演示中是对原接口更改,我这里就保留不动了
package cn.zeal4j.controller; import io.jsonwebtoken.Claims; import io.jsonwebtoken.Jws; import io.jsonwebtoken.JwtParser; import io.jsonwebtoken.Jwts; import org.springframework.security.core.Authentication; import org.springframework.stereotype.Controller; import org.springframework.web.bind.annotation.RequestMapping; import org.springframework.web.bind.annotation.ResponseBody; import javax.servlet.http.HttpServletRequest; import java.nio.charset.StandardCharsets; /** * @author Administrator * @file Spring-Security + Oauth2 * @create 2020 09 29 12:01 */ @Controller @RequestMapping("user") public class UserController { /** * 获取当前用户 * @param authentication * @return user/getCurrentUser */ @RequestMapping("/getCurrentUser") @ResponseBody public Object getCurrentUser(Authentication authentication) { return authentication.getPrincipal(); } /** * 获取当前用户 * @param authentication * @return user/getCurrentUser */ @RequestMapping("/getJwtToken") @ResponseBody public Object getJwtToken(HttpServletRequest httpServletRequest, Authentication authentication) { String authorization = httpServletRequest.getHeader("Authorization"); String token = authorization.substring(authorization.indexOf("bearer") + 7); JwtParser jwtParser = Jwts.parser(); Jws<Claims> claimsJws = jwtParser. setSigningKey("这不是盐【滑稽】 It's not salt [funny]".getBytes(StandardCharsets.UTF_8)). parseClaimsJws(token); Claims claimsJwsBody = claimsJws.getBody(); return claimsJwsBody; } }
启动项目:还是一样,第一步Postman获取JWT令牌
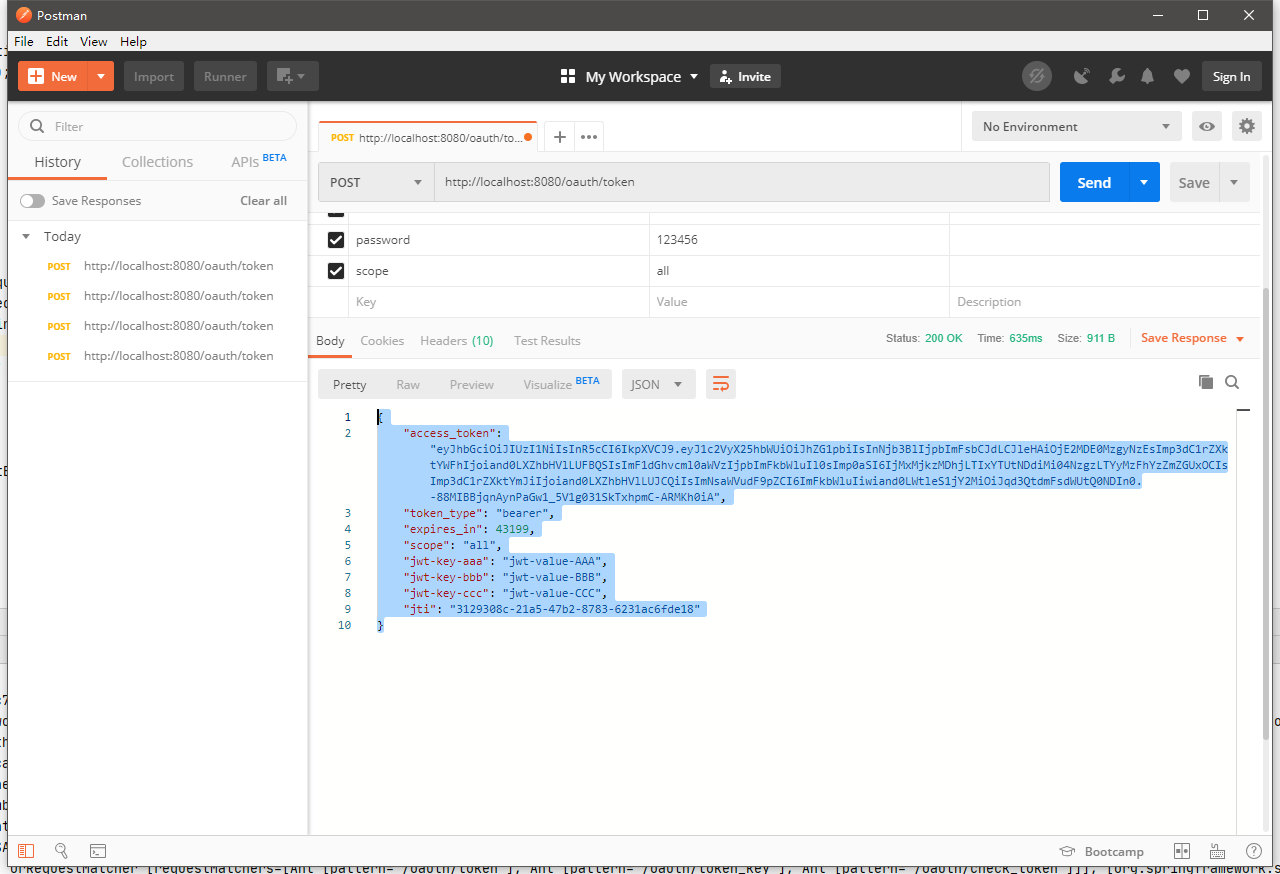
{ "access_token": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX25hbWUiOiJhZG1pbiIsInNjb3BlIjpbImFsbCJdLCJleHAiOjE2MDE0MzgyNzEsImp3dC1rZXktYWFhIjoiand0LXZhbHVlLUFBQSIsImF1dGhvcml0aWVzIjpbImFkbWluIl0sImp0aSI6IjMxMjkzMDhjLTIxYTUtNDdiMi04NzgzLTYyMzFhYzZmZGUxOCIsImp3dC1rZXktYmJiIjoiand0LXZhbHVlLUJCQiIsImNsaWVudF9pZCI6ImFkbWluIiwiand0LWtleS1jY2MiOiJqd3QtdmFsdWUtQ0NDIn0.-88MIBBjqnAynPaGw1_5V1g031SkTxhpmC-ARMKh0iA", "token_type": "bearer", "expires_in": 43199, "scope": "all", "jwt-key-aaa": "jwt-value-AAA", "jwt-key-bbb": "jwt-value-BBB", "jwt-key-ccc": "jwt-value-CCC", "jti": "3129308c-21a5-47b2-8783-6231ac6fde18" }
然后Postman访问获取接口:
http://localhost:8080/user/getJwtToken
传输的响应头信息:
KEY -> Authorization
VALUE -> bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX25hbWUiOiJhZG1pbiIsInNjb3BlIjpbImFsbCJdLCJleHAiOjE2MDE0MzgyNzEsImp3dC1rZXktYWFhIjoiand0LXZhbHVlLUFBQSIsImF1dGhvcml0aWVzIjpbImFkbWluIl0sImp0aSI6IjMxMjkzMDhjLTIxYTUtNDdiMi04NzgzLTYyMzFhYzZmZGUxOCIsImp3dC1rZXktYmJiIjoiand0LXZhbHVlLUJCQiIsImNsaWVudF9pZCI6ImFkbWluIiwiand0LWtleS1jY2MiOiJqd3QtdmFsdWUtQ0NDIn0.-88MIBBjqnAynPaGw1_5V1g031SkTxhpmC-ARMKh0iA
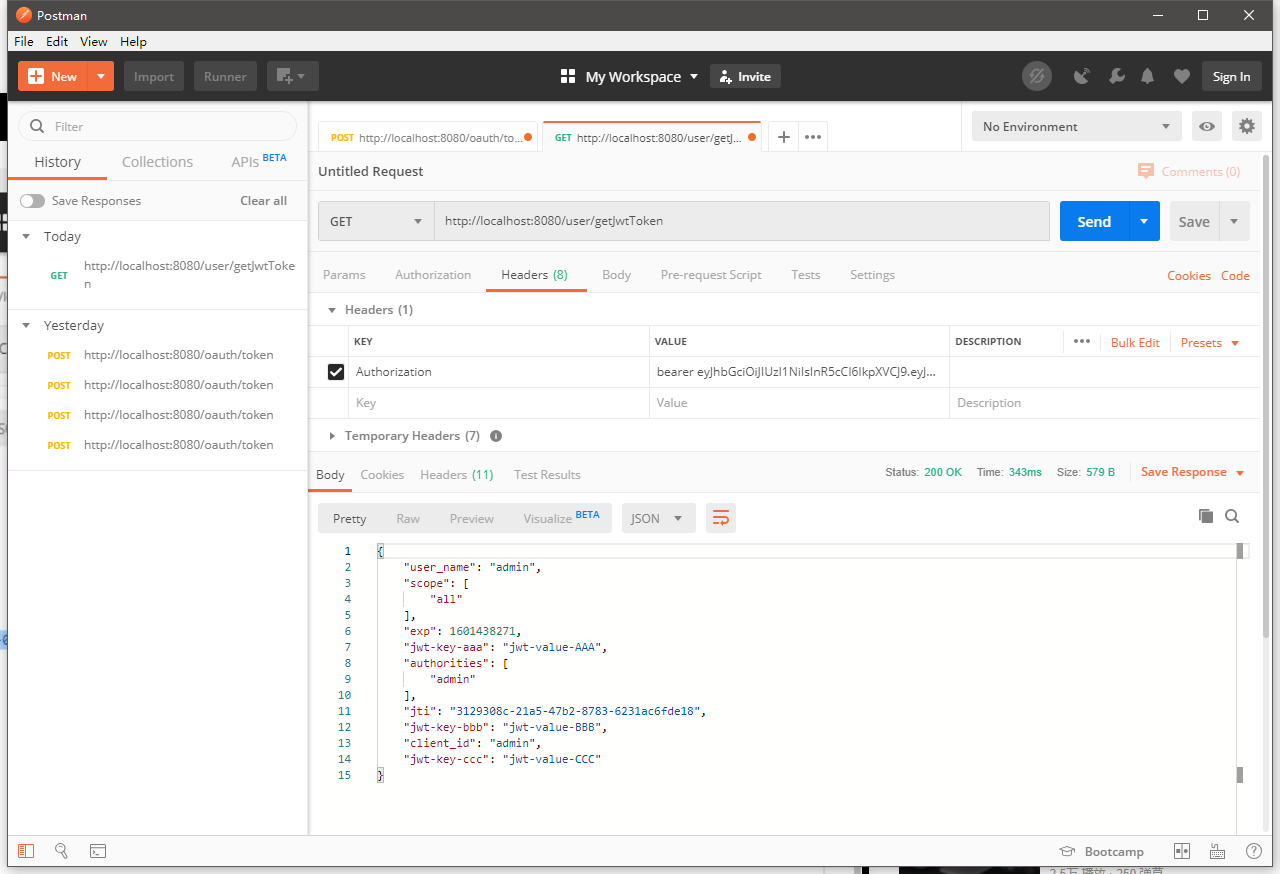
解析出来的JSON数据
{ "user_name": "admin", "scope": [ "all" ], "exp": 1601438271, "jwt-key-aaa": "jwt-value-AAA", "authorities": [ "admin" ], "jti": "3129308c-21a5-47b2-8783-6231ac6fde18", "jwt-key-bbb": "jwt-value-BBB", "client_id": "admin", "jwt-key-ccc": "jwt-value-CCC" }
5、刷新令牌
package cn.zeal4j.configuration; import org.springframework.beans.factory.annotation.Autowired; import org.springframework.beans.factory.annotation.Qualifier; import org.springframework.context.annotation.Configuration; import org.springframework.security.authentication.AuthenticationManager; import org.springframework.security.core.userdetails.UserDetails; import org.springframework.security.core.userdetails.UserDetailsService; import org.springframework.security.crypto.password.PasswordEncoder; import org.springframework.security.oauth2.config.annotation.configurers.ClientDetailsServiceConfigurer; import org.springframework.security.oauth2.config.annotation.web.configuration.AuthorizationServerConfigurerAdapter; import org.springframework.security.oauth2.config.annotation.web.configuration.EnableAuthorizationServer; import org.springframework.security.oauth2.config.annotation.web.configurers.AuthorizationServerEndpointsConfigurer; import org.springframework.security.oauth2.provider.token.TokenEnhancer; import org.springframework.security.oauth2.provider.token.TokenEnhancerChain; import org.springframework.security.oauth2.provider.token.TokenStore; import org.springframework.security.oauth2.provider.token.store.JwtAccessTokenConverter; import java.util.ArrayList; import java.util.List; /** * @author Administrator * @file Spring-Security + Oauth2 * @create 2020 09 29 11:48 * @description 授权服务器配置 */ @Configuration @EnableAuthorizationServer public class AuthorizationServerConfiguration extends AuthorizationServerConfigurerAdapter { @Autowired private PasswordEncoder passwordEncoder; @Autowired private AuthenticationManager authenticationManager; @Qualifier("customUserDetailsServiceImpl") @Autowired private UserDetailsService userDetailsService; @Qualifier("getTokenStore") @Autowired private TokenStore tokenStore; @Qualifier("getJwtAccessTokenConverter") @Autowired private JwtAccessTokenConverter jwtAccessTokenConverter; @Qualifier("getJwtTokenEnhancer") @Autowired private TokenEnhancer tokenEnhancer; // @Qualifier("getRedisTokenStore") // @Autowired // private TokenStore tokenStore; /** * 使用密码模式需要的配置方法 * @param endpoints * @throws Exception */ @Override public void configure(AuthorizationServerEndpointsConfigurer endpoints) throws Exception { // - - - - - 配置JWT自定义申明增强 Starter - - - - - TokenEnhancerChain tokenEnhancerChain = new TokenEnhancerChain(); List<TokenEnhancer> tokenEnhancerList = new ArrayList<>(); tokenEnhancerList.add(tokenEnhancer); tokenEnhancerList.add(jwtAccessTokenConverter); tokenEnhancerChain.setTokenEnhancers(tokenEnhancerList); // - - - - - 配置JWT自定义申明增强 End - - - - - endpoints. authenticationManager(authenticationManager). userDetailsService(userDetailsService). accessTokenConverter(jwtAccessTokenConverter). tokenEnhancer(tokenEnhancerChain); // tokenStore(tokenStore); } @Override public void configure(ClientDetailsServiceConfigurer clients) throws Exception { clients. inMemory(). withClient("admin"). secret(passwordEncoder.encode("112233")). // accessTokenValiditySeconds(3600). // 令牌有效时间 一小时 redirectUris("http://www.baidu.com"). // 授权成功的跳转 scopes("all"). // 所有范围 // authorizedGrantTypes("authorization_code"); // 授权类型:授权码模式 authorizedGrantTypes("password", "refresh_token", "authorization_code"); // 授权类型:密码模式 追加令牌刷新,和兼容授权码模式 } }
重启项目:继续请求JWT令牌
这个时候会发现多了一个刷新的令牌:
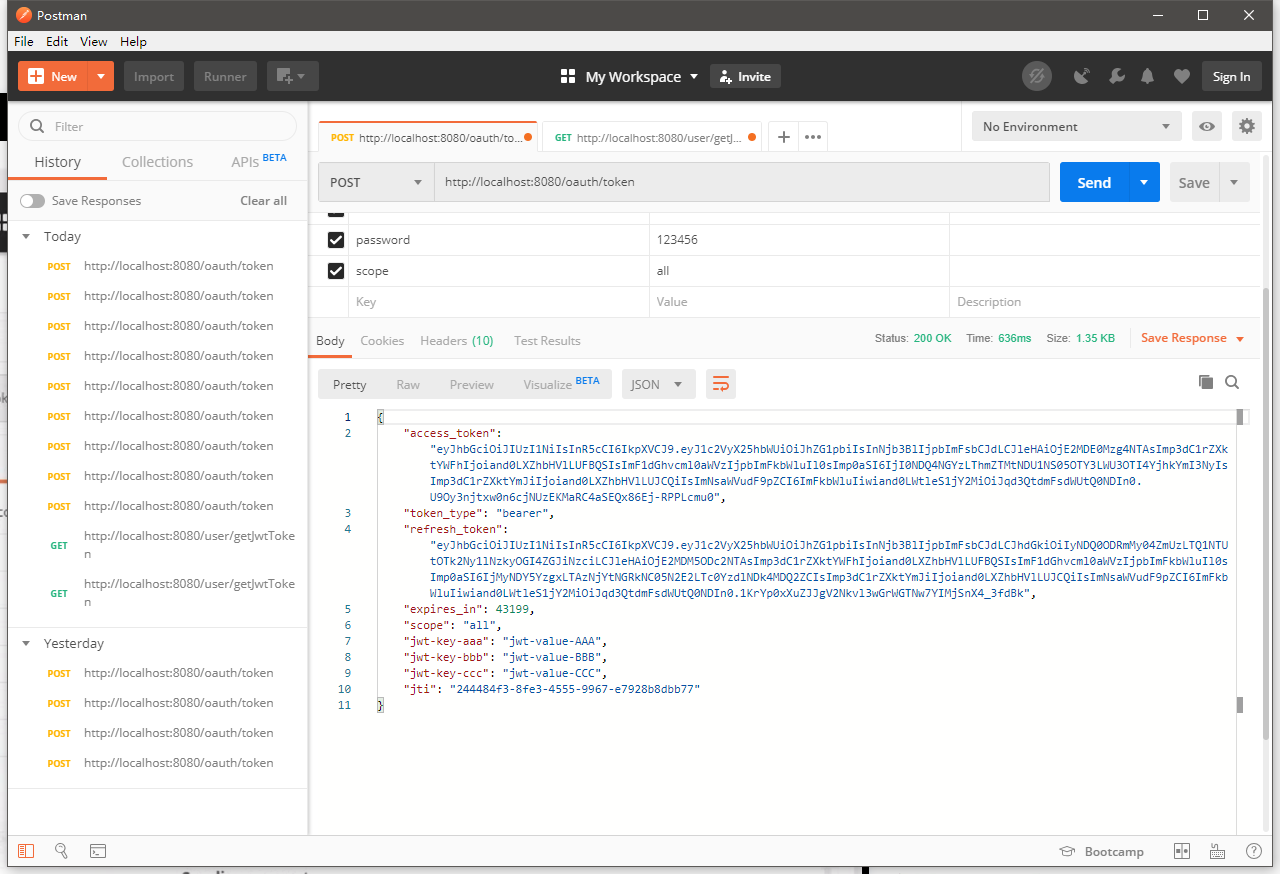
{ "access_token": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX25hbWUiOiJhZG1pbiIsInNjb3BlIjpbImFsbCJdLCJleHAiOjE2MDE0Mzg4NTAsImp3dC1rZXktYWFhIjoiand0LXZhbHVlLUFBQSIsImF1dGhvcml0aWVzIjpbImFkbWluIl0sImp0aSI6IjI0NDQ4NGYzLThmZTMtNDU1NS05OTY3LWU3OTI4YjhkYmI3NyIsImp3dC1rZXktYmJiIjoiand0LXZhbHVlLUJCQiIsImNsaWVudF9pZCI6ImFkbWluIiwiand0LWtleS1jY2MiOiJqd3QtdmFsdWUtQ0NDIn0.U9Oy3njtxw0n6cjNUzEKMaRC4aSEQx86Ej-RPPLcmu0", "token_type": "bearer", "refresh_token": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX25hbWUiOiJhZG1pbiIsInNjb3BlIjpbImFsbCJdLCJhdGkiOiIyNDQ0ODRmMy04ZmUzLTQ1NTUtOTk2Ny1lNzkyOGI4ZGJiNzciLCJleHAiOjE2MDM5ODc2NTAsImp3dC1rZXktYWFhIjoiand0LXZhbHVlLUFBQSIsImF1dGhvcml0aWVzIjpbImFkbWluIl0sImp0aSI6IjMyNDY5YzgxLTAzNjYtNGRkNC05N2E2LTc0YzdlNDk4MDQ2ZCIsImp3dC1rZXktYmJiIjoiand0LXZhbHVlLUJCQiIsImNsaWVudF9pZCI6ImFkbWluIiwiand0LWtleS1jY2MiOiJqd3QtdmFsdWUtQ0NDIn0.1KrYp0xXuZJJgV2Nkvl3wGrWGTNw7YIMjSnX4_3fdBk", "expires_in": 43199, "scope": "all", "jwt-key-aaa": "jwt-value-AAA", "jwt-key-bbb": "jwt-value-BBB", "jwt-key-ccc": "jwt-value-CCC", "jti": "244484f3-8fe3-4555-9967-e7928b8dbb77" }
以上面的刷新的令牌重新写入请求参数:

就可以以这个刷新令牌重新获得令牌:
{ "access_token": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX25hbWUiOiJhZG1pbiIsInNjb3BlIjpbImFsbCJdLCJleHAiOjE2MDE0MzkwNDcsImp3dC1rZXktYWFhIjoiand0LXZhbHVlLUFBQSIsImF1dGhvcml0aWVzIjpbImFkbWluIl0sImp0aSI6ImFmZjBlYTk0LTQ2YTctNDNmZi1iMTQzLTk3NmEzZmRkY2MxMyIsImp3dC1rZXktYmJiIjoiand0LXZhbHVlLUJCQiIsImNsaWVudF9pZCI6ImFkbWluIiwiand0LWtleS1jY2MiOiJqd3QtdmFsdWUtQ0NDIn0.ZA2tiTaJpKcnAMdKnVRH2M5zylb2DRTQGs7wYIXeQZE", "token_type": "bearer", "refresh_token": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX25hbWUiOiJhZG1pbiIsInNjb3BlIjpbImFsbCJdLCJhdGkiOiJhZmYwZWE5NC00NmE3LTQzZmYtYjE0My05NzZhM2ZkZGNjMTMiLCJleHAiOjE2MDM5ODc2NTAsImp3dC1rZXktYWFhIjoiand0LXZhbHVlLUFBQSIsImF1dGhvcml0aWVzIjpbImFkbWluIl0sImp0aSI6IjMyNDY5YzgxLTAzNjYtNGRkNC05N2E2LTc0YzdlNDk4MDQ2ZCIsImp3dC1rZXktYmJiIjoiand0LXZhbHVlLUJCQiIsImNsaWVudF9pZCI6ImFkbWluIiwiand0LWtleS1jY2MiOiJqd3QtdmFsdWUtQ0NDIn0.WJVF6_hSTDhKCAzIdX31BppArv6pYkHTOcymbEF5sBU", "expires_in": 43199, "scope": "all", "jwt-key-aaa": "jwt-value-AAA", "jwt-key-bbb": "jwt-value-BBB", "jwt-key-ccc": "jwt-value-CCC", "jti": "aff0ea94-46a7-43ff-b143-976a3fddcc13" }