Forensic examiners usually acquire images from suspect’s PC or Laptop. What if the target computer is not a physical PC/Laptop/Server? Let’s say the target computer is one of the VMs on a server, what will you do to acquire this VM?
Forensic guy 008 says that he will power off this VM and use EnCase or FTK to directly analyze those vmdk files. Yes EnCase/FTK could add vmdk file as evidence, but only few things found after processing. 008 couldn’t help wondering that EnCase/FTK could “see” everything inside those vmdk files or not?
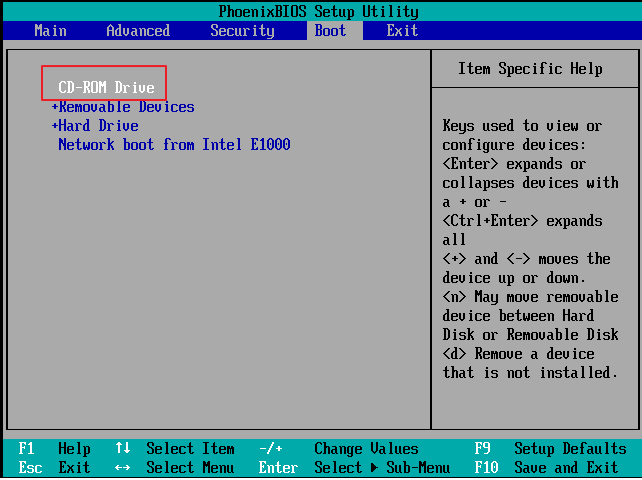
Forensic guy 007 decides to use forensic sound bootable LiveCD to acquire this VM. First he changes the boot order in BIOS setting of that VM to make sure“CD-ROM Drive”the first priority.
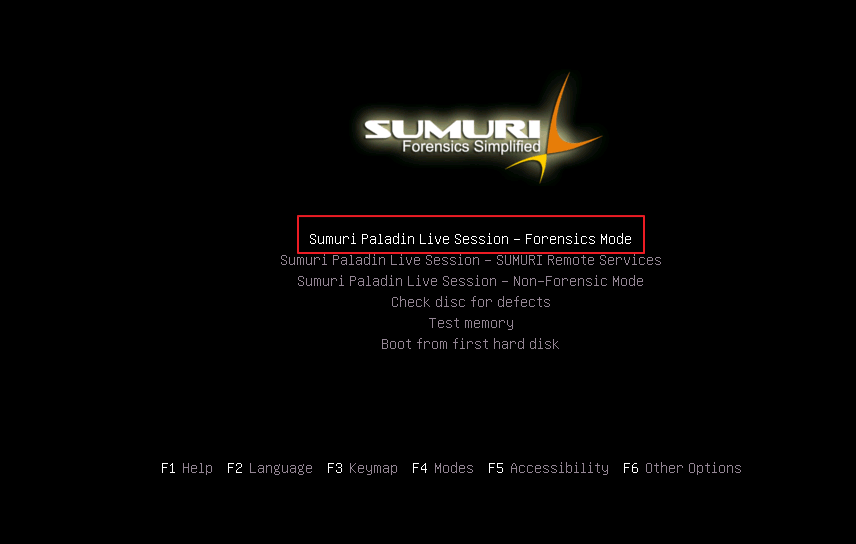
When powering on 007 could see the menu of Sumuri Paladin LiveCD, all he has to do is enter “Forensics Mode”.

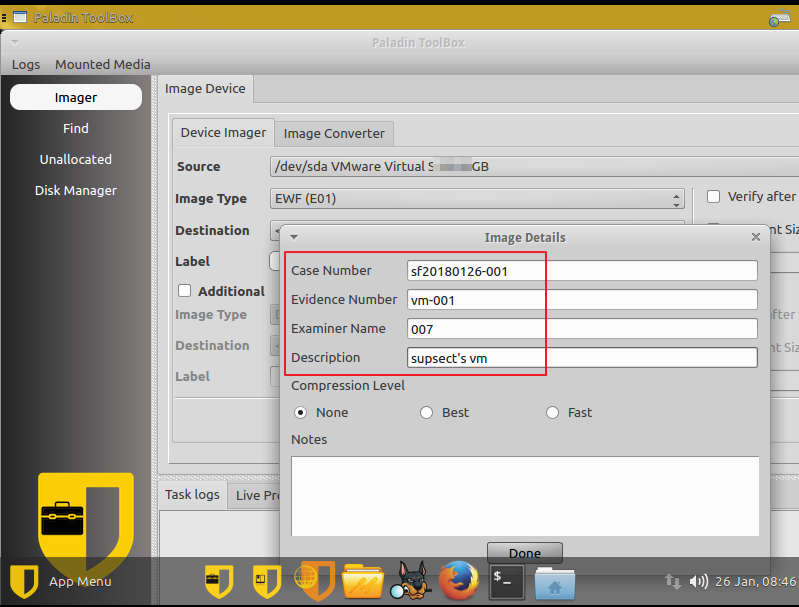
007 uses Paladin toolbox to acquire this VM and the image type is EWF(E01). He also inputs some image details such as case number、evidence number、examiner name, etc.
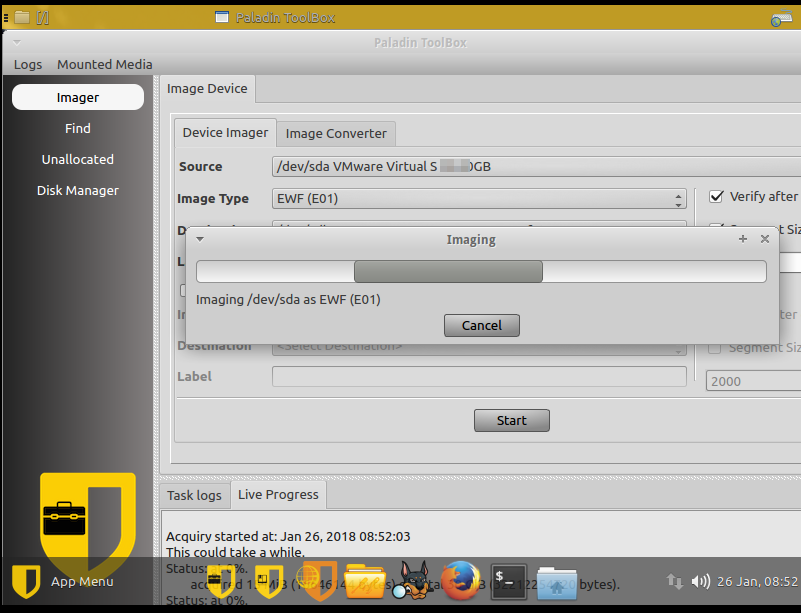
By the way do not forget to verify hash values after acquiring.
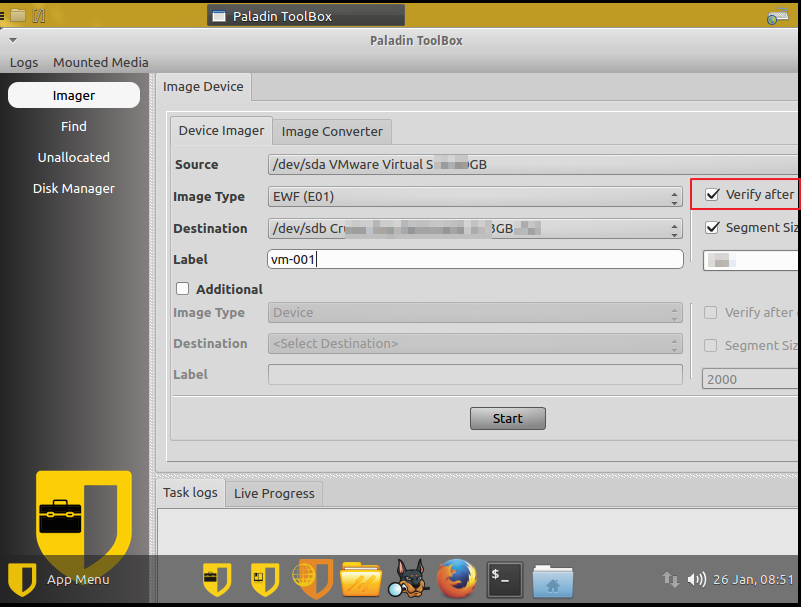
Paladin starts to acquire images from this VM. Once done you could use forensics tools to analyze these evidence files. I bet 007 extract more evidence than 008 did.