Easy
1.Basic Android
分析
主要函数

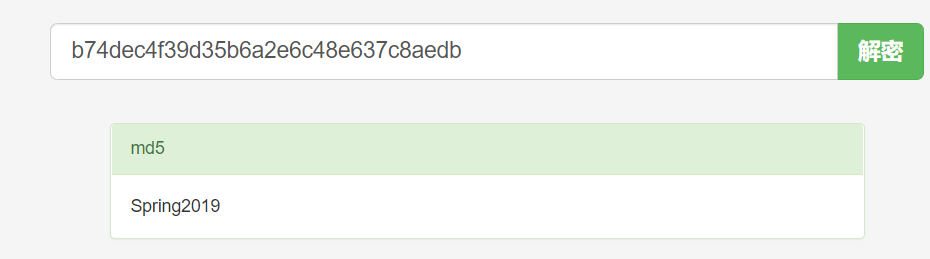
将输入的值转为MD5进行比较,若相等,则将输入的值拼接字符串输出。
解密
2.Reykjavik
分析

通过传入参数的方法来判断输入的flag是否正确。
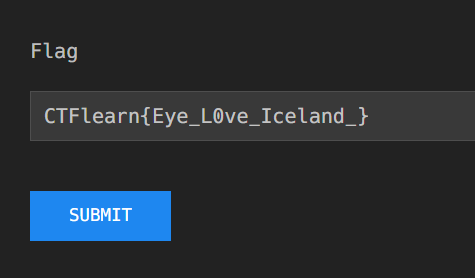
分析可知 flag= 加密后的密文异或0XAB
解密
脚本
str=[0xC5,0xD9,0xCA,0xCE,0xC7,0xED,0xFF,0xE8]
str1=[0xDD,0x9B,0xE7,0xF4,0xCE,0xD2,0xEE,0xD0]
str2=[ 0xC5,0xCA,0xC7,0xCE,0xC8,0xE2,0xF4,0xCE]
flag1=''
flag2=''
flag3=''
for i in str:
i^=0xab
flag1+=chr(i)
for i in str1:
i^=0xab
flag2+=chr(i)
for i in str2:
i^=0xab
flag3+=chr(i)
ss1=0x0CF^ 0xAB
ss2=0x0f4^ 0xAB
ss3=0x0d6^ 0xAB
print(flag1[::-1]+flag2[::-1]+flag3[::-1]+chr(ss1)+chr(ss2)+chr(ss3))
3.Riyadh
吐槽一下,这道题无脑,纯碎体力活。但是做后仔细一想,可以省略好多重复的操作。
分析
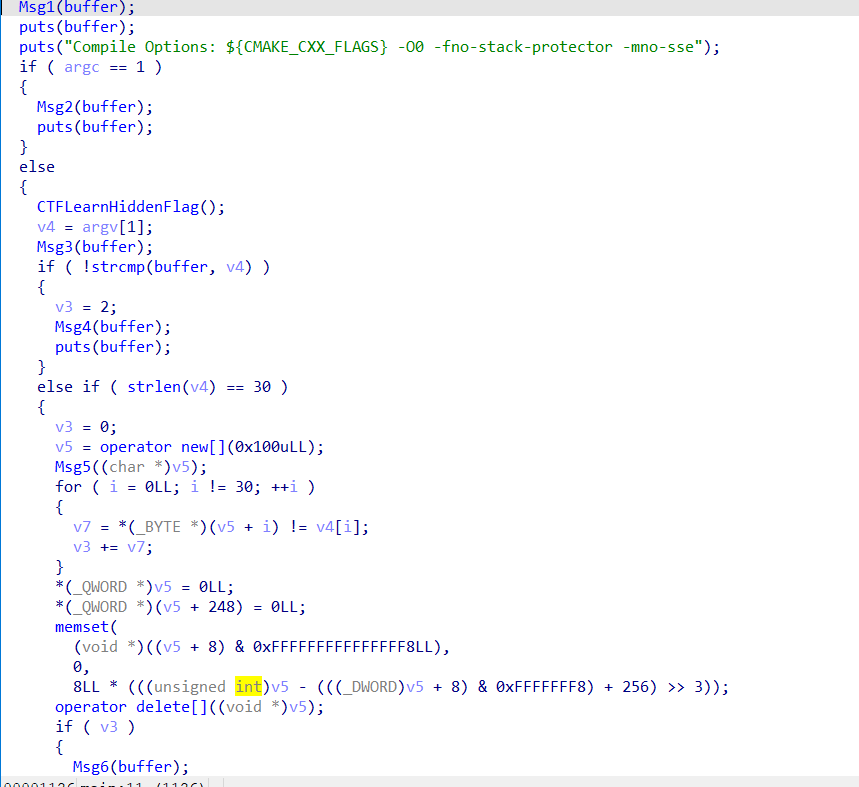
字符串全被加密过了。
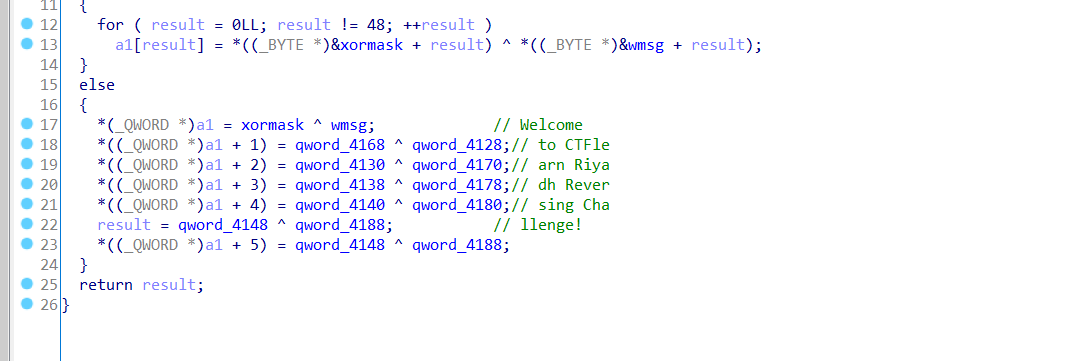
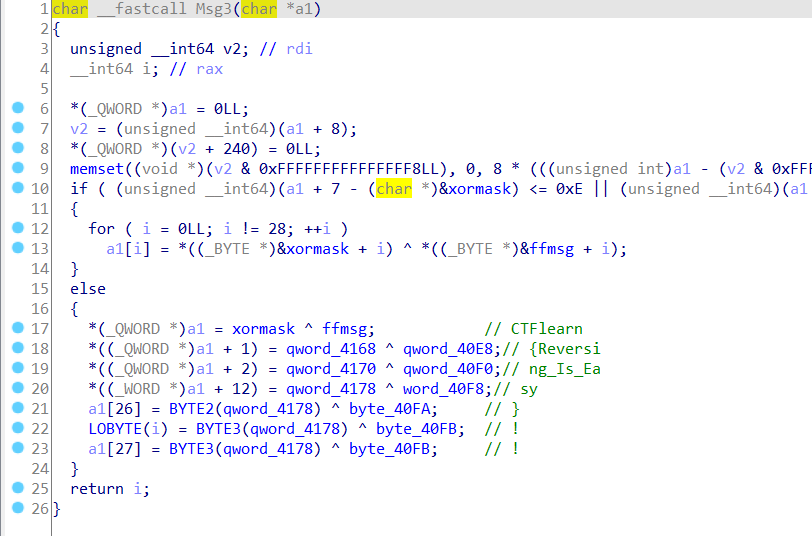
其他同。
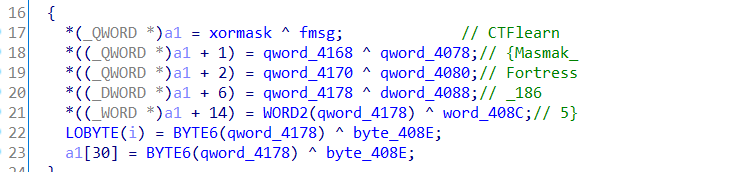
全部抠出来一步一步还原。到msg5函数的时候就出现flag了
ms3是假的
解密
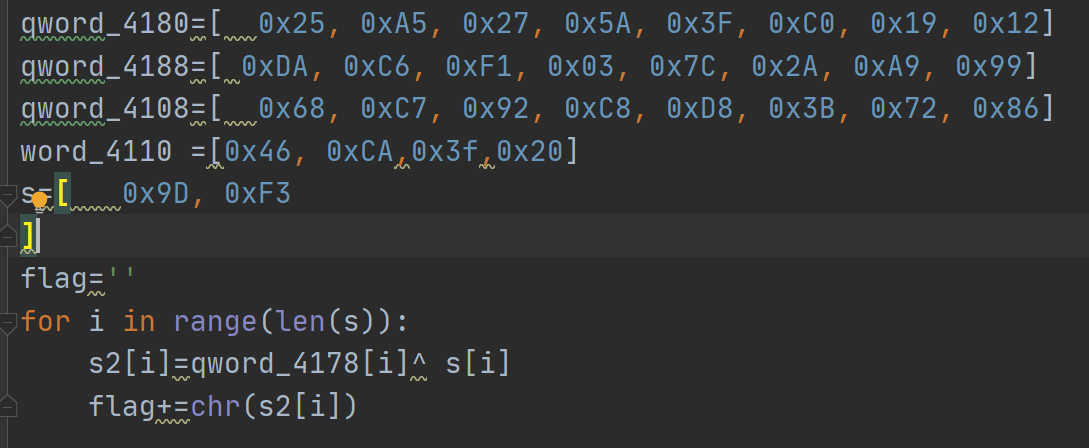
MID
1.RE_verseDIS
分析:
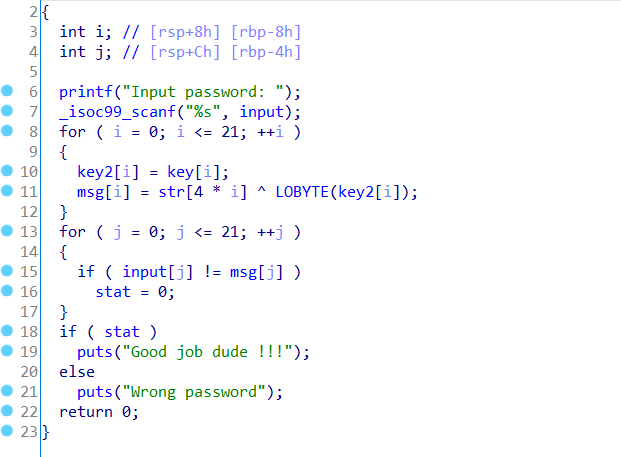
简单的异或
解密
str=[ 0x41, 0x62, 0x43, 0x54, 0x46, 0x7B, 0x72, 0x33, 0x76, 0x65,
0x72, 0x73, 0x31, 0x6E, 0x67, 0x5F, 0x64, 0x75, 0x64, 0x33,
0x7D, 0x00, 0x00, 0x00]
flag=''
for i in str:
flag+=chr(i)
print(flag)
#AbCTF{r3vers1ng_dud3}
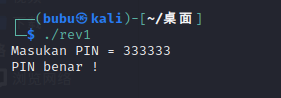
2.PIN
分析
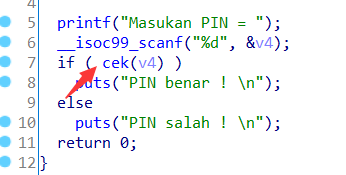
cek函数判断输入的值是否等于valid
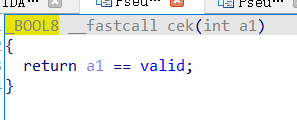

解密
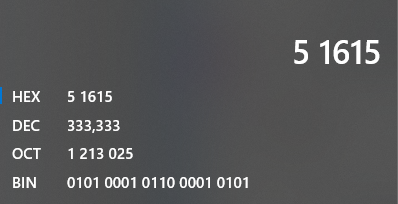
3.Time to Eat
分析
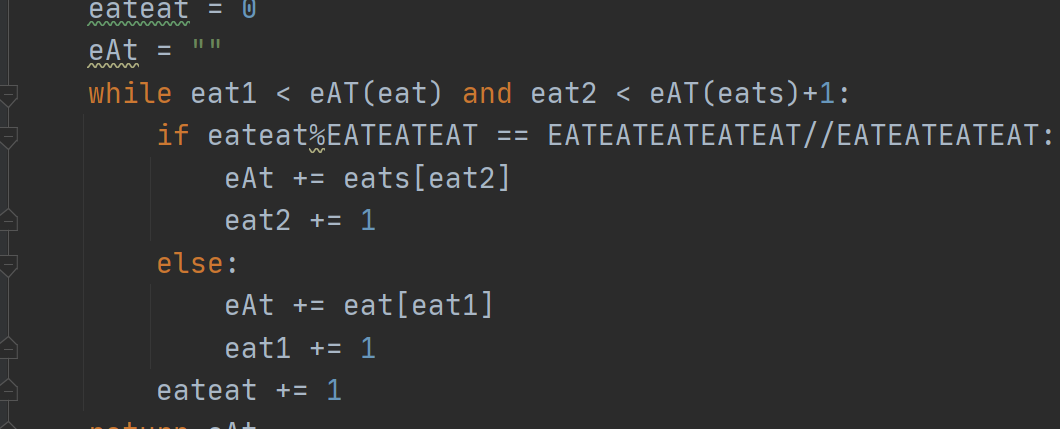
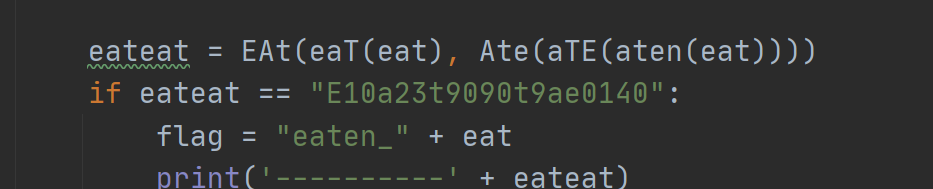
逆向一下然后跑一下,纯碎体力活
解密
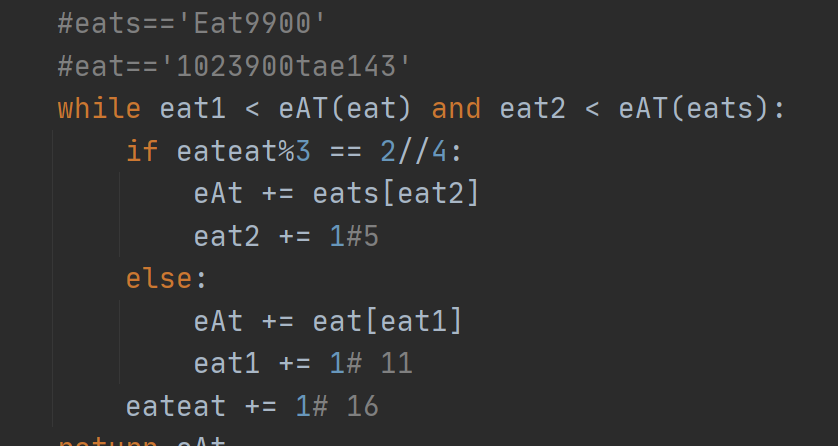
人肉还原了两个参数,再加大功率人肉对比函数还原出了flag
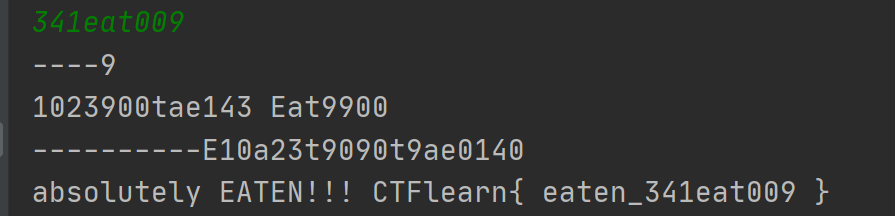
#CTFlearn{ eaten_341eat009 }#注意有空格
4.dis
分析
Disassembly of func2:
2 0 LOAD_FAST 1 (c2)
2 STORE_FAST 2 (tmp1)
3 4 LOAD_FAST 0 (c1)
6 STORE_FAST 3 (tmp2)
4 8 LOAD_FAST 2 (tmp1)
10 LOAD_FAST 3 (tmp2)
12 BINARY_XOR
14 RETURN_VALUE
Disassembly of func:
7 0 LOAD_GLOBAL 0 (open)
2 LOAD_CONST 1 ('flag.txt')
4 CALL_FUNCTION 1
6 LOAD_METHOD 1 (read)
8 CALL_METHOD 0
10 STORE_FAST 0 (fp)
8 12 LOAD_CONST 2 ('')
14 STORE_FAST 1 (cipher)
9 16 LOAD_GLOBAL 2 (range)
18 LOAD_GLOBAL 3 (len)
20 LOAD_FAST 0 (fp)
22 CALL_FUNCTION 1
24 CALL_FUNCTION 1
26 GET_ITER
>> 28 FOR_ITER 40 (to 70)
30 STORE_FAST 2 (i)
10 32 LOAD_GLOBAL 4 (func2)
34 LOAD_GLOBAL 5 (ord)
36 LOAD_FAST 0 (fp)
38 LOAD_FAST 2 (i)
40 BINARY_SUBSCR
42 CALL_FUNCTION 1
44 LOAD_CONST 3 (170)
46 CALL_FUNCTION 2
48 STORE_FAST 3 (temp)
11 50 LOAD_FAST 1 (cipher)
52 LOAD_GLOBAL 6 (chr)
54 LOAD_GLOBAL 4 (func2)
56 LOAD_FAST 3 (temp)
58 LOAD_FAST 2 (i)
60 CALL_FUNCTION 2
62 CALL_FUNCTION 1
64 INPLACE_ADD
66 STORE_FAST 1 (cipher)
68 JUMP_ABSOLUTE 28
12 >> 70 LOAD_GLOBAL 7 (print)
72 LOAD_FAST 1 (cipher)
74 CALL_FUNCTION 1
76 POP_TOP
13 78 LOAD_GLOBAL 0 (open)
80 LOAD_CONST 4 ('encrypted_flag.txt')
82 LOAD_CONST 5 ('w')
84 CALL_FUNCTION 2
86 SETUP_WITH 16 (to 104)
88 STORE_FAST 4 (f)
14 90 LOAD_FAST 4 (f)
92 LOAD_METHOD 8 (write)
94 LOAD_FAST 1 (cipher)
96 CALL_METHOD 1
98 POP_TOP
100 POP_BLOCK
102 BEGIN_FINALLY
>> 104 WITH_CLEANUP_START
106 WITH_CLEANUP_FINISH
108 END_FINALLY
110 LOAD_CONST 0 (None)
112 RETURN_VALUE
# output = éÿîÅËÎÞÃÙóÙÕÎÈÊúèÞÎÜÌÌÕÓÕìùÂéçÆÐþÿñÖËîÿôÿ
直接翻译就完了。也是体力活。
有几个不错的blog可以去看看
:https://www.cnblogs.com/blili/p/11799398.html
https://www.jianshu.com/p/bf9e2d9f4909
还有官网文档:
https://docs.python.org/3/library/dis.html
解密
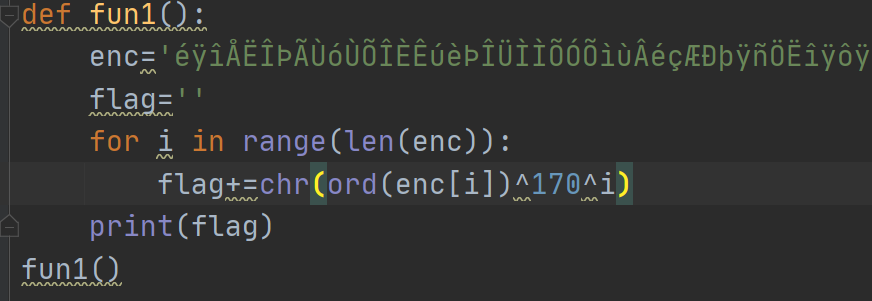
5.Reverse Me
分析

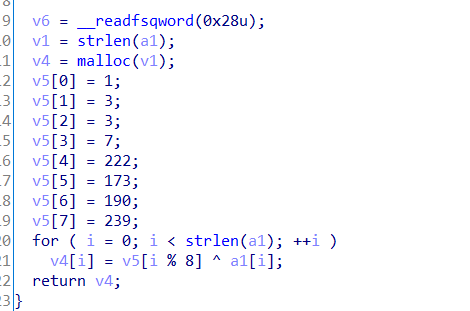
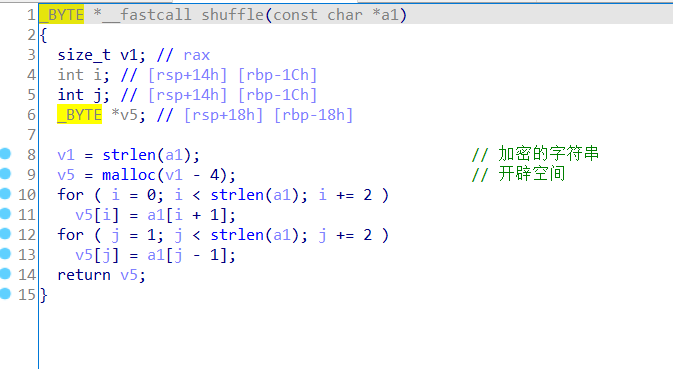
输入的字符串经过两个函数处理,一个进行异或加密,一个奇偶位变换。然后与v7中的字符串进行判断。
解密
脚本
v7=[0]*26
v7[0] = 87
v7[1] = 66
v7[2] = 75
v7[3] = 69
v7[4] = 204
v7[5] = -69+256
v7[6] = -127+256
v7[7] = -52+256
v7[8] = 113
v7[9] = 122
v7[10] = 113
v7[11] = 102
v7[12] = -33+256
v7[13] = -69+256
v7[14] = -122+256
v7[15] = -51+256
v7[16] = 100
v7[17] = 111
v7[18] = 110
v7[19] = 92
v7[20] = -14+256
v7[21] = -83+256
v7[22] = -102+256
v7[23] = -40+256
v7[24] = 126
v7[25] = 111
print(v7)
v6=[0]*26
for j in range(1,26,2):
v6[j]=v7[j-1]
for i in range(0,26,2):
v6[i]=v7[i+1]
print(v6)
v5=[0]*8
v5[0] = 1
v5[1] = 3
v5[2] = 3
v5[3] = 7
v5[4] = 222
v5[5] = 173
v5[6] = 190
v5[7] = 239
v4=[0]*26
#直接爆破
for i in range(26):
for f in range(0x20,0x7f):
enc=f
if v6[i]==v5[i%8]^enc:
print(chr(f),end='')
#CTFLearn{reversing_is_fun}
Hard
1.Lost In The Binary
分析:

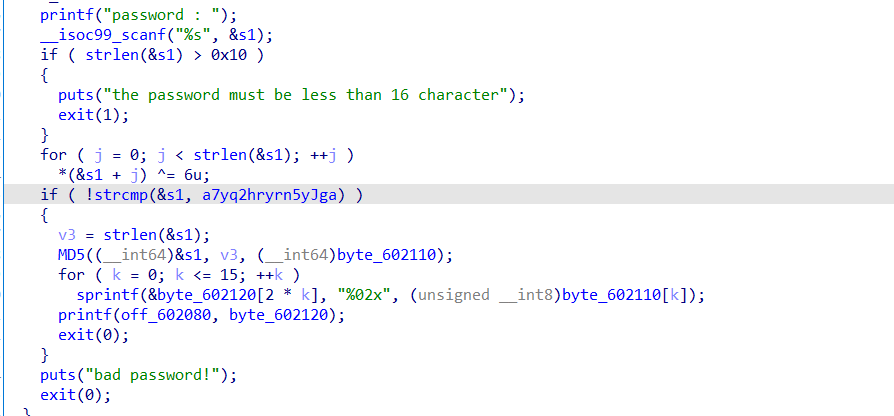
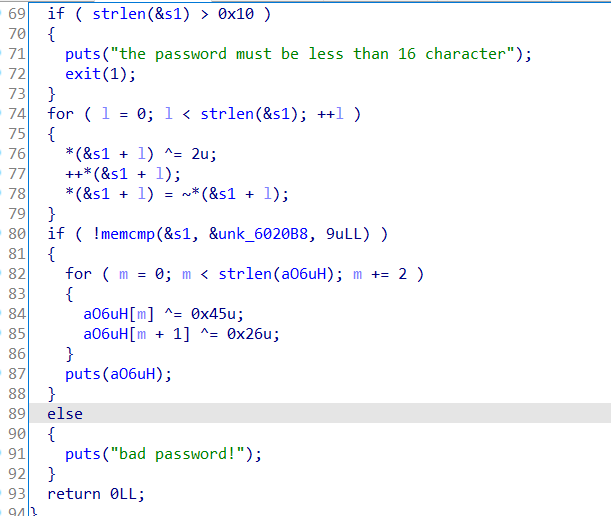
如果检测到被调试,则会执行错误语句,得出来的flag都是错误的。
解密
错误的:
str=[ 0x37, 0x59, 0x71, 0x32, 0x68, 0x72, 0x59, 0x52, 0x6E, 0x35,
0x59, 0x60, 0x6A, 0x67, 0x61]
flag=""
for i in range(15):
str[i]^=0x6
flag+=chr(str[i])
print(flag)
#1_w4nt_Th3_flag
str=[ 0x28, 0x4F, 0x36, 0x55, 0x2C, 0x48, 0x22, 0x06, 0x24, 0x54,
0x22, 0x53, 0x28, 0x43, 0x2B, 0x52, 0x36, 0x26]
flag=''
for i in range(0,18,2):
str[i]^=0x45
str[i+1]^=0x26
for i in range(len(str)):
flag+=chr(str[i])
print(flag)
#missing arguments
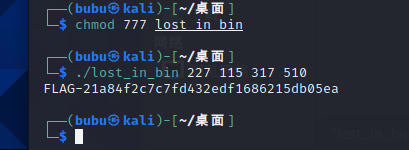
正确的应该用求出四个参数的值传进去。即可打印flag
from z3 import *
import _md5
qword_602148=Int('qword_602148')
qword_602150=Int('qword_602150')
qword_602158=Int('qword_602158')
qword_602160=Int('qword_602160')
# x,y=Ints('x','y')
s=Solver()
s.add(-24 * qword_602148 - 18 * qword_602150 - 15 * qword_602158 - 12 * qword_602160 == -18393)
s.add(9 * qword_602158 + 18 * (qword_602150 + qword_602148) - 9 * qword_602160 == 4419)
s.add(4 * qword_602158 + 16 * qword_602148 + 12 * qword_602150 + 2 * qword_602160 == 7300)
s.add(-6 * (qword_602150 + qword_602148) - 3 * qword_602158 - 11 * qword_602160 == -8613)
if s.check()==sat:
print(s.model())
#[qword_602160 = 510,
# qword_602148 = 227,
# qword_602158 = 317,
# qword_602150 = 115]
2.APK
分析
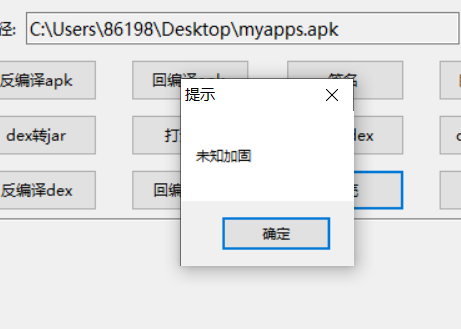
未加固