1.rndc远程管理
一般而言,dns服务都是很繁忙的,一台公网的dns会维护成千上万个zone,named服务不会轻易被重启,登陆dns服务器进行维护也有极大的风险,所以需要对named服务进行远程管理。
1.1.生成rndc-key
- 安装完bind9会自动生成rndc-key,在/etc/rndc.key
[root@hdss7-11 named]# cat /etc/rndc.key
key "rndc-key" {
algorithm hmac-sha256;
secret "lJULDN7O3rEJnyGVIItsD3XMN8nJ026f4sBTkKHb8JM=";
};
- 手动生成rndc.key
[root@hdss7-11 named]# rndc-confgen -r /dev/urandom
# Start of rndc.conf
key "rndc-key" {
algorithm hmac-md5;
secret "YcHr6Mdp/hFVnx+x81kELw==";
};
options {
default-key "rndc-key";
default-server 127.0.0.1;
default-port 953;
};
# End of rndc.conf
# Use with the following in named.conf, adjusting the allow list as needed:
# key "rndc-key" {
# algorithm hmac-md5;
# secret "YcHr6Mdp/hFVnx+x81kELw==";
# };
#
# controls {
# inet 127.0.0.1 port 953
# allow { 127.0.0.1; } keys { "rndc-key"; };
# };
# End of named.conf
1.2.把rndc-key和controls配置到bind的主配置文件的options段
[root@hdss7-11 ~]# vi /etc/named.conf
key "rndc-key" {
algorithm hmac-md5;
secret "YcHr6Mdp/hFVnx+x81kELw==";
};
controls {
inet 10.4.7.11 port 953
allow { 10.4.7.11;10.4.7.12; } keys { "rndc-key"; };
};
注意,这里需要配置一下controls段的acl,限定好哪些主机可以rndc管理DNS服务
1.3.重启bind9服务
[root@hdss7-11 ~]# systemctl restart named
[root@hdss7-11 ~]# netstat -nltup|grep 953
tcp 0 0 10.4.7.11:953 0.0.0.0:* LISTEN 20544/named
1.4.在远程管理主机上安装bind
[root@hdss7-12~]#yum install bind -y
远程主机安装bind,因为rndc命令在bind包里(不需要启动named)
1.5.在远程管理主机上做rndc.conf
注意:使用rndc管理的主机上,都需要配置rndc.conf,且rndc-key要和DNS服务器保持一致
[root@hdss7-12 named]# vi /etc/rndc.conf
key "rndc-key" {
algorithm hmac-md5;
secret "YcHr6Mdp/hFVnx+x81kELw==";
};
options {
default-key "rndc-key";
default-server 10.4.7.11;
default-port 953;
};
[root@hdss7-12 named]# rm -f /etc/rndc.key
1.6.使用rndc命令远程管理DNS
1.6.1.查询DNS服务状态(可以取值做监控)
[root@hdss7-12 named]# rndc status
version: BIND 9.11.4-P2-RedHat-9.11.4-9.P2.el7 (Extended Support Version) <id:7107deb>
running on hdss7-11.host.com: Linux x86_64 3.10.0-1062.4.1.el7.x86_64 #1 SMP Fri Oct 18 17:15:30 UTC 2019
boot time: Thu, 26 Dec 2019 00:28:41 GMT
last configured: Thu, 26 Dec 2019 00:28:41 GMT
configuration file: /etc/named.conf
CPUs found: 2
worker threads: 2
UDP listeners per interface: 1
number of zones: 106 (97 automatic)
debug level: 0
xfers running: 0
xfers deferred: 0
soa queries in progress: 0
query logging is OFF
recursive clients: 0/900/1000
tcp clients: 2/150
server is up and running
1.6.2.管理静态域
静态域zone文件
zone "od.com" IN {
type master;
file "od.com.zone";
allow-update { none; };
};
增、删、改、一条记录后
# rndc reload od.comzone
reload up-to-date
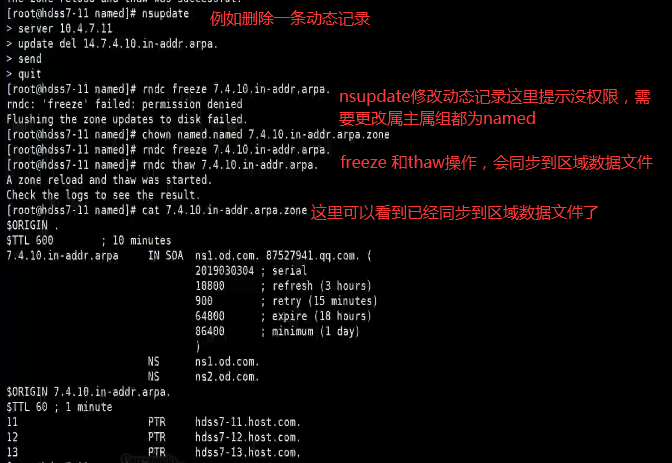
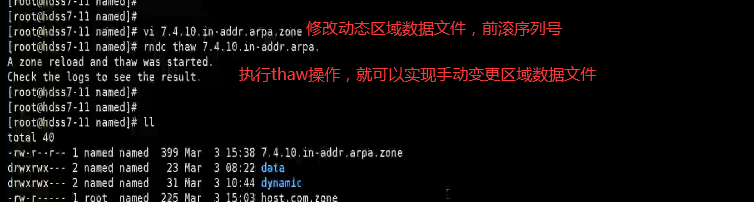
1.6.3.管理动态域(有rndc后可以手动变更区域数据文件)
动态域文件
zone "host.com" IN {
type master;
file "host.com.zone";
allow-update { 10.4.7.11; };
};
增、删、改、一条记录后其实是直接可以生效的(去域数据文件都是named权限)
#rndc reload host.com
rndc: 'reload' failed: dynamic zone 无需reload而且报错
需要先 freeze 再 thaw
#rndc freeze host.com
#rndc thaw host.com
The zone reload and thaw was successful.
示例:
有rndc后可以手动变更区域数据文件
2.智能DNS实战
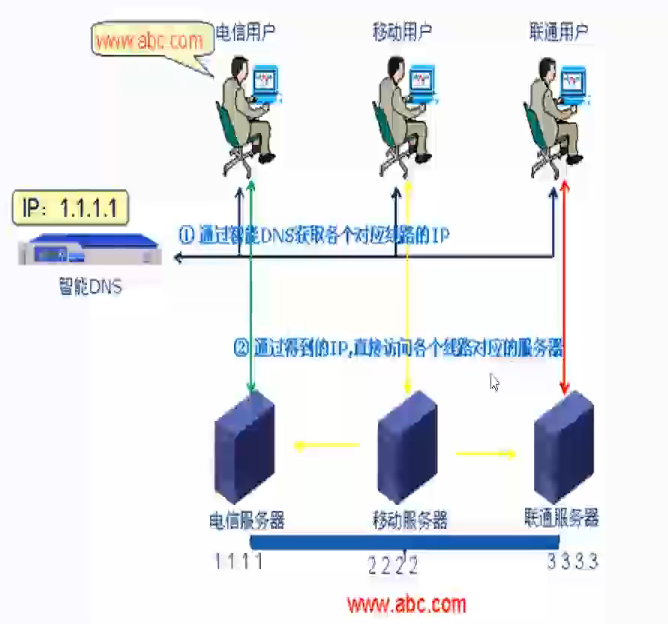
2.1.智能DNS概要
- 智能DNS就是根据用户的来路,自动智能化判断来路IP返回给用户,而不需要用户进行选择
- 比如一个企业的站点,3个运营商的带宽都有:电信、网通、移动,同样三个不同运营商网络的访问用户,那电信访问企业网址的时候,智能DNS会自动更具IP判断,再从电信返回给电信用户;
2.2.BIND的acl访问控制列表
2.2.1.4个内置acl
- any:任何主机
- none:没有主机
- localhost:本机
- localnet:本地子网所有IP
2.2.2.自定义acl
2.2.2.1. 简单acl
acl "someips" { //定义一个名为someips的ACL
10.0.0.1; 192.168.23.1; 192.168.23.15; //包含3个单个IP
};
2.2.2.2.复杂acl
acl "complex" { //定义一个名为complex的ACL
"someips"; //可以嵌套包含其他ACL
10.0.15.0/24; //包含10.0.15.0子网中的所有IP
!10.0.16.1/24; //非10.0.16.1子网的IP
{10.0.17.1;10.0.18.2;}; //包含了一个IP组
localhost; //本地网络接口IP(含实际接口IP和127.0.0.1)
};
2.2.3 使用acl
allow-update { "someips"; };allow-transfer { "complex"; };...
2.3.BIND9的view视图功能
- view语句定义了视图功能。视图是BIND9提供的强大的新功能,允许DNS服务器根据客户端的不同,有区别地回答DNS查询,每个视图定义了一个被特定客户端子集见到的DNS名称空间。这个功能在一台主机上运行多个形式上独立的DNS服务器时特别有用。
2.3.1.view的语法范例
view view_name [class] {
match-clients { address_match_list } ;
match-destinations { address_match_list } ;
match-recursive-only { yes_or_no } ;
[ view_option; ...]
[ zone-statistics yes_or_no ; ]
[ zone_statement; ...]
};
2.3.2.view配置范例1:按照不同业务环境解析
注:以下是内网DNS的view使用范例
acl "env-test" {
10.4.7.11;
};
acl "env-prd" {
10.4.7.12;
};
view "env-test" {
match-clients { "env-test"; };
recursion yes;
zone "od.com" {
type master;
file "env-test.od.com.zone";
};
};
view "env-prd" {
match-clients { "env-prd"; };
recursion yes;
zone "od.com" {
type master;
file "env-prd.od.com.zone";
};
};
view "default" {
match-clients { any; };
recursion yes;
zone "." IN {
type hint;
file "named.ca";
};
include "/etc/named.rfc1912.zones";
};
2.3.3.view配置范例2:智能DNS
注:以下特指公网智能DNS配置范例
//电信IP访问控制列表
acl "telecomip"{ telecom_IP; ... };
//联通IP访问控制列表
acl "netcomip"{ netcom_IP; ... };
view "telecom" {
match-clients { "telecomip"; };
zone "ZONE_NAME" IN {
type master;
file "ZONE_NAME.telecom.zone";
};
};
view "netcom" {
match-clients { "netcomip"; };
zone "ZONE_NAME" IN {
type master;
file "ZONE_NAME.netcom.zone";
};
};
view "default" {
match-clients { any; };
zone "ZONE_NAME" IN {
type master;
file "ZONE_NAME.zone";
};
};
3.bind-chroot和dnssec技术实战
- 用到公网DNS,在安全上必须引起注意,bind9本身是一个开源软件,免不了会有漏洞,通过哪些手断保证公网DNS的安全性呢?
- bind-chroot技术
- dnssec技术
3.1部署bind-chroot
注意,要用到公网主机,本次实验环境腾讯云主机,并有公网ip
3.1.1.系统环境
服务器:腾讯云主机,公网ip
OS:CentOS 7.5.1804
bind-chroot:bind-chroot-9.11.4-9.P2.el7
3.1.2.yum安装
[root@VM_0_15_centos etc]# yum remove bind
[root@VM_0_15_centos ~]# yum install bind-chroot -y
//会将bind一并安装
3.1.3.配置bind-chroot
- bind-chroot本质上就是使用chroot方式给bind软件换了个“根”,这时bind软件的“根”在/var/named/chroot下,弄懂这一点,配置起来就跟bind9没什么区别了
- 把yum安装的bind-chroot 在 /etc下产生的配置文件硬链接到/var/named/chroot/etc下
/var/named/chroot/etc
[root@VM_0_15_centos ~]# cd /var/named/chroot/etc/
[root@VM_0_15_centos etc]# ls /etc/named
named/ named-chroot.files named.conf named.iscdlv.key named.rfc1912.zones named.root.key
[root@VM_0_15_centos etc]# ln /etc/named.* .
/var/named/chroot/var/named
[root@VM_0_15_centos named]# pwd
/var/named/chroot/var/named
[root@VM_0_15_centos named]# ln /var/named/named.* .
[root@VM_0_15_centos named]# mkdir data/ dynamic/ slaves/ dnssec-key/
[root@VM_0_15_centos named]# chown -R named.named data/ dynamic/ slaves/ dnssec-key/
[root@VM_0_15_centos named]# ll
3.1.4./etc/named.conf主配置文件
编辑主配置文件,修改以下几项,把53端口开放到公网
options {
listen-on port 53 { any; };
allow-query { any; };
recursion yes;
dnssec-enable yes;
dnssec-validation yes;
dnssec-lookaside auto;
};
3.1.4.测试
使用随便一台主机测试
[root@hdss7-12 ~]# dig -t A baidu.com @111.231.227.17 +short
220.181.38.148
39.156.69.79
这里可以查到百度,因为recursion 是开启的,但是在生产中,此选项一般为no
3.2.使用dnssec技术维护一个业务域
- 在公网上使用BIND9维护的业务域,最好使用dnssec技术对该域添加数字签名 *
- DNSSEC(DNS Security Extension)—-DNS安全扩展,主要是为了解决DNS欺骗和缓存污染问题而设计的一种安全机制。
DNSSEC技术参考文献1
DNSSEC技术参考文献2
3.2.1.打开dnssec支持选项
/etc/named.conf
dnssec-enable yes;
dnssec-validation yes;
dnssec-lookaside auto;
3.2.2.配置一个业务域bkjf-inc.com
/etc/named.rfc1912.zones
zone "bkjf-inc.com" IN {
type master;
file "bkjf-inc.com.zone";
key-directory "dnssec-key/bkjf-inc.com";
inline-signing yes;
auto-dnssec maintain;
allow-update { none; };
};
3.2.3.创建数字签名证书
/var/named/chroot/var/named/dnssec-key
[root@VM_0_13_centos dnssec-key]# mkdir bkjf-inc.com
[root@VM_0_13_centos dnssec-key]# chgrp named bkjf-inc.com
[root@VM_0_13_centos dnssec-key]# cd bkjf-inc.com
[root@VM_0_13_centos bkjf-inc.com]# dnssec-keygen -a RSASHA256 -b 1024 bkjf-inc.com
Generating key pair..................................++++++ .++++++
Kbkjf-inc.com.+008+53901
[root@VM_0_13_centos bkjf-inc.com]# dnssec-keygen -a RSASHA256 -b 2048 -f KSK bkjf-inc.com KSK bkjf-inc.com
Generating key pair..........................................................................................+++ ............................................
.....+++
Kbkjf-inc.com.+008+40759
[root@VM_0_13_centos bkjf-inc.com]# chgrp named *
[root@VM_0_13_centos bkjf-inc.com]# chmod g+r *.private
[root@VM_0_13_centos bkjf-inc.com]# ll
total 16
-rw-r--r-- 1 root named 607 Feb 28 14:10 Kbkjf-inc.com.+008+40759.key
-rw-r----- 1 root named 1776 Feb 28 14:10 Kbkjf-inc.com.+008+40759.private
-rw-r--r-- 1 root named 433 Feb 28 14:10 Kbkjf-inc.com.+008+53901.key
-rw-r----- 1 root named 1012 Feb 28 14:10 Kbkjf-inc.com.+008+53901.private
这里如果生成秘钥的速度很慢,需要yum安装一下haveged软件并开启
# systemctl start haveged.service
3.2.4.创建区域数据库文件
/var/named/chroot/var/named/bkjf-inc.com.zone
[root@VM_0_13_centos named]# cat bkjf-inc.com.zone
$TTL 600 ; 10 minutes
@ IN SOA ns1.bkjf-inc.com. 87527941.qq.com. (
2018121605 ; serial
10800 ; refresh (3 hours)
900 ; retry (15 minutes)
604800 ; expire (1 week)
86400 ; minimum (1 day)
)
NS ns1.bkjf-inc.com.
NS ns2.bkjf-inc.com.
$ORIGIN bkjf-inc.com.
$TTL 60 ; 1 minute
ns1 A 192.144.198.128
ns2 A 192.144.198.128
www A 192.144.198.128
eshop CNAME www
3.2.5.启动bind-chroot服务
# systemctl start named-chroot
3.2.6.自动生成了签名zone
如果启动成功且配置无误,应该自动生成了带签名的zone
/var/named/chroot/var/named/
[root@VM_0_13_centos named]# ll
total 60
-rw-r--r-- 1 root named 507 Feb 28 14:34 bkjf-inc.com.zone
-rw-r--r-- 1 named named 512 Feb 28 14:26 bkjf-inc.com.zone.jbk
-rw-r--r-- 1 named named 742 Feb 28 14:35 bkjf-inc.com.zone.jnl
-rw-r--r-- 1 named named 4102 Feb 28 14:44 bkjf-inc.com.zone.signed
-rw-r--r-- 1 named named 7481 Feb 28 14:35 bkjf-inc.com.zone.signed.jnl
检查签名区需要用到完全区域传送
[root@VM_0_13_centos named]# dig -t AXFR bkjf-inc.com @localhost
; <<>> DiG 9.9.4-RedHat-9.9.4-73.el7_6 <<>> -t AXFR bkjf-inc.com @localhost
;; global options: +cmd
bkjf-inc.com. 600 IN SOA ns1.bkjf-inc.com. 87527941.qq.com. 2018121608 10800 900 604800 86400
bkjf-inc.com. 86400 IN RRSIG NSEC 8 2 86400 20190330063503 20190228053503 53901 bkjf-inc.com. 0fyLJXxaDOI+RWnYjK2tGpd6WgbWmgeIADtjpPQFQLrv1X9fuDLi2MFR q0+csg5P22eVUdasKi3q5tMmFW8GZtLEBBVtOtSba3/FvtoitvyBGcG6 KJ155dPbhEFe/eR0/JhWtFsIsyj/UHtgELB4eGYJYCeEI+WzUopT7voz 4UE=
bkjf-inc.com. 86400 IN NSEC eshop.bkjf-inc.com. NS SOA RRSIG NSEC DNSKEY TYPE65534
bkjf-inc.com. 600 IN RRSIG NS 8 2 600 20190330063017 20190228053309 53901 bkjf-inc.com. Y/T0m4p0yNrJwJiHc0mjDgit/9E4h7MXPb5F2WgBd+huXYgL0pS0vOb3 c2aRvHHW/zngPjShOfy3sYY5203SzPS15tN6E/RAs36/I33sZE7jZBFo 9q0KjEdKHNsoC9XISSdbLPCX879/B1rKZcmhpPNmhpAK6P351nWWgd9L jtU=
bkjf-inc.com. 600 IN RRSIG SOA 8 2 600 20190330063503 20190228053503 53901 bkjf-inc.com. eE3nKlCmAZrjJ3DwdzPStYmrC38X6VCqCxIc6otLJDX65Uk2uSqGSPre WIu16zEsbuuxq7/38ABrupQNwkPAgaSaiLIRC/000PXzKsUPhll0xO4x u9tLg2LBRATQ+4dHpKtLsoBTX0nXVHlz09YeAAA82r5wyQye2/ebesxH +A4=
bkjf-inc.com. 0 IN RRSIG TYPE65534 8 2 0 20190330054441 20190228053309 53901 bkjf-inc.com. sEX7jpdTbUZ3hlIR2CRWHbgceAQFVOVKnVl6CXvyQhavIFjUyBMMhXTw hKYwXd2Hc0LGg9koWJqlt0oYS8YbXacKbeBUrLovmcbYP46Uhm05zaVo jswG7oYYsYDE3ekbl5ImnAEyjksSNOgk8if/WoUvXfF5QH6Rdl+6Q3qG cEI=
bkjf-inc.com. 600 IN RRSIG DNSKEY 8 2 600 20190330063309 20190228053309 53901 bkjf-inc.com. rUGjMTxmbthB6UbmemoorQOfuen8u0xeOosl7lPRNLV2Hk7KsAZzUD2/ tRAJaY9NRZ1JhZHkmX/N5hncuVpPxZnrp8UB7qOoairqgjA73IFGoT0F 00KIU0FZaqsQAbBSzpzfbwr9KVbn1hTAq6/5Q/wrWZvQOASMYrF5Xhr9 lW4=
bkjf-inc.com. 600 IN RRSIG DNSKEY 8 2 600 20190330063309 20190228053309 40759 bkjf-inc.com. lBXWXbTshdeH/oOkBGdwIspet0ABbhUZfzAXUjOP3ivCMW5sse3ZayEA qPe6mZncURqomWNA/xQKemoJJjtlAwc5F4CjmtrUierdy3EVVKS0NFnz 9L3PxiJcOxl1VVtSBX+XAOPa0xkS3cpEbFVOym4NaKsoLgcqKKBjjBu4 dhWoXoxXk7PE5fogo9/BM0heGI4XpnixUSTbucMw4bcnNYPY0qKUBs2o alt1CvrGz78oOO10//pXpw/ml89UwWo28/FDvxeuXS7soeImDRklTLlE xV/Q3//v7o73ZosAdSR+9xFdcZtVs43Jjo3Cy8WL1Zjz6BdRd59Fyu6h WghEKg==
bkjf-inc.com. 0 IN TYPE65534 # 5 08D28D0001
bkjf-inc.com. 0 IN TYPE65534 # 5 089F370001
bkjf-inc.com. 600 IN DNSKEY 256 3 8 AwEAAflXAWLXAVJUEj29iidwVvZALuQr03hLn1bEl81XDtD63H7wwHS9 i9fNDYL0q0FkRDkuzXEQpb3UUleu/RYtSd9w6Ads0RWNUyB6X1E4Djmv sPwFwvo570svZSVky2rjEHnySgVI2ywqhcRYLMKjxE6pXuzXrqecQcF2 qrMq2xmJ
bkjf-inc.com. 600 IN DNSKEY 257 3 8 AwEAAbxFYlbq+R8y/hGg/xL8xDBasZGYtgPOqVd3bP68p98YHsFwHyG8 u3svatzRoq8STNjKKZEluDC2bcUIn9/mRHyorTYPtwyePxPEgVE4yhBy 9xqD4ES+ty7kuHOUz/WEHdNdYRhYyHe+SGf4dHnmU49pHIBCE8xFX6fs t270webjuXs4Pt6qRlyoFC3XmpRDiMNVwtM+doUxo/MRK4mw5zTeHyyf dFLVOvE3mW/ZKgBfnrsj0zE71bnD5nTxJIjDv1bUppbiRy5RK40jPhHu zaa3quxg1yS/BceYcjJpZJUc3LS55HGzatfuK799KvukuDKf7u71ylW+ 5ynT7Sxhbt0=
bkjf-inc.com. 600 IN NS ns1.bkjf-inc.com.
bkjf-inc.com. 600 IN NS ns2.bkjf-inc.com.
eshop.bkjf-inc.com. 86400 IN RRSIG NSEC 8 3 86400 20190330063503 20190228053503 53901 bkjf-inc.com. dHM2PhYs7BVuhD//iGhcwPZGZmHDkBCfWKju6ZZlvSx3I+QmWWvVdKCj 8YCw2AkWhgARxFfRMzhxRwDjgEgHhxUr4UGPH9+kJpvGi+UpFBVoBvPw iL43qCn/4J2f6URuAY8Dcq0DFpR0QLVJgIXBZpyhUYu5hZNWI2tzfyhO GlM=
eshop.bkjf-inc.com. 86400 IN NSEC ns1.bkjf-inc.com. CNAME RRSIG NSEC
eshop.bkjf-inc.com. 60 IN RRSIG CNAME 8 3 60 20190330063503 20190228053503 53901 bkjf-inc.com. 9ONt81AjpHFrM8YwDm7pQAg62oDBgaNzdtDIqtBHt5h/BPl83fOP/dOp P0Xi+y/OsFjDzHBSBDU4sy3fJwHBqm8uuMc6m33pIZfTq15fxFXF+2hU ift1bc0b0dk/L7ANZ5haEsDcl+hSVjwru2o2ISJtvp5zySZ61pdMvA6y ktg=
eshop.bkjf-inc.com. 60 IN CNAME www.bkjf-inc.com.
ns1.bkjf-inc.com. 60 IN RRSIG A 8 3 60 20190330063017 20190228053309 53901 bkjf-inc.com. 9MUZhsTxlmn5B6QXg/iCQoFyilRh8H4OJcTgpu1KgSyMTiBoEwJGdhIx k2XimlJZr9/MrSeRbuLwMZOnwFJ7w9fcIunrYHiE1T71y0BcLnQOKaJf SkJI5VKUam80+J6unkscCj0i/Y1kXTjXWLODKsZzw4+zLz5cGJk6hvsn XP4=
ns1.bkjf-inc.com. 86400 IN RRSIG NSEC 8 3 86400 20190330063017 20190228053309 53901 bkjf-inc.com. EFeX2LsEd/flN2/5lCgKlSTtC93WH0LDw9GW1RAlLIfxFAptPsXkmy7y B0Blt7tOuaxA/cTNbnFZBnyo8G3YW90LnYagqeuNzl+90gjUxsbbhE4f pTkQkRXRsvcagYDKQjs9nkN1SAF13SagnupR8D2crHADICjy8RHjHtgA byM=
ns1.bkjf-inc.com. 86400 IN NSEC ns2.bkjf-inc.com. A RRSIG NSEC
ns1.bkjf-inc.com. 60 IN A 192.144.198.128
ns2.bkjf-inc.com. 60 IN RRSIG A 8 3 60 20190330063017 20190228053309 53901 bkjf-inc.com. N2ssp0Eh6SyHBYHskedxUpfIp29DETt2g74sCuhrXwMuwLjOdVwuB02i /LqzDLyDbVZnMZncqoQ367AV2b/ttU/FJZcHiAlI2tLRTxVuNyj/E2YN BIDAtIqueNdJzsyE7n1yz9sPcsTrOidrIqqbM3qom5tMQvdo+2jrnhR3 UoY=
ns2.bkjf-inc.com. 86400 IN RRSIG NSEC 8 3 86400 20190330063017 20190228053309 53901 bkjf-inc.com. sTTRnUQxPBbeAG0WrQpn4iK/U62D2s8umLwx8w8bx+bwxQdhR8Yyz8Ke tSelkffgctCtyUi5i7ibSTnvUJTcvOcvWWteMOQfQqXJmAngADx87cba /M+OJqRwp8tu3PEniPpTYN3msGSEFILyxLCO/2cyBzK+8jhFFKYyMOn/ ViQ=
ns2.bkjf-inc.com. 86400 IN NSEC www.bkjf-inc.com. A RRSIG NSEC
ns2.bkjf-inc.com. 60 IN A 192.144.198.128
www.bkjf-inc.com. 60 IN RRSIG A 8 3 60 20190330063017 20190228053309 53901 bkjf-inc.com. aKI5N4y6eqN/xunC7+4vYa3cSHyXcW533iGA6/q34/ahvq0sTgYN36aF oBO0t8fRvwS3chZaPxwuqbk6hGSW+tRhJ8x/Nnwtbcn004W0ZxI1k046 JW/ePLhq1Cw2GPHXJTsfCjYmAOcwssX2yUv6q9/vocXx/mipuTMljrId yhE=
www.bkjf-inc.com. 86400 IN RRSIG NSEC 8 3 86400 20190330063017 20190228053309 53901 bkjf-inc.com. 0q3C+xMKE1p586q+p8U4AHGiNjzzI899TcmL2P4x8x1B7rkc22rsakX9 AnNFAzkPOTVLr81GQtBraI1K6El2QDKcPkE9+0e+34tirpuUzVlzjYB2 f4WHGxTscdOMpCestqnmspQpmXm37+EBWS0alBBq3Db8T+F/3CSEGRS7 Ao0=
www.bkjf-inc.com. 86400 IN NSEC bkjf-inc.com. A RRSIG NSEC
www.bkjf-inc.com. 60 IN A 192.144.198.128
bkjf-inc.com. 600 IN SOA ns1.bkjf-inc.com. 87527941.qq.com. 2018121608 10800 900 604800 86400
;; Query time: 1 msec
;; SERVER: 127.0.0.1#53(127.0.0.1)
;; WHEN: Thu Feb 28 15:22:46 CST 2019
;; XFR size: 31 records (messages 1, bytes 3433)
这里看到每个记录都附带了一个RRSIG记录,说明已经进行了数字签名
3.2.7.检查本地解析
[root@VM_0_13_centos named]# dig -t A www.bkjf-inc.com @localhost +dnssec +short
192.144.198.128
A 8 3 60 20190330063017 20190228053309 53901 bkjf-inc.com. aKI5N4y6eqN/xunC7+4vYa3cSHyXcW533iGA6/q34/ahvq0sTgYN36aF oBO0t8fRvwS3chZaPxwuqbk6hGSW+tRhJ8x/Nnwtbcn004W0ZxI1k046 JW/ePLhq1Cw2GPHXJTsfCjYmAOcwssX2yUv6q9/vocXx/mipuTMljrId yhE=
3.2.8.DS记录
在生成证书的目录对ZSK执行dnssec-dsfromkey命令,得到bkjf-inc.com的DS记录,这里我们使用比较长的那个
/var/named/chroot/var/named/dnssec-key/bkjf-inc.com
[root@VM_0_13_centos bkjf-inc.com]# dnssec-dsfromkey `grep -l zone-signing *key`
bkjf-inc.com. IN DS 53901 8 1 5E13F6C0ECEE84248C2543693CE7D8617920983B
bkjf-inc.com. IN DS 53901 8 2 3006068B784AFBBC67133F123A0C389514959FCB6CAB0032DB200F08E6E5C384
其中:
53901:关键标签,用于标识域名的DNSSEC记录,一个小于65535的整数值
8:生成签名的加密算法,8对应RSA/SHA-256
2:构建摘要的加密算法,2对应SHA-256
最后一段:摘要值,就是DS记录值
参考万网(阿里云)上关于dnssec配置的文档:参考文档
DS记录需要通过运营商提交到上级DNS的信任锚中,这里是通过万网的配置页面,提交到.com域
注意:要在阿里云上将该域名的dns服务器指向自定义DNS服务器:参考文档
3.2.9.后续文虎
dnssec需要定期轮转,所以需要经常变更签名,其中
- ZSK轮转
建议每年轮转
- KSK轮转
建议更新ssl证书后尽快轮转?
轮转方法:
- ZSK(zone-signing key)
/var/named/chroot/var/named/dnssec-key/bkjf-inc.com
$ cd /var/named/chroot/var/named/dnssec-key/bkjf-inc.com
$ dnssec-settime -I yyyy0101 -D yyyy0201 Kbkjf-inc.com.+008+53901
$ dnssec-keygen -S Kbkjf-inc.com.+008+53901
$ chgrp bind *
$ chmod g+r *.private
- KSK轮转(key-signing key)
/var/named/chroot/var/named/dnssec-key/bkjf-inc.com
$ cd /var/named/chroot/var/named/dnssec-key/bkjf-inc.com
$ dnssec-settime -I yyyy0101 -D yyyy0201 Kbkjf-inc.com.+008+40759
$ dnssec-keygen -S Kbkjf-inc.com.+008+40759
$ chgrp bind *
$ chmod g+r *.private
注意:KSK轮转需要同步在万网上更新DS记录
3.2.10.在任意客户端验证解析
#dig -t A www.bkjf-inc.com @8.8.8.8 +dnssec +short
192.144.198.128
A 8 3 60 20190330063017 20190228053309 53901 bkjf-inc.com. aKI5N4y6eqN/xunC7+4vYa3cSHyXcW533iGA6/q34/ahvq0sTgYN36aF oBO0t8fRvwS3chZaPxwuqbk6hGSW+tRhJ8x/Nnwtbcn004W0ZxI1k046 JW/ePLhq1Cw2GPHXJTsfCjYmAOcwssX2yUv6q9/vocXx/mipuTMljrId yhE=
#dig CNAME eshop.bkjf-inc.com @8.8.8.8 +dnssec +short
www.bkjf-inc.com.
CNAME 8 3 60 20190330063503 20190228053503 53901 bkjf-inc.com. 9ONt81AjpHFrM8YwDm7pQAg62oDBgaNzdtDIqtBHt5h/BPl83fOP/dOp P0Xi+y/OsFjDzHBSBDU4sy3fJwHBqm8uuMc6m33pIZfTq15fxFXF+2hU ift1bc0b0dk/L7ANZ5haEsDcl+hSVjwru2o2ISJtvp5zySZ61pdMvA6y ktg=
3.2.11.在第三方网站验证
https://en.internet.nl/site/www.bkjf-inc.com/473349/